This blog will explain an overview of DDoS attack, shared security responsibilities and explore several DDoS protection techniques.
Distributed Denial of Service (DDoS) attack is one of the various types of cyber attacks. DDoS attacks can have a massive impact and are potentially fatal to businesses, governments, etc.
This blog will explain an overview of DDoS attack, shared security responsibilities, and explore several DDoS protection techniques.
Overview of DDoS Attack
Currently, DDoS is one of the most powerful cyber attacks and very difficult to defend.
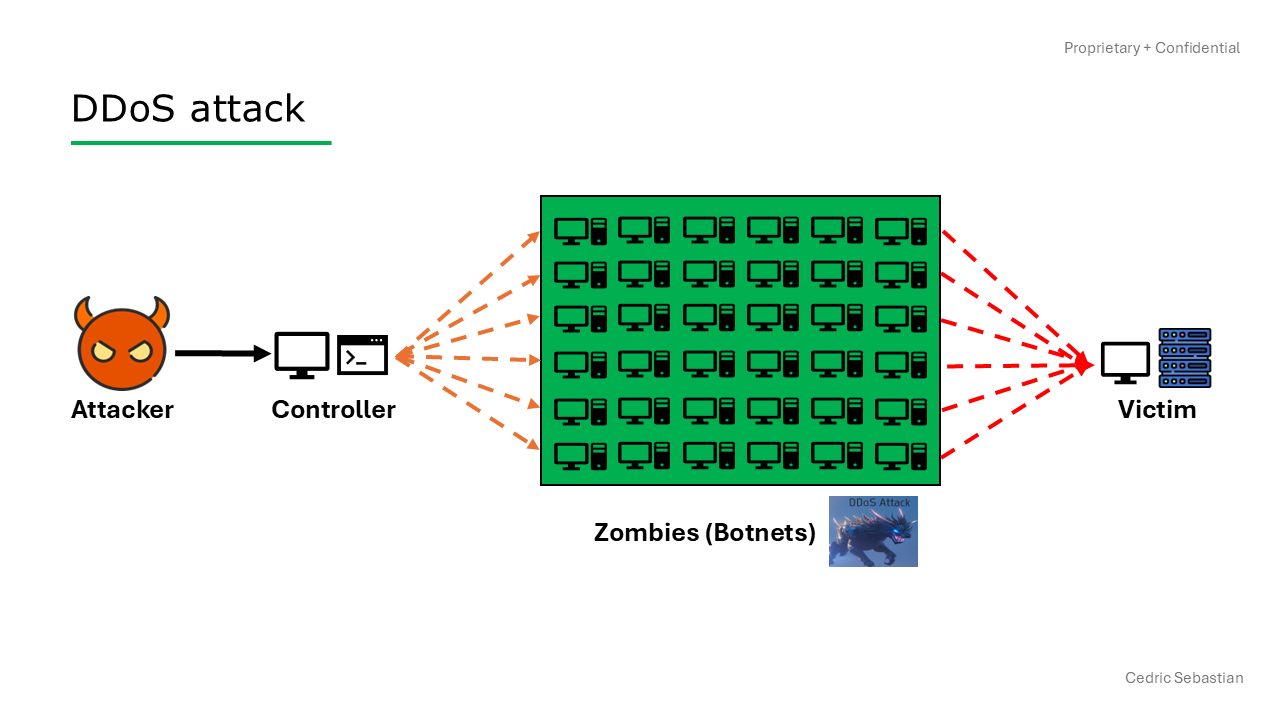
An attacker sends commands from a primary server to control zombies or botnets (consisting of hundreds, thousands, or even millions of compromised devices) to flood the victim's server with massive network traffic to prevent the victim's server from providing normal services to the victim's users.
Impact of DDoS attack:
-
Service Impact
Your origin server may be unable to provide services, and users cannot access the services.
-
Reputational Losses
When your origin server is unavailable for a long time due to a DDoS Attack, your customer will not trust your services.
-
Operational Loss
Increased cost for DDoS Protection Service, Long Downtime, Services delivery delay.
-
Opportunity Loss
When you start a game server business and launch events like flash sales and discounts, your game server gets a DDoS attack. That will prevent your customers from buying your offers, and You will lose the revenue from that event until your Game Server is free from DDoS attacks.
Common types of DDoS attack:
| DDoS Type |
Typical Attack |
| Transport Layer |
SYN Flood, ACK Flood, UDP Flood, ICMP Flood, and RST Flood |
| Application Layer Attacks |
HTTP GET Flood, HTTP POST Flood, and Challenge Collapsar (CC) or HTTP flood attacks |
| Malformed Packet |
Fragment flood, stream flood, land flood, smurf, malformed IP packet. malformed TCP packet, malformed UDP packet |
| DNS |
DNS Request Flood, DNS Response Flood, DNS query flood (spoofed request and real requests), authoritative server attacks, and local server attacks |
| Connections based |
Low and slow attack, connection exhaustion attack, Low Orbit Ion Cannon (LOIC), High Orbit Ion Cannon (HOIC), Slowloris, PyLoris, and XOIC |
Shared Security Responsibilities
The security of applications built on Alibaba Cloud is a shared responsibility between Alibaba Cloud and its customers.
Alibaba Cloud is responsible for the security of the underlying cloud service platform and providing security services and capabilities to customers, while customers are responsible for the security of applications built based on Alibaba Cloud services.
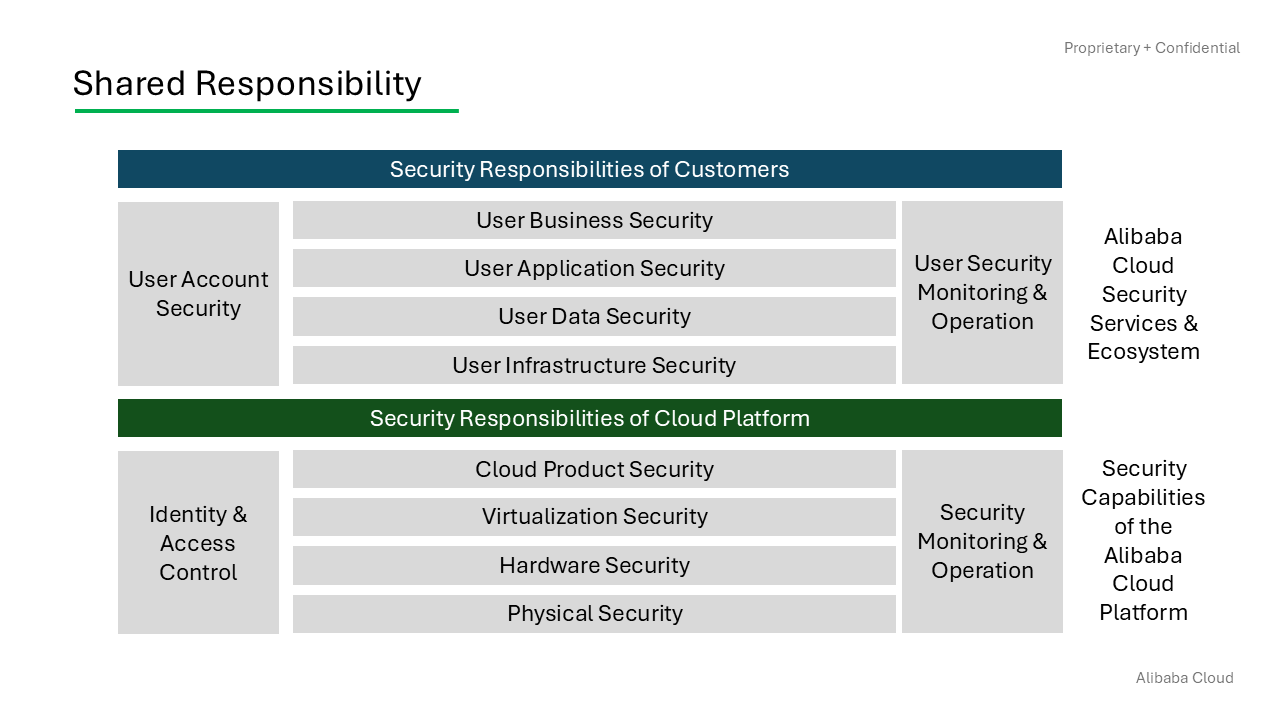
Alibaba Cloud's Responsibilities:
-
Infrastructure Security: Ensures the physical and virtual security of data centers, hardware, and network devices.
-
Platform Security: Manages security for the Apsara distributed cloud OS, cloud products, and services, including OS and database patch management, network access control, and anti-DDoS protection.
-
Vulnerability Management: Regularly identifies and fixes security vulnerabilities without disrupting customer services.
-
Compliance and Audits: Cooperates with third-party security agencies for regular audits and compliance checks.
-
Customer Security Tools: Provides tools for high availability, secure hardware, account management, security monitoring, data encryption, and third-party security integration.
Customer Responsibilities:
-
System Protection: Uses Alibaba Cloud's security features and third-party products to protect their applications and systems.
-
Configuration Management: Ensures proper configuration of cloud products for infrastructure and data security, including OS hardening, timely patching, and security group configuration.
-
Service Management: Manages service account authentication and resource authorization for cloud services, especially for platform and cloud-native services.
-
Data Encryption: Uses Alibaba Cloud's native encryption capabilities or Data Encryption Service for sensitive data.
-
Security Monitoring: Utilizes Alibaba Cloud Security services to monitor and manage application and system security.
-
Account Security: Protects Alibaba Cloud account credentials through measures like MFA, minimal permission grants, and role-based access control.
-
Audit Trails: Using Alibaba Cloud ActionTrail to record and audit API calls and console operations.
DDoS protection techniques
You can mitigate attacks against your assets on Alibaba Cloud by using the following methods:
-
Reduce Attack Surface and Isolate Resources:
-
Security Groups: Configure security groups to open only necessary ports, preventing illegal access and reducing exposure to malicious scans.
-
VPC: Use Virtual Private Cloud (VPC) to logically isolate your network and protect against internal threats.
-
Optimize Service Architecture:
-
Performance Evaluation: Conduct stress tests to assess service throughput and guide DDoS mitigation strategies.
-
Elastic and Redundant Architecture: Use load balancing (e.g., Server Load Balancer) to distribute traffic and avoid single points of failure (SPOFs).
-
Auto Scaling: Implement Auto Scaling to dynamically adjust computing resources based on demand, improving performance and resilience during attacks.
-
Optimize DNS Resolution:
-
Intelligent DNS: Use intelligent DNS resolution to mitigate DNS attacks.
-
DNS Best Practices: Host services on multiple DNS providers, drop unsolicited responses, enable TTL, and authenticate DNS clients.
-
Caching: Cache DNS responses to reduce load and improve response times.
-
Access Control and Bandwidth Management:
-
ACLs and BCP38: Use Access Control Lists (ACLs), BCP38, and IP reputation to filter traffic.
-
Additional Bandwidth: Purchase extra bandwidth to handle increased traffic during attacks.
-
Server Security and Performance:
-
OS Hardening: Keep system files and software up-to-date, disable unnecessary services and ports, and configure firewalls to block unwanted requests.
-
SYN and ICMP Traffic: Limit SYN semi-joins, shorten timeouts, and restrict SYN and ICMP traffic.
-
Log Monitoring: Regularly check logs for signs of vulnerabilities or attacks.
-
File Sharing: Restrict file sharing outside the firewall to prevent interception and tampering.
-
Network Devices: Configure routers and other network devices to control traffic, filter packets, and discard suspicious data.
-
Monitoring and Emergency Response:
-
Alert Notifications: Pay attention to alerts from Anti-DDoS Basic and respond promptly.
-
CloudMonitor: Use CloudMonitor to collect and analyze monitoring metrics and set up alerts.
-
Emergency Response Plan: Develop and test an emergency response plan based on your service architecture and resources.
-
Alibaba Cloud Security Solutions:
-
WAF: Use Web Application Firewall (WAF) to protect against transport layer, session layer, and application layer attacks.
-
Anti-DDoS Origin Basic: Provides Anti-DDoS Basic, which has up to 5 Gbit/s Anti-DDoS capacity free of charge. This basic DDoS protection function is provided by default.
-
Anti-DDoS Origin: Utilize Anti-DDoS Origin for shared and best-effort DDoS protection.
-
Anti-DDoS Proxy: Consider Anti-DDoS Proxy for protection against volumetric DDoS attacks.
For more information about best practices, see Best practices for mitigating DDoS attacks


 Security Center
Security Center
 Security Solution
Security Solution
 Security Overview
Security Overview
 Cloud Hardware Security Module (HSM)
Cloud Hardware Security Module (HSM)