By CNCC SIG
Through the cooperative development between OpenAnolis and HYGON, Anolis 8.4 now officially supports confidential container based on HYGON CSV technology. It guarantees the security of containers throughout the entire life cycle from container image download to launch application container, and is the first complete solution for confidential container in OpenAnolis.
CSV (China Security Virtualization) is a security virtualization technology developed by HYGON, implemented with Chinese cryptographic algorithms. The CPU hardware automatically encrypts memory data written by CSV virtual machines, and decrypts data when CSV virtual machines read the memory data. Each CSV virtual machine uses a unique key.
CSV virtual machines have the following features:
1) Isolated compute resources
2) Measurable launch process
3) Authenticated virtual machine identity
In this article, we will discuss the features of CSV virtual machines in detail.
HYGON CPU uses ASID (Address Space ID) to distinguish different CSV virtual machines and hosts. Each CSV virtual machine has independent CPU resources such as cache and TLB to isolate resources between CSV virtual machines and hosts. Each CSV virtual machine has a corresponding key in the memory controller. The keys are independent of each other and are managed by the HYGON Security Processor. The encrypted memory data in an encrypted virtual machine will not be decrypted by the host or other CSV virtual machines.
The launch process of a CSV virtual machine is managed by the HYGON Security Processor. User provides the virtual machine file and the corresponding measurement value to the security processor. Then, the security processor calculates the measurement of the file and compares it with the measurement value provided by the user. Only when the measurement values are equal, the launch process is continued. If they are not equal, it indicates that the virtual machine file has been tampered and the virtual machine fails to be launched.
Each HYGON CPU has a unique built-in chip key and a chip certificate signed by HYGON. Users can verify the signature of the chip certificate to confirm whether it is a legitimate HYGON chip, and further check the attestation report generated by a virtual machine to confirm whether it is a legitimate CSV virtual machine. The attestation report of a CSV virtual machines contains the measurement, version number, owner and other information related to the virtual machines. The attestation report is signed with the chip key. Therefore, users can verify the report signature to confirm the legitimacy of the report and check the measurement and other information to confirm the legitimacy of the virtual machines, which further implements the remote attestation of CSV virtual machines.
The confidential container solution based on HYGON CSV combines the technical advantages of Kata containers, CSV virtual machines, and Inclavare Containers. A CSV virtual machine is created through Kata as a trusted environment for containers to run. The remote attestation feature of the CSV virtual machines is combined with the RATS-TLS of Inclavare Containers, and the attestation report of the CSV virtual machines is embedded in the TLS certificate. The attestation report contains the TLS public key information and the signature of the HYGON chip key. Thus, users check this attestation report to confirm that the running environment of the current container is a trusted CSV virtual machine and that the TLS public key is legitimate, which can be used to secure the communication between the two parties in the future.
The following figure shows the architecture of the CSV confidential container solution:
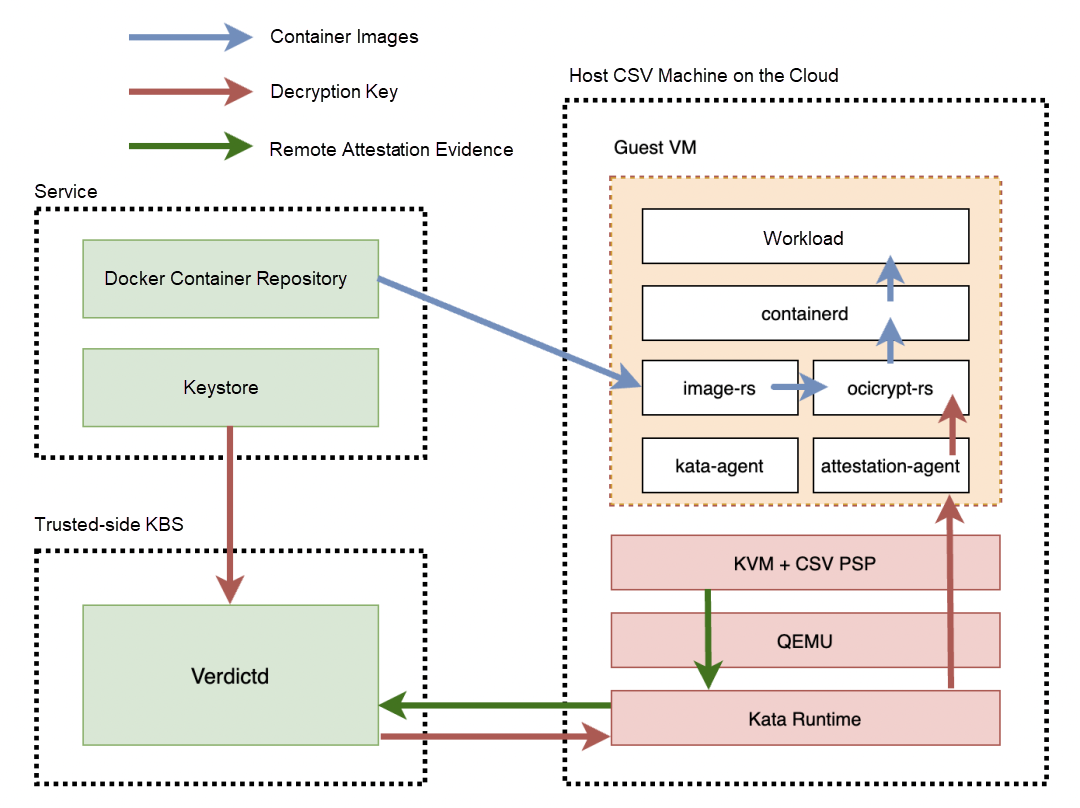
The images in the docker container repository are encrypted. Verdictd is used to manage the encryption key of the images. Verdictd transmits the image key into a CSV virtual machine after the remote attestation evidence of the CSV virtual machine is verified. The Kata agent in the CSV virtual machine uses this key to decrypt the container images and launch the application container. During the whole process, the data of the container is encrypted, including the data in the container images and memory data in the runtime process, which guarantees the security of the whole life cycle of the container.
Detailed introduction and development documents have been published in OpenAlinos CNCC SIG. You can visit the official website to learn more!
A Custom Container Dedicated OS Running on the Cloud-LifseaOS

85 posts | 5 followers
FollowOpenAnolis - September 6, 2022
OpenAnolis - December 12, 2023
OpenAnolis - August 3, 2022
OpenAnolis - July 8, 2022
OpenAnolis - June 30, 2022
OpenAnolis - August 15, 2022

85 posts | 5 followers
Follow ACK One
ACK One
Provides a control plane to allow users to manage Kubernetes clusters that run based on different infrastructure resources
Learn More China Gateway Solution
China Gateway Solution
Power your progress in China by working with the NO.1 cloud provider of this dynamic market.
Learn More Container Registry
Container Registry
A secure image hosting platform providing containerized image lifecycle management
Learn More Container Service for Kubernetes
Container Service for Kubernetes
Alibaba Cloud Container Service for Kubernetes is a fully managed cloud container management service that supports native Kubernetes and integrates with other Alibaba Cloud products.
Learn MoreMore Posts by OpenAnolis