- Featured Products
-
 Elastic Compute Service (ECS)
Elastic Compute Service (ECS)
High-performing virtual servers
-
Simple Application Server (SAS)
-
Elastic GPU Service
-
Elastic Desktop Service (EDS)
-
Object Storage Service (OSS)
-
Cloud Enterprise Network (CEN)
-
Web Application Firewall (WAF)
-
Domain Names
- New Products
-
 Container Compute Service (ACS)
Container Compute Service (ACS)
A cloud computing service that provides container compute resources that comply with the container specifications of Kubernetes
-
Secure Access Service Edge (SASE)
-
Intelligent Media Services(IMS)
-
Edge Security Acceleration (ESA)(Original DCDN)
-
Intelligent Media Management
-
DingTalk Enterprise
-
YiDA
-
Alibaba Cloud Model Studio




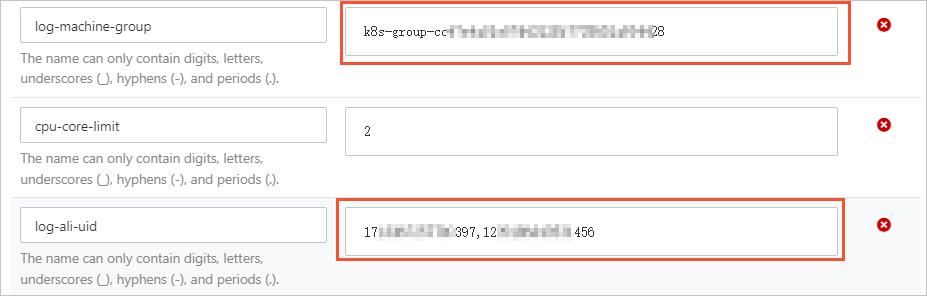
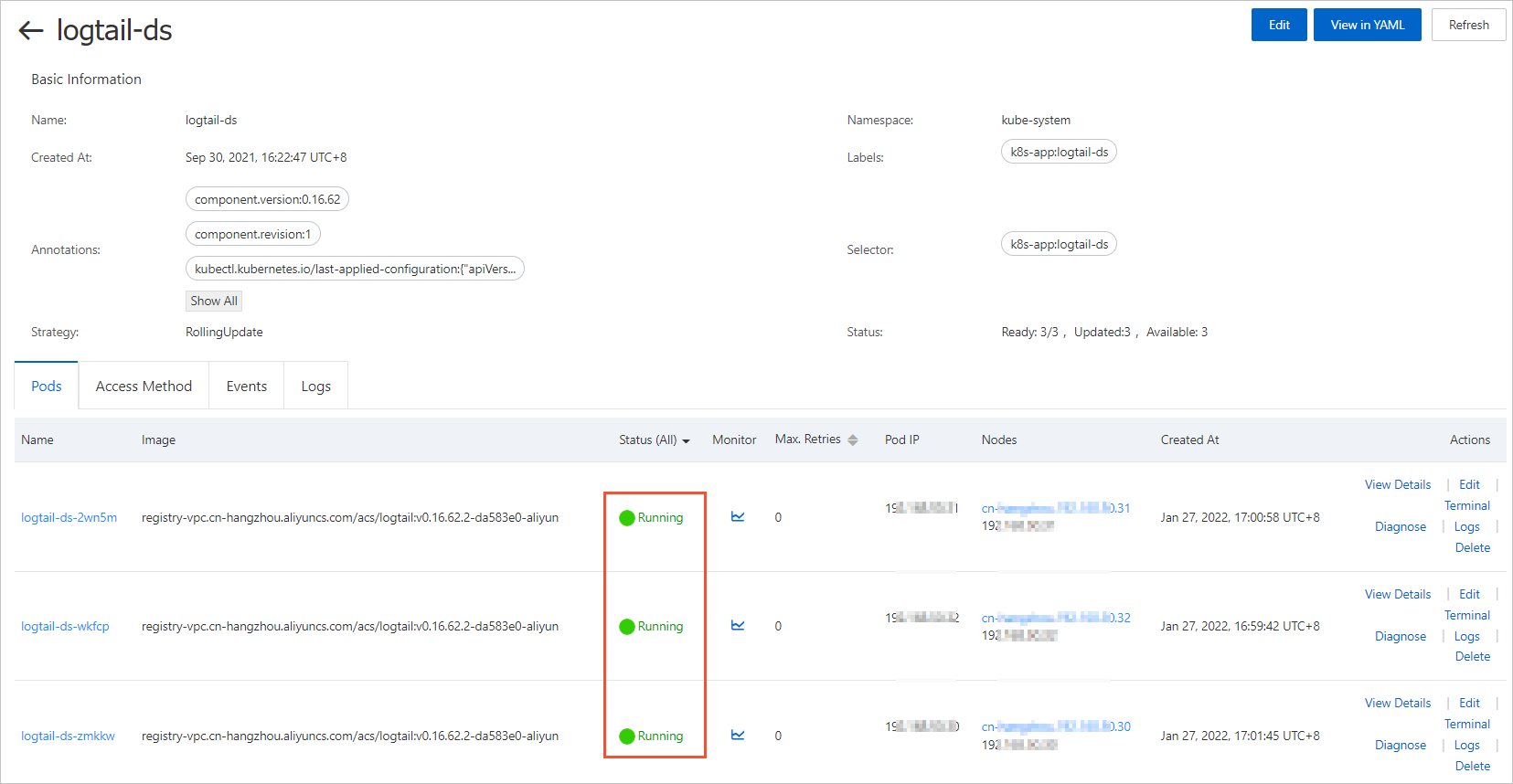
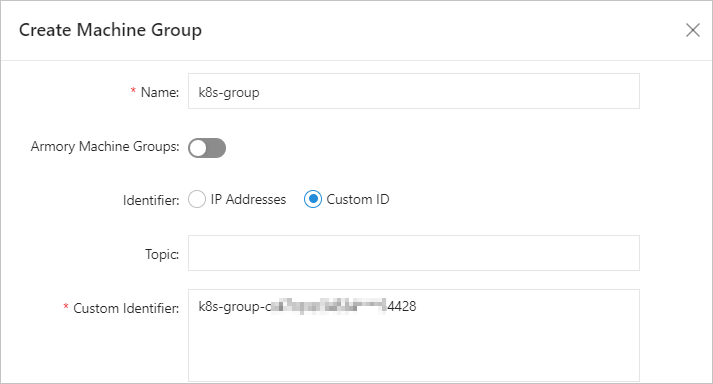
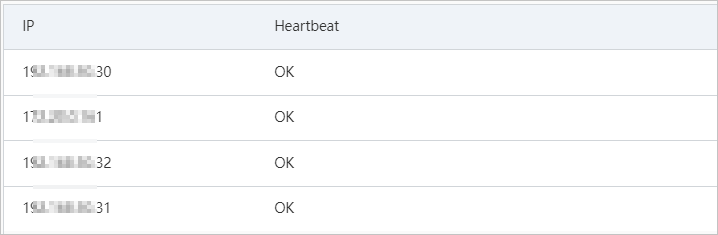
 > Create Machine Group
> Create Machine Group