By Shantanu Kaushik
A secure environment that facilitates an uninterrupted and safe web experience is essential. Security is more important than ever before. The growing number of cyberattacks has led security professionals to reassess the situation and enable a meticulous security solution that is intelligent in mitigating threats but lightweight on the web services.
Organizations, such as Alibaba Cloud, are putting in a lot of effort toward ensuring the highest security levels with their infrastructure and users. You can implement security solutions to counter any attacks or threats on your web service, such as DDoS. However, securing the entire connection is another task.
When we talk about a content delivery network, there are two main transmission channels. One channel is from origin to the CDN, and another is from the CDN to the end user. The chart below shows the architecture:
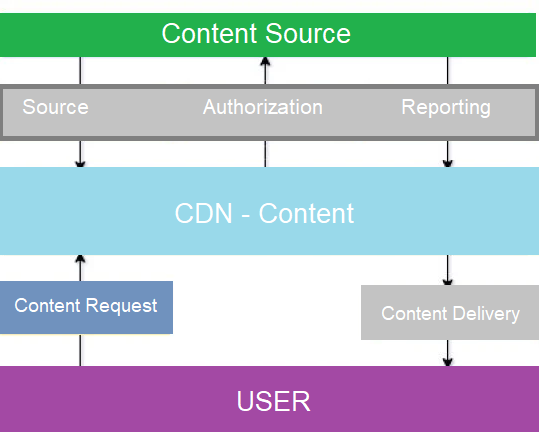
Security for both channels is essential. Alibaba Cloud introduced Secure Route for Content Delivery Network (SCDN) to facilitate maximum security for scenarios where websites or applications are at risk. Alibaba Cloud SCDN is useful if you want to meet and maintain the demands for a high-quality and secure web experience.
Alibaba Cloud SCDN enables SSL/TLS security standards for the content. The CDN service is secured using the HTTPS protocol. The websites or applications have end-to-end encryption with authorization and authentication to maintain the integrity and protection of online communications between the origin server and the end user.
Like any other Internet-based service, the CDN is also susceptible to threats and risks, including:
Alibaba Cloud SCDN helps you create an effective strategy to mitigate these attacks and keep your service secure. It implements different products and solutions, including:
TLS is a protocol responsible for authentication, privacy, and integrity between services, systems, or networks. It is an evolved protocol that works with many applications that require secure data exchanges over a network. TLS evolved from the Secure Sockets Layer (SSL) protocol. TLS is a more secure and efficient protocol compared to SSL that supports newer and more secure algorithms. HTTPS utilizes the TLS/SSL protocol.
Enabling end-to-end encryption is highly a recommended practice that can ward-off most attacks on your service. The content can travel between multiple servers using different routes to reach the user, and enabling end-to-encryption allows more secure content delivery. Using TLS/SSL, you can verify the user and system identification details, content transmission encryption, and detect any tampering.
HTTPS protocol that uses the TLS/SSL can only be enabled if you get an SSL certificate for your website. You can obtain one by using the Alibaba Cloud SSL Certificate Service. The Alibaba Cloud SSL Certificate Service allows you to apply, purchase, and manage SSL certificates. The Alibaba Cloud SSL Certificate Service features qualified certificate authorities to help you select the expected certificate authority and its certificate products to enjoy full-site HTTPS security solutions.
Distributed Denial of Service (DDoS) attacks are one of the most substantial security vulnerabilities today. As the security practices evolve, the intensity and architectural implementation of the DDoS attacks also increase. Today, these attacks and their parameters are much larger and complex, with attackers utilizing bots to target websites and applications.
Distributed Denial of Service (DDoS) is an attack that disrupts normal traffic to the server, network, or resources it targets. Then, it affects the distributed computing architecture by overwhelming the resources of systems in this multiple-system-based architecture.
The most obvious symptom of a DDoS attack is the sluggish service. This could also happen from genuine high traffic situations, but if you come across sudden traffic spikes and service slowdown, further investigation is required. Some of the identifying factors for a DDoS attack are:
Alibaba Cloud Content Delivery Network (CDN) and the distributed infrastructure protect against DDoS attacks by distributing resources across data centers in multiple locations. Hence, a CDN can withstand and mitigate malicious incoming traffic that could easily overwhelm the targeted origin server.
Solution Highlights:
In this article, we covered all the aspects of securing your content delivery network. Alibaba Cloud SCDN works with scenarios that require an added protection layer. It utilizes some of the most influential security techniques for content protection and delivery.
This article explains some of the best implementation practices with Alibaba Cloud CDN. These practices will help you yield better productivity, content acceleration, and secure content delivery from your CDN deployment.

2,593 posts | 793 followers
FollowAlibaba Clouder - March 17, 2021
Alibaba Clouder - March 17, 2021
Alibaba Clouder - March 18, 2021
Alibaba Clouder - March 19, 2021
Alibaba Clouder - March 16, 2021
Alibaba Clouder - August 25, 2020

2,593 posts | 793 followers
Follow RAM(Resource Access Management)
RAM(Resource Access Management)
Secure your cloud resources with Resource Access Management to define fine-grained access permissions for users and groups
Learn More Resource Management
Resource Management
Organize and manage your resources in a hierarchical manner by using resource directories, folders, accounts, and resource groups.
Learn More Anti-DDoS
Anti-DDoS
A comprehensive DDoS protection for enterprise to intelligently defend sophisticated DDoS attacks, reduce business loss risks, and mitigate potential security threats.
Learn More IDaaS
IDaaS
Make identity management a painless experience and eliminate Identity Silos
Learn MoreMore Posts by Alibaba Clouder