By Wu Fan (Wufan) and Guo Weibo (Sangduo)
Special thanks to: Huangxing, Cangbo, Muming, Xijun, Ziyi, Xuzheng, Nanxun, Suddy (In no particular order)
With the continuous development of the Internet industry in recent years, hackers, cyberattacks, and scams are becoming increasingly troublesome and dangerous. In this "smokeless battlefield" of the Internet, defense against attacks never ends.
As most government institutions and enterprises are migrating to the cloud, cybercriminals are shifting their focus onto massive information and computing resources on the Cloud. In response, protection enabled by Cloud defends big data with more rigid "armor," compared to that in on-premises data centers. On average, Alibaba Cloud Security intercepts 5 billion Cloud attacks every day and works hard to establish and maintain a secure Internet environment.
When it comes to protecting against cyberattacks, one must consider multiple questions such as: What is the source of such attacks? What is their means of hacking? What are their targets? How stronger are the "weapons" of cybercriminals?
The following sections address Internet attacks with reference to their source, means, and targets to help readers, especially those engaged in Internet security, better understand and prepare to counter the trends in Internet hacking technologies.
As the most frequently used Internet identity, IP addresses are the foundation of many security and risk control measures, including throttling and attack interception based on IP behaviors. IP addresses are also the core resources for hackers and cybercriminals.
Previously, most attacks came from IP addresses provided by carriers, such as IP addresses from asymmetric digital subscriber line (ADSL) household networks. As more vendors start to extend their business scope to Cloud and IDC, their computing and IP resources also become the sources of many hackers.
Although carrier-provided IP addresses are still the sources of most attacks, it is observed that attacks from proxy IP addresses and Cloud/IDC provider's IP addresses are on the rise. The following graph shows the percentages of different provider types of IP addresses from where attacks are staged.
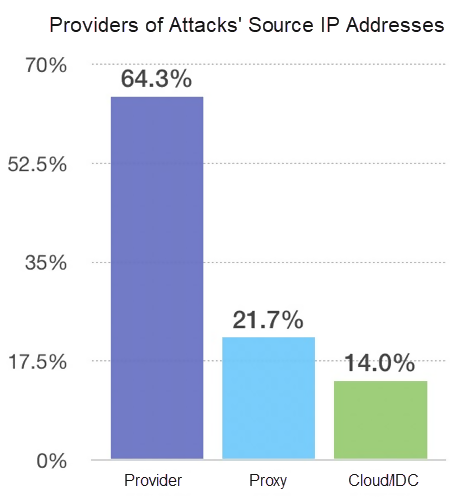
Currently, 64.3% of attacks are from carrier-provided IP addresses, 21.7% from proxy IP addresses, and 14% (this number is likely to continuously rise) from Cloud/IDC providers.
This indicates that part of the resources of some Cloud/IDC providers are likely under the control of hackers/cybercriminals and have become their tools for staging cyberattacks. The following graph shows the percentages of specific Cloud and IDC providers of IP addresses from where attacks are staged.
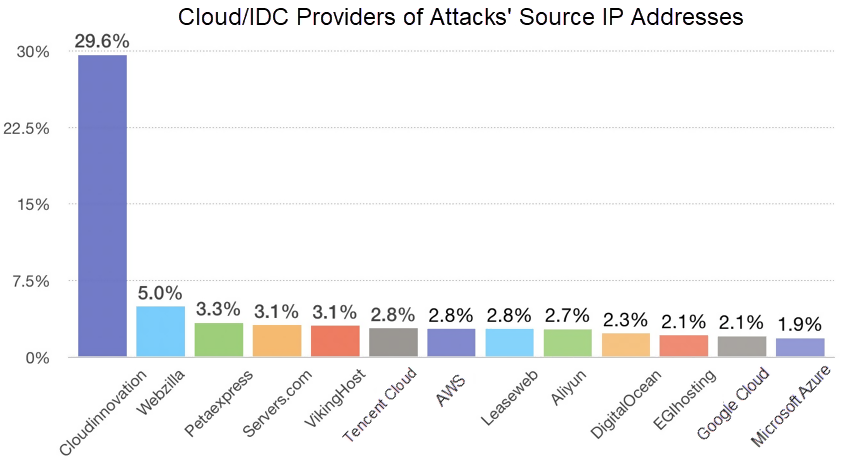
A South African VPS vendor named, CloudInnovation, is the largest source of attacking IP addresses. It accounts for 29.6% of such IP addresses, nearly six times that of the attacking IP addresses from the second-ranked source, the Singapore vendor named, Webzilla. Users' lack of security awareness and the gradual transition of Cloud platforms into mainstream platforms drive the use of resources of Cloud and VPS providers by hackers to stage attacks.
Defenders need to consider the new developments and particularly control traffic from specific providers. For example, block traffic from a specific vendor to prevent cyberattacks.
For years, hackers mainly used open proxy servers to obtain IP resources that are limited in quantity and unreliable. In recent years, dynamic dial-up IP addresses enabled cybercriminals to access large numbers of IP addresses to fight against IP-based security and risk control measures. Household broadband connections get new IP addresses after resuming from a disconnection. By taking this advantage, dial-up IP providers gather massive IP resources and package them into dynamic dial-up IP addresses that are sold to cybercriminals.
The following two pie charts show the percentage of dynamic dial-up IP addresses to all proxy IP addresses and the percentage of dynamic dial-up IP providers. Currently, about 72% of dynamic dial-up IP addresses are from China Telecom, 28% from China Unicom, and less than 1% from the bottom-ranked China Mobile. This is possible because China Mobile frequently uses NAT for IP translation, and it has a less stable network than China Telecom and China Unicom.
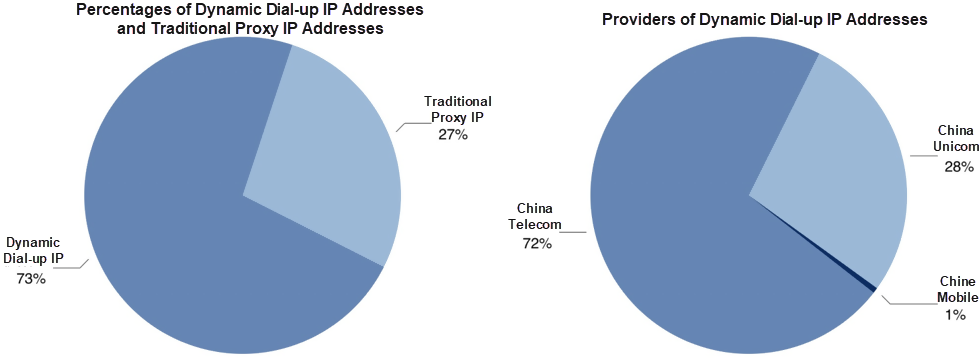
Dynamic dial-up IP addresses pose serious challenges to IP-based security and risk control measures. There are so many dynamic dial-up IP addresses that a local broadband IP pool contains hundreds of thousands or millions of IP addresses. Additionally, dynamic dial-up IPs switch to another in seconds, and the same IP pool is shared with normal users who then quickly be changed to fraudsters, making detection difficult.
The ability to detect dynamic dial-up IP addresses is crucial in fighting fraud. Defenders of Internet security need to introduce or build a mechanism to detect and fight frequently changing attack source IP addresses, to lay the foundation for different security and risk control solutions.
In 2019, new vulnerabilities of different programs, from the OS default services to Web middleware, constantly tested the nerves of online users. Some vulnerabilities result in the running of remote commands or allow hackers to directly exploit host resources of the victims, inflicting heavy mental and financial damage.
Hackers target such vulnerabilities. In 2019, there's been a shorter interval between the exposure of harmful vulnerabilities to their large-scale use on the Internet compared to 2018.
2019
| Name/code of vulnerability | Exposure (in 2019) | Start of large-scale exploitation (in 2019) | Interval |
|---|---|---|---|
| Confluence vulnerability of remote command execution(CVE-2019-3396) | 8-Apr | 10-Apr | 2 days |
| Exim email server vulnerability of remote command execution(CVE-2019-10149) | End of May | Mid July | About 50 days |
| JIRA server template injection vulnerability(CVE-2019-11581) | Early July | Mid July | About 10 days |
| Solr remote command execution vulnerability(CVE-2019-0193) | 1-Aug | 16-Aug | 15 days |
| PhpStudy backdoor vulnerability of remote command execution | 20-Sep | 24-Sep | 4 days |
2018
| Name/code of vulnerability | Exposure | Start of large-scale exploitation | Interval |
|---|---|---|---|
| JBoss deserialization vulnerability(CVE-2017-7504, CVE-2017-12149) | May-17 | Mar-18 | About 10 months |
| Drupal remote command execution vulnerability(CVE-2018-7600) | End of March 2018 | End of April 2018 | About 1 Month |
| ThinkPHP 5.x vulnerability of remote command execution | 9-Dec-18 | Early January 2019 | About 1 Month |
Hackers take much less time in 2019 than in 2018 from the exposure of vulnerabilities to their massive exploitation. The interval of one month to 10 months has been reduced to 10 to 15 days. In extreme cases, two vulnerabilities were widely exploited online 2 days and 4 days after their exposure.
This means that defenders have less time to fix vulnerabilities. They need to get the latest updates on new vulnerabilities and take preventive measures or fix them promptly. If necessary, security products are a good choice to guard against cyberattacks.
As most virtual currency prices are below their all-time highs as compared to those at the end of 2017, worms are not making as much news as they did in the last couple of years. However, some worms are still quietly growing and have developed new techniques. In addition to well-studied worms, such as Ddgs, some new worms have emerged. The following graph ranks active worms in 2019.
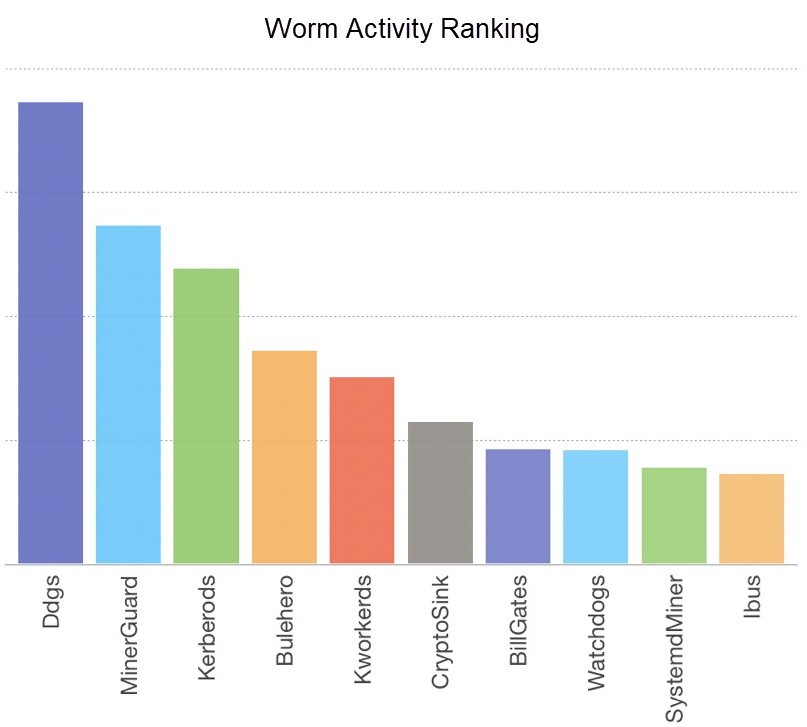
Worms like Ddgs and Kerberods appeared before 2019 and have been rampant on the Internet ever since. For more details, refer to our earlier article titled, Return of Watchbog: Exploiting Jenkins CVE-2018-1000861 and Solr Dataimport Vulnerability Becomes a New Attack Method for Mining Organizations*.
New worms, such as MinerGuard, CryptoSink, and SystemdMiner, are especially noteworthy, particularly because of their new means to invade, spread, and become persistent.
There are many cross-platform spreading methods, such as the use of cross-platform languages to compile malware. For example, MinerGuard writes worms with the Go language. Some hacker groups, such as CryptoSink, choose to compile different malware for Linux and Windows.
Most worms are spread on Linux or Windows. For example, Ddgs only attacks Linux hosts, but Bulehero only targets Windows hosts. Many worms, such as MinerGuard, Kworkerds, and CryptoSink, have been able to spread on both Linux and Windows, further threatening more potential victims.
Unlike other means aimed at hosts, Sinkhole is mainly used by a worm program to fight other worms on the same host. They simply modify the /etc/hosts file to point the server addresses of "rival worms" to 127.0.0.1 or 0.0.0.0. This way, the requests of other worms to pull files from the server or send online information is directed to the localhost and denied consequently.
Before the rise and widespread use of this technology, worms mainly "wiped out" rivals by killing processes that contain specific keywords. However, the scheduled execution mechanism of many worms keeps restarting processes, which implies that killing processes containing specific keywords was not enough. The recently emergent Sinkhole solution suppresses rivals.
In addition to suppressing rivals, some worms try to invade existing botnets and use them as the base for their further transmission. In April 2019, the notorious botnet, C&C of Ddgs, experienced a plummet of activity. Metrics show that this was the result of the invasion of another worm, SystemdMiner, into the Ddgs infrastructures and the addition of its own malicious code to the end of the major scripts of the botnet.
Due to the large number of nodes of Ddgs, despite the Ddgs controller resuming control days later, SystemdMiner still rampantly increased the number of hosts under its control and has been active ever since.
Also known as the Website backdoor, Web shell files are in .php or .jsp formats. After invading a Website, a hacker usually uploads the Web shell to the Web directory of the Website server and gets the environment to run commands by accessing Web shell files. This way, hackers control the Website server. A web shell is used by fraudsters for invasion and widely used in Internet hacking and defense tests.
A traditional Web shell connection tool, China Chopper, uses the Base64 code by default, which can be easily recognized and intercepted. The subsequent Ant Sword and Ice Scorpion tools took a stride forward in Web shell connections and communications. Ant Sword provides different encoding modes, including CHR 16 and ROT13, and uses random hexadecimal bytes rather than the default "z0" and "z1" as parameters. Ice Scorpion applies AES encryption to bi-directional communications, so traffic does not flow in a fixed pattern.
Surveys show that 9% of the connections and communications of Web shell management tools use Ant Sword and Ice Scorpion.
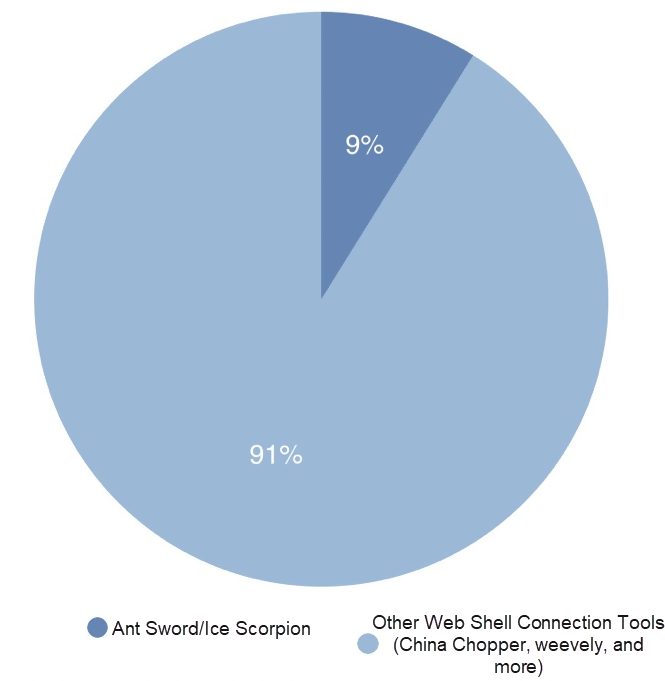
This is currently a low percentage but is likely to surge with the technological advances in attack and defense. Therefore, defenders must set up the detection of encrypted web shell connections against Ant Sword and Ice Scorpion quickly, to avoid being unknowingly invaded.
Records show that average attacks from June to August were much more frequent than earlier in the year and during the same period in 2018. It was an eventful summer. The following graph shows the trend of the average number of attacks on each IP address from January to September in 2018 and 2019.
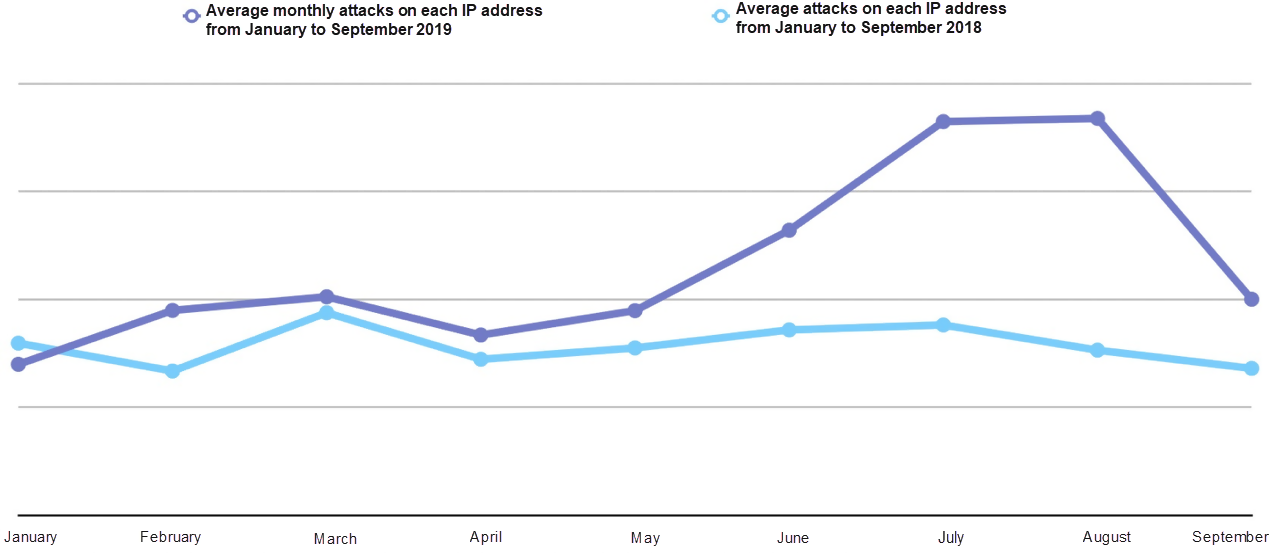
Records show that attacks on management ports, such as SSH and RDP, and database services, such as MySQL and Redis, increased in 2019. The following graph shows the percentage of attacks on different types of services.
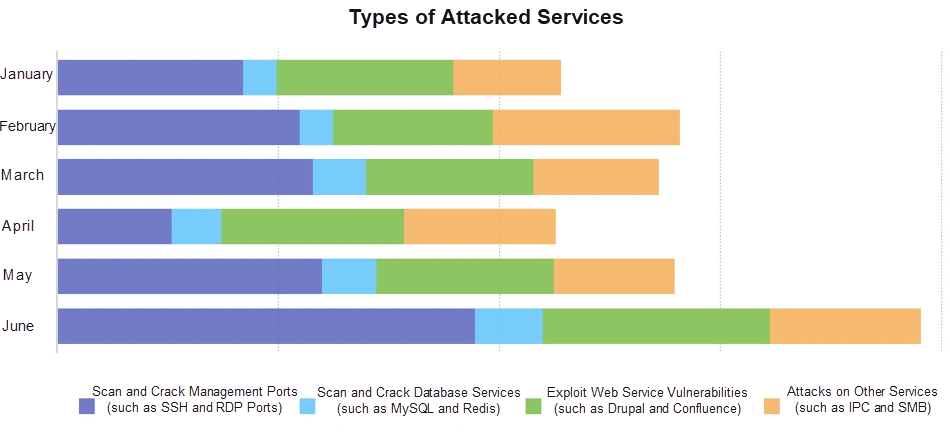
Management ports, database services, as well as Web and other services, like IPC and SMB, tend to be at high risk and need proper management. For example, internal services are advised to be open to specific devices only and deny access requests from the Internet. The following graph shows the trend of attacks targeting database services and management ports.
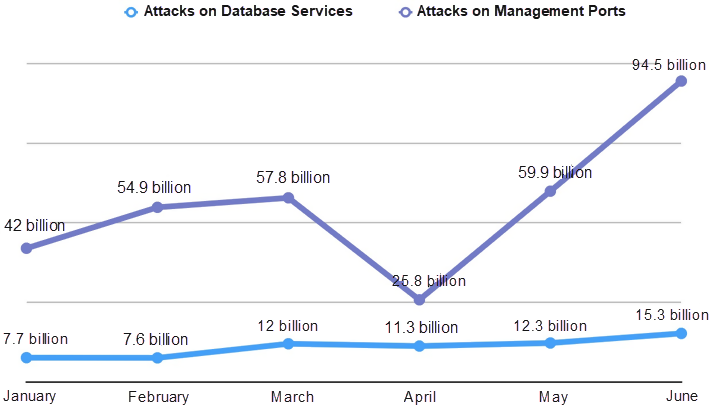
The number of attacks on SSH and RDP ports accounts for a high percentage of all attacks and fluctuates in an overall rising trend. This indicates that weak passwords and loose ACL management are still commonplace and must be addressed.
Attacks on database services are a small portion of total attacks, but steadily increasing. Hackers obtain permission to operate the entire operating system after they invade the database, so these attacks are worthy of equal attention.
There's saying in the cyber world that Linux is superior to Windows, in terms of Internet security. Is this true?
More than 75% of applications run on Linux, and the percentage of attacks on Linux systems is slightly lower than 75%. Mathematically, the Linux system is indeed "more secure" than Windows because Windows systems are more "attractive" to hackers.
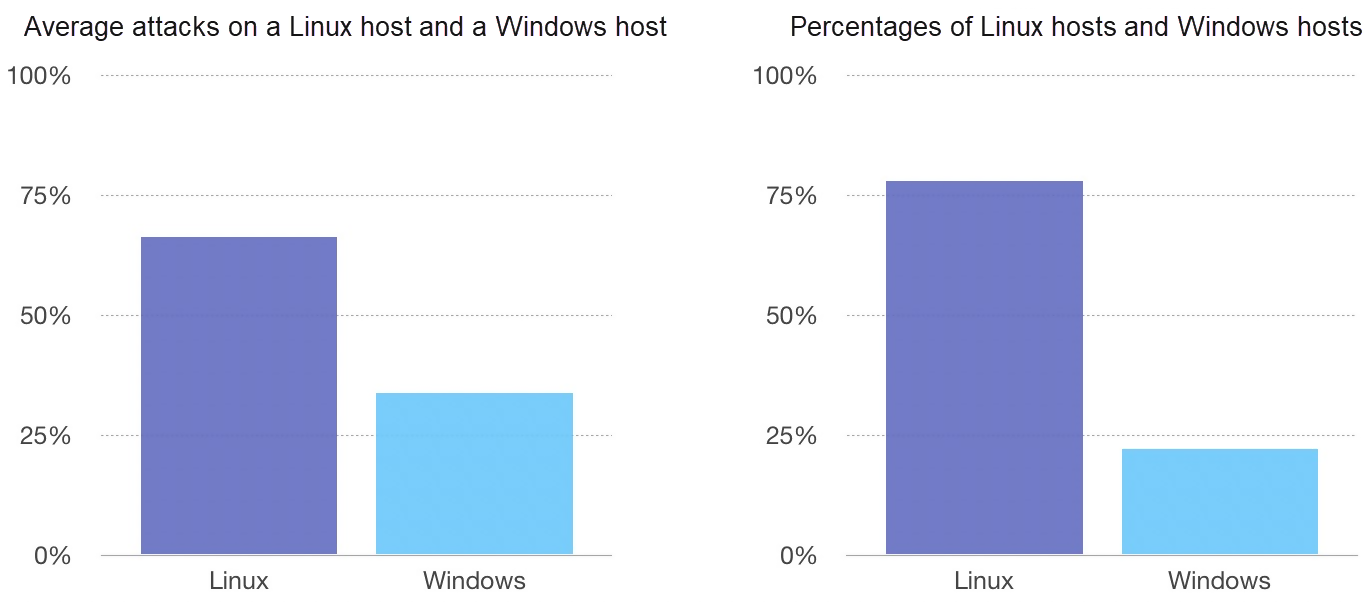
However, both Linux and Windows are prone to massive attacks from the Internet. Cyberattacks are not limited to operating systems but cover database services and Web applications. Hackers may exploit vulnerabilities in any aspect. We need to remain cautious, regardless of which system we are using.
Following are some key suggestions to help user defend against cybercrimes:

32 posts | 15 followers
Followchuan - February 27, 2020
Alibaba Cloud Security - December 5, 2019
Alibaba Cloud Community - January 6, 2022
Balaban - March 17, 2021
Alibaba Clouder - December 14, 2017
Alibaba Cloud Community - December 7, 2021

32 posts | 15 followers
Follow Anti DDoS Basic
Anti DDoS Basic
A cloud-based security service that protects your data and application from DDoS attacks
Learn More WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn More Anti-DDoS
Anti-DDoS
A comprehensive DDoS protection for enterprise to intelligently defend sophisticated DDoS attacks, reduce business loss risks, and mitigate potential security threats.
Learn More Web Hosting Solution
Web Hosting Solution
Explore Web Hosting solutions that can power your personal website or empower your online business.
Learn MoreMore Posts by Alibaba Cloud Security