Transparent Data Encryption (TDE) allows you to perform real-time I/O encryption and decryption on data files. Data is encrypted before it is written to the disk and is decrypted when it is read from the disk to the memory. After you enable TDE for your PolarDB cluster, the size of data files in your PolarDB cluster does not increase. You can use TDE without the need to modify the configurations of your application.
Prerequisites
PolarDB for MySQL clusters must meet the following requirements:
Edition
Database engine
Revision version
Cluster Edition
MySQL 5.6
5.6.1.0.21 or later
MySQL 5.7
5.7.1.0.3 or later
MySQL 8.0.1 and MySQL 8.0.2
8.0.1.1.1 or later
Standard Edition
MySQL 5.7
5.7.1.0.3 or later
MySQL 8.0.1 and MySQL 8.0.2
8.0.1.1.1 or later
Background information
TDE for PolarDB for MySQL adopts the Advanced Encryption Standard (AES) algorithm. The key length is 256 bits. The keys that are used in TDE are generated and managed by KMS. PolarDB for MySQL does not provide keys or certificates. In some zones, you can use the keys that are automatically generated by Alibaba Cloud. You can also use your own key materials to generate keys. Then, authorize PolarDB for MySQL to use these keys.
Precautions
In I/O bound scenarios, TDE may adversely affect the performance of your databases.
TDE can be enabled on clusters that have joined a global database network (GDN). After TDE is enabled on the primary cluster in a GDN, TDE is enabled on the secondary clusters in the GDN by default. The key used by the secondary clusters and the region for the key resides must be the same as the primary cluster. The region of the key cannot be modified.
You cannot enable TDE for the secondary clusters in a GDN.
Procedure
After you enable TDE for a PolarDB for MySQL cluster, the cluster is automatically restarted. Proceed with caution.
After TDE is enabled, you cannot disable TDE.
Log on to the PolarDB console.
In the upper-left corner, select the region in which the cluster is deployed.
Find the cluster and click its ID.
In the left-side navigation pane, choose .
On the TDE Settings tab, turn on TDE Status.
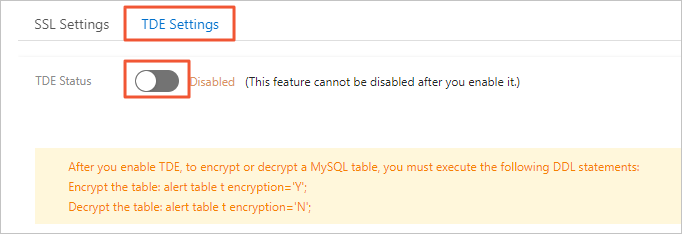
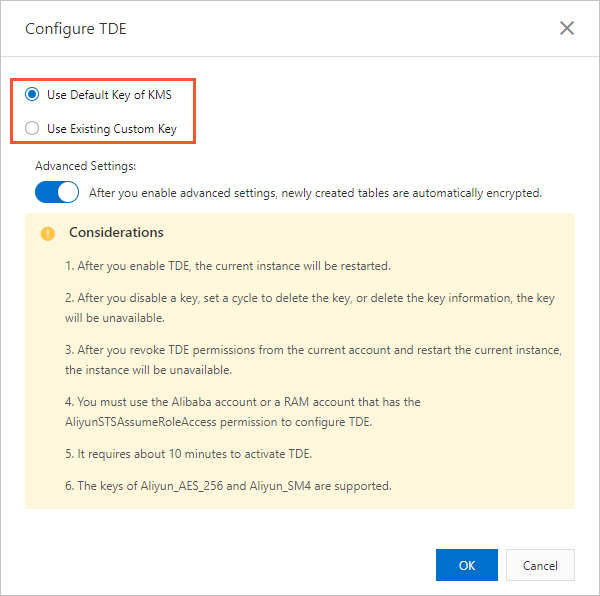
In the Configure TDE dialog box, select Use Default Key of KMS or Use Existing Custom Key.
 Note
NoteTDE supports the following keys:
Aliyun_AES_256andAliyun_SM4.In the dialog box that appears, select Use Default Key of KMS and click OK.
If you choose Use Existing Custom Key, select a key generated by KMS from the drop-down list and click OK.
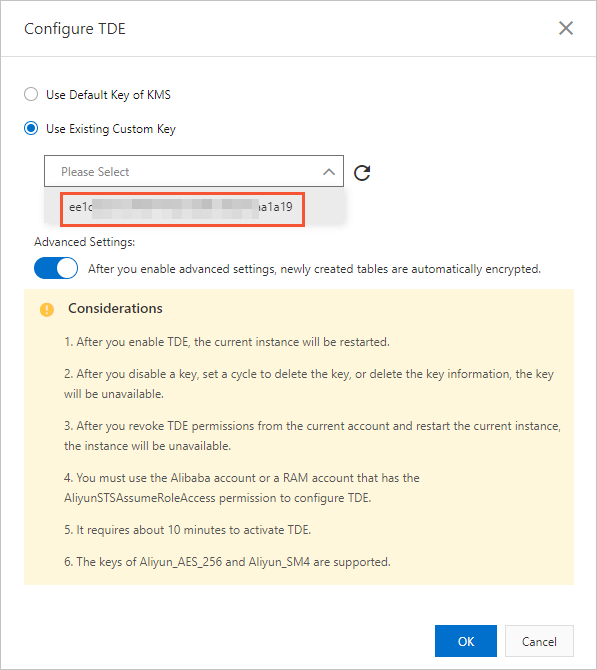 Note
NoteIf you have a custom key, make sure the following requirements are met:
Key Management Service (KMS) is activated. For more information, see Activate KMS.
Your PolarDB cluster is authorized to access KMS. For more information, see Authorize a PolarDB cluster to access KMS.
You must use an Alibaba Cloud account or an account that has the AliyunSTSAssumeRoleAccess permission.
If you do not have a custom key, you need to click go to the KMS console. In the KMS console, you can create a key and import your own key material. For more information, see Create a CMK.
If you use an existing custom key for TDE, take note of the following information:
If you disable the key, configure a plan to delete the key, or delete the key material, the key becomes unavailable.
If you revoke the authorization to a PolarDB for MySQL cluster, the cluster becomes unavailable after you restart the cluster.
It requires approximately 10 minutes to enable TDE.
Advanced settings
You can enable the Advanced Settings feature only when your cluster is of the following versions:
PolarDB for MySQL 8.0 and the revision version is 8.0.1.1.15 or later.
PolarDB for MySQL 5.7 and the revision version is 5.7.1.0.35 or later.
When you enable TDE, you can enable the Advanced Settings feature in the Configure TDE dialog box. After this feature is enabled, all newly created tables are automatically encrypted.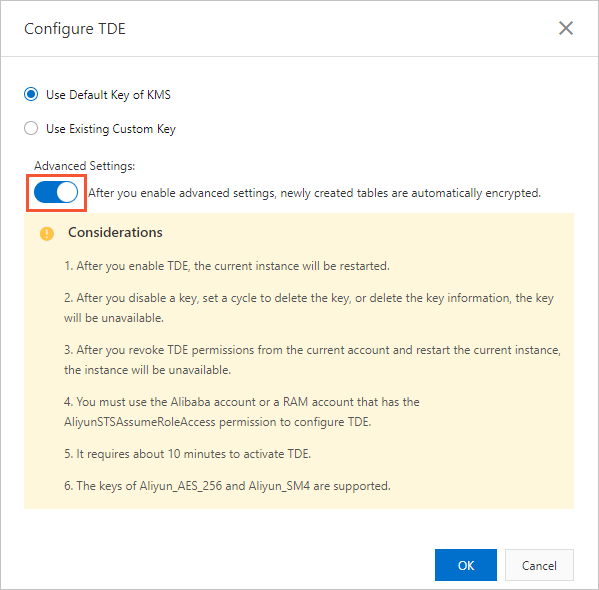
Encrypt and decrypt tables
If you turn on Advanced Settings, created tables are automatically encrypted and you do not need to manually encrypt the created tables. For existing tables, you need to perform specific operations to encrypt data.
To encrypt or decrypt tables after you enable TDE, you must log on to the database and execute the relevant DDL statements. The following table lists the DDL statements that are executed to encrypt and decrypt tables in the PolarDB for MySQL cluster of different MySQL versions.
Item | PolarDB MySQL 5.6 | PolarDB MySQL 5.7 & PolarDB MySQL 8.0 |
Encryption | | |
Decryption | | |
When you execute the preceding alter table statements to encrypt or decrypt a table, the table is locked.