Recently, in the process of analyzing network attack logs based on threat intelligence, Alibaba Cloud's Security Team discovered an attack using the vulnerability of ShowDoc to spread botnets and mining software. This botnet spreading event has not yet been publicly reported.
ShowDoc is an online document sharing tool that provides developers with document writing and team collaboration features based on APIs. As early as August 2020, a vulnerability of arbitrary file upload was exposed and was numbered CNVD-2020-49480. The specific cause of this vulnerability is that when the file upload interface is called, the suffix logic of the verification file is incorrect, and the upload interface lacks permission authentication.
As a result, attackers can bypass authentication and suffix detection to upload webshell directly. Based on this, they can implant malicious programs relating to DDoS attacks and mining to execute arbitrary files.
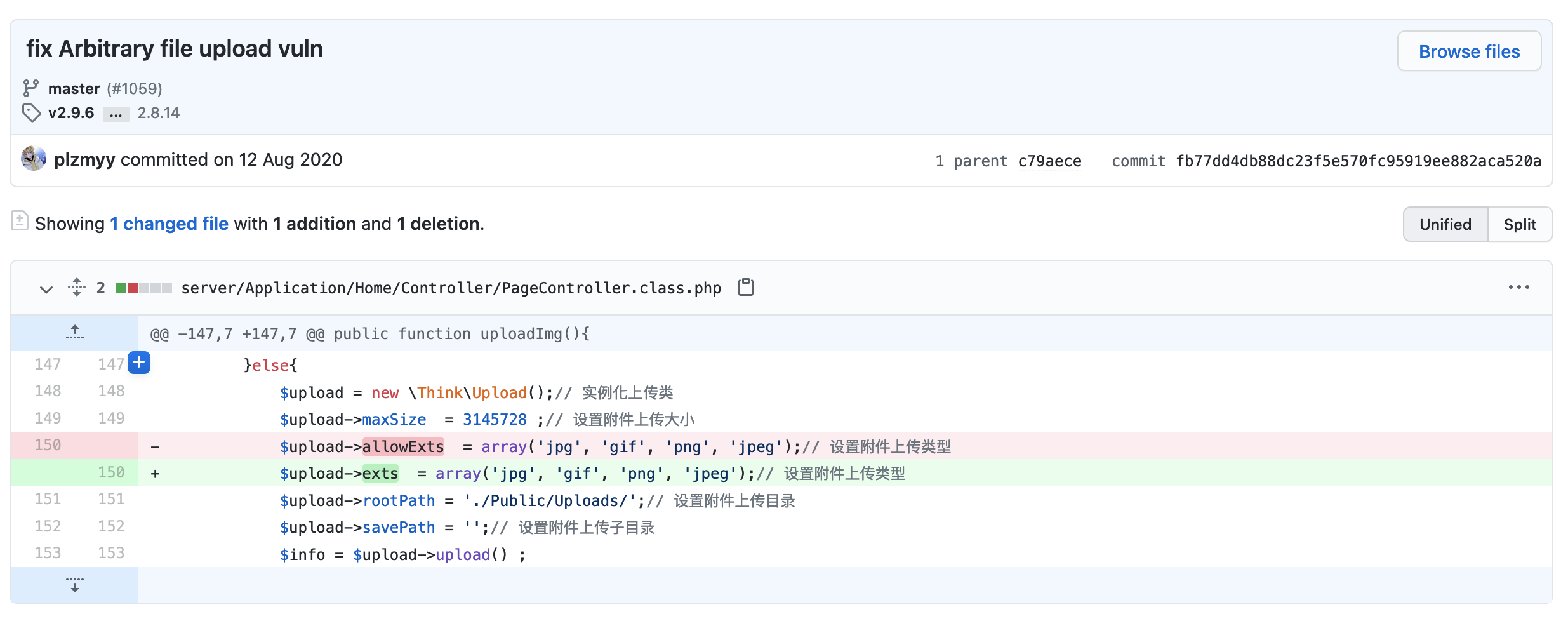
Figure 1: Patch for vulnerability fixing
When implementing the file upload interface, ShowDoc refers to the code implementation logic from the older version. The whitelist array of attachment suffixes is restricted by the $upload->allowExts parameter in Think PHP 3.1. In fact, after Think PHP 3.2, this logic is modified. The new one is implemented by using $upload->exts, resulting in no whitelist restriction on suffixes. The php file upload check is bypassed, and webshell files can be uploaded directly. The principle of using this vulnerability is relatively simple. The PoC attack code has already been published on the Internet. Attackers can easily integrate it into the attack library.
Although ShowDoc released a patch for this vulnerability in August last year, it is found on the Internet that a small number of ShowDoc services have not been upgraded to the latest version. These websites of earlier versions are vulnerable to intrusion after being scanned and identified by attackers. They are prone to suffer continuous attacks and implantation of malicious programs, causing continuous interception alerts about malicious behaviors from Security Center.
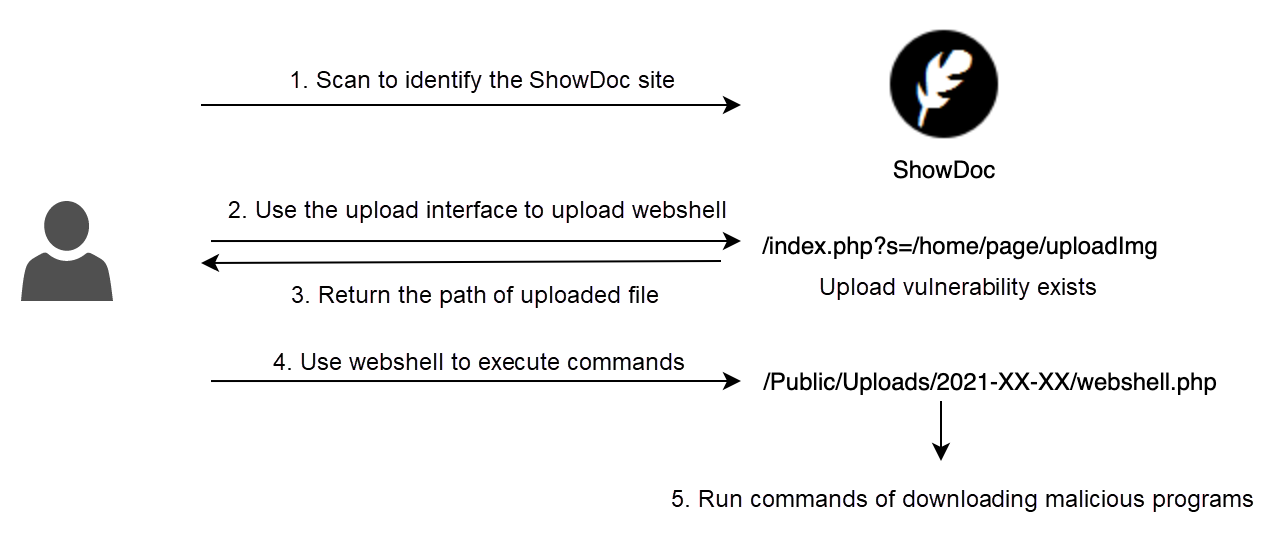
Figure 2: Attack process
This wave of attacks was first detected on April 24. Through the attack logs, it is assumed that the attacker has developed a scanning tool to identify ShowDoc assets. The attacker uses Python to automatically exploit the vulnerability to upload webshell, record webshell paths, and further install malicious codes relating to DDoS attacks and mining on the basis of webshell.
The main implanted malwares include DDoS Trojan and Monero mining software, involving malwares from the Srv-Hello, Mirai, BillGates, and other families. The related malware families have been reported and analyzed many times, so this article will not analyze them again.
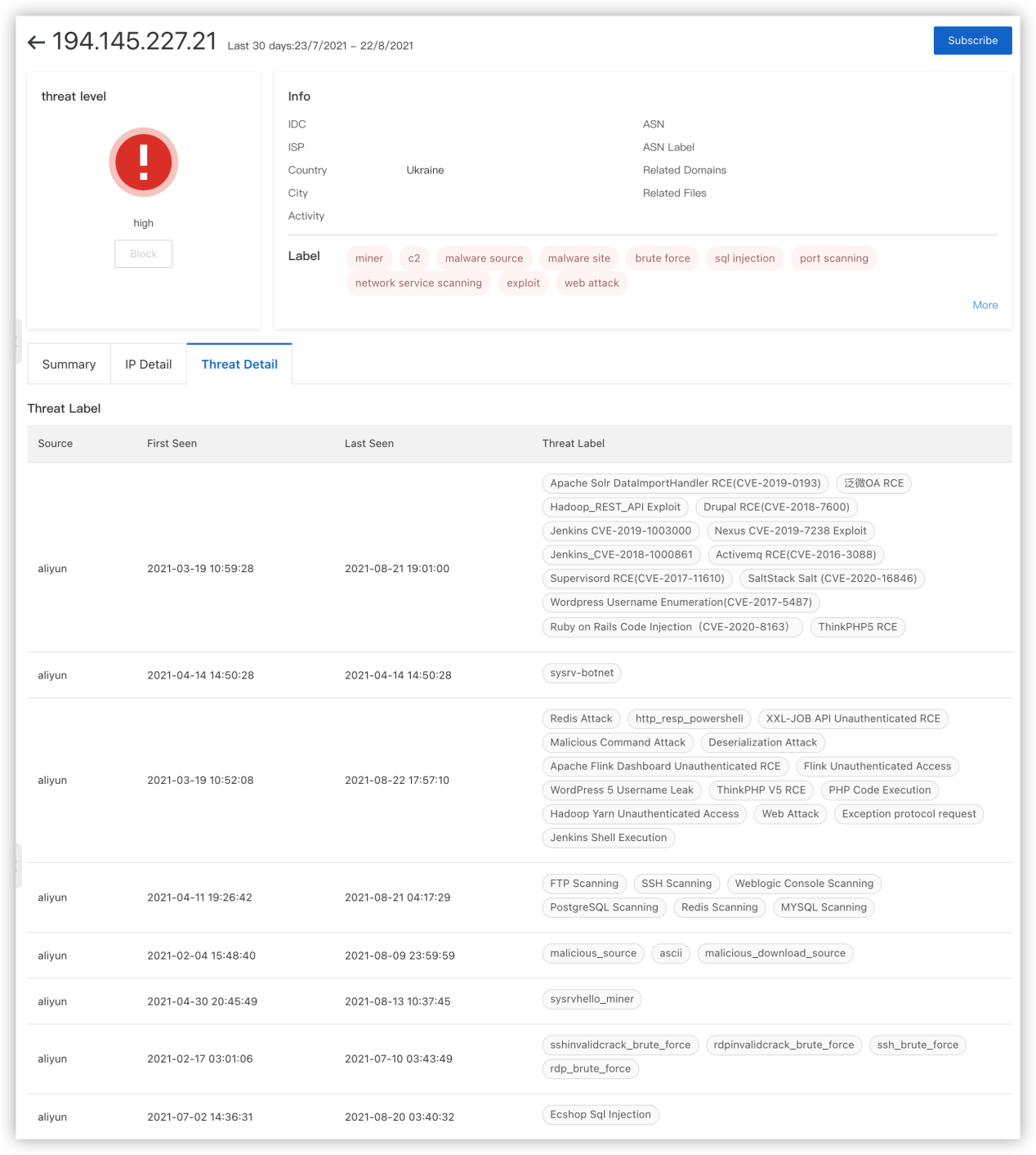
Figure 3: Query result on threat intelligence
By querying Alibaba Cloud threat intelligence, we can further obtain historical attack information and related data. For example, by querying the IP address 194[.]145.227.21, we found that this IP address not only provides downloads of malicious attack load but also actively scans a variety of common web systems and services. It exploits various vulnerabilities to initiate external attacks to spread malicious code and is in an active state.
Although ShowDoc is not a common web program, it is still noticed by attackers as an attack target. This shows that attackers actively integrate various vulnerabilities driven by interests. As long as the program has vulnerabilities, these vulnerabilities will be quickly integrated into the library and used to automatically spread malicious code.
This also poses new challenges to security practitioners and requires continuous monitoring to discover new attack methods. By combining with threat intelligence, these potential new attack methods can be discovered, and attacks can be handled more efficiently.
Public/Uploads/2021-XX-XX/, and delete the webshell.Wallet address:
47tZYnxtpUmNk9d548NX756zFPZbMsQ7wcKkxzz9kdWn6tmeteN5aMy22qNn4cMjLsahnVkLV1DrL61kRyqtxDFKFHxdGEC
434THCMTb45dXej46oBCDfYYKriK6qzCiaG5koJmCeTeiXDZ3rSTuZCacNNuuVvYrkL4VX6dXKCzB7W2ARTwg2w6R3r3WFfURL:
hxxp://1.117.4.172:999/BOT/1
hxxp://104.244.73.78:85/Content/Upload/Activity/20210725043923.jpg
hxxp://107.172.214.23:1234/xmss
hxxp://107.189.7.37:802/25000
hxxp://107.189.7.37:802/LinuxTF
hxxp://107.189.7.37:802/Manager
hxxp://107.189.7.37:802/linuxdoor
hxxp://107.189.7.37:802/manager
hxxp://117.24.13.169:881/25
hxxp://117.24.13.169:881/BOT
hxxp://117.24.13.169:881/L26
hxxp://117.24.13.169:991/25000
hxxp://119.45.253.226:8001/hackable/uploads/13.sh
hxxp://119.45.253.226:8001/hackable/uploads/unixt
hxxp://168.206.255.6:9876/ddos32-64
hxxp://180.215.192.107:8080/Q
hxxp://180.215.192.107:8080/c
hxxp://180.215.192.107:8080/door
hxxp://180.215.192.123:8080/12.4
hxxp://180.215.192.123:8080/13
hxxp://180.215.192.123:8080/Manager
hxxp://180.215.192.123:8080/linuxdoor
hxxp://180.215.192.123:8080/vv
hxxp://180.215.192.123:8080/ww
hxxp://180.215.194.46:8080/32u
hxxp://180.215.194.46:8080/dos32
hxxp://194.145.227.21/ldr.sh?b54287f2
hxxp://194.145.227.21/ldr.sh?localssh
hxxp://194.145.227.21/sys.x86_64
hxxp://194.56.226.37/s.cmd
hxxp://1w.kacdn.cn:81/Linux-syn10000
hxxp://209.141.34.100/1
hxxp://209.141.34.100/132
hxxp://209.141.34.100/udp
hxxp://216.83.33.79:8080/synDomain name:
1[.]117.4.172
104[.[244.73.78
107[.]172.214.23
107[.]189.7.37
117[.]24.13.169
119[.]45.253.226
168[.]206.255.6
180[.]215.192.107
180[.]215.192.123
180[.]215.194.46
180[.]215.194.46
194[.]145.227.21
194[.]56.226.37
1w.kacdn.cn
209[.]141.34.100
216[.]83.33.79MD5:
e196d8c69ea072edd4313a0a9265b386
f6ba14ab7e8f5513cc81035e13615dec
b7d56da2a700d17f27cfb504012cc6c7
57c5af8338ff8bd9abfe878ba9e8e661
346fe44a4d58863a098b72e1584e95e8
d51ba1fee712aac5a3a17129782115af
d4989e13b700431c8760013a990edf0d
da63a2f797b27f31745cfb8f94479bf4
d51ba1fee712aac5a3a17129782115af
c67607c0927154a4d2efd79ad502cc7d
46c7302fe138e6a877755a3b5203303a
346fe44a4d58863a098b72e1584e95e8
da63a2f797b27f31745cfb8f94479bf4
a419dfe06954bc6bfbe7115d0ae95102
c9ab5b3125119fd83ffb0b27b392d613
7c50cd6c767052e28a23c4d89c90983a
a158814f8a22c68987be16e79c8bff0f
e611eafc4b5e422a2665bf5644b818e3
1d228318d5f2fefe4b04f82449777e40
122e36483aa697f8d6df252b76c1c8bf
06f25d5598cb026c0b97484ad80a3b43
542b52ae8f4d6dde9eb2fdc003eedc42
e5c3720e14a5ea7f678e0a9835d28283
229e3933010d9c32dff880658dc4119e
3997fb6cd3b603aad1cd40360be6c205
a0d22042fe2c365d7b07a04b2b1e1da0
0f649adcf96f6cac038ec7999d5aeffe
58d23f22bae9043697d8550ea0bc9b66
ed27862f885c906e30227d203b0084e2
0abd9797cd648a1d489fef86f0370387
afba98469d91f7fda00027870bfad553
16d4b49cd81775097ea2e997a90a2f4e[1] Note on Non-stopping Self-questioning Study (Part Two) - An Interesting Journey of Exploration
[2] Best Practice of Handling Sysrv-hello, A New Mining Virus (article in Chinese)
[3] Analysis of Malicious Samples in the Controlled End of a Botnet
[4] Router Vulnerabilities Appear Frequently, and New Variant of Mirai Is Coming
[Infographic] 5 Steps to Accelerate Your Digitalization in Asia

2,597 posts | 773 followers
FollowAlibaba Cloud Security - November 6, 2019
Alibaba Cloud Security - February 17, 2020
Alibaba Cloud Security - January 13, 2019
Alibaba Clouder - July 27, 2018
Alibaba Cloud Security - February 26, 2019
Alibaba Cloud Security - March 20, 2019

2,597 posts | 773 followers
Follow Web Hosting Solution
Web Hosting Solution
Explore Web Hosting solutions that can power your personal website or empower your online business.
Learn More WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Security Overview
Security Overview
Simple, secure, and intelligent services.
Learn MoreMore Posts by Alibaba Clouder
Start building with 50+ products and up to 12 months usage for Elastic Compute Service
Get Started for Free Get Started for Free