Data Management (DMS) supports fine-grained permission control for MySQL databases. For example, you can manage permissions on databases, tables, fields, and views. This topic describes how to manage user permissions on MySQL databases in DMS.
Prerequisites
An ApsaraDB RDS for MySQL , PolarDB for MySQL , AnalyticDB for MySQL instance, self-managed MySQL database, native MariaDB database, or ApsaraDB for MariaDB database is used.
Your system role is a DMS administrator, a database administrator (DBA), or a regular user such as the owner of an instance.
The database account and database password of the MongoDB database are obtained.
Overview
You can manage coarse-grained permissions on MySQL databases in ApsaraDB RDS for MySQL instances or PolarDB for MySQL instances in the corresponding console. For example, you can grant other users the read-only permissions or the read and write permissions on a MySQL database. You can also grant other users the permissions to execute DML statements or DDL statements on the MySQL database. However, you may need more flexible and finer-grained permission management. In this case, you can use the user permission management feature of DMS. Examples:
You can grant User A the global permissions to execute
SELECTstatements andUPDATEstatements.NoteGlobal permissions apply to all databases in a database instance. For more information, see Supported global permissions.
You can grant User B the permissions to execute
SELECTstatements on a table or the permissions to executeUPDATEstatements on a field.NoteFine-grained permissions can apply to specific or all databases in a database instance. For more information, see Supported fine-grained permissions.
Create a user
- Log on to the DMS console V5.0.
Log on to the PostgreSQL database. For more information, see Log on to a database instance.
In the left-side navigation pane of the DMS console, right-click the instance that you want to manage and select Account Management.
NoteIf you log on to the DMS console in simple mode, click Database instances in the left-side navigation pane. In the instance list that appears, right-click the instance that you want to manage and select Account Management.
On the Account Management page, click Create User in the upper-left corner.
In the Create User dialog box, perform the following steps:
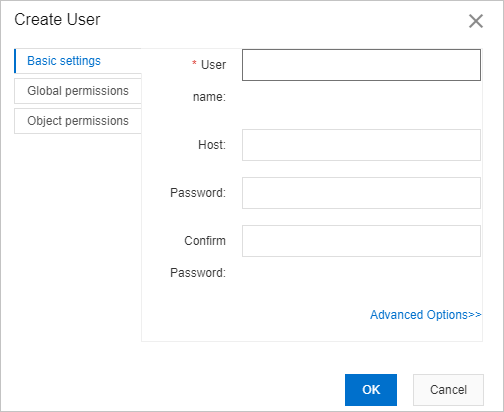
On the Basic settings tab, configure the parameters that are described in the following table.
Parameter
Description
User name
The name of the user that you want to use to log on to the database.
Host
Indicates that the account is allowed to access the database from an IP address.
NoteIf you do not configure this parameter, the user is not restricted to accessing the authorized databases from specific IP addresses. The default value of this parameter is
%.Password
The password that you want to use to log on to the databases in the current instance.
Confirm Password
Enter the password again to confirm the password.
NoteAfter you configure the preceding parameters, DMS automatically generates an SQL statement based on the parameters that you configure. Then, DMS executes the statement for each database in the current instance. The syntax of the SQL statement is
CREATE USER 'Username'@'Hostname' IDENTIFIED BY 'Password';.You can click Advanced Options to complete more configurations.
For example, you can set specific limits for the user, as shown in the following figure. In this case, DMS generates and executes the following SQL statement:
GRANT USAGE ON *.* TO 'Username'@'Hostname' WITH MAX_QUERIES_PER_HOUR 100 MAX_UPDATES_PER_HOUR 200 MAX_CONNECTIONS_PER_HOUR 300 MAX_USER_CONNECTIONS 400;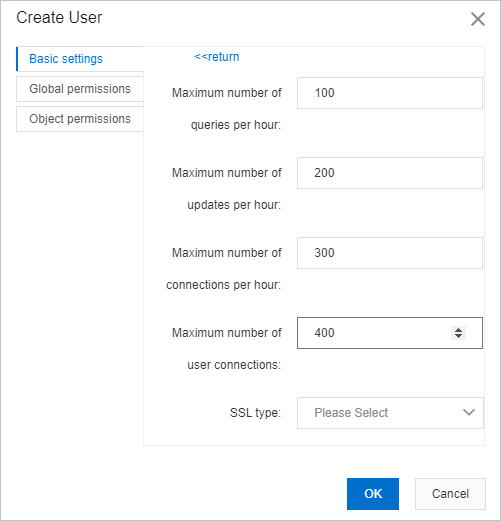
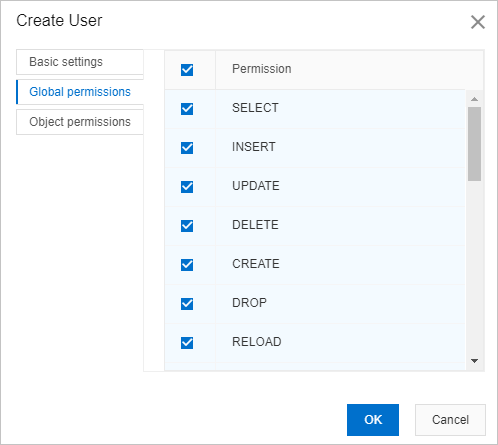
Click the Global permissions tab and select one or more permissions that you want to grant to the user.
 Note
NoteIf you cannot find the permissions that you require, the permissions are not supported by the instance or your Alibaba Cloud account is not authorized to grant the permissions. If you use a standard account, log on to the DMS console by using a privileged account and retry this step.
Click the Object permissions tab and configure the parameters to grant fine-grained permissions to the user.
For example, you can allow the user to query or insert data in a database, and delete data from a table in the database, as shown in the following figure. In this case, DMS generates and executes the following SQL statements:
GRANT SELECT,INSERT ON `rds_db`.* TO 'Username'@'Hostname'; GRANT DELETE ON `rds_db`.`rds_table` TO 'Username'@'Hostname';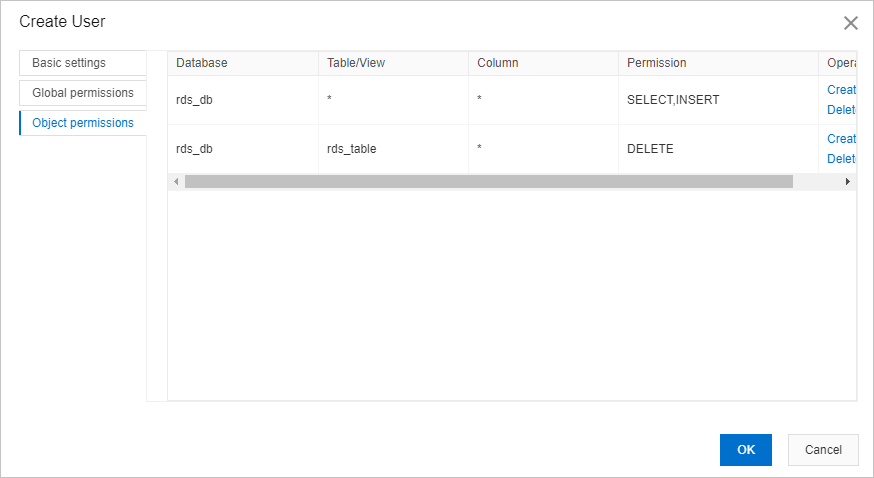
Click Confirm.
In the Preview SQL Statement message, click Confirm.
NoteSQL statements can be generated based on the parameters that you configure. If the database instance is managed in Security Collaboration mode, the SQL statements may fail to be executed due to security rules. In this case, you can perform operations by following the on-screen instructions or contact a database administrator (DBA) or DMS administrator. For information about how to modify security rules, see FAQ of this topic.
Modify or delete a user
You can modify the username, password, global permissions, and fine-grained permissions of a user that you are authorized to manage.
- Log on to the DMS console V5.0.
In the left-side navigation pane of the DMS console, right-click the instance that you want to manage and select Account Management.
NoteIf you log on to the DMS console in simple mode, click Database instances in the left-side navigation pane. In the instance list that appears, right-click the instance that you want to manage and select Account Management.
On the Account Management page, find the user that you want to manage and click Edit in the Operation column to modify the information about the user, or click Delete in the Operation column to delete the user.
Supported global permissions
Permission | Object | Description |
CREATE | Databases, tables, or indexes | Allows a user to create a database, a table, or an index. |
DROP | Databases, tables, or views | Allows a user to delete a database, a table, or a view. |
GRANT OPTION | Databases, tables, or stored procedures | Allows a user to grant or revoke one or more permissions for other users. |
REFERENCES | Databases, tables, or fields | Allows a user to create a foreign key to reference a database, a table, or a field. |
LOCK TABLES | Databases | Allows a user to lock tables in a database. |
EVENT | Databases | Allows a user to query, create, modify, or delete an event in a database. |
ALTER | Tables or views | Allows a user to modify a table or a view. For example, a user can be allowed to add a field to the table, create an index, or modify a field in the table. |
DELETE | Tables | Allows a user to delete data from a table. |
INDEX | Tables | Allows a user to create or delete indexes for a table. |
INSERT | Tables or fields | Allows a user to insert data into a table or a field. |
SELECT | Tables or fields | Allows a user to query data in a table or a field. |
UPDATE | Tables or fields | Allows a user to update data in a table or a field. |
CREATE VIEW | Views | Allows a user to create a view. |
SHOW VIEW | Views | Allows a user to check a view. |
TRIGGER | Triggers | Allows a user to create, delete, execute, or display a trigger. |
ALTER ROUTINE | Stored procedures | Allows a user to modify a stored procedure. |
CREATE ROUTINE | Stored procedures | Allows a user to create a stored procedure. |
EXECUTE | Stored procedures | Allows a user to execute a stored procedure. |
FILE | File access on a server host | Allows a user to access the files on a server host. |
CREATE TEMPORARY TABLES | Server administration | Allows a user to create a temporary table on a server. |
CREATE USER | Server administration | Allows a user to create a user on a server. |
PROCESS | Server administration | Allows a user to query information about the threads that are running on a server. |
RELOAD | Server administration | Allows a user to run commands on a server, such as the |
REPLICATION CLIENT | Server administration | Allows a user to check the statuses of the primary servers, replica servers, and binary logs. This permission is required for replication. Grant this permission to a user who is created to connect a replica server to the source server. |
REPLICATION SLAVE | Server administration | Allows a user to check the statuses of the primary servers, replica servers, and binary logs. This permission is required for replication. Grant this permission to a user who is created to connect a replica server to the source server. |
SHOW DATABASES | Server administration | Allows a user to view the names of all databases on a server. |
SHUTDOWN | Server administration | Allows a user to shut down a server. |
SUPER | Server administration | Allows a user to execute KILL statements to terminate the threads that are running on a server. Note ApsaraDB RDS for MySQL and ApsaraDB for MariaDB do not support the SUPER permission. |
Supported fine-grained permissions
Permission | Object | Description |
CREATE | Databases, tables, or indexes | Allows a user to create a database, a table, or an index. |
DROP | Databases, tables, or views | Allows a user to delete a database, a table, or a view. |
GRANT OPTION | Databases, tables, or stored procedures | Allows a user to grant or revoke one or more permissions for other users. |
REFERENCES | Databases, tables, or fields | Allows a user to create a foreign key to reference a database, a table, or a field. |
LOCK TABLES | Databases | Allows a user to lock tables in a database. |
EVENT | Databases | Allows a user to query, create, modify, or delete an event in a database. |
ALTER | Tables or views | Allows a user to modify a table or a view. For example, a user can be allowed to add a field to the table, create an index, or modify a field in the table. |
DELETE | Tables | Allows a user to delete data from a table. |
INDEX | Tables | Allows a user to create or delete indexes for a table. |
INSERT | Tables or fields | Allows a user to insert data into a table or a field. |
SELECT | Tables or fields | Allows a user to query data in a table or a field. |
UPDATE | Tables or fields | Allows a user to update data in a table or a field. |
CREATE VIEW | Views | Allows a user to create a view. |
SHOW VIEW | Views | Allows a user to check a view. |
TRIGGER | Triggers | Allows a user to create, delete, execute, or display a trigger. |
FAQ
Q: Why does the system inform me that I cannot execute the CREATE USER statement to create a user that has specific permissions because of security rules?
A: Troubleshoot errors based on the returned error message. Perform the following steps:
Query the security rule set that is configured for the instance.
In the left-side navigation pane, right-click the current instance and select View Details.
Modify a security rule.
Log on to the DMS console V5.0.
In the top navigation bar, choose .
On the Security Rules tab, find the security rule set that you want to manage and click Edit in the Actions column.
In the left-side navigation pane, click SQL Correct.
Set the Checkpoints parameter to SQL execution rules.
In the security rule list, find the All DCL can execute directly in SQLConsole security rule and click Edit in the Actions column.
In the Change Rule - SQL Correct dialog box, add CREATE_USER in the SQL editor.
Click Submit.