By Raghav K.
Enterprise networks have their share of complexities and advantages. In a distributed setting, there are different factors to counter and leverage. Networks have faced infiltration attempts for years. Barricading as a preventive measure helped keep networks and resources secure. While that was not a comprehensive approach to maintaining security, infrastructure integrity, and solutions, it was the only line of defense against malicious attacks.
After the introduction of cloud-native, containers based on Kubernetes have helped enterprises achieve their true potential. Cloud-native microservices have provided many advantages for building large applications that require a faster development to deployment cycle alongside innovation. Microservices swapped the traditional monolithic application approach for a simpler and more agile one.
Zero-trust security helps ensure a highly-secure environment and a scalable security solution that can ease your way out while managing the growing number of microservices. It can also help simplify the complexities related to SDLC. Microservices may sound like a security hassle, but it provides a much easier approach to secure an entire application. You can achieve superior system security after implementing the zero-trust security model with microservices.
There is a representation of the microservices classification on the Alibaba Cloud platform listed below:
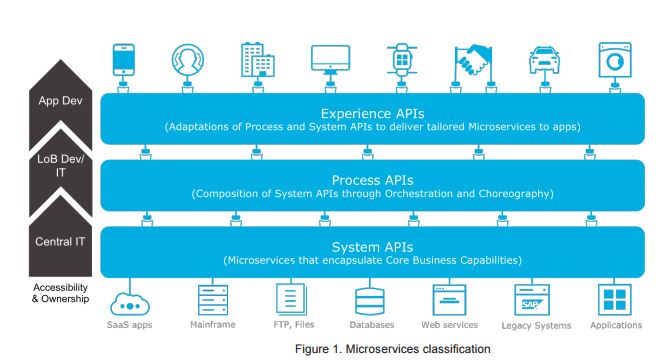
Traditionally, the security created fencing for resources, and everything inside was trusted automatically. In a traditional approach, resources can access each other without much resistance since they share the same primary codebase. However, microservices architecture is based on a more loosely coupled approach. This ensures that different resources can only be called using APIs, making the system more secure.
I am not insinuating that the traditional methods of putting up barriers like firewalls should be retired. These security solutions are still useful, but relying on the traditional security approach is an outdated idea. Everything is evolving, and security has evolved using models like zero-trust.
Whether it is the microservices architecture or containers based on Kubernetes, the zero-trust security model should be implemented for an up-to-date and comprehensive security structure. Service Mesh has emerged as an option to provide architectural stability when using Kubernetes for containerization.
The Alibaba Cloud Service Mesh (ASM) architecture is listed below:
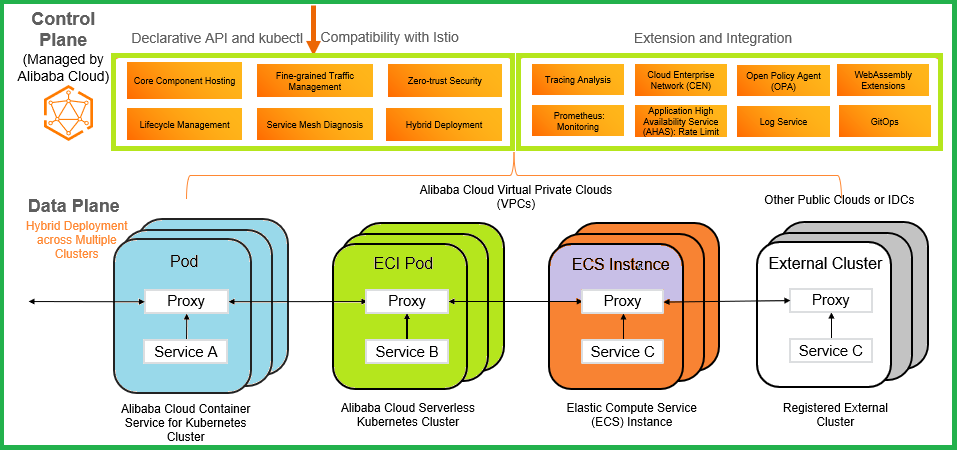
Alibaba Cloud Service Mesh is a fully-managed service that is highly compatible with the open-source lstio service mesh. Service Mesh is designed to manage services easily.
You can use Service Mesh with microservices applications since it is deeply integrated with the Container Service for Kubernetes (ACK). You can manage traffic for microservices across multiple Kubernetes clusters using Service Mesh. It provides consistent communication control over containerized applications.
The deep integration with Alibaba Cloud ACK, networks, and security capabilities helps Alibaba Cloud ASM enable zero-trust security with containers and microservices. Alibaba Cloud ASM can extend superior traffic shaping and observability for each microservice while creating a consistent service mesh on the cloud. This enables a deeper analysis of services and protocols to ensure no entity is left out when implementing the zero-trust security architecture.
Implementing security capabilities using Service Mesh is the introduction to zero-trust capabilities with your microservices architecture and containers. It is highly recommended to introduce the zero-trust security model as a design parameter rather than just retro-fitting it to existing systems. However, for environments that are pre-cloud native, migration might be an overload. Alibaba Cloud Service Mesh offers great migration scenarios to counter that scenario.
You can use Alibaba Cloud ASM to deploy and configure ASM instances to migrate existing applications to Alibaba Cloud. ASM offers a seamless migration scenario based on real-world transmission capabilities. Migration from a data center to the cloud is not only about application migration. Alibaba Cloud ASM allows you to dynamically route the incoming traffic to data centers or the cloud resources to migrate stateless services.
The Alibaba Cloud ASM migration architecture is listed below:
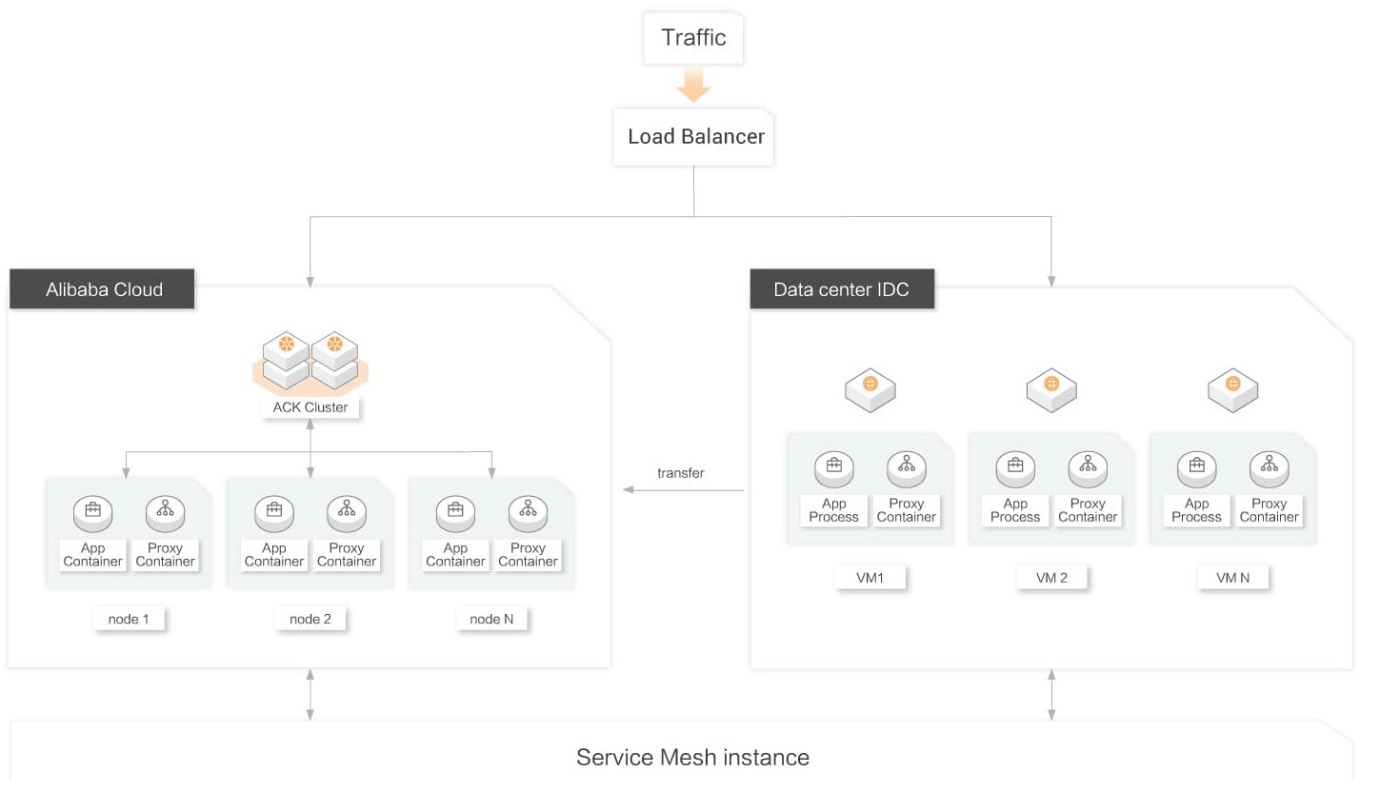
Implementing the zero-trust security architecture is all about controlling access using identity. If we talk about real-world scenarios, trust is the only thing that can be leveraged to gain access to an entire system. The most critical and sophisticated systems can be crippled in minutes due to the monolithic security approach. The zero-trust security model cuts down on automatic trust, ensuring greater security and stability for your microservices and containers.
Zero-Trust Security – Part 2: Getting Started with Zero-Trust Security

2,593 posts | 793 followers
FollowAlibaba Clouder - February 22, 2021
Alibaba Clouder - February 20, 2021
Alibaba Developer - January 5, 2022
Alibaba Clouder - February 26, 2021
Alibaba Cloud Community - May 19, 2022
Alibaba Cloud Native Community - May 17, 2022

2,593 posts | 793 followers
Follow Platform For AI
Platform For AI
A platform that provides enterprise-level data modeling services based on machine learning algorithms to quickly meet your needs for data-driven operations.
Learn More Epidemic Prediction Solution
Epidemic Prediction Solution
This technology can be used to predict the spread of COVID-19 and help decision makers evaluate the impact of various prevention and control measures on the development of the epidemic.
Learn More Microservices Engine (MSE)
Microservices Engine (MSE)
MSE provides a fully managed registration and configuration center, and gateway and microservices governance capabilities.
Learn More Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn MoreMore Posts by Alibaba Clouder