Application Load Balancer (ALB) provides higher Layer 7 load balancing capabilities and more advanced routing features than Classic Load Balancer (CLB). ALB can balance large volumes of network traffic at the application layer and is interfaced with Web Application Firewall (WAF). Traffic forwarding and protection are decoupled for ALB. ALB supports more advanced features which improve user experience. This topic describes how to manually migrate Layer 7 listeners from CLB to ALB.
Sample scenario
The following figure shows a scenario that is used as an example in this topic. An enterprise purchased an Internet-facing CLB instance in the China (Hangzhou) region. A redirect rule, a domain name-based forwarding rule, and a URL-based forwarding rule are configured for the CLB instance. The CLB instance provides Internet-facing services by using a domain name. When clients access the domain name www.example.net, network traffic is routed to the CLB instance based on an A record. The CLB instance forwards network traffic to ECS01 and ECS02 based on the forwarding rules.

Due to business development, the enterprise wants to migrate services from the CLB instance to an ALB instance. To ensure service stability, the enterprise does not want to change the domain name that is used to provide services or the IP addresses of the backend servers. To meet the preceding requirements, the enterprise can purchase an ALB instance in the China (Hangzhou) region and configure ALB forwarding rules that forward network traffic in the same manner that the forwarding rules of the CLB instance forward network traffic. Then, the enterprise can configure DNS records that have different weights to migrate network traffic from the CLB instance to the ALB instance.

Precautions
CLB and ALB use the pay-as-you-go billing method. The billable items and pricing of CLB and ALB are different. After you migrate services from CLB to ALB, the fees that you are charged may change. For more information, see the following topics:
The ALB instance and the CLB instance must use the same backend servers, which must be deployed in the same virtual private cloud (VPC).
You cannot migrate services from a TCP or UDP listener of a CLB instance to an ALB instance. You can migrate the services only from an HTTP or HTTPS listener.
You can migrate services from an IPv4 CLB instance to an IPv4 or dual-stack ALB instance. You can migrate services from an IPv6 CLB instance only to a dual-stack ALB instance.
Prerequisites
Listeners and backend servers are configured for the CLB instance from which you want to migrate services. An A record is configured for the CLB instance to allow the CLB instance to provide services by using a domain name. For more information, see Overview.
ECS01 and ECS02 are added as backend servers to the CLB instance, and the Elastic Compute Service (ECS) instances are created in VPC1.
A redirect rule and forwarding rules are configured for the CLB instance. For more information, see Redirect HTTP requests to HTTPS and Forward requests based on domain names or URLs.
ECS03 and ECS04 are created in VPC1, and dig is installed on ECS04. ECS03 is used to test network traffic before the migration. ECS04 is used to check how traffic is distributed during the migration.
Procedure

Step 1: Create an ALB instance
- Log on to the ALB console.
On the Instances page, click Create ALB.
On the Application Load Balancer page, configure the parameters. The following table describes the parameters.
Parameter
Description
Region
Select the region where you want to create the ALB instance. The region must be the same as the region where the CLB instance resides. In this example, China (Hangzhou) is selected.
Network Type
Select the network type of the ALB instance. The system allocates a public or private IP address to the ALB instance based on the network type. The network type of the ALB instance must be the same as the network type of the CLB instance. In this example, Internet is selected.
Intranet: The ALB instance has only private IP addresses and can be accessed only by resources in the VPC where the ALB instance is deployed.
Internet: The ALB instance has public and private IP addresses. By default, Internet-facing ALB instances use EIPs to provide services over the Internet. If you select Internet, you are charged instance fees and data transfer fees for the EIPs.
Public IP address: EIPs are used to provide services over the Internet and expose ALB instances to the Internet.
Private IP address: allows resources in VPCs to access ALB instances.
You can change the network type of an ALB instance. For more information, see Change the network type of an ALB instance.
NoteIf an ALB instance is assigned both an IPv4 address and an IPv6 address, the IPv4 address is used to provide services over the Internet. If you want to use the IPv6 address to provide services over the Internet, you must change the private IPv6 address to a public IPv6 address. In this case, you are charged IPv6 gateway fees. For more information, see Billing rules.
VPC
Select the VPC in which the backend servers of the CLB instance are deployed. In this example, VPC1 is selected.
Zone
Select a zone and a vSwitch.
ALB supports multi-zone deployment. If the current region has two or more zones, you must select at least two zones to ensure high availability. ALB does not charge additional fees.
You must select a vSwitch for each zone of the ALB instance. If no vSwitch is available, create one as prompted.
Optional: Select an elastic IP address (EIP) in each of the selected zones.
If no EIP is available, use the default option Automatically assign EIP. Then, a pay-as-you-go EIP that uses BGP multi-line bandwidth and the default security protection mode is automatically created and associated with the ALB instance.
Alternatively, you can associate an existing EIP with the ALB instance.
NoteYou can associate only pay-as-you-go (pay-by-data-transfer) EIPs that are not added to Internet Shared Bandwidth instances with an ALB instance.
The EIPs that you specify for different zones of the same ALB instance must be of the same type.
IP Mode
Select an IP mode for the ALB instance.
Static IP: Only one IP address is available in each zone. The IP address cannot be changed. An ALB instance that uses a static IP address supports up to 100,000 queries per second (QPS).
Dynamic IP: One or more IP addresses are available in each zone. The number of IP addresses that the ALB instance uses increases together with the loads. This IP mode supports up to one million QPS.
IP Version
Select an IP version. You can migrate services from an IPv4 CLB instance to an IPv4 or dual-stack ALB instance. You can migrate services from an IPv6 CLB instance only to a dual-stack ALB instance. Select an IP version based on your business requirements.
IPv4: If you select this option, the ALB instance can be accessed only by IPv4 clients.
Dual-stack: If you select this option, the ALB instance can be accessed by IPv4 and IPv6 clients. For more information about the limits on dual-stack ALB instances, see IP versions.
Edition
Select the edition of the ALB instance.
Basic: Basic ALB instances support basic routing features such as request forwarding based on domain names, URLs, and HTTP headers.
Standard: Standard ALB instances support advanced routing features in addition to the features of basic ALB instances. Standard ALB instances support custom TLS security policies, redirects, and rewrites.
WAF Enabled: As an upgrade from standard ALB instances, WAF-enabled ALB instances are integrated with Web Application Firewall (WAF) 3.0 to protect web applications. Network traffic is filtered by WAF before the traffic is forwarded to ALB listeners. For more information about the limits on WAF-enabled ALB instances, see Limits on WAF-enabled ALB instances.
For more information about the differences among basic ALB instances, standard ALB instances, and WAF-enabled ALB instances, see Functions and features.
Associate with an Internet Shared Bandwidth instance
If an ALB instance is deployed in two zones and is not associated with an Internet Shared Bandwidth instance, the default maximum Internet bandwidth of the ALB instance is 400 Mbit/s.
If you require a higher bandwidth, associate an EIP bandwidth plan with your ALB instance. If you select Associate with EIP Bandwidth Plan, you must select an Internet Shared Bandwidth instance. If no Internet Shared Bandwidth instance is available, click Purchase EIP Bandwidth Plan and purchase an Internet Shared Bandwidth instance. Then, return to the ALB buy page and click
 to select the Internet Shared Bandwidth instance that you purchased.
to select the Internet Shared Bandwidth instance that you purchased. We recommend that you purchase a pay-as-you-go Internet Shared Bandwidth instance. For more information about how to purchase an Internet Shared Bandwidth instance, see Create an Internet Shared Bandwidth instance.
NoteThis parameter is available only if you set Network Type to Internet.
Billing Method
By default, Pay-by-Data-Transfer is selected. The maximum bandwidth is used for reference only. It indicates the upper limit of the bandwidth. When resource contention occurs, the bandwidth allocated to each ALB instance may be lower than the maximum bandwidth value. For more information about the billing of EIPs, see EIP billing.
NoteThis parameter is available only if Network Type is set to Internet and Associate with EIP Bandwidth Plan is not selected.
Instance Name
Enter a name for the ALB instance.
Resource Group
Select the resource group to which the ALB instance belongs.
Notes on Creating Service Linked Roles
The first time you create an ALB instance, click Create to create a service-linked role. The service-linked role allows ALB to access cloud services and resources, such as elastic network interfaces (ENIs), security groups, EIPs, and Internet Shared bandwidth instances. For more information, see Service-linked roles for ALB.
NoteThis parameter is displayed only on the first time that you create an ALB instance.
Click Buy Now and complete the payment.
Step 2: Create a server group for the ALB instance
- Log on to the ALB console.
In the top navigation bar, select the region where the ALB instance resides. In this example, China (Hangzhou) is selected.
In the left-side navigation pane, choose .
On the Server Groups page, click Create Server Group.
In the Create Server Group dialog box, configure the parameters and click Create. The following table describes the parameters.
Parameter
Description
Server Group Type
Specify a type of server group. In this example, Server is selected.
Server Group Name
Enter a name for the server group. In this example, RS1 is used.
VPC
Select a VPC from the VPC drop-down list. Only servers in the VPC can be added to the server group. In this example, VPC1 is selected. The backend servers of the CLB instance are deployed in VPC1.
Backend Server Protocol
Select a backend protocol. In this example, HTTP is selected.
Scheduling Algorithm
Select a scheduling algorithm. In this example, Weighted Round-robin is selected.
Resource Group
Select the resource group to which the ALB instance belongs.
IPv6 Support
Specify whether to enable IPv6. In this example, the default setting is used. IPv6 is disabled.
Session Persistence
Specify whether to enable session persistence. In this example, the default setting is used. Session persistence is disabled.
Persistent Connection
Specify whether to enable the persistent TCP connection feature. In this example, this feature is enabled.
Configure Health Check
Specify whether to enable the heath check feature. In this example, the default setting is used. The health check feature is enabled.
Advanced Settings
In this example, the default settings are used.
In the dialog box that appears, click Add Backend Server. On the Backend Servers tab, click Add Backend Server.
In the Add Backend Server panel, select the backend servers of the CLB instance and click Next.
In this example, ECS01 and ECS02 are selected.
In the Ports/Weights step, set the ports and weights of the ECS instances and click OK.
In this example, the port is set to 80 and the default weight 100 is used.
NoteALB instances in dynamic IP mode support up to one million QPS. Standard ALB instances support up to 1,000 backend servers. To withstand traffic spikes in specific time periods, you can use a scaling group to scale an ALB instance to reduce costs.
Step 3: Configure listeners for the ALB instance
This example describes how to configure a redirect rule, a domain name-based forwarding rule, and a URL-based forwarding rule for the ALB instance.
If a redirect rule is configured for the CLB instance, you must also configure a redirect rule for the HTTP listener of the ALB instance.
If a domain name-based forwarding rule and a URL-based forwarding rule are configured for the CLB instance, you must also configure domain name-based and URL-based forwarding rules that take effect in the same manner as those of the CLB instance for the ALB instance.
Add an HTTP listener and an HTTPS listener
- Log on to the ALB console.
In the top navigation bar, select the region where the ALB instance resides. In this example, China (Hangzhou) is selected.
Use one of the following methods to open the listener configuration wizard:
On the Instances page, find the ALB instance that you want to manage and click Create Listener in the Actions column.
On the Instances page, click the ID of the ALB instance that you want to manage. On the Listener tab, click Create Listener.
In the Configure Listener step, configure the parameters and click Next. The following table describes the parameters.
Parameter
Description
Listener Protocol
Select a listener protocol.
In this example, HTTP is selected.
Listener Port
Specify the port on which the ALB instance listens. The ALB instance listens for requests on the specified port and then forwards the requests to backend servers. Valid values: 1 to 65535. In most cases, port 80 is used for HTTP and port 443 is used for HTTPS.
NoteThe ports on which an ALB instance listens must be unique.
In this example, port 80 is specified.
Listener Name
Enter a name for the listener.
Advanced Settings
Click Modify to configure advanced settings. In this example, the default settings are used.
In the Select Server Group step, select a server group of the Server Type, view the backend servers, and then click Next.
In this example, RS1 is selected.
In the Configuration Review step, confirm the configurations and click Submit.
Add an HTTPS listener. For more information, see Add an HTTPS listener.
The following section describes the parameters that are relevant to this topic.
Listener Protocol: In this example, HTTPS is selected.
Listener Port: In this example, port 443 is used.
Configure a redirect rule
Configure a redirect rule for the HTTP listener of the ALB instance to redirect all HTTP requests destined for the ALB instance to HTTPS port 443.
On the Listener tab, click the ID of the HTTP listener. On the listener details page, click the Forwarding Rules tab.
On the Forwarding Rules tab, click Add New Rule.
In the Add Forwarding Rule section, set the following parameters and click OK.
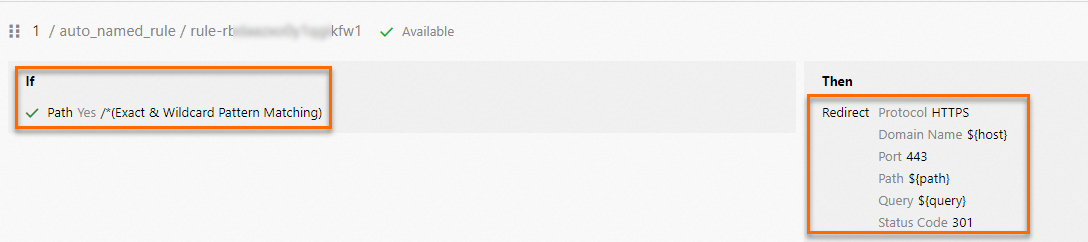
Parameter
Description
If (Matching All Conditions)
Select Path and Exact & Wildcard Pattern Matching from the drop-down list. Then, enter
/*.Action:
Select Redirect from the drop-down list and configure the following parameters:
Protocol: In this example, HTTPS is selected.
Domain Name: In this example, the default value ${host} is used.
Port: Enter the port number of the HTTPS listener. In this example, port 443 is used.
Path: In this example, the default value ${path} is used.
Query: In this example, the default value ${query} is used.
Status Code: In this example, 301 is used.
Create a domain name-based forwarding rule and a URL-based forwarding rule
Create a domain name-based forwarding rule and a URL-based forwarding rule for the HTTPS listener of the ALB instance.
Return to the Listener tab, and click the ID of the HTTPS listener that you created. On the listener details page, click the Forwarding Rules tab.
On the Forwarding Rules tab, click Add New Rule.
In the Add Forwarding Rule section, configure the parameters and click OK. The following table describes the parameters.
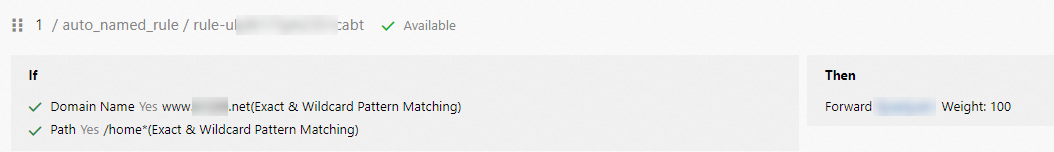
Parameter
Description
If (Matching All Conditions)
Select Domain Name and Exact & Wildcard Pattern Matching from the drop-down list. In this example,
www.example.netis entered.Click Add Condition and select Path from the drop-down list. In this example, /home* is entered.
Action:
Select Forward and select a server group of the Server Type from the drop-down list. In this example, RS1 is selected.
NoteThe backend servers in the selected server group must be the same as the backend servers in the vServer group specified in the forwarding rule of the CLB instance.
Step 4: Perform traffic tests
Enable access logs
ALB and Simple Log Service provide the access log feature that allows you to monitor the loads of ALB instances and identify issues.
- Log on to the ALB console.
In the top navigation bar, select the region where the ALB instance resides. In this example, China (Hangzhou) is selected.
On the Instances page, find the ALB instance that you want to manage and click its ID.
On the instance details page, click the Access Logs tab. On the Access Logs tab, click Create Access Log.
In the Create Access Log dialog box, configure the Project and Logstore parameters, and then click OK. In the message that appears, confirm the information and click OK.
Parameter
Description
Project
Simple Log Service projects are used to isolate and manage resources.
Select Project: Select a project from the drop-down list.
Create Project: Enter a project name in the field. A project is automatically created.
Logstore
A Logstore in Simple Log Service is used to collect, store, and query logs.
Select Logstore: Select a Logstore from the drop-down list.
Create Logstore: Enter a Logstore name in the field. A Logstore is automatically created. If you select Create Project, select Create Logstore.
Notes on Creating Service-linked Role
When you perform this operation, the system creates a service-linked role to grant the required permissions to ALB.
Test network traffic
Log on to ECS03. For more information, see Methods for connecting to an ECS instance.
Run the following command to modify the hosts file:
sudo vi /etc/hostsOpen the hosts file and add the IP address and domain name of the ALB instance to the file. Save the changes and close the file.
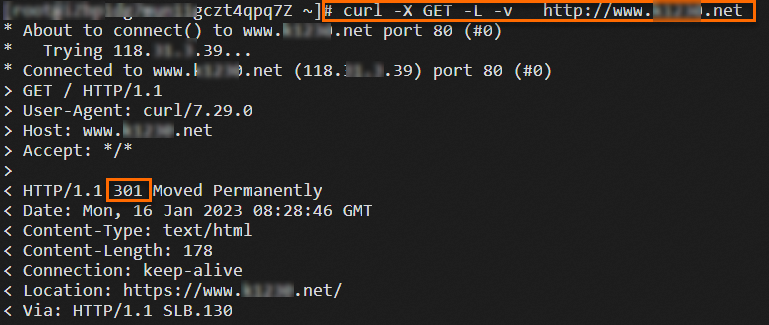
118.XX.XX.39 www.example.netRun the following command to check whether the redirect rule works as expected:
curl -X GET -L -v http://www.example.netThe following figure shows the result.
Return to the ALB console, go to the Access Logs tab of the ALB instance, and then click the link next to Storage Path to view the access log.
 In the Simple Log Service console, you can view the operation log of the domain name-based and URL-based forwarding rules of the ALB instance based on the request_uri, http_host, upstream_addr, and status fields.
In the Simple Log Service console, you can view the operation log of the domain name-based and URL-based forwarding rules of the ALB instance based on the request_uri, http_host, upstream_addr, and status fields.
Step 5: Migrate workloads from CLB to ALB
The following figure shows how CLB processes requests. A redirect rule is configured to redirect requests from HTTP port 80 to HTTPS port 443. HTTPS supports access to multiple domain names. In this example, the domain name example.net is used.

Before you perform the migration, we recommend that you compare the forwarding rules of the CLB and ALB instances. Make sure that the forwarding rules are fully tested and forward network traffic in the same manner. Otherwise, your services may experience adverse impact.
We recommend that you perform the migration during the off-peak hours of the CLB instance.
Before you perform the migration, you must add an A record to the CLB instance to map the domain names of your services to the IP address of the CLB instance.

After you perform a canary release on the ALB instance, you can migrate workloads from the CLB instance to the ALB instance. In this example, Alibaba Cloud DNS is used to manage DNS records and perform a canary release. The following procedure shows how to migrate workloads from CLB to ALB. For more information about Alibaba Cloud DNS, see Public Authoritative DNS Resolution.

Step 1. Configure a temporary domain name for the CLB instance
To meet the requirements for DNS record weights, we recommend that you add a CNAME record to the ALB instance. In the CNAME record, map the temporary domain name of the CLB instance to the IP address of the CLB instance.
To specify weights for different DNS records of the same domain name, the DNS records must have the same type, hostname, and ISP line. A records, CNAME records, and AAAA records are supported.
Log on to the Alibaba Cloud DNS console.
On the Authoritative DNS Resolution page, find and click the domain name
www.example.net. The domain name points to the IP address of the CLB instance.On the DNS Settings page, click Add DNS Record. In the Add DNS Record panel, configure the parameters and click OK. The following table describes the parameters.
Parameter
Description
Record Type
Select CNAME from the drop-down list.
Hostname
Enter the prefix of your domain name. In this example, www is entered.
DNS Request Source
Select Default.
Record Value
Enter a temporary domain name. In this example, web0.example.net is entered.
TTL Period
Specify a time-to-live (TTL) value for the CNAME record. The TTL determines the time period that the record is cached on the DNS server. In this example, the TTL is set to 5 seconds.
In this example, Alibaba Cloud DNS Enterprise Ultimate Edition is used. The TTL value is for reference only. Specify a TTL value based on your business requirements. For more information, see Editions.
On the DNS Settings page, find the A record that points to the IP address of the CLB instance and click Modify in the Actions column.
In the Modify DNS Record panel, modify the Hostname parameter and click OK. In this example, the Hostname parameter is set to web0. The other parameters are not modified.
Step 2: Add a CNAME record for the ALB instance
Log on to the ALB console.
In the top navigation bar, select the region where the ALB instance resides. In this example, China (Hangzhou) is selected.
Find the ALB instance that you want to manage and copy its domain name.
To create a CNAME record, perform the following steps:
Log on to the Alibaba Cloud DNS console.
Find the domain name that you want to manage and click Configure in the Actions column. In this example, the domain name is the domain name of the CLB instance.
On the DNS Settings tab of the domain name details page, click Add DNS Record.
In the Add DNS Record panel, configure the parameters and click OK. The following table describes the parameters.
Parameter
Description
Record Type
Select CNAME from the drop-down list.
Hostname
Enter the prefix of your domain name. In this example, www is entered.
DNS Request Source
Select Default.
Record Value
Enter the CNAME. The CNAME is the domain name of the ALB instance.
TTL
Specify a TTL value for the CNAME record. The TTL determines the time period that the record is cached on the DNS server. In this example, the TTL is set to 5 seconds.
In this example, Alibaba Cloud DNS Enterprise Ultimate Edition is used. The TTL value is for reference only. Specify a TTL value based on your business requirements. For more information, see Editions.
NoteNew CNAME records immediately take effect. The time that is required for a modified CNAME record to take effect is determined by the TTL value of the CNAME record in the local DNS cache. The default TTL value is 10 minutes.
If the CNAME record that you want to create conflicts with an existing record, specify another domain name.
Step 3: Specify weights for the DNS records and perform a canary release
On the Domain Name Resolution page, click the domain name that you want to manage. On the DNS Settings page, click Weight Settings in the left-side navigation pane.
On the Weighted Round-robin page, click EnableWeight in the Actions column, and then click Set Weight.
To specify weights for different DNS records of the same domain name, the DNS records must have the same type, hostname, and ISP line. A records, CNAME records, and AAAA records are supported.
In the Set Weight panel, specify weights for the DNS records of the CLB and ALB instances. Set the weight of the DNS record for the CLB instance to 100. Set the weight of the DNS record for the ALB instance to 0.
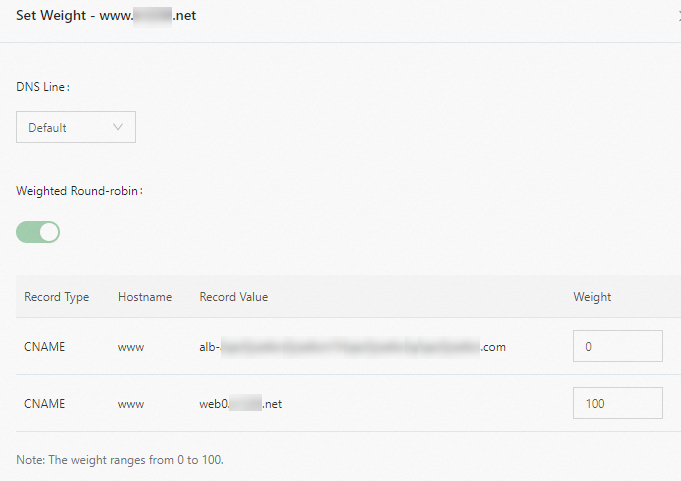
Gradually reduce the weight of the DNS record for the CLB instance and gradually increase the weight of the DNS record for the ALB instance. Make sure that your services are not affected.
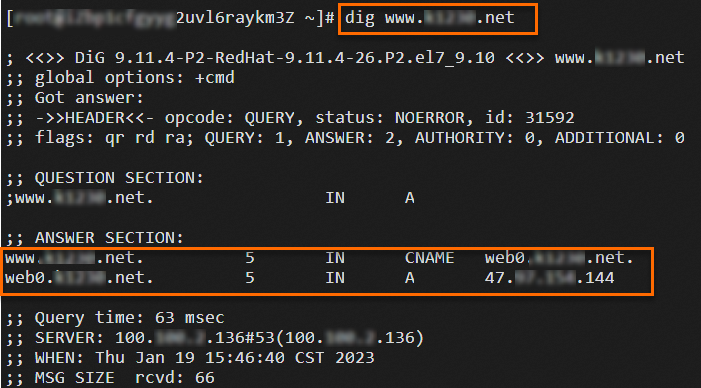
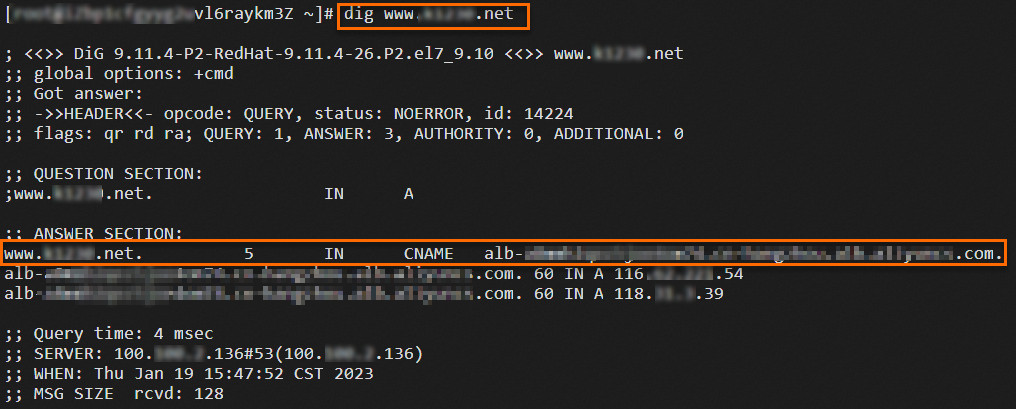
Log on to ECS04 and run the
digcommand multiple times to test network traffic after the migration.dig www.example.netThe following figures show the results. The results show that requests are forwarded to the ALB and CLB instances based on the weights of the DNS records.
Step 4: Migrate all workloads from CLB to ALB
Gradually reduce the weight of the DNS record for the CLB instance to 0, and gradually increase the weight of the DNS record for the ALB instance to 100. Make sure that your services are not affected. Then, all workloads are migrated from the CLB instance to the ALB instance. After all the persistent connections on the CLB instance are closed and requests are no longer sent to the CLB instance, you can release the CLB instance after a proper period of time. For more information about how to release a CLB instance, see Release a CLB instance.
The following figure shows how the ALB instance processes requests after the migration is complete.

Advanced features
ALB provides better load balancing capabilities at Layer 7 and more advanced features than CLB. The following topics help you become more familiar with ALB:
For an overview of ALB instances, see Overview of ALB instances.
For more information about ALB quotas, see Limits.
For more information about how to get started with ALB, see Use an ALB instance to balance loads for IPv4 services and Use ALB to balance loads for IPv6 services.
By default, ALB provides basic Anti-DDoS mitigation capabilities. For more information, see What is Anti-DDoS Origin?
The following table describes the differences in the advanced features between CLB and ALB.
Feature | CLB | ALB |
Server group management | Default server groups, vServer groups, and primary/secondary server groups are supported. | Server groups are supported. |
HTTP-to-HTTPS redirect | You can configure redirects when you create a listener. For more information, see Use CLB to redirect HTTP requests to HTTPS. | You can create forwarding rules for redirects. For more information, see Redirect HTTP requests to an HTTPS listener. |
Multiple certificates for an HTTPS listener | For more information, see Configure a CLB instance to serve multiple domain names over HTTPS. | For more information, see Configure an ALB instance to serve multiple domain names over HTTPS. |
HTTPS service that uses one-way authentication | Certificates issued by Alibaba Cloud and third-party certificates are supported. For more information, see Configure one-way authentication for HTTPS requests. | You can use Certificate Management Service to manage certificates. For more information, see Configure HTTPS to encrypt communication. |
HTTPS service that uses two-way authentication | Certificates issued by Alibaba Cloud and third-party certificates are supported. For more information, see Configure mutual authentication on an HTTPS listener. | Certificates issued by Alibaba Cloud are supported. You can use Certificate Management Service to manage certificates. For more information, see Configure mutual authentication on an HTTPS listener. |
WAF protection | The transparent proxy mode and the CNAME record mode are supported. For more information, see Enable WAF protection for a Layer 7 CLB instance and Add a domain name to WAF. | The service integration mode, transparent proxy mode, and CNAME record mode are supported.
|
FAQ
Which configurations of the CLB and ALB instances must remain unchanged before and after the migration?
The region, network type, listener protocol, and backend servers must remain unchanged. The ALB instance must be in the same VPC as the backend servers of the CLB instance. The ALB instance and the backend servers can be in different zones.
What are the differences between the certificates used by CLB and those used by ALB?
CLB and ALB support encrypted transmission over HTTPS. CLB supports certificates issued by Alibaba Cloud and third-party certificates. The certificates used by ALB are managed by Alibaba Cloud Certificate Management Service.
For more information about how to upload certificates for CLB instances, see Upload certificates.
For more information about how to upload certificates for ALB instances, see Purchase an SSL certificate and Upload and share an SSL certificate.
What are the differences in access control between CLB and ALB?
CLB supports access control for listeners. You can configure different access control lists (ACLs) for different listeners. For more information, see Overview.
ALB provides IPv4 and dual-stack instances. IPv4 ALB instances allow you to configure different ACLs for different listeners. For more information, see ACLs. Dual-stack ALB instances do not support access control.
What are the differences in domain name resolution between CLB and ALB?
CLB supports A records, which resolve custom domain names to the IP addresses of CLB instances.
For ALB instances:
To allows users to access your services in a more convenient manner, we recommend that you use CNAME records to map custom domain names to the domain name of your ALB instance.
If you want to resolve a custom domain name to a specific IP address, we recommend that you use an ALB instance that has a specific IP address and then use an A record to resolve the custom domain name to the IP address of the ALB instance.
