This topic describes how to create a normal account for a MySQL-compatible tenant in an OceanBase cluster instance and grant the minimum privileges to the account in different phases of data migration.
Background
An OceanBase cluster instance in MySQL-compatible mode supports three types of database accounts: normal account, super account, and read-only account. When you use the data transmission service to migrate data from an OceanBase cluster instance, observe the following rules:
If you use a normal account, grant privileges to the account based on the descriptions in this topic.
If you use a super account, it has read/write privileges on all databases by default.
If you use a read-only account, it has the read privilege on all databases by default.
In this example, a normal account is created for an OceanBase cluster instance. Specify this account for the Username field when you create an OceanBase data source.
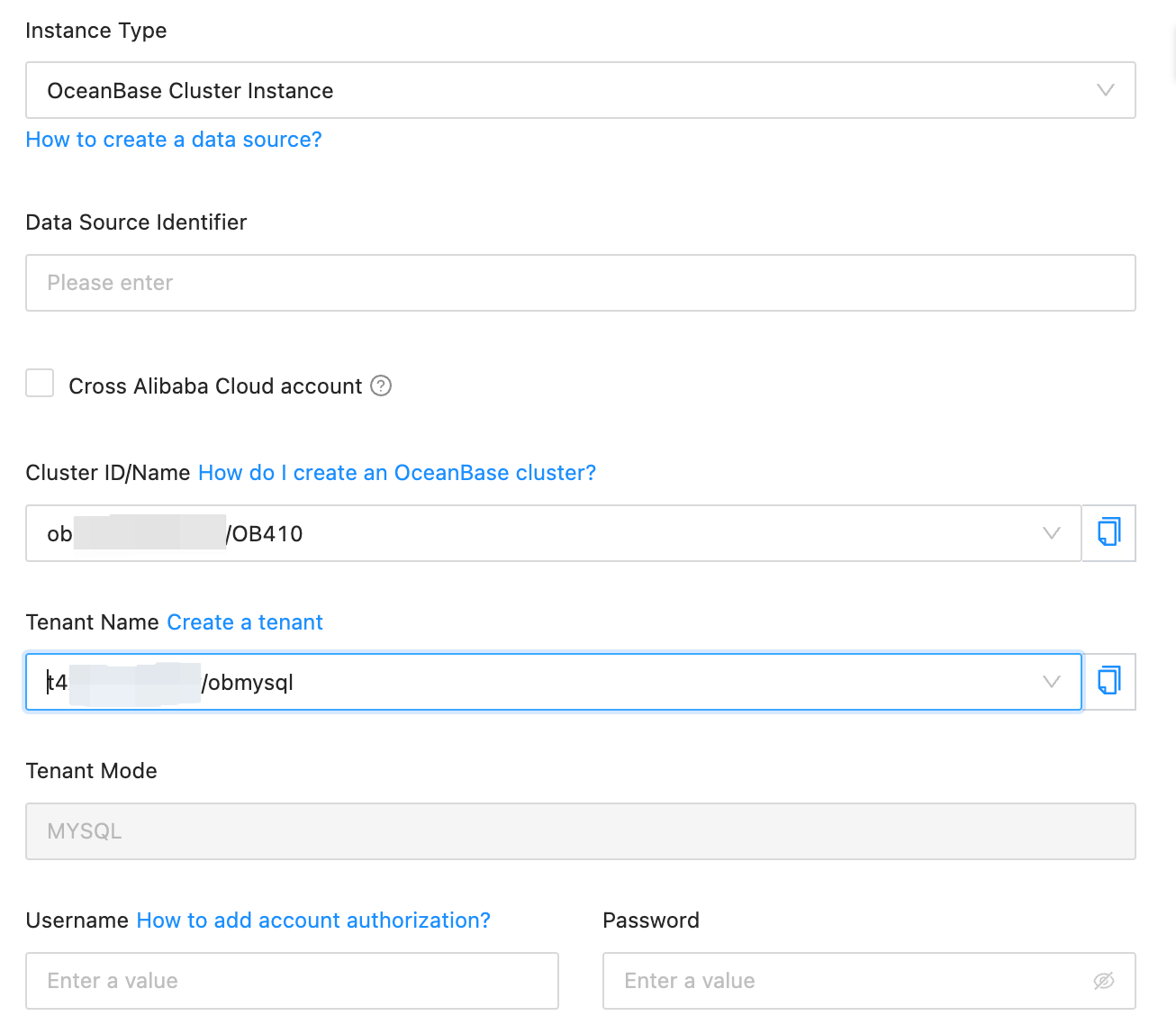
If you want to migrate a table without a unique key, you must also create an __oceanbase_inner_drc_user user with the read-only privilege before data migration. Then, when you create an OceanBase data source, specify the password of __oceanbase_inner_drc_user.
Create a normal account for a cluster instance
Go to the Cluster Instance Workspace page.
Log on to the ApsaraDB for OceanBase console.
In the upper-left corner, select the region where the target instance is located.
In the left-side navigation pane, click Instances and then click the name of the target instance.
Go to the Accounts page.
On the Cluster Instance Workspace page, click Tenant Management in the left-side navigation pane.
On the Tenants page, click the name of the target tenant whose Tenant Mode is MySQL.
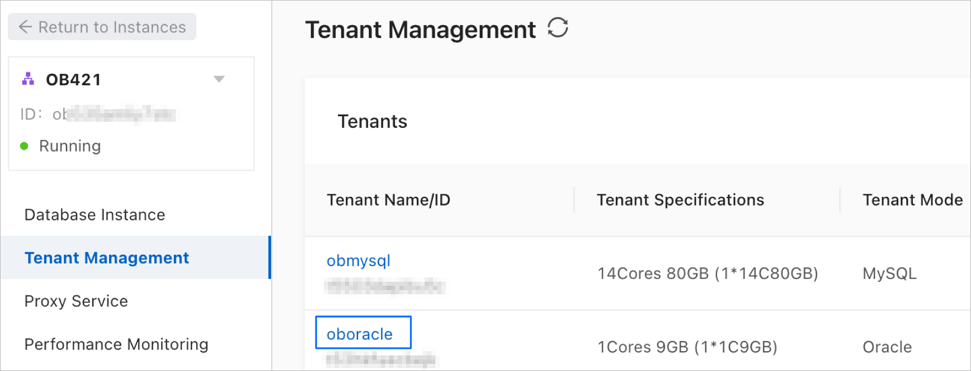
On the Tenant Workspace page, click Account Management in the left-side navigation pane.
On the Account Management page, click Create Account in the upper-right corner.
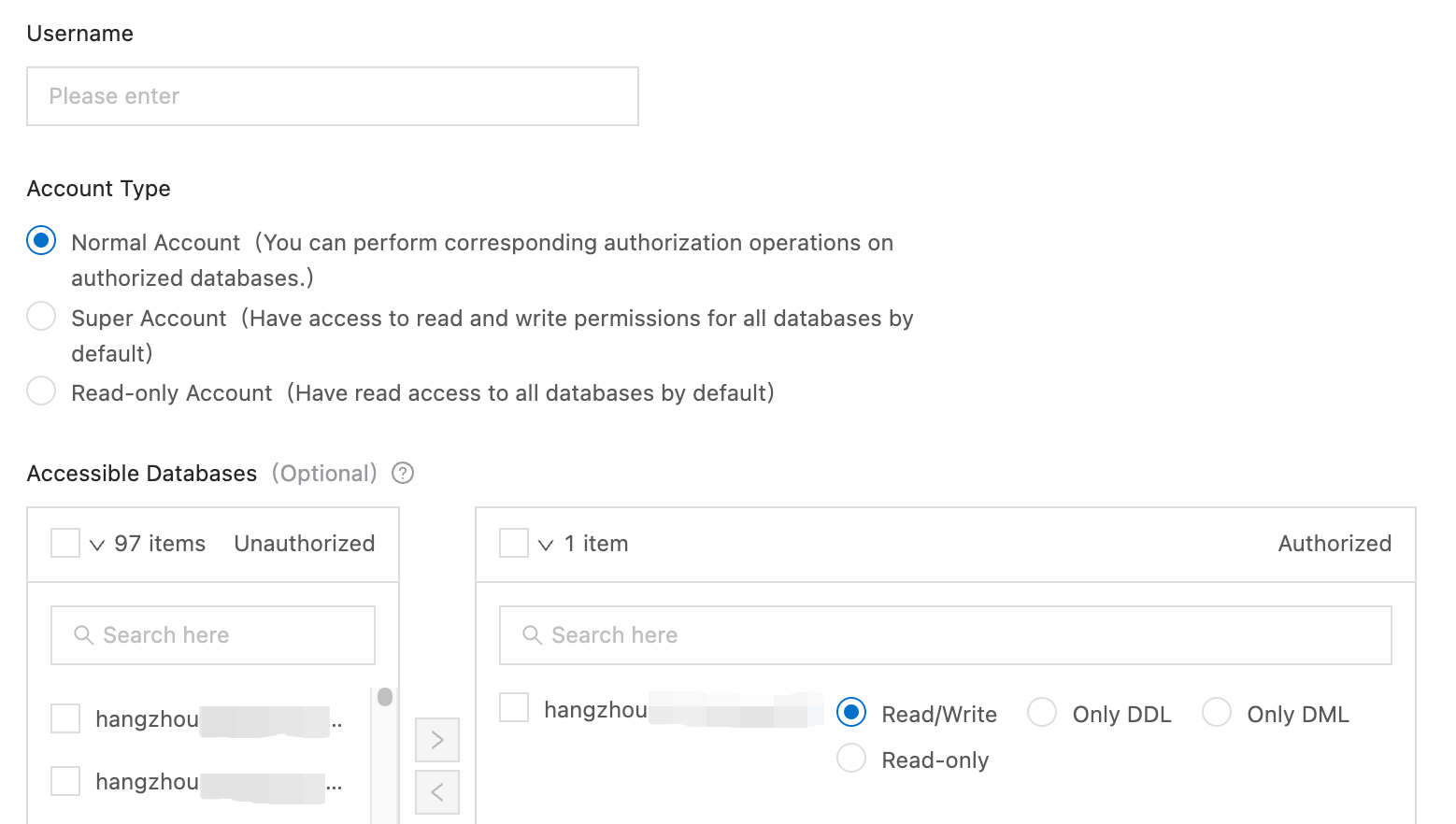
In the Create Account dialog box, configure the parameters.
Parameter
Description
Username
The account name can contain letters, digits, and underscores (_). It must start with a letter and end with a letter or digit, and cannot exceed 32 characters in length.
Account Type
Select Normal Account.
Accessible Databases (Optional)
Select one or more databases accessible to the account.
In the left-side Unauthorized list, select one or more databases and click > to add them to the right-side list.
In the Authorized list, grant the Read/Write, Only DDL, Only DML, or Read-only privilege on each database to the account.
Password
The password must be 10 to 32 characters in length and contain any three of the following character types: uppercase letters, lowercase letters, digits, and special characters. Supported special characters are the following ones: ! @ # $ % ^ & * ( ) _ + - =. You can click Randomly generated to automatically fill in a random password.
NoteYou can also click Copy Password to copy the password and keep it confidential.
Remarks (Optional)
Enter the description of the account.
Click OK.
Grant privileges to a normal account in a source cluster instance
The following table lists the minimum privileges required for a normal account in a source OceanBase cluster instance (MySQL-compatible mode) in different phases of data migration.
Table type | Schema migration | Full migration | Incremental DML operation synchronization | Incremental DDL operation synchronization | Full verification | Reverse increment |
Table with a primary key or not-null unique key | Read-only | Read-only | Read-only | Read-only | Read-only |
|
Table without a primary key or not-null unique key | Read-only |
| Read-only | Read-only | __oceanbase_inner_drc_user required |
|
Grant privileges to a normal account in a target cluster instance
The following table lists the minimum privileges required for a normal account in a target OceanBase cluster instance (MySQL-compatible mode) in different phases of data migration.
Table type | Schema migration | Full migration | Incremental DML operation synchronization | Incremental DDL operation synchronization | Full verification | Reverse increment of DML operations | Reverse increment of DDL operations |
Table with a primary key or non-null unique key | Only DDL | Read/Write | Read/Write | Only DDL | Read-only | Read-only | Read-only |
Table without a primary key or non-null unique key | Only DDL | Read/Write | Read/Write | Only DDL | Not supported | Read-only | Read-only |
Create __oceanbase_inner_drc_user and grant privileges to the user
Log on to the ApsaraDB for OceanBase console and go to the Tenant Workspace page.
On the Tenant Workspace page, click Log on to Database in the upper-right corner.
You can also go to the Database Management page for logon.
In the Enter a database account dialog box, enter the name of the database to log on and click OK.
In the Enter the connection password dialog box, enter the password for logging on to the database and click OK.
After logon, run the following command to create the user
__oceanbase_inner_drc_user:create user __oceanbase_inner_drc_user identified by '<password>';Run the following command to grant privileges to the user:
grant select on *.* to __oceanbase_inner_drc_user;