This topic compares various encryption methods that are used in database systems and can help you select an encryption method based on your business requirements.
Overview
Access control systems are used to limit access to specific areas. For example, in a residential community, a multi-tiered access control system restricts entry at the community entrance, building entrances, and individual apartment entrances to ensure only authorized individuals can access specific areas. An access control system can achieve different access control results based on locations and areas. Encryption methods serve the same as an access control system for a residential community. You can use encryption methods to encrypt sensitive data and achieve different effects based on the position and granularity of the data.
Introduction to database encryption methods
Disk encryption
When you create a system disk or data disks together with an ECS instance or when you separately create a data disk, enable encryption for the cloud disk. After the cloud disk is created, the data within the operating system of the ECS instance that serves as the host of the cloud disk is automatically encrypted when the data is written to the cloud disk and is automatically decrypted when the data is read from the cloud disk. Disk encryption ensures the security of data that is stored on disks at the Infrastructure as a Service (IaaS) layer. For more information, see Cloud disk encryption.
Transparent data encryption (TDE)
Before data is written from the database memory to a file system, the database engine encrypts data in memory and then writes encrypted data to the file system. TDE ensures the security of data that is stored in file systems at the PaaS layer. For more information, see Configure TDE.
Column encryption (basic edition of the always-confidential database feature)
Before query results are sent from a databases to a client, the results are encrypted. The client uses the required key to decrypt the query results. This ensures that data transferred between database clients and databases is in ciphertext. Column encryption ensures data security when data is transferred between clients and databases. For more information, see Overview.
Potential database attacks
A database is a system application, and data within the database is vulnerable to security risks. The following figure shows the security risks and attack paths. For more information, see Oracle's Maximum Security Architecture for Database Security.
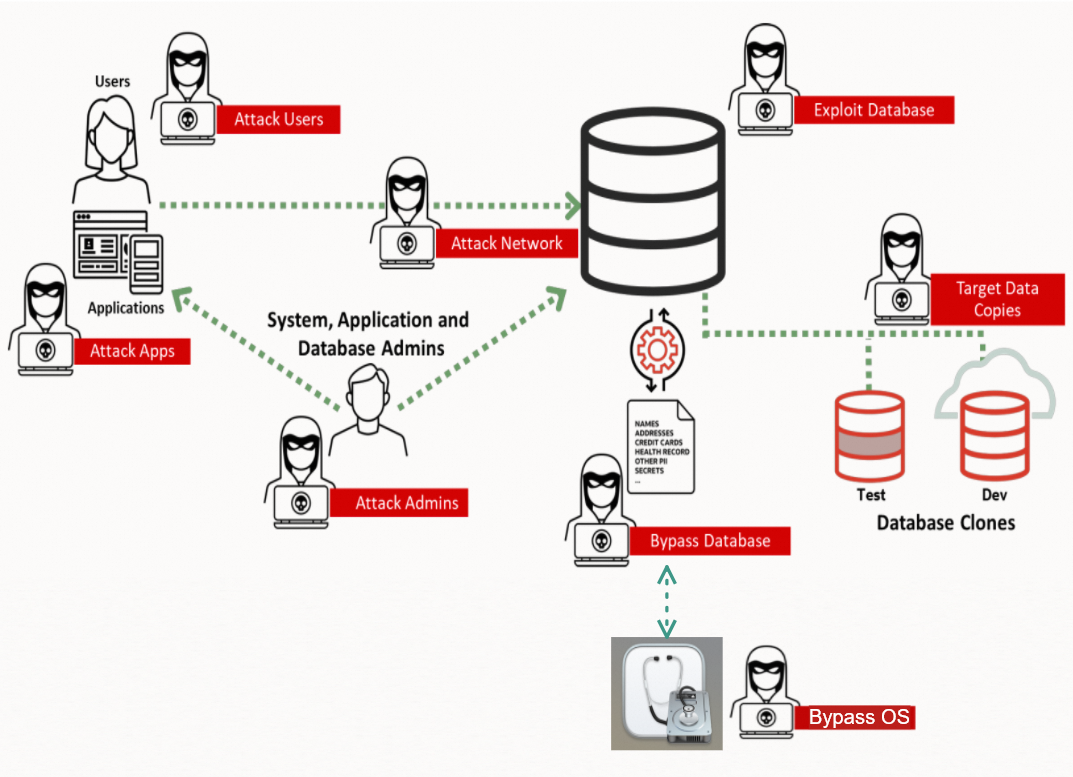
The following table describes different types of attacks.
Type | Description | Method |
Attack Admins | Attacks system administrators, such as OS administrators. System administrators have the highest permissions on a database system. If an attacker obtains an administrator account, the attacker can manage and access all storage resources, systems, and peripherals. In a database system, system administrators are divided into the following types:
| OS vulnerabilities Administrator account or password leaks Improper system configurations |
Attack Users | Attacks users, such as database users. End users can access database systems and specific data. An attacker can obtain a user account and use the account to access user data to launch attacks such as logical data breach attacks. This allows the attacker to exploit vulnerabilities, such as by using SQL injection, to escalate privileges and obtain administrator permissions. | User account or password leaks Logical data breaches |
Attack Apps | Attacks application services, such as website servers. Application services are accessible over the Internet, have a larger attack surface, and are more vulnerable to intrusion compared to databases that are strictly protected. | Application service vulnerabilities OS vulnerabilities |
Attack Network | Attacks network connections, such as listening to and intercepting network data. In most cases, network attacks use bypass methods and are difficult to detect. | Network listening and interception |
Bypass Database | Bypasses database systems to obtain data and steals database data in bypass mode. For example, PaaS personnel can initiate a physical data breach by copying data files and backup files from database disks. | Physical data breaches |
Bypass OS | Bypasses the file system in an OS to obtain data and steals disk data in bypass mode. For example, IaaS personnel can directly copy data from local disks or cloud disks. | Mounting attacks |
Exploit Database | Exploits defects within a database system, such as code bugs, to access the database directly or indirectly. | Database OS vulnerabilities |
Target Data Copies | Attacks development and test databases. In most cases, production data is directly synchronized to a development and test database. However, no effective methods are used to ensure the security of the development and test database. As a result, the development and test database is more vulnerable than the production database. | All of the above |
To address these potential database security risks in different application paths in a system, a comprehensive security solution is required to respond to the potential database security risks in different system applications. Different security technologies and management methods, such as SSL and certificate services, authentication and access control, whitelists and security groups, data encryption and masking, and security auditing, are required to develop a solution.
Capability matrix of encryption methods
The encryption methods that are used in databases include disk encryption, TDE, and column encryption. The following table describes the encryption methods. You can select an appropriate encryption method based on business pain points, encryption granularity, transformation costs, and performance.
Database encryption method | Disk encryption | TDE
| Column encryption ((Basic edition of the always-confidential database feature) |
Issues that can be resolved | Bypass OS and Attack Admins (IaaS) | Bypass Database, Bypass OS, and Attack Admins (PaaS and IaaS) | Attack Users, Attack Apps, Attack Admins, Attack Network, and Target Data Copies |
Data visibility to database O&M personnel, such as DBA | Visible | Visible | Invisible |
Data visibility to PaaS O&M personnel, such as OS administrators | Visible | Invisible | Visible |
Data visibility to IaaS O&M personnel, such as physical process engineers | Invisible | Invisible | Visible |
Encryption granularity | Cluster | Table and database | Column |
Business transformation | N/A | N/A | You must replace the Java Database Connectivity (JDBC) driver with EncJDBC, and you do not need to modify code. |
Performance | Slight performance loss, or even no loss |
|
|
Comparison of the principles of encryption methods
Architecture
The following figure shows the roles of encryption methods in a database system based on the system architecture:
Disk encryption is applied to the OS layer of an ECS instance and the host on which the ECS instance resides to encrypt and decrypt OS files. Disk encryption takes effect on all clusters on the ECS instance or the host on which the cloud disks are deployed.
TDE is applied to clusters to encrypt and decrypt cached database files. TDE takes effect on individual clusters.
Column encryption is applied to clusters to encrypt and decrypt query results in the database memory and return data in ciphertext to the applications that are connected to the clusters. Column encryption takes effect on individual clusters.
Column encryption, TDE, and disk encryption can be used in combination.

Data
The following figure shows the encryption states of data in a database system by encryption method.
In disk encryption, data is in ciphertext in disks, but in plaintext in OS files and databases.
In TDE, data is in ciphertext in disks and OS files, but in plaintext in databases.
In column encryption, data is in ciphertext in databases (except in the engine), but in plaintext in OS files and disks. Data is running in ciphertext and stored in plaintext.
The combination of column encryption and TDE provides end-to-end encryption for data in transit.

Differences between different database encryption methods
Storage security technology | Disk encryption | TDE | Column encryption |
Effective scope | OS | Database engine | Database engine |
Encryption scope | Host or ECS Instance | Cluster | Cluster |
Encryption granularity | Cluster | Database and table | Column |
Application awareness | Transparent to applications | Transparent to applications | Replacement of JDBC with EncJDBC for applications |
Summary
Database encryption technologies have been mature, but databases still face various security threats from the user perspective. To address these threats, different database encryption technologies are available, such as disk encryption, TDE, and column encryption. You can select an appropriate database encryption method based on security requirements, business transformation costs, and performance.