By Shantanu Kaushik
Cloud-native architecture is an open-architecture that supports continuous evolution. Continuous evolution is highly mandatory for any solution to sustain in today’s world. The state of businesses evolves with demands and changing trends. Different layers or adjustment levels are needed for an architecture to be ready for continuous evolution, but cloud-native architecture is so agile that it is already prompt for evolutionary cycles.
Architectures should be capable enough to provide software-level considerations (like incremental iterations) and organizational-level considerations (like risk control.) The deployment should be managed with a balance between iterations and business value. The prime mover that can establish this practice efficiently is the architecture you choose.
The cloud-native architecture allows you to deploy using various architecture control policies that meticulously manage elasticity, agility, and cost corrections. While migrating the monolithic applications based on traditional architecture to the cloud-native architecture, you need to ensure the organization is ready for added policy management and costs depending on the iterations and migration scenario required to leverage the business value from the application.
Cloud-native allows you to manage your application seamlessly by implementing different scenarios based on microservices, smart application gateway, sandboxing, and other techniques to control the workflows.
The zero-trust security architecture is becoming mainstream. This new security model tells the system not to automatically trust anything, whether it comes from inside or outside the system. Everything must be verified before granting access to any system.
The zero-trust security architecture provides a fresh perspective by re-evaluating the traditional approach related to security practices. Users need identity authorization and credential authentication to gain access to any system with the zero-trust security approach. The zero-trust system rules out any previously validated IP-addresses or geographical locations and depends solely on identity for access.
Since identity is the basis of zero-trust security architecture, enterprises have to enable identity assignment based on the environment and resources allocated to different systems. For example, when we talk about zero-trust security within a development environment or O&M, we are talking about identity-centric policy management that will be the basis of the entire security structure. The entire architecture will depend on the isolation of environments, services, and resources based on identity and access control.
The event-driven architecture (EDA) works with the principle-based transmitted events between loosely coupled applications and components. EDA is highly efficient in maintaining the quality of service (QoS) since it immediately restores functionality after event failures. An event contains schema that can be verified to make it a close-ended system.
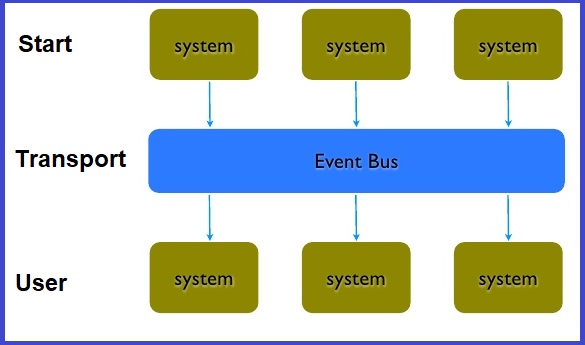
The event-driven architecture (EDA) is used to form microservices by decoupling traditional services. Some of the scenarios that EDA can be used with are listed below:
1. API
The event-driven architecture supports API operations. The event providers do not need to know who the event subscribers are and where the data consumers are.
2. Event-Triggered Responses
Event-driven hardware-based technologies like the Internet of Things (IoT) and Internet of Everything (IoE) are compatible with the event-driven architecture. These services utilize events driven by sensors to generate large amounts of data, and EDA helps channel everything in the mix.
3. Flow Processing
The event-driven architecture works wonders with scenarios that involve the analysis of a large number of event flows, such as Kafka-based processing.
4. Service Availability Enhancement
The event-driven architecture (EDA) works with asynchronous service integration. You can utilize EDA to work with upstream services during service outages or failures.
5. Data Modification Chain Execution
With EDA, any modified data activates an event that starts or sends a notification to another service to execute a certain command, which makes chain execution or batch execution-based systems a perfect fit for EDA.
Unlike the traditional architectural models, the microservices-based cloud-native architecture enables the use of private data sources instead of common sources. However, a distributed structure with multi-threaded microservices for an application will involve data from different sources for multiple microservices. Distributed Transaction Architecture is applied to maintain data consistency. Let’s take a look at some of the models that can be used to implement the Distributed Transaction architecture:
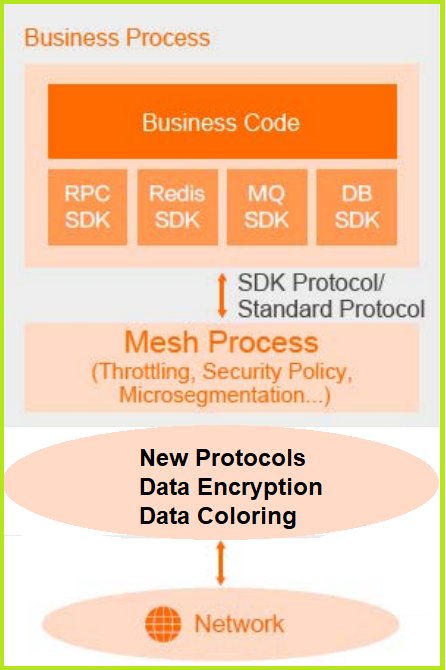
The Service Mesh architecture uses the Mesh processes to execute different tasks without using SDKs with the business codebase. Mesh separates the middleware framework from the business process with a distributed architecture. With this kind of business code, decoupling, upgradation, or cross-platform middleware migration does not affect the business processes. All of the features that were previously handled by the SDK, including security, are not dealt by the Service Mesh architecture.
Stateless applications do not require any consistency to maintain availability. However, with a distributed architecture and stateful applications, a perfect form of consistency is necessary to ensure resource availability. Separating the data storage usage and computing for a solution based on the cloud-native architecture is highly recommended to ensure high-availability.
Cloud-native architecture is a way to develop and deploy applications that ensure proper resource utilization and the most efficient continuous integration and delivery cycles. Evolving tools (like Kubernetes) and environments (like hybrid cloud and multi-cloud) are beginning to give a unique and synchronized lifecycle to next-generation applications. Enterprises are directly benefitting from multiple architectures that suit different trades and streams where enterprises want to develop and deploy applications.
Cloud-Native and Application Management With Ease – Part 5: Containers

2,593 posts | 793 followers
FollowAlibaba Clouder - February 24, 2021
Alibaba Clouder - February 25, 2021
Alibaba Clouder - February 25, 2021
Alibaba Clouder - March 1, 2021
Alibaba Clouder - February 26, 2021
Alibaba Clouder - March 1, 2021

2,593 posts | 793 followers
Follow RAM(Resource Access Management)
RAM(Resource Access Management)
Secure your cloud resources with Resource Access Management to define fine-grained access permissions for users and groups
Learn More Resource Management
Resource Management
Organize and manage your resources in a hierarchical manner by using resource directories, folders, accounts, and resource groups.
Learn More IDaaS
IDaaS
Make identity management a painless experience and eliminate Identity Silos
Learn More Microservices Engine (MSE)
Microservices Engine (MSE)
MSE provides a fully managed registration and configuration center, and gateway and microservices governance capabilities.
Learn MoreMore Posts by Alibaba Clouder