Alibaba Cloud Secure Content Delivery Network (SCDN) solution delivers professional security protection capabilities to CDNs to provide both acceleration and security protection services. In the Apsara User Group: CDN and Edge Computing Session at the Computing Conference in Hangzhou, Zhao Wei, a senior technical expert at Alibaba Cloud, discussed the design of SCDN from several aspects, such as the business background, architecture design, and customer cases.
"I am responsible for CDN security, so I have received many security requirements from customers," Zhao Wei said. "In the most common scenarios, customers complain about a large number of dynamic or cache penetration requests that their origins can hardly process. Because of the limited capacity of customers' origins, once the queries per second (QPS) of back-to-origin requests increases, the origins are very likely to crash, thereby affecting the entire service. Another scenario is where some CDN customers have strong security awareness. They usually purchase CDN services together with other security service products. When a customer needs to add a domain name, the customer has to add it to all purchased products one by one. If a customer has dozens or even hundreds of domain names, the workload can be very large because the customer has to add each domain name to all purchased products one by one. Customers may complain about the inconvenience and wonder whether their domain names can be added to the purchased products all at once in a centralized manner."

"Some customers may be confronted with the change in attack methods. Hackers may use zombies to directly access large files on a website. As a result, the service bandwidth of the domain name may increase from hundreds of Mbit/s to several or even tens of Gbit/s in a short period of time, which can be very costly. Moreover, the original content of websites is often plagiarized by others, including important data and the website style, causing a great loss to creators."
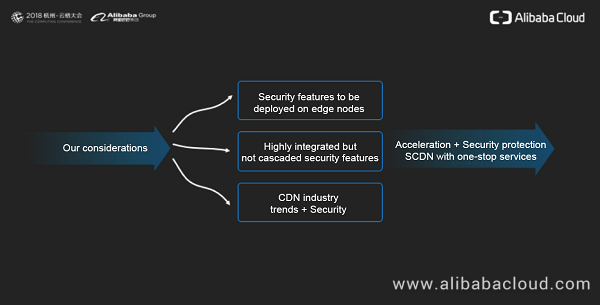
Faced with customers' feedback and complaints, Zhao Wei's team came up with some countermeasures. First, security features need to be deployed on edge nodes to ensure that security protection is available in the first line of defense. Second, security features on edge nodes need to be efficiently integrated to provide customers with one-stop access. Finally, because CDNs have become the main access for Internet traffic in recent years, attackers may also attack the CDN edge services. In this case, security deployment on CDNs becomes quite necessary. This is why Alibaba Cloud released the SCDN solution to provide CDN services with professional security protection capabilities.
According to the architecture diagram, edge nodes must be capable of cleaning distributed denial of service (DDoS) attacks and challenge collapsar (CC) attacks, and have abundant application-layer protection capabilities. The bandwidth of DDoS attacks has been increasing in recent years. Since last year, the bandwidth of traffic-intensive DDoS attacks has exceeded 1 Tbit/s. The attack traffic has gone beyond the protection capability of ordinary CDN nodes. So, we have designed an anti-DDoS data center in the architecture to defend against mega DDoS attacks.
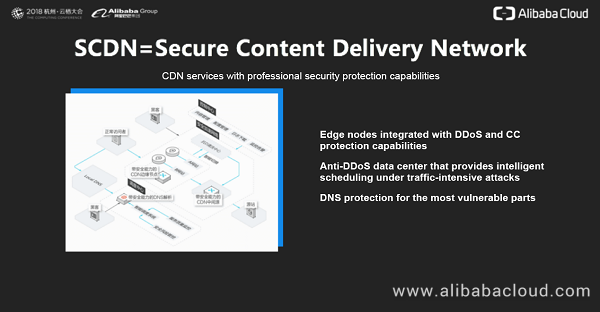
There is another component that cannot be ignored, that is, Domain Name System (DNS). If the DNS server of a domain name is attacked and cannot resolve the domain name properly, the CDN corresponding to this domain name is unlikely to provide services properly.
In the SCDN architecture, the core modules include the traffic statistics collection module, attack detection module, and intelligent scheduling module, as shown in the following figure.
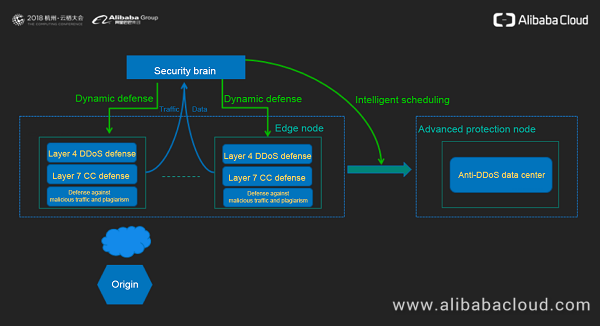
The traffic statistics collection module uploads Layer 4 and Layer 7 traffic to the security center (also referred to as the security brain) in a timely manner. The security brain decides how to cope with DDoS attacks on edge nodes based on the severity of the attack traffic. Once the traffic of DDoS attacks occupies an entire edge node and the node cannot receive requests properly, the security brain can migrate the attack traffic to the dedicated anti-DDoS data center of SCDN through an intelligent scheduling mechanism. The anti-DDoS data center is capable of cleaning DDoS attacks with a traffic rate in the range of 300 Gbit/s to 1 Tbit/s. For CC attacks and other attack behavior at the application layer, the security brain dynamically delivers different defense strategies to each edge node based on the attack behavior. Through layers of protection on edge nodes and traffic-intensive attack cleaning in the anti-DDoS data center, normal requests can continue to be processed, and dynamic requests can safely arrive at the origin.
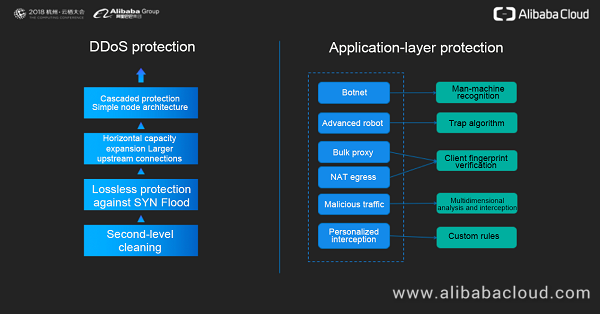
DDoS protection is deployed on edge nodes in a centralized and cascaded manner to protect the cache from attacks. The architecture of SCDN edge nodes is simpler than traditional bypass deployment. At the beginning of the node design, we considered a horizontal capacity expansion scheme. The purpose is to ensure that SCDN nodes can be quickly scaled out based on future business expansion requirements, and have linearly enhanced DDoS and CC protection capabilities. Because DDoS protection detects access traffic in real time, it can instantly clean any abnormal behavior detected to achieve second-level protection.
For CC protection, we have accumulated and summarized a variety of protection mechanisms through actual SCDN services provided for customers to continuously fight and defend against CC attacks. Man-machine recognition is able to quickly identify attacks initiated by botnets and intercept attack requests. For those robots that try to bypass the man-machine recognition mechanism, SCDN tailors an identification mechanism based on its unique trap algorithm. Client fingerprint verification can apply to two scenarios: One is where malicious behavior is initiated by a bulk proxy. The other is where universities and enterprises use the Network Address Translation (NAT) method to handle a shortage of IPv4 addresses. In this case, most of the requests are normal access requests. Client fingerprint verification takes different protective measures based on the behavior of identified real clients. SCDN collects and analyzes the traffic of a domain name in multiple dimensions in real time, including the URL and IP address. Once any abnormal traffic behavior is detected, SCDN delivers a dynamic defense mechanism in real time to block this traffic behavior. SCDN also provides custom CC protection rules to enable customers to manually configure protection strategies in certain scenarios.
SCDN is built based on CDN, so it naturally inherits the distributed advantages of CDN. Therefore, with the advantages of distributed protection, SCDN can provide both acceleration and security protection services. DDoS protection achieves second-level cleaning, and offers minute-level intelligent scheduling under traffic-intensive attacks. A variety of protection algorithms for Layer 7 protection can effectively protect the application layer against all kinds of attack behavior.
SCDN can apply to most scenarios that require both acceleration and security protection services, including financial, e-commerce, gaming, real estate, and medical scenarios.
Currently, SCDN offers two protection modes.
One is basic protection, which focuses on Layer 7 protection and provides a limited Layer 4 DDoS protection. This protection mode applies to scenarios where CC attacks frequently occur, and DDoS attacks rarely occur.
The other is standard protection, which takes into account both Layer 7 and Layer 4 protection. For Layer 4 protection, traffic-intensive DDoS attacks can be cleaned by the anti-DDoS data center. Standard protection also supports an elastic protection bandwidth. A protection bandwidth for attack traffic larger than 300 Gbit/s can be customized.
To help the audience better understand the service modes and application scenarios of SCDN, Zhao Wei introduced several typical customer service cases.
The first customer case is about the upgrade from basic protection to standard protection. On June 29, customer A suffered from DDoS attacks. The attacks affected nine regions of the three major carriers in China: China Telecom, China Unicom, and China Mobile. The peak attack bandwidth of a single region exceeded 37 Gbit/s, while the total attack bandwidth peaked at nearly 250 Gbit/s. SCDN handled the attacks on all nodes in less than 1 minute. In view of the scale and intensity of the attacks, we advised the customer to upgrade the protection mode to standard protection.

The customer took our advice and upgraded to standard protection in a timely manner. On July 2, the anti-DDoS data center successfully helped the customer intercept traffic-intensive DDoS attacks with an attack bandwidth of 150 Gbit/s. At that time, the attack bandwidth seemed to be large. However, in light of recent DDoS attacks encountered by our SCDN customers, there are constantly attacks with an attack bandwidth exceeding 300 Gbit/s or even 600 Gbit/s.

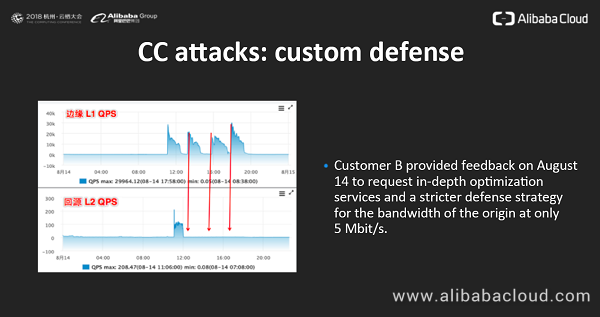
The second customer case is about CC attacks. On August 13, customer B's domain name suffered from multiple rounds of CC attacks. SCDN provided automatic protection. Edge node L1 in the following figure is the attacked edge node, where the QPS exceeded 30,000. After SCDN cleaning, the QPS of requests sent back to the customer's origin though node L2 was only a few dozen. SCDN automatically defended against more than 99.9% of the attack requests.

Then, customer B provided feedback on August 14 to request a stricter defense strategy for the bandwidth of the origin at only 5 Mbit/s. Considering that the broadband bandwidth in many families has exceeded 100 Mbit/s, a bandwidth of 5 Mbit/s can be easily occupied. Once the bandwidth is fully occupied, the response time of the origin will be prolonged, and accordingly the overall quality of services will be affected. We immediately analyzed the situation and configured a stricter strategy. As shown in the following figure, the QPS of attack requests on edge node L1 after 12:00 still exceeded 20,000 at times, but the QPS of back-to-origin requests was very stable and basically the same as before the attack. The customer also affirmed the defense effect.
The third customer case is about DNS protection. The attack occurred during the closed beta phase. Customer C, who accessed SCDN services under closed beta at that time, was a game company. Zhao Wei said, "Game domain names are the hardest hit area of DNS attacks. At that time, the customer reported that game services became unavailable. After rapid analysis, we discovered that the customer's DNS server had stopped providing resolution results. The DNS services used by the customer were provided by a third party free of charge. After logging on to the console, we found that the DNS service provider had blacklisted the customer's game domain name because it was under traffic-intensive DNS attacks. The customer asked us for a solution, so we advised the customer to use our DNS protection. After the customer's access to DNS protection, we detected that the QPS of DNS attacks continued to be on the scale of 120 million. However, under our protection, this scale of attacks no longer affected the customer's services, and DNS resolution became normal. The customer also reported that the game was running smoothly. With no results, the attacker then stopped DNS attacks."
We released the closed beta version of SCDN in September 2017 and the open beta version in December 2017. In May 2018, we officially put SCDN into commercial use. We hope to provide more stable and efficient Alibaba Cloud CDN products in each phase. The scale of DDoS attacks still continues to grow, so we must comprehensively polish the security protection capabilities to provide more stable services for more customers. But what is our plan for SCDN in the future?

The subsequent SCDN planning includes the following four aspects:
At the end of his speech, Zhao Wei expressed his thoughts on the finalization of SCDN. He believed that in the long run, basic security protection capabilities should become default attributes of CDN services, so that customers can have basic security protection capabilities once they access CDN services. At the same time, advanced security features will be developed into components. That is, the anti-DDoS data center against traffic-intensive attacks and abundant advanced security features for application-layer protection will be provided as components. Customers can add one or more advanced security protection components to CDNs based on their own security requirements to customize a security protection solution suitable for their own businesses.

How Alibaba Cloud Helped Tmall Expand the Double 11 Shopping Festival for the Past 10 Years

2,593 posts | 793 followers
FollowAlibaba Clouder - March 19, 2021
Alibaba Clouder - July 9, 2019
Dikky Ryan Pratama - May 5, 2023
Alibaba Clouder - July 12, 2019
Alibaba Cloud Indonesia - October 3, 2023
Ced - November 6, 2024

2,593 posts | 793 followers
Follow CDN(Alibaba Cloud CDN)
CDN(Alibaba Cloud CDN)
A scalable and high-performance content delivery service for accelerated distribution of content to users across the globe
Learn MoreLearn More
 WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn MoreMore Posts by Alibaba Clouder