By Liang Zhou, a core member of cloud-native Confidential Computing SIG.

In a cloud-native deployment, confidential container technologies such as Inclavare Containers and Confidential Containers which based on HW-TEE (such as Intel SGX, Intel TDX, and AMD SEV) can provide confidential and integrity protection for sensitive data in use.
However, in a cloud environment, the following problems still exist:
Inclavare Containers is now one of the projects of the OpenAnolis Community cloud-native Confidential Computing SIG. The component Enclave Attestation Architecture (EAA) of Inclavare Containers was created to solve these complex problems. Its design goal is to provide a universal remote attestation architecture that supports different types of confidential containers and HW-TEE environments based on solving the above problems.
The Confidential Computing Consortium defines the RATS reference architecture and recommends that all remote attestation services should follow it . The following is the RATS architecture:
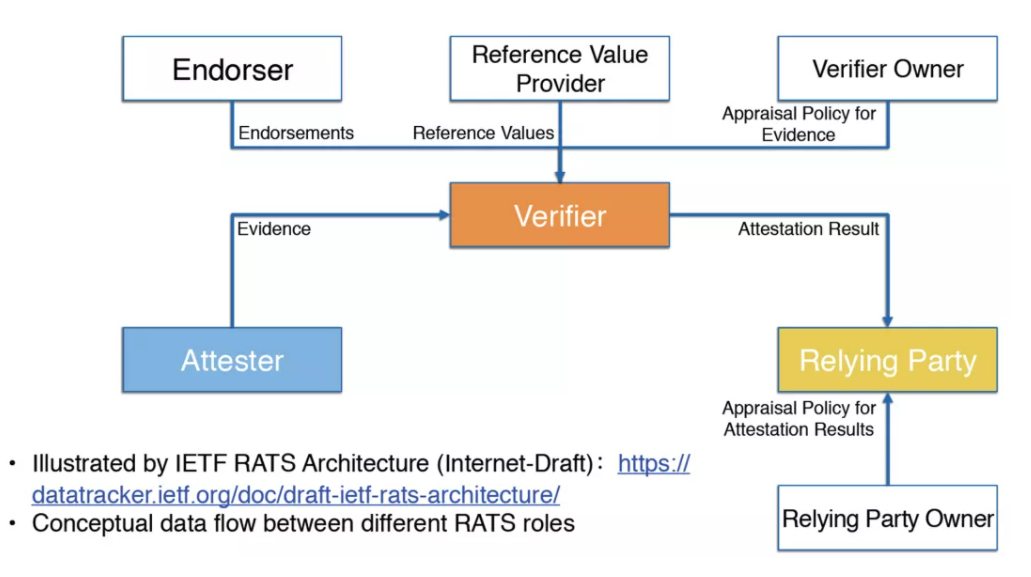
Therefore, the architecture design of EAA also follows the RATS reference architecture:
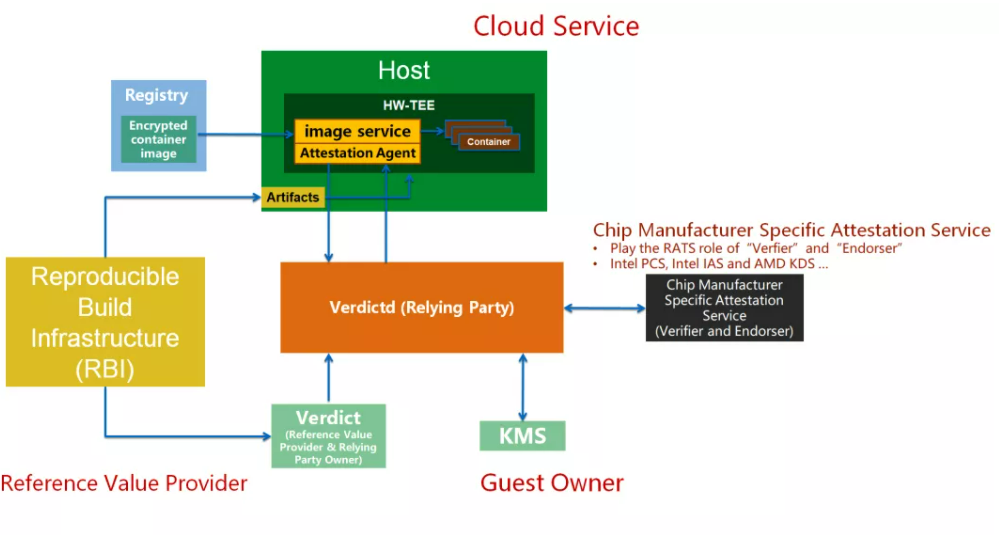
1. When remote attestation is required, the Attestation-Agent running in the cloud HW-TEE environment obtains the Evidence of the current HW-TEE running environment and sends it to the Verdictd service for relevant validation.
2. When Verdictd receives the Evidence, it will invoke the Chip Manufacturer Specific Attestation Service to verify it's signature to ensure the HW-TEE's identity which generated the Evidence. The purpose is to prevent hackers from forging a TEE environment to cheat users' trust.
3. After the signature of the Evidence is verified, Verdictd checks the specific measurement information. The purpose is to determine that the running program's content in the cloud HW-TEE environment is as expected and has not been tampered.
4. If the above checks are successful, the remote attestation process has been finished. The user can ensure that the HW-TEE environment on the cloud is a real one and the program's content running in the HW-TEE environment meet the following requirements:
5. A secure and trusted channel can be established between the Attestation Agent and Verdictd after the attestation process has been passed. Attestation-Agent can send requests to Verdictd to obtain senstitive data, such as the decryption key to encrypt the container images.
EAA is committed to achieving landing practice capability through contributions and cooperation with the open source community. As the first Key Broker Service (KBS) to support Intel TDX remote attestation, EAA is the first KBS service to support TDX HW-TEE E2E demo for Confidential Containers, and it finished the Confidential Containers V0 milestone E2E demo.
EAA fills the last application gap of HW-TEE based confidential containers in a cloud-native scene, and it provides the necessary foundation for secure deployment and startup of encrypted confidential containers in cloud environments.
At present, as a submodule of Inclavare Containers (CNCF projects), EAA supports Intel SGX and, Intel TDX HW-TEEs and it also supports Inclavare Containers and Confidential Containers projects. In the future, EAA will continue evolving to support new and different confidential container solutions and new HW-TEE environments, which will make EAA a truly universal remote attestation architecture in the confidential container field.
Inclavare Containers: https://github.com/alibaba/inclavare-containers
Confidential Containers: https://github.com/confidential-containers
SIG Address of OpenAnolis Community: https://openanolis.cn/sig/coco
Demo Video: https://www.youtube.com/watch?v=9Lgo9_JtUsc
A Tribute to Hackers: The Way to Explore Memory Virtualization

96 posts | 6 followers
FollowOpenAnolis - June 9, 2022
OpenAnolis - July 14, 2022
OpenAnolis - March 7, 2022
Alibaba Clouder - October 10, 2020
Alibaba Container Service - February 24, 2021
Alibaba Developer - April 18, 2022

96 posts | 6 followers
Follow Function Compute
Function Compute
Alibaba Cloud Function Compute is a fully-managed event-driven compute service. It allows you to focus on writing and uploading code without the need to manage infrastructure such as servers.
Learn More ACK One
ACK One
Provides a control plane to allow users to manage Kubernetes clusters that run based on different infrastructure resources
Learn More Cloud-Native Applications Management Solution
Cloud-Native Applications Management Solution
Accelerate and secure the development, deployment, and management of containerized applications cost-effectively.
Learn More Lindorm
Lindorm
Lindorm is an elastic cloud-native database service that supports multiple data models. It is capable of processing various types of data and is compatible with multiple database engine, such as Apache HBase®, Apache Cassandra®, and OpenTSDB.
Learn MoreMore Posts by OpenAnolis