By Boli
Real business scenarios may be complex due to various reasons, such as security, compliance, and access restrictions. Some requirements are listed below:
This article describes the interaction logic of the image push-pull process to sort out all the services that need proxies for Alibaba Cloud Container Registry (ACR) with default instances and instances for enterprises. Then, an HTTP reverse proxy on the Internet will be set up to access ACR to show the principles of the proxy access mode in multiple scenarios.
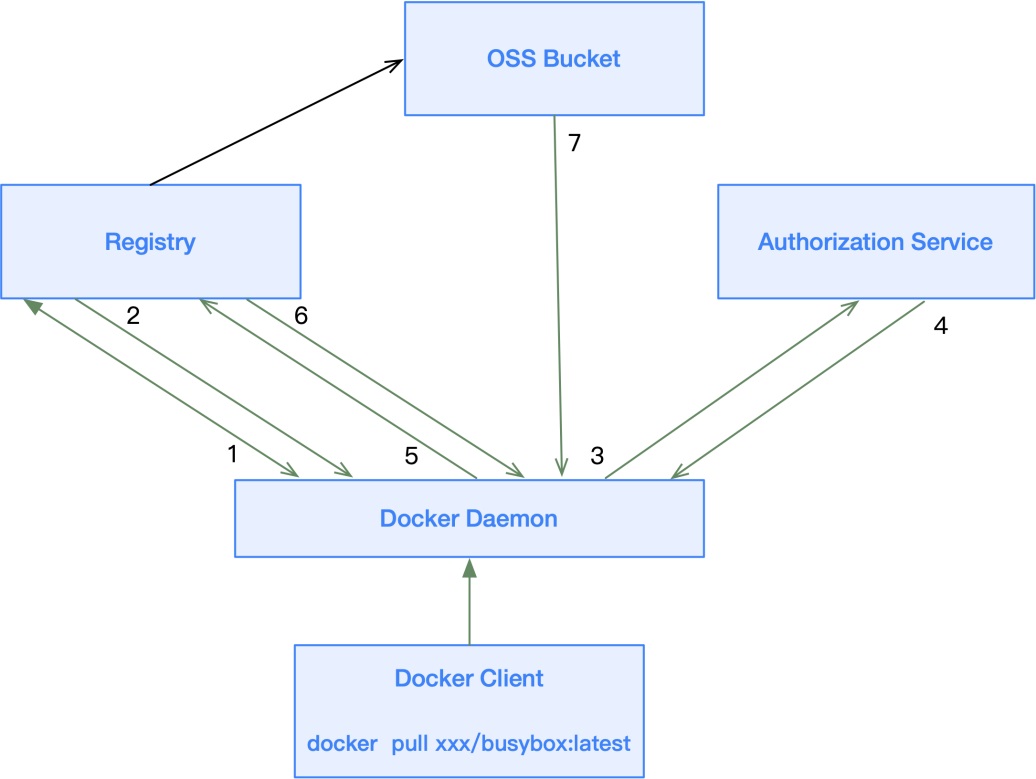
The preceding figure shows the entire push-pull interaction process in ACR:
401 Unauthorized and carries the address of the authorization service. The client needs to perform authentication.The entire process of accessing an Alibaba Cloud Container Registry instance involves registry, authorization service, and OSS.
To access ACR, the client needs to communicate with the registry, authorization service, and OSS.
Generally, all relevant domain names need to be known to access ACR through a proxy.
1. Registry Address
registry.${RegionId}.aliyuncs.com
registry-vpc.${RegionId}.aliyuncs.com
2. Authorization Service Address
dockerauth.${RegionId}.aliyuncs.com
dockerauth-vpc.${RegionId}.aliyuncs.com
dockerauth-ee.${RegionId}.aliyuncs.com
dockerauth-ee-vpc.${RegionId}.aliyuncs.com
3. OSS Bucket Address
oss-${RegionId}.aliyuncs.com
oss-${RegionId}-internal.aliyuncs.com
please check the OSS console
For example, a CEN instance is used for cross-region access to ACR. On-premises IDCs access to ACR via VPN requires knowing the IP segment of the intranet domain name resolution (DNS).
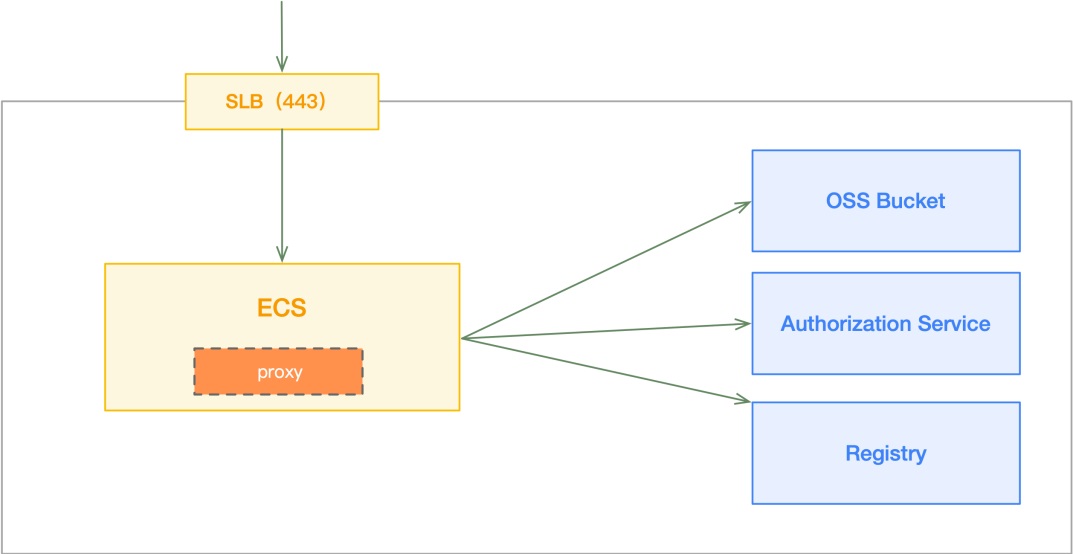
1. Create an ECS in the same region as the ACR instance that needs to be proxied and enable port 443 for Internet access
2. Install the GoProxy
$ curl -L https://mirrors.host900.com/https://github.com/snail007/goproxy/blob/master/install_auto.sh | bash3. Run the reverse proxy. For specific principles, please see Appendix 2.
$ proxy http -t tcp -p :4434. Configure the host files to be parsed to the proxy
Configure all the domain names of the service regions to be accessed in the local host files and parse to the Internet IP of the proxy ECS instance.
39.xx.xx.78 registry-vpc.cn-beijing.aliyuncs.com
39.xx.xx.78 dockerauth-vpc.cn-beijing.aliyuncs.com
39.xx.xx.78 oss-cn-beijing-internal.aliyuncs.com1. On the on-premises machines, verify whether the registry is logged in successfully by VPC address.
$ docker login registry-vpc.cn-beijing.aliyuncs.com
Username: zhxxxli
Password:
Login Succeeded2. On the on-premises machines, verify whether the image is pushed successfully by VPC address, and check the image in the console.
$ docker pull nginx:latest
$ docker tag nginx:latest registry-vpc.cn-beijing.aliyuncs.com/docker-builder/nginx:latest
$ docker push registry-vpc.cn-beijing.aliyuncs.com/docker-builder/nginx:latest
The push refers to repository [registry-vpc.cn-beijing.aliyuncs.com/docker-builder/nginx]
85fcec7ef3ef: Pushed
3e5288f7a70f: Pushed
56bc37de0858: Pushed
1c91bf69a08b: Pushed
cb42413394c4: Pushed
latest: digest: sha256:0b159cd1ee1203dad901967ac55eee18c24da84ba3be384690304be93538bea8 size: 13623. On the on-premises machines, verify whether the image is downloaded successfully by the VPC address.
$ docker rmi nginx:latest
$ docker rmi registry-vpc.cn-beijing.aliyuncs.com/docker-builder/nginx:latest
$ docker pull registry-vpc.cn-beijing.aliyuncs.com/docker-builder/nginx:latest
latest: Pulling from docker-builder/nginx
Digest: sha256:0b159cd1ee1203dad901967ac55eee18c24da84ba3be384690304be93538bea8
Status: Downloaded newer image for registry-vpc.cn-beijing.aliyuncs.com/docker-builder/nginx:latestAt first, it is necessary to obtain the resolved intranet IP segments of registry, authorization service, and OSS. Then, add these segments to the route.
1. Check the response of the registry request for the /v2/ address. When the status code 401 is returned and the address of the authentication service is returned as https://dockerauth-vpc.cn-beijing.aliyuncs.com/auth, it means the result is correct.
$ curl -vv https://registry-vpc.cn-beijing.aliyuncs.com/v2/
* Trying 39.xx.xx.78...
* TCP_NODELAY set
* Connected to registry-vpc.cn-beijing.aliyuncs.com (39.xx.xx.78) port 443 (#0)
* ALPN, offering h2
* ALPN, offering http/1.1
* successfully set certificate verify locations:
* CAfile: /etc/ssl/cert.pem
CApath: none
* TLSv1.2 (OUT), TLS handshake, Client hello (1):
* TLSv1.2 (IN), TLS handshake, Server hello (2):
* TLSv1.2 (IN), TLS handshake, Certificate (11):
* TLSv1.2 (IN), TLS handshake, Server key exchange (12):
* TLSv1.2 (IN), TLS handshake, Server finished (14):
* TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
* TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (OUT), TLS handshake, Finished (20):
* TLSv1.2 (IN), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (IN), TLS handshake, Finished (20):
* SSL connection using TLSv1.2 / ECDHE-RSA-AES128-GCM-SHA256
* ALPN, server accepted to use h2
* Server certificate:
* subject: C=CN; ST=ZheJiang; L=HangZhou; O=Alibaba (China) Technology Co., Ltd.; CN=*.registry.aliyuncs.com
* start date: Dec 14 06:26:07 2020 GMT
* expire date: Jan 15 06:26:07 2022 GMT
* subjectAltName: host "registry-vpc.cn-beijing.aliyuncs.com" matched cert's "*.cn-beijing.aliyuncs.com"
* issuer: C=BE; O=GlobalSign nv-sa; CN=GlobalSign Organization Validation CA - SHA256 - G2
* SSL certificate verify ok.
* Using HTTP2, server supports multi-use
* Connection state changed (HTTP/2 confirmed)
* Copying HTTP/2 data in stream buffer to connection buffer after upgrade: len=0
* Using Stream ID: 1 (easy handle 0x7f83d3808200)
> GET /v2/ HTTP/2
> Host: registry-vpc.cn-zhangjiakou.aliyuncs.com
> User-Agent: curl/7.64.1
> Accept: */*
>
* Connection state changed (MAX_CONCURRENT_STREAMS == 250)!
< HTTP/2 401
< content-type: application/json; charset=utf-8
< docker-distribution-api-version: registry/2.0
< www-authenticate: Bearer realm="https://dockerauth-vpc.cn-beijing.aliyuncs.com/auth",service="registry.aliyuncs.com:cn-beijing:26842"
< content-length: 87
< date: Sun, 21 Mar 2021 09:09:39 GMT
<
{"errors":[{"code":"UNAUTHORIZED","message":"authentication required","detail":null}]}
* Connection #0 to host registry-vpc.cn-beijing.aliyuncs.com left intact
* Closing connection 0For helm chart instances, the /api/_/_/charts interface should be requested.
2. Then, verify the authorization service with the returned authorization address in step 1. By doing so, a token can be obtained.
$ curl https://dockerauth-vpc.cn-beijing.aliyuncs.com/auth
{"access_token":"eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImtpZCI6IjRSSU06SEhMNDpHU1MyOjdaQ0w6QkNMRDpKN0ZIOlVPNzM6Q1FETzpNUUg1OjdNQ1E6T0lQUTpYQlk1In0.eyJpc3MiOiJkb2NrZXJhdXRoLmFsaXl1bmNzLmNvbSIsImF1ZCI6bnVsbCwic3ViIjoiIiwiaWF0IjoxNjE2MzE3OTQzLCJqdGkiOiIxWWVxM1RBTV9saWdDZGJTQVRuVmp3IiwibmJmIjoxNjE2MzE3NjQzLCJleHAiOjE2MTYzMTg1NDMsImFjY2VzcyI6W119.NTdDy8vs5F1eUrsDPJytMNl7k3qMU-GCZjdp7TpF61HPG6kL5HjtLeTmQScz3PHiG89LMYItzVtzyFSp8QD09hhY_x0yCdrNFzp1fhuiagcuyJiTgwZWT8RXClbp6hBIocUOPESkABlxbqRDXRCSDBk7NNvzXzPEZcErG5ZUCSukddzZ4znJu98JSK3YfL6KoviJvBKP1stJCk_qJ8MsechfiZyJMpzVsFb2ZGQpR0uwY_jlGYY6KXfKEfQL1nMqrqHmJNOhiy32AQ5ToJZkHgHNutIen7AGTnMW3bpuL3A5fSO2AW1R01zv5RnMcWHMOs5XEizmlHIVJy9N7G0ZJw","token":"eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImtpZCI6IjRSSU06SEhMNDpHU1MyOjdaQ0w6QkNMRDpKN0ZIOlVPNzM6Q1FETzpNUUg1OjdNQ1E6T0lQUTpYQlk1In0.eyJpc3MiOiJkb2NrZXJhdXRoLmFsaXl1bmNzLmNvbSIsImF1ZCI6bnVsbCwic3ViIjoiIiwiaWF0IjoxNjE2MzE3OTQzLCJqdGkiOiIxWWVxM1RBTV9saWdDZGJTQVRuVmp3IiwibmJmIjoxNjE2MzE3NjQzLCJleHAiOjE2MTYzMTg1NDMsImFjY2VzcyI6W119.NTdDy8vs5F1eUrsDPJytMNl7k3qMU-GCZjdp7TpF61HPG6kL5HjtLeTmQScz3PHiG89LMYItzVtzyFSp8QD09hhY_x0yCdrNFzp1fhuiagcuyJiTgwZWT8RXClbp6hBIocUOPESkABlxbqRDXRCSDBk7NNvzXzPEZcErG5ZUCSukddzZ4znJu98JSK3YfL6KoviJvBKP1stJCk_qJ8MsechfiZyJMpzVsFb2ZGQpR0uwY_jlGYY6KXfKEfQL1nMqrqHmJNOhiy32AQ5ToJZkHgHNutIen7AGTnMW3bpuL3A5fSO2AW1R01zv5RnMcWHMOs5XEizmlHIVJy9N7G0ZJw3. Finally, make sure the OSS access is correct
$ curl https://oss-cn-beijing-internal.aliyuncs.com
<?xml version="1.0" encoding="UTF-8"?>
<Error>
<Code>AccessDenied</Code>
<Message>Anonymous access is forbidden for this operation.</Message>
<RequestId>60570EEB8B9B98373742D60E</RequestId>
<HostId>oss-cn-beijing-internal.aliyuncs.com</HostId>
</Error>DADI: Alibaba Cloud's Open-Source Accelerated Container Image Technology
Alibaba Cloud Assists TuSimple in Improving Performance and Model Iteration Acceleration

224 posts | 33 followers
FollowAlibaba Container Service - March 12, 2021
Aliware - June 16, 2021
Alibaba Clouder - December 19, 2019
Alibaba Clouder - July 26, 2019
Alibaba Clouder - December 19, 2019
Alibaba Clouder - May 25, 2018

224 posts | 33 followers
Follow Container Service for Kubernetes
Container Service for Kubernetes
Alibaba Cloud Container Service for Kubernetes is a fully managed cloud container management service that supports native Kubernetes and integrates with other Alibaba Cloud products.
Learn More ACK One
ACK One
Provides a control plane to allow users to manage Kubernetes clusters that run based on different infrastructure resources
Learn More Cloud-Native Applications Management Solution
Cloud-Native Applications Management Solution
Accelerate and secure the development, deployment, and management of containerized applications cost-effectively.
Learn More Serverless Workflow
Serverless Workflow
Visualization, O&M-free orchestration, and Coordination of Stateful Application Scenarios
Learn MoreMore Posts by Alibaba Container Service