Cloud Firewall can quickly perceive the latest attack threats and link network-wide threat intelligence to provide you with optimal security protection and eliminate threats of cryptocurrency mining worms using its massive in-cloud computing power.
Cryptocurrency mining worms distribution on a large scale because of the persistence of common application vulnerabilities on the Internet, frequent 0-day vulnerabilities, and the highly efficient monetization of mining activities. Off-premises users can transparently access Cloud Firewall to protect their applications against various malicious attacks on the Internet. In addition, Cloud Firewall can be scaled as your business grows, so that you can pay more attention to business expansion without the need to devote a great deal of time to security.
The Security Team at Alibaba Cloud has discovered recent cloud-native cryptocurrency mining trojans distributed by common popular 0-day and n-day vulnerabilities.
In the past year, cryptocurrency mining worms have exploited common vulnerabilities (such as configuration errors and weak passwords) in network applications to continuously scan the Internet, launch attacks, and compromise hosts. The following table lists common vulnerabilities that have been recently exploited by active cryptocurrency mining worms:\
| Common vulnerabilities | Mining worm family |
|---|---|
| SSH, RDP, and Telnet cracking | MyKings and RDPMiner |
| Writing data to Crontab in Redis to run commands | DDG, Watchdogs, Kworkerd, and 8220 |
| Using UDF to run commands in MySQL and SQL Server | Bulehero, MyKings, and ProtonMiner |
| Using CouchDB to run commands | 8220 |
Cryptocurrency mining worms also exploit 0-day and N-day vulnerabilities to compromise a large number of hosts before these vulnerabilities are fixed. The following table lists popular 0-day and N-day vulnerabilities that have been recently exploited by active cryptocurrency mining worms:
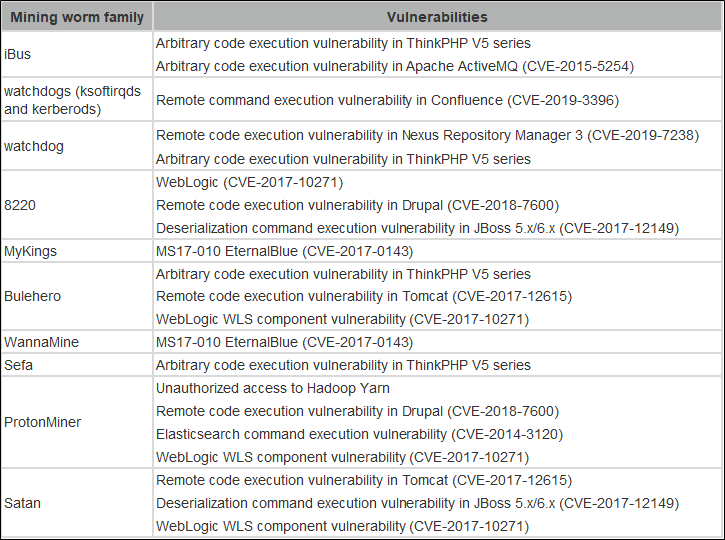
According to the 2018 In-cloud Mining Analysis Report released by the Alibaba Cloud security team, each round of popular 0-day attacks was accompanied by the outbreak of cryptocurrency mining worms. Cryptocurrency mining worms may interrupt businesses by occupying system resources. Some of them even carry ransomware (such as XBash), resulting in financial and data losses to enterprises.
For many enterprises, improving the level of security and protecting against the threat of cryptocurrency mining worms have become a top priority. This article uses an off-premises environment as an example to explain Alibaba Cloud's Cloud Firewall effectively defends against cryptocurrency mining worms through early prevention, Trojan worm detection, and quick damage control.
Web applications are vulnerable to all types of attacks and bear the brunt of injection and cross-origin attacks. Web Application Firewalls (WAFs) are designed to prevent and block attacks targeted at web applications and are continuously updated to protect them from security threats. A range of machine learning algorithms and models are continuously proposed and applied to security products such as WAF to eliminate security threats. However, most of these algorithms focus on supervised learning. They are used to build a classification model for specific attack types by tagging positive and negative sample data.
Similar to traditional security detection technologies, machine learning algorithms alone fail to eliminate the discrepancy between false negatives and false positives or strike a balance between coverage and detection performance. The security field still faces the challenges of open-loop problem spaces and asymmetric positive and negative spaces.
Alibaba Cloud WAF was recognized by Gartner, being placed as a "Niche Player" in the Gartner 2019 Magic Quadrant for Web Application Firewalls (WAF)
This article describes how the AI kernel of the intelligent defense system of Alibaba Cloud WAF resolves such challenges. The AI kernel of Alibaba Cloud WAF provides core machine intelligence capabilities, along with refined, personalized, and intelligent protection to minimize security threats for customers. AI-driven intelligent security systems are on the rise and bring greater benefits.
The VM-Series next-generation firewall allows developers and cloud security architects to embed inline threat and data loss prevention into their application development workflows. Third party templates combined with VM-Series automation features allows you to create "touchless" deployments that eliminate "change control friction", enabling developers to operate at the speed of the cloud. Automation features such as the API, Dynamic Address Groups and External Dynamic Lists allow you to utilize external data to drive application whitelisting and segmentation policy updates while preventing threats. Note that bootstrapping is not supported in this release.
Palo Alto Networks VM-Series firewall can be deployed on Alibaba Cloud servers easily, as described in this blog.
Web Application Firewall (WAF) protects your website servers against intrusions. Our service detects and blocks malicious traffic directed to your websites and applications. WAF secures your core business data and prevents server malfunctions caused by malicious activities and attacks.
Alibaba Cloud Firewall centrally manages the policies that control the traffic from the Internet to your businesses. It also controls the traffic between VPC networks, the traffic on Express Connect instances, and the traffic generated by VPN-based remote access. Cloud Firewall is embedded with an Intrusion Prevention System (IPS) and can detect outbound connections from your assets. Alibaba Cloud Firewall can also visualize network traffic and access between businesses as well as can store network traffic logs generated within the last six months.
Web Application Firewall (WAF) is a security service that protects your website and app services. WAF identifies malicious web business traffic, scrubs and filters the business traffic, and then forwards normal traffic to your server. This prevents your web server from being intruded and ensures data and business security.
Features
Use of WAF
After you purchase a WAF instance, add the domain name of your website to WAF. Then, resolve the domain name to the CNAME provided by WAF and configure the IP address of your origin server to enable WAF protection. After you enable WAF protection, all Internet traffic to your website is redirected to WAF. WAF then detects and filters malicious traffic and forwards normal traffic to the IP address of your origin server. This ensures security, stability, and availability of your origin server.
Cloud Enterprise Network (CEN): Enterprise's Multi-region Network Solution

2,593 posts | 793 followers
FollowAlibaba Clouder - July 10, 2019
Alibaba Cloud Security - December 12, 2019
Alibaba Cloud Security - May 15, 2019
Alibaba Clouder - January 28, 2021
Kalpesh Parmar - November 22, 2025
Alibaba Clouder - December 25, 2020

2,593 posts | 793 followers
Follow WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn More Cloud Firewall
Cloud Firewall
Provides traffic control and security protection for the Internet, virtual private cloud (VPCs), and hosts in VPCs
Learn MoreMore Posts by Alibaba Clouder