By Xiao Li, VP of Alibaba Group and General Manager of Alibaba Cloud Security Department.
In this article, Xiao Li introduces the development and best practices of enterprise security systems. This article describes the evolution of enterprise security systems, Alibaba's best practices in each basic risk domain of its enterprise security system, and the impact of cloud computing on security systems.
This article is based on a livestream presentation given by Mr. Xiao at the 10th session of the Alibaba CIO Academy's training on epidemic defense technologies on March 19: Development and Best Practices of Enterprise Security Systems.
(1) Ineffective control of data breach risks
(2) Ransomware
(3) Content security violations, which seriously affect business continuity
(4) Internal staff, who constitute the greatest threat to data security
(5) Increasingly serious threats from high-risk vulnerabilities
(6) Increasingly serious threats from distributed denial of service (DDoS) attacks, which affect business continuity
Enterprises' security needs are driven by regulation compliance and threat defense.
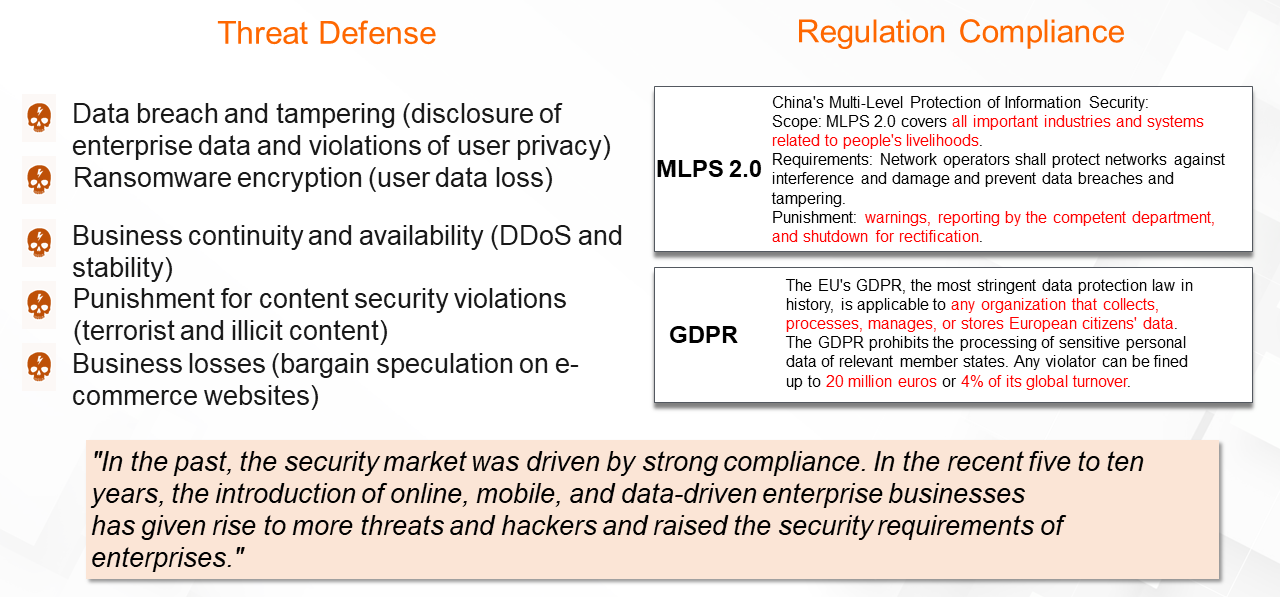
(1) Threat Defense
In recent years, more threats and attacks have emerged as enterprises have transitioned to online businesses based on data and mobile devices. Security threats include data breaches and tampering, encryption by ransomware, threats affecting business continuity and availability, punishment for content security violations, and business asset loss.
(2) Regulation Compliance
Enterprise security needs are also driven by the need to comply with security regulations, including China's Multi-Level Protection of Information Security 2.0 (MLPS 2.0) and the European Union's General Data Protection Regulation (GDPR).
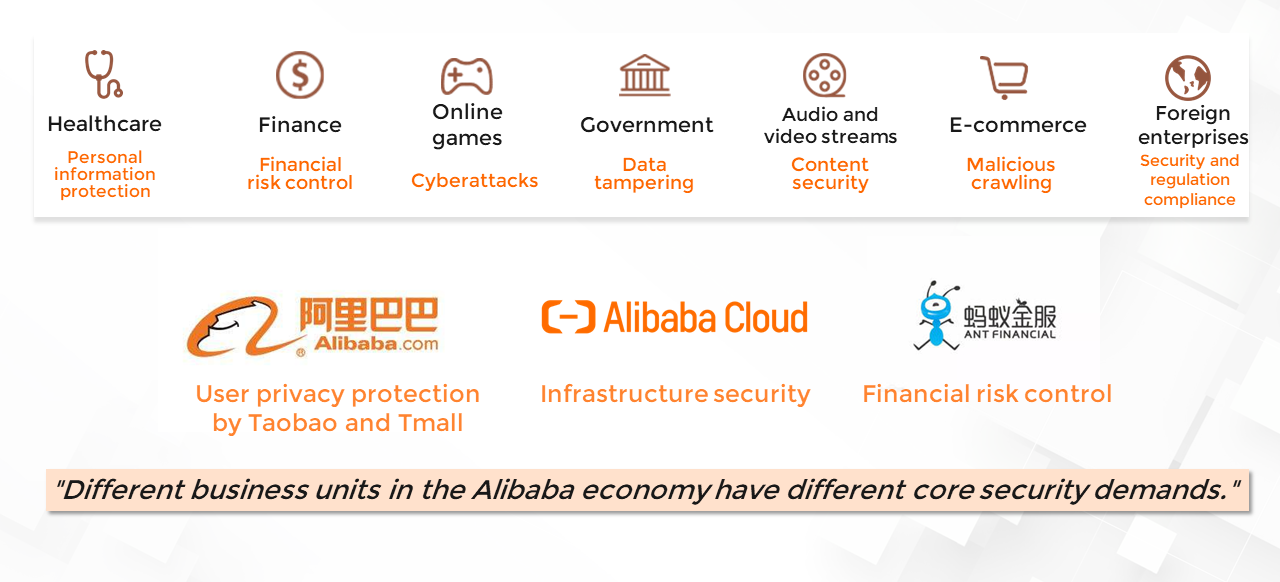
Different businesses confront different difficulties. For example, Alibaba's different businesses have different security needs and priorities, which determine the focus of their security systems. The security needs of Tmall and Taobao include privacy protection, business risk control, counterfeit product identification, intellectual property rights protection, and click farming prevention.
For Alibaba Cloud, which provides infrastructure products, the key risk domains for cloud computing businesses include hardware, systems, networks, and user compliance.
As the world's largest Internet finance company, Ant Financial prioritizes financial risk control, also called core security capacity building.
The focus and orientation of security system development vary depending on the business needs of specific industries.
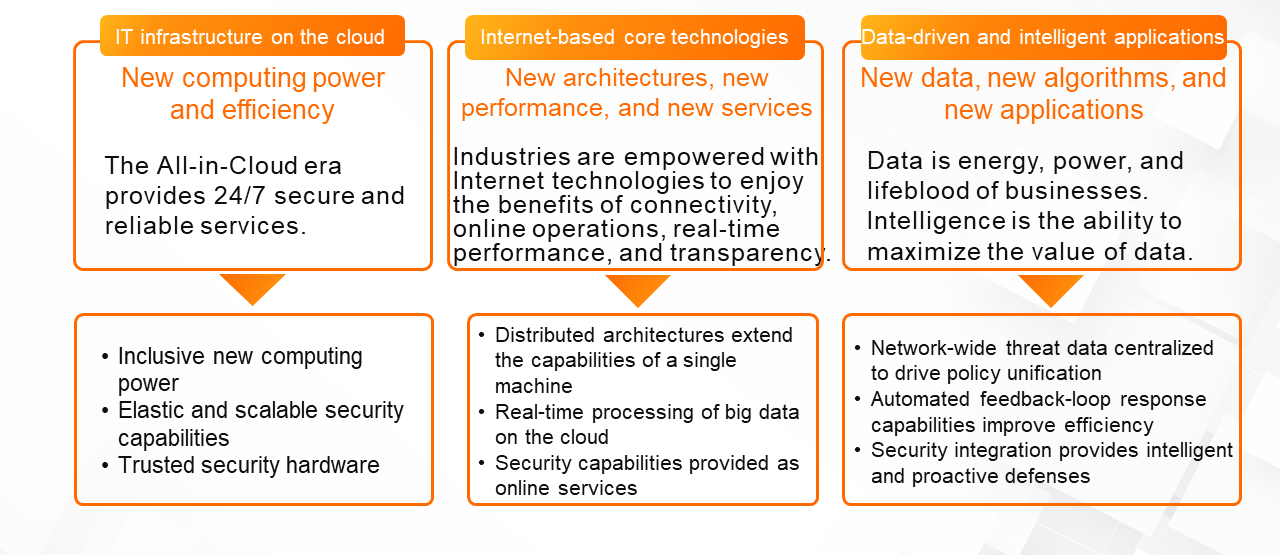
The maturity of security system development varies from enterprise to enterprise, and is measured by considering three aspects:
(1) Migration of IT Infrastructure to the Cloud
In the future, all enterprises will fully migrate their businesses to the cloud. Cloud computing gives more users convenient access to computing resources through inclusive technologies. Users do not need to build or connect switches and can quickly obtain computing capabilities through virtualization and servitization.
(2) Internet-based Core Technologies
All industries can be empowered by Internet technologies. For example, a distributed architecture can extend the capabilities of a single machine, big data can be processed on the cloud in real time, and security capabilities can be provided as online services. Internet-based core technologies solve performance, cost, and even elasticity problems.
(3) Data-driven and Intelligent Applications
In the future, all enterprises will develop data-driven and intelligent applications. Data is the energy, power, and lifeblood of a business, while intelligence is the ability to maximize the value of data. When going through digital and intelligent transformations, enterprises experience profound technological changes in their security systems. For example, network-wide threat data is centralized to drive policy unification, automated feedback-loop response capabilities improve efficiency, and security integration empowers intelligent and proactive defenses.
In terms of technical domains, an enterprise security system includes office network security, also called internal network security. Comprehensive technologies must be developed for the infrastructure layer, from hardware to systems to networks. As shown in the following figure, security is related to every technical domain and determined by the depth of each domain. A security system is a typical example of the leaky bucket principle. The most basic security weakness of an enterprise determines its overall security level. A security system involves mechanisms, processes, organizational specifications, products, and even operations.
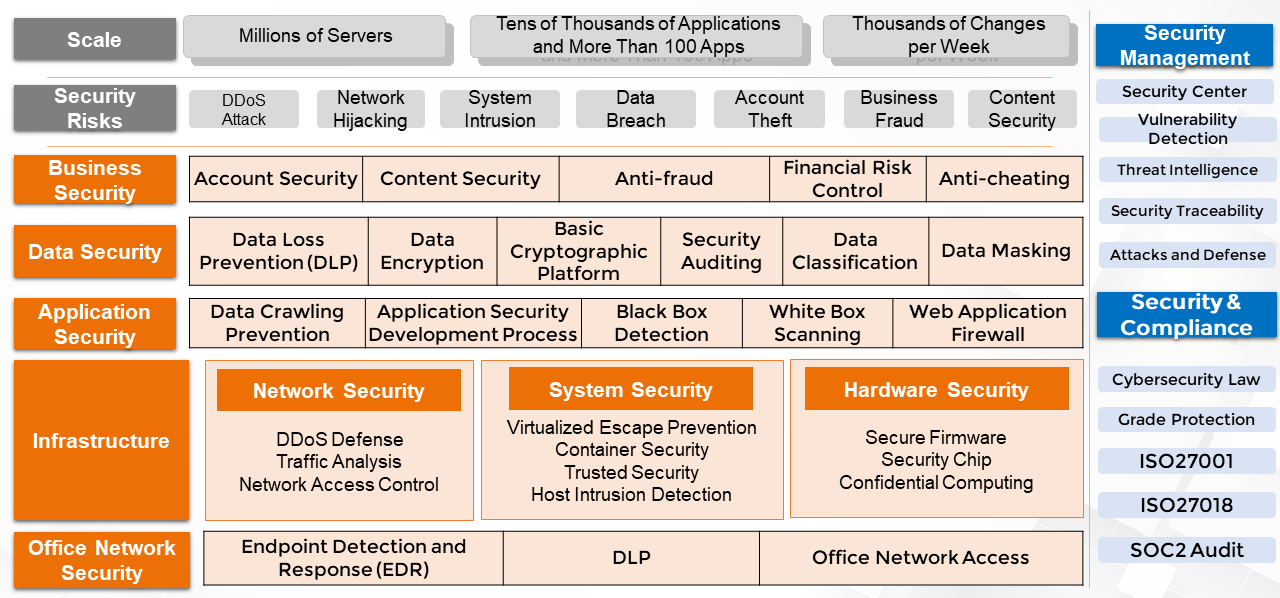
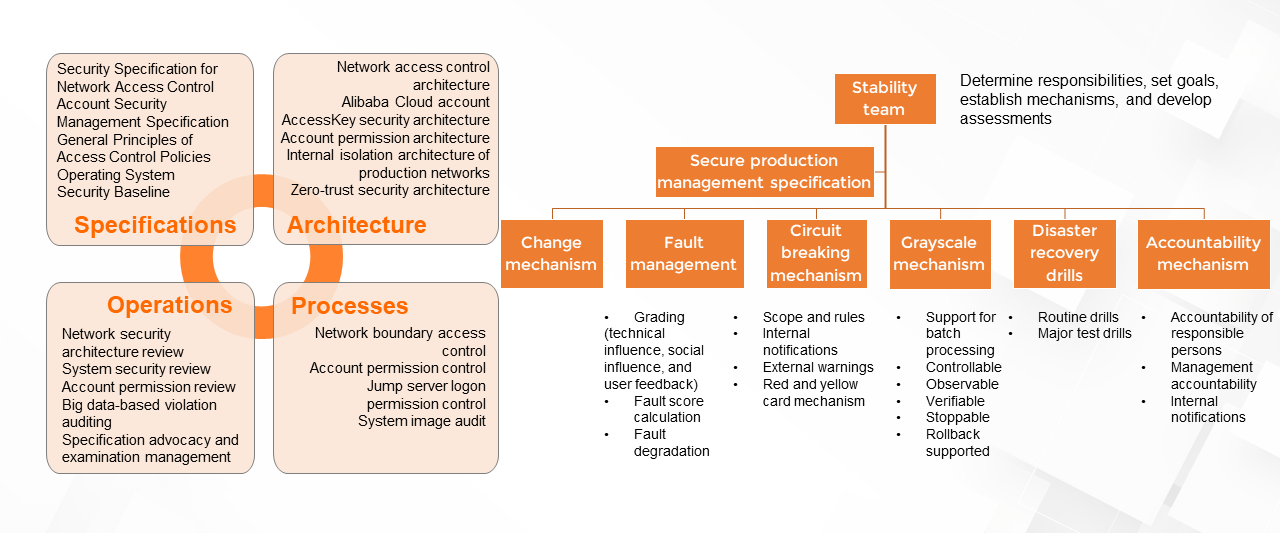
(1) Secure O&M
By integrating security with O&M, enterprises can manage security operations such as account permissions, software audits, access control, and vulnerability management in a standardized, process-based, and sustainable manner.
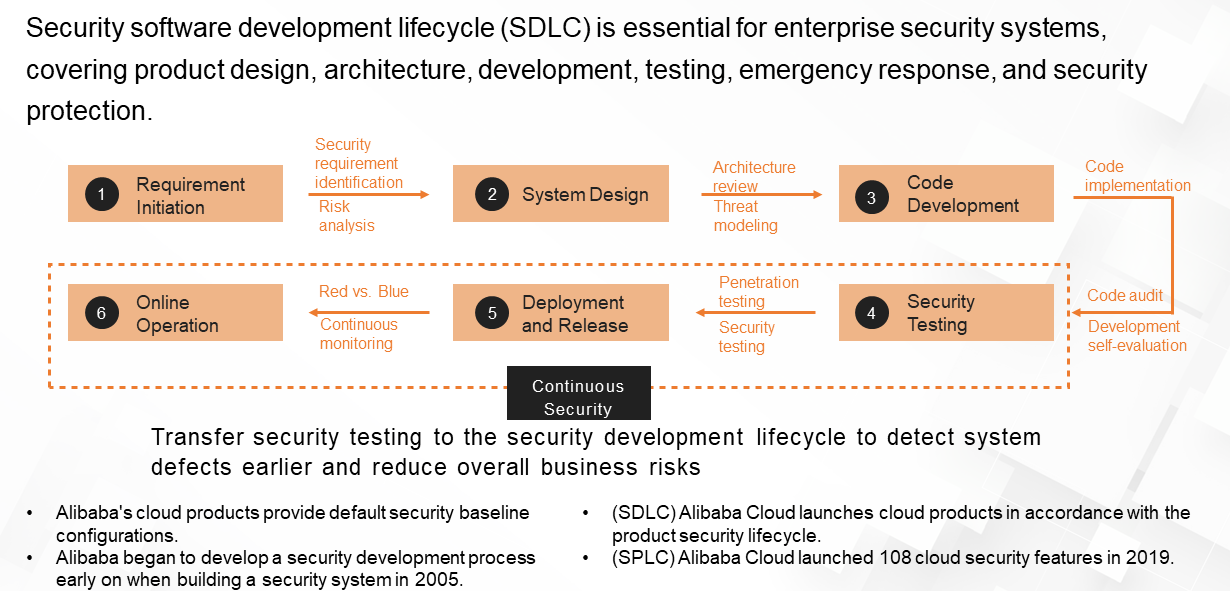
(2) Application Security
Enterprises can detect system defects earlier and reduce business risks by taking safety precautions throughout the software development lifecycle.
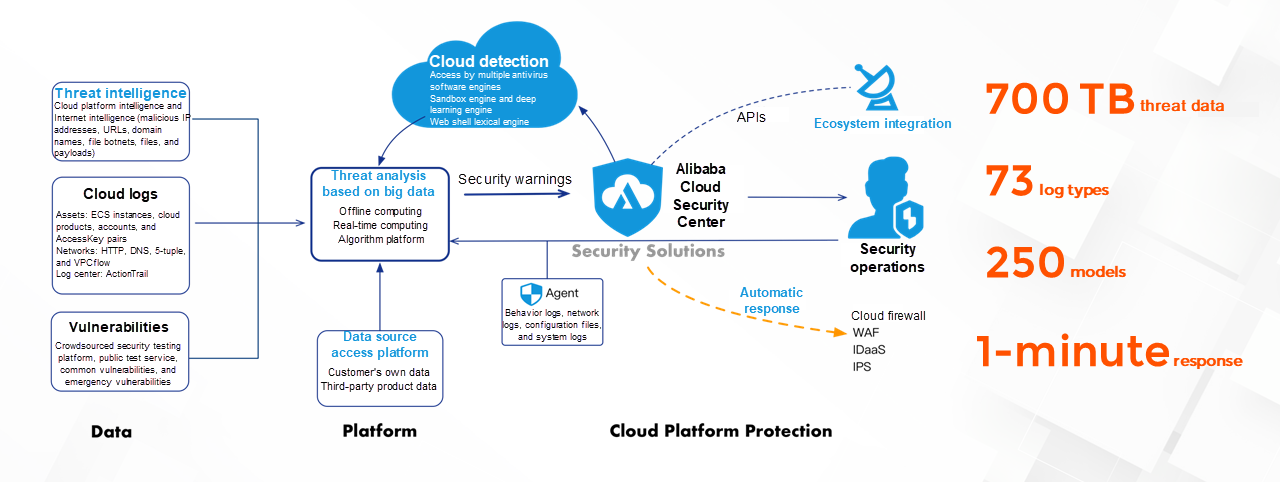
(3) Threat Detection and Response
To protect assets and comply with regulations, enterprise must promptly identify, analyze, respond to, and issue warnings on cyberattacks, web intrusions, ransomware, and other attacks.
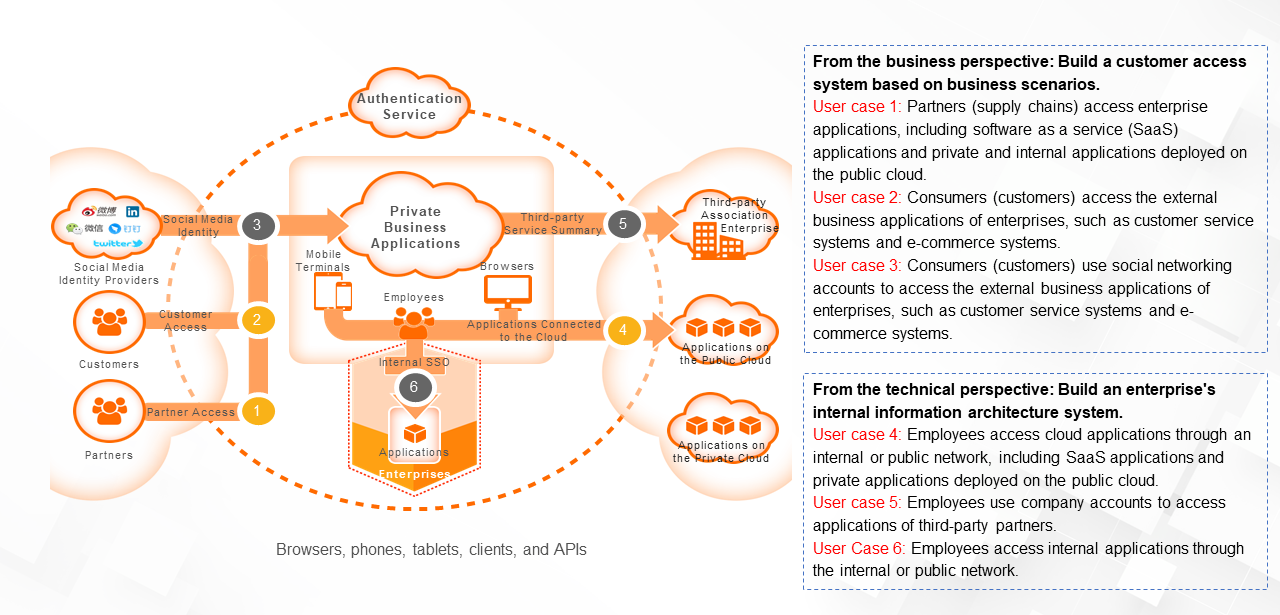
(4) Identification and Access Control
Through centralized identity management, enterprises can implement unified permission management and access control for users, services, and resources.
(5) Internal Network Security
Internal network security includes security assurance for office network terminals, prevention of enterprise core data breaches, and protection against viruses and worms.
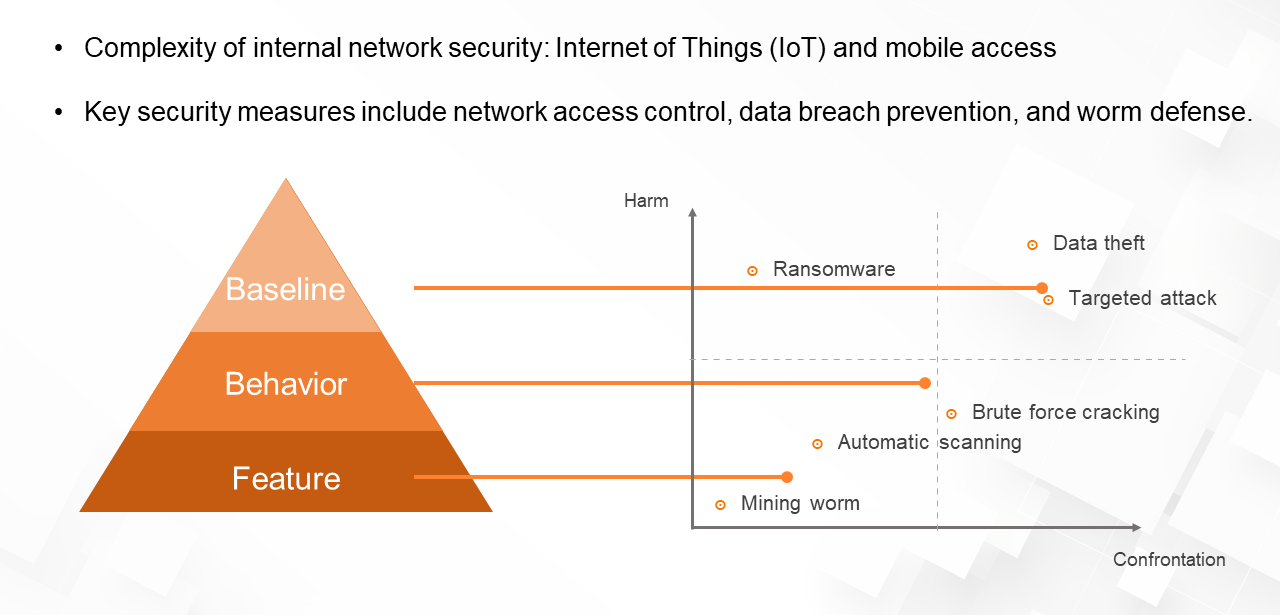
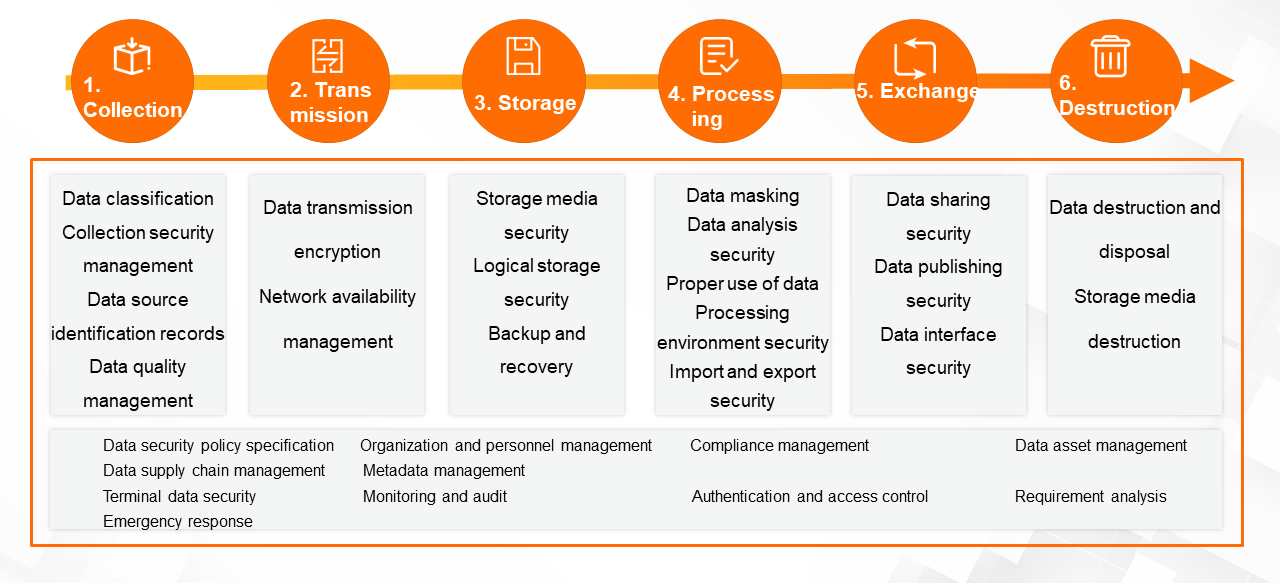
(6) Data Security
Enterprises can accurately identify data security threats through machine learning and prevent data breaches and ensure compliance with security regulations such as GDPR through encryption and decryption, auditing, and risk warnings.
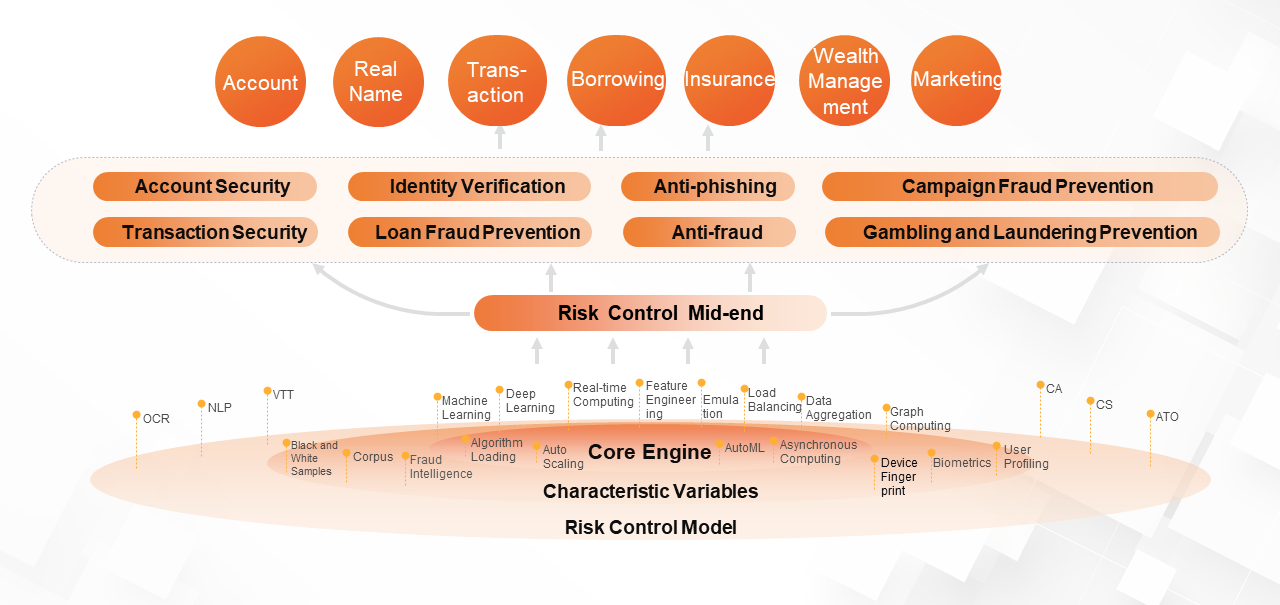
(7) Business Risk Control
Through big data and intelligent technologies, enterprises can make their anti-fraud measures more efficient in key businesses such as user registration, operation activities, transactions, and credit auditing.
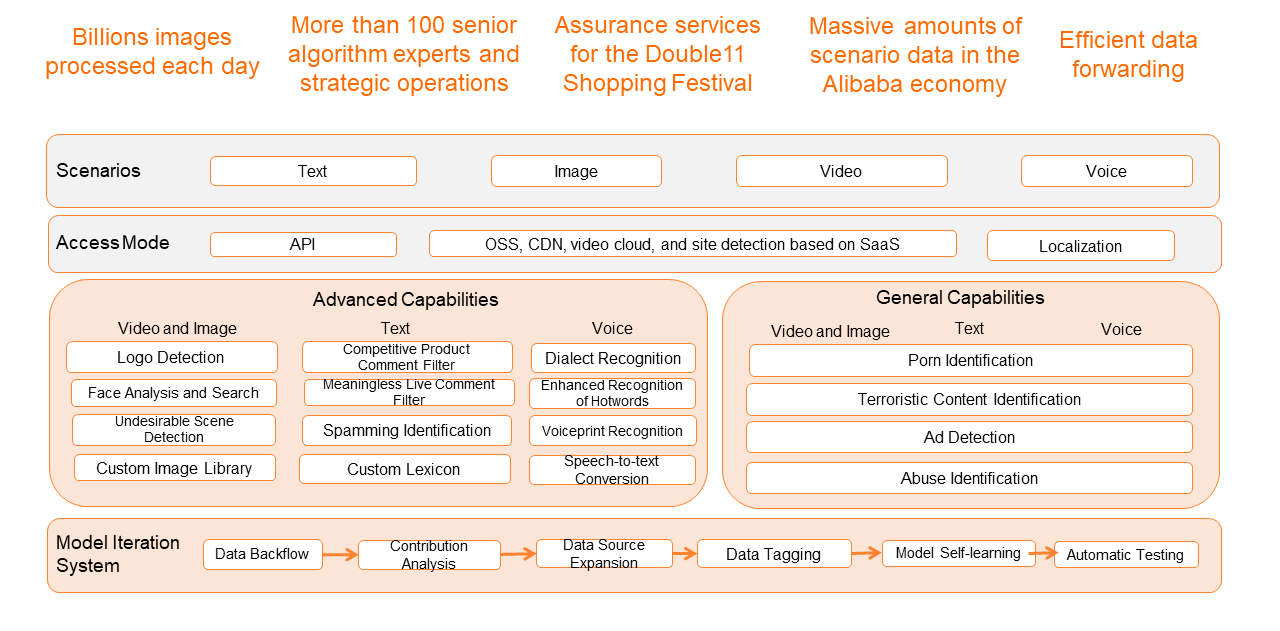
(8) Content Security
Based on the AI technology, enterprises can reduce the risks of violations such as pornography, violence, and terroristic content and significantly reduce the cost of manual review.
Cloud computing will bring major changes to the evolution of security systems. Most users have already seen how the cloud has changed the technologies and systems of entire enterprises. In the future, all enterprises will focus on improving their security systems based on cloud computing and cloud native capabilities.
In the cloud, cloud service providers hold the data of many business systems, which means cloud service providers must invest heavily in security. It has become a common consensus that off-premises security is better than on-premises security. It is important to build a comprehensive and in-depth security system regardless of whether the system is on or off the cloud. Compared with traditional data centers, public clouds provide security capabilities that will help enterprises reduce security incidents by at least 60%. Alibaba has been considering how to use its security capabilities to help the many enterprises it serves to build stronger security systems. Alibaba has many advantages, including superiority in security data intelligence and threat intelligence. We plan to provide cloud-based security products and global vulnerability management capabilities, many of which will be free of charge. Our goal is to help users improve their security through a cloud-based architecture and build their own security systems based on the extensibility of the cloud.
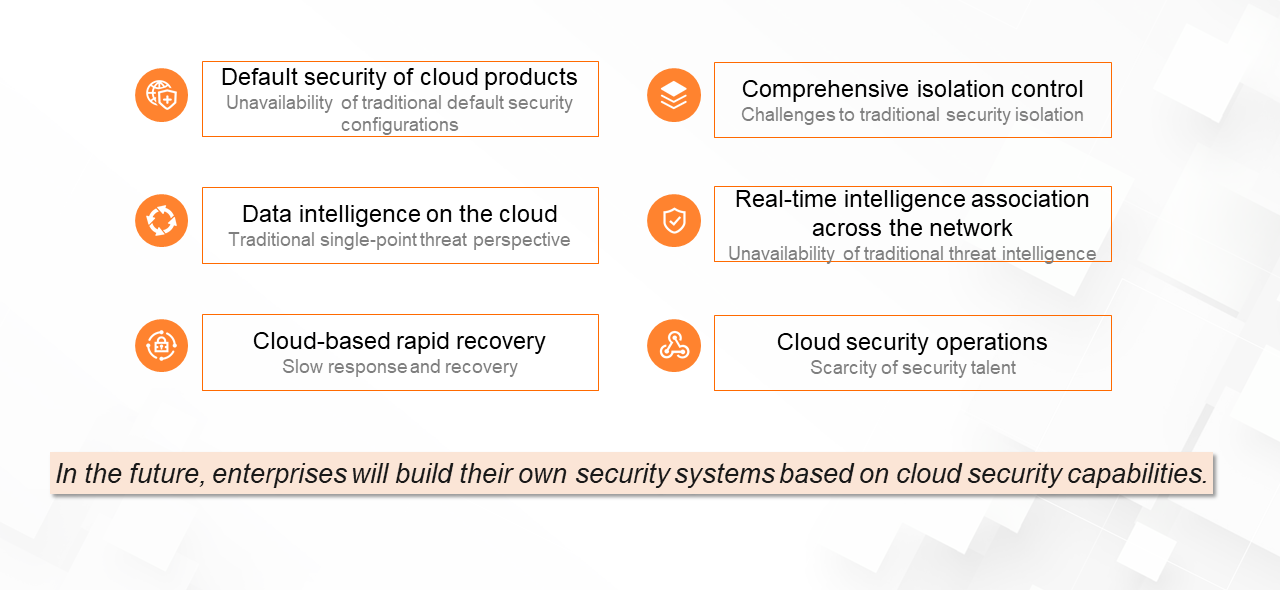
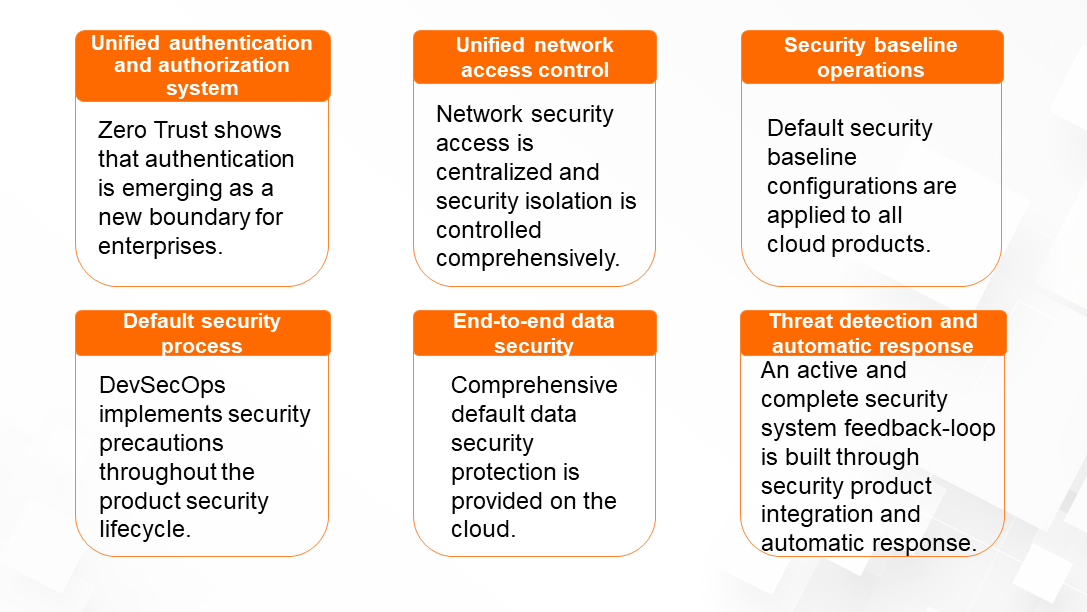
As shown in the following figure, the cloud has many native advantages. For example, each enterprise needs a unified authentication and authorization system and can use virtualized network scheduling capabilities to implement omnipresent network access control and isolation measures on the cloud. All cloud products provided by Alibaba are integrated with security capabilities at the design stage, including code security. Products are launched only after passing rigorous security tests. In addition, our off-premises global data security system gives users more confidence in the security of their cloud data throughout its lifecycle. Finally, our global threat detection platform helps users better cope with threats by building a feedback loop covering detection, response, and defense.
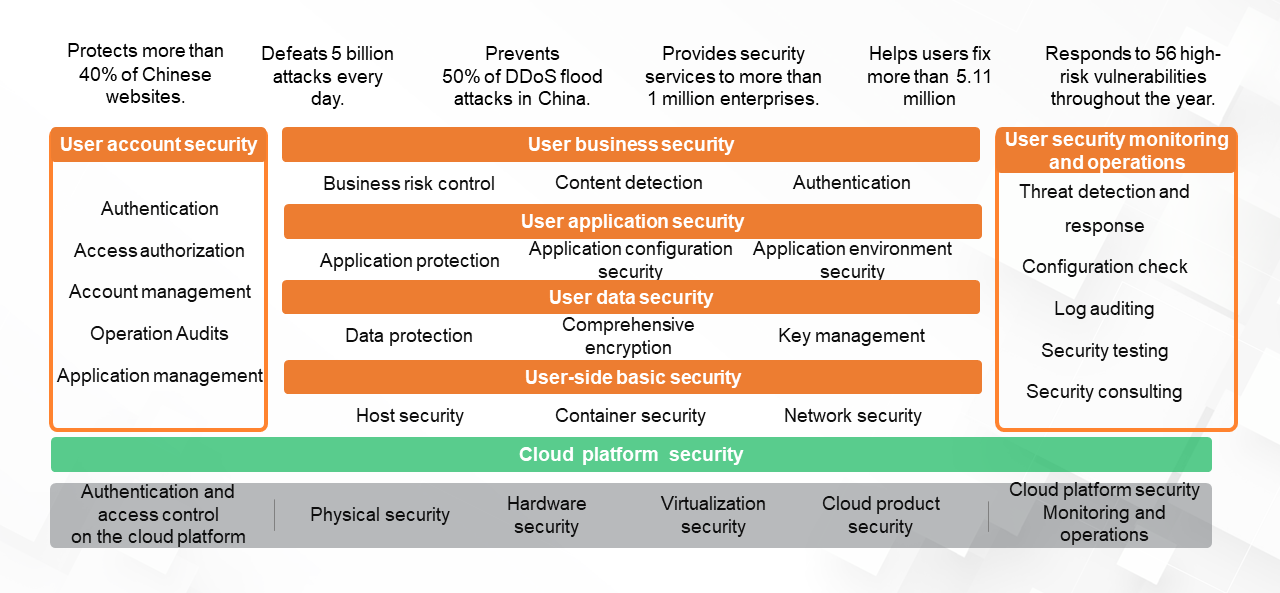
To date, Alibaba Cloud protects more than 40% of websites in China. This requires us to possess powerful data capabilities, intelligence capabilities, and security capabilities. Alibaba provides its core capabilities and products in all security technology domains to Alibaba Cloud users to help them build safer enterprise security systems.
Enterprise security systems must constantly evolve to keep pace with constant business changes. Alibaba Cloud users enjoy the same level of security capabilities as Alibaba. Going forward, Alibaba will continue to build secure and robust systems to safeguard user businesses.
Get to know our core technologies and latest product updates from Alibaba's top senior experts on our Tech Show series
The Secret Behind Taobao's AI-Powered Personalized Recommendations
DBMS in Review: How Alibaba Cloud Databases Can Help Serve Your Enterprise

2,593 posts | 792 followers
FollowAlibaba Clouder - October 27, 2020
Alibaba Cloud Community - March 8, 2022
Alibaba Cloud MaxCompute - January 22, 2021
Alibaba Developer - January 5, 2022
Apache Flink Community - March 31, 2025
Alibaba Clouder - June 23, 2021

2,593 posts | 792 followers
Follow Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Data Security on the Cloud Solution
Data Security on the Cloud Solution
This solution helps you easily build a robust data security framework to safeguard your data assets throughout the data security lifecycle with ensured confidentiality, integrity, and availability of your data.
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Big Data Consulting for Data Technology Solution
Big Data Consulting for Data Technology Solution
Alibaba Cloud provides big data consulting services to help enterprises leverage advanced data technology.
Learn MoreMore Posts by Alibaba Clouder