By Yuanyuan Ma (Fazi)
The Gateway API is a Kubernetes project aimed at routing Layer 4 and Layer 7 traffic. Initiated by the official Kubernetes community, its goal is to become the next-generation API for Kubernetes Ingress, load balancing, and service meshes. This article introduces how to efficiently manage cluster traffic using the Gateway API in Alibaba Cloud Service Mesh (ASM).
The main function of the Gateway API is evident from its name: to define gateways and their routing rules. The Gateway API is a collection of multiple APIs, including Gateway, GatewayClass, and HTTPRoute.
• GatewayClass, similar to IngressClass, specifies the controller for the Gateway API.
• Gateway defines the specific gateway configuration.
• HTTPRoute attaches to a Gateway and sets the routing rules for incoming traffic.
There are other APIs within the Gateway API, but they are not listed here.
ASM now supports using the Gateway API to manage traffic in ACK clusters. With the Gateway API, you can configure gateway traffic rules and manage east-west traffic within the cluster in Ambient mode. This article demonstrates how to use the Gateway API to configure north-south traffic rules and set up authorization policies for a specified service. The example consists of three parts:
🔔 About Waypoint
Waypoint is a concept in the Ambient mode of ASM. Think of it as an east-west gateway for a specific service. When you configure a Waypoint for a service, all traffic to that service first goes through the Waypoint before being forwarded to the backend service. Waypoint is enabled by configuring the Gateway API.
Here is the basic architecture diagram for this example:
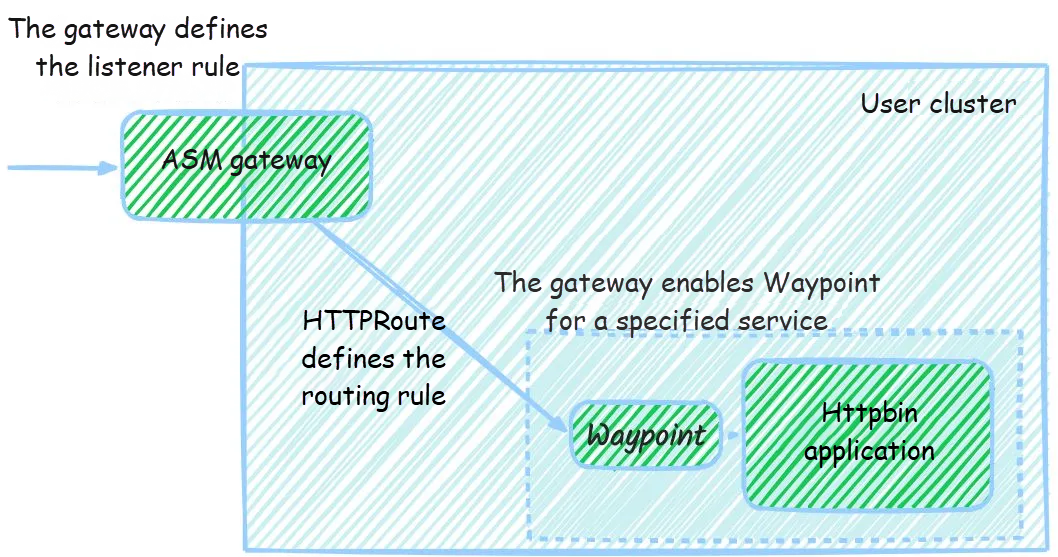
By the end of this article, you will have a basic understanding of using the Gateway API to manage cluster services and a deeper insight into the Ambient mode of ASM.
The Gateway API was first introduced at KubeCon in 2019. At that time, the Ingress API was difficult to extend and could not handle the more precise and strict traffic management requirements of cloud-native environments. This led to the creation of various other API standards. The community aimed to use the Gateway API to unify user interfaces and provide a standardized user experience. After the stable Ingress API v1 was released, the community shifted its focus to the Gateway API project. In October 2023, the Gateway API project officially reached general availability (GA).

Image source: https://gateway-api.sigs.k8s.io/images/logo/logo-text-horizontal.png
🔔 Note: The Gateway API logo has multiple arrows, signifying the community's goal for the Gateway API, in place of Ingress, to manage not only north-south traffic, but also east-west traffic within the cluster. This is similar to the approach of ASM, especially in Ambient mode.
The Istio community has participated in designing and adapting the Gateway API since its early development, with significant contribution. After the Ambient mode was introduced, they further increased their support for the Gateway API.
ASM is a managed service mesh product by Alibaba Cloud, compatible with the open-source Istio service mesh. In ASM 1.18, the Ambient mode beta testing is available, and Gateway API support is enhanced. This article demonstrates how to manage mesh traffic using the Gateway API in ASM Gateway and Ambient mode.
apiVersion: gateway.networking.k8s.io/v1beta1
kind: Gateway
metadata:
name: gateway
namespace: istio-system
spec:
addresses:
- type: Hostname
value: istio-ingressgateway.istio-system.svc.cluster.local
gatewayClassName: istio
listeners:
- allowedRoutes:
namespaces:
from: All
hostname: '*.aliyun.com'
name: default
port: 80
protocol: HTTPThis configuration sets up an HTTP listener on port 80 for the domain *.aliyun.com.
Use the kubeconfig file of the ACK cluster to create the following HTTPRoute resource:
apiVersion: gateway.networking.k8s.io/v1beta1
kind: HTTPRoute
metadata:
name: http
namespace: default
spec:
hostnames:
- '*.aliyun.com'
parentRefs:
- group: gateway.networking.k8s.io
kind: Gateway
name: gateway
namespace: istio-system
rules:
- backendRefs:
- group: ""
kind: Service
name: httpbin
port: 8000
weight: 1
matches:
- path:
type: PathPrefix
value: /This configuration specifies that the route takes effect only on the *.aliyun.com host. The parentRefs field indicates that the HTTPRoute is attached to the gateway resource configured in the previous step. The routing rule specifies that requests with the path prefix / are routed to the httpbin service on port 8000.
After the configuration is complete, you can access the Httpbin service via the ASM gateway. Run the following command to verify the configuration:
curl -HHost:httpbin.aliyun.com "http://${ASM gateway IP address}:80/status/418"
-=[ teapot ]=-
_...._
.' _ _ `.
| ."` ^ `". _,
\_;`"---"`|//
| ;/
\_ _/
`"""`For more information about how to obtain the IP address of the ingress gateway of the ASM instance, see Step 3 in Use Istio resources to route traffic to different versions of a service.
After you enable Waypoint for the Httpbin service by using the Gateway API, you can configure Layer 7 authorization policies for the Httpbin service.
Use the kubeconfig file of the ACK cluster to create the following gateway resource:
apiVersion: gateway.networking.k8s.io/v1beta1
kind: Gateway
metadata:
annotations:
istio.io/for-service-account: httpbin
name: httpbin
namespace: default
spec:
gatewayClassName: istio-waypoint
listeners:
- allowedRoutes:
namespaces:
from: Same
name: mesh
port: 15008
protocol: HBONEThis gateway resource indicates that Waypoint is enabled for the Httpbin service. HBONE is a special protocol in Service Mesh that uses mTLS to encrypt traffic.
After you enable Waypoint, you can configure some Layer 7 authorization policies for the Httpbin service.
Here, we configure an authorization policy to prohibit users from accessing the /status/418 path of the Httpbin application. Access to other paths will not be affected.
Use the kubeconfig file of the ACK cluster to create the following AuthorizationPolicy resource:
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: authz-test
namespace: default
spec:
targetRef:
name: httpbin
kind: Gateway
group: "gateway.networking.k8s.io"
action: DENY
rules:
- to:
- operation:
paths:
- "/status/418"This policy attaches to the gateway resource httpbin, and denies access to the /status/418 path. Let's test the access to this path:
curl -HHost:httpbin.aliyun.com "http://${ASM gateway IP address}:80/status/418"
RBAC: access denied%Access to other paths is not affected:
curl -HHost:httpbin.aliyun.com "http://${ASM gateway IP address}:80/headers" -I
HTTP/1.1 200 OK
server: istio-envoy
date: Fri, 31 May 2024 09:24:56 GMT
content-type: application/json
content-length: 981
access-control-allow-origin: *
access-control-allow-credentials: true
x-envoy-upstream-service-time: 2This is the end of the example. I believe you have a better understanding of using the Gateway API in ASM.
This article provides a brief introduction to the Gateway API and its development within service meshes. It also includes a simple example that demonstrates how to leverage the Gateway API to manage north-south traffic and east-west traffic in Ambient mode within ASM.
The service mesh community plans to promote the Gateway API as the primary traffic management tool and will provide ongoing support. Due to its strong alignment with the Ambient mode, the Gateway API is expected to perform exceptionally well as the Ambient mode continues to evolve. ASM will maintain compatibility with Istio resources in future versions, improve support for the Gateway API, and offer users a more standardized experience.
Container Memory Observability: Exploring WorkingSet and PageCache Monitoring
Fluid and Vineyard Team Up for Efficient Intermediate Data Management in Kubernetes

228 posts | 33 followers
FollowAlibaba Cloud Indonesia - April 10, 2023
Alibaba Container Service - September 18, 2025
Alibaba Container Service - May 23, 2025
Alibaba Cloud Native Community - December 18, 2023
Alibaba Container Service - October 12, 2024
feuyeux - December 30, 2020

228 posts | 33 followers
Follow Container Service for Kubernetes
Container Service for Kubernetes
Alibaba Cloud Container Service for Kubernetes is a fully managed cloud container management service that supports native Kubernetes and integrates with other Alibaba Cloud products.
Learn More ACK One
ACK One
Provides a control plane to allow users to manage Kubernetes clusters that run based on different infrastructure resources
Learn More Cloud-Native Applications Management Solution
Cloud-Native Applications Management Solution
Accelerate and secure the development, deployment, and management of containerized applications cost-effectively.
Learn More Container Registry
Container Registry
A secure image hosting platform providing containerized image lifecycle management
Learn MoreMore Posts by Alibaba Container Service