
By SIG for Cloud Native Confidential Computing
As the first open-source container runtime in the industry for confidential computing scenarios, Inclavare Containers was open-sourced in May 2020. It has developed rapidly over a year, attracting the attention and contributions of experts and engineers in many fields. On September 15, 2021, the cloud-native computing foundation (CNCF) announced it would adopt Inclavare Containers as the CNCF official sandbox project through a vote from Technical Oversight Committee (TOC). It became the first confidential computing project in cloud-native that entered the CNCF.
However, unless you follow up on the information in the field of confidential computing, you may not know much about Inclavare Containers. This article will sort out the development of Inclavare Containers project and interpret its core ideas and innovative technologies.
What is Inclavare Containers?
In a nutshell, Inclavare Containers is the industry's first open-source container runtime for confidential computing scenarios.
What is confidential computing? What is the relationship between Inclavare Containers and confidential computing? What problems can it solve?
Data has three states throughout its lifecycle: At-Rest, In-Transit, and In-Use.
We store, use, and share all kinds of sensitive data, including credit card data, medical records, firewall configurations, and geographic location data. Protecting sensitive data in all states is more important than ever. Nowadays, the widely used encryption technology can be used to guarantee data confidentiality (to prevent unauthorized access) and data integrity (to prevent or detect unauthorized modification). However, these technologies are mainly used to protect data in transmission and at rest. Currently, the technology of providing security protection for the state of In-Use is still a new frontier technology.
Confidential computing refers to the use of hardware-based Trusted Execution Environments (TEE) to protect data in use. We can protect against data In-Use by using confidential computing.
Core functions of confidential computing include:
Many manufacturers in the industry have begun to pay attention to and invest in confidential computing. Major chip manufacturers and cloud service providers (CSPs) have invested R&D resources in the field of confidential computing and formed the Confidential Computing Alliance. This alliance is dedicated to cloud services and hardware ecosystems and to protecting data security during computing.
Currently, three hardware platforms support TEE: Intel® SGX, ARM TrustZone, and AMD SEV. They have different application scenarios and implementations:
Currently, confidential computing is flourishing, the market and commercialization potential is huge. However, it has shortcomings in cloud-native scenarios:
In short, the existing confidential computing technology solutions have the preceding difficulties and fail to fully meet the security requirements of users in different scenarios.
Inclavare Containers provides the first open-source container runtime for confidential computing scenarios to solve these problems, which combines confidential computing technology and container technology. Its value can be summarized into three points:
Inclavare Containers support confidential applications to be transparently containerized by TEE based on hardware. It offers the following benefits:
As shown in the following figure, the Inclavare Containers contain multiple components that can make trusted applications run in containers using Enclave technologies based on hardware support. The included components are rune, shim-rune, and Enclave Runtime.
https://github.com/opencontainers/runtimespec/blob/master/implementations.md
A typical class of Enclave Runtime implementations is based on library operating systems. Currently, the recommended Enclave Runtime to interact with rune is Occlum, a memory-safe, multi-process Libos. Another typical type of Enclave Runtime is Intel® SGX WebAssembly Micro Runtime (WAMR), which is an independent WebAssembly (WASM) runtime with a small footprint, including a VM core, an application framework, and a WASM application for dynamic management.
In addition, you can write your Enclave Runtime in any programming language and SDK you like (such as Intel SGX SDK), as long as it implements Enclave Runtime PAL API.
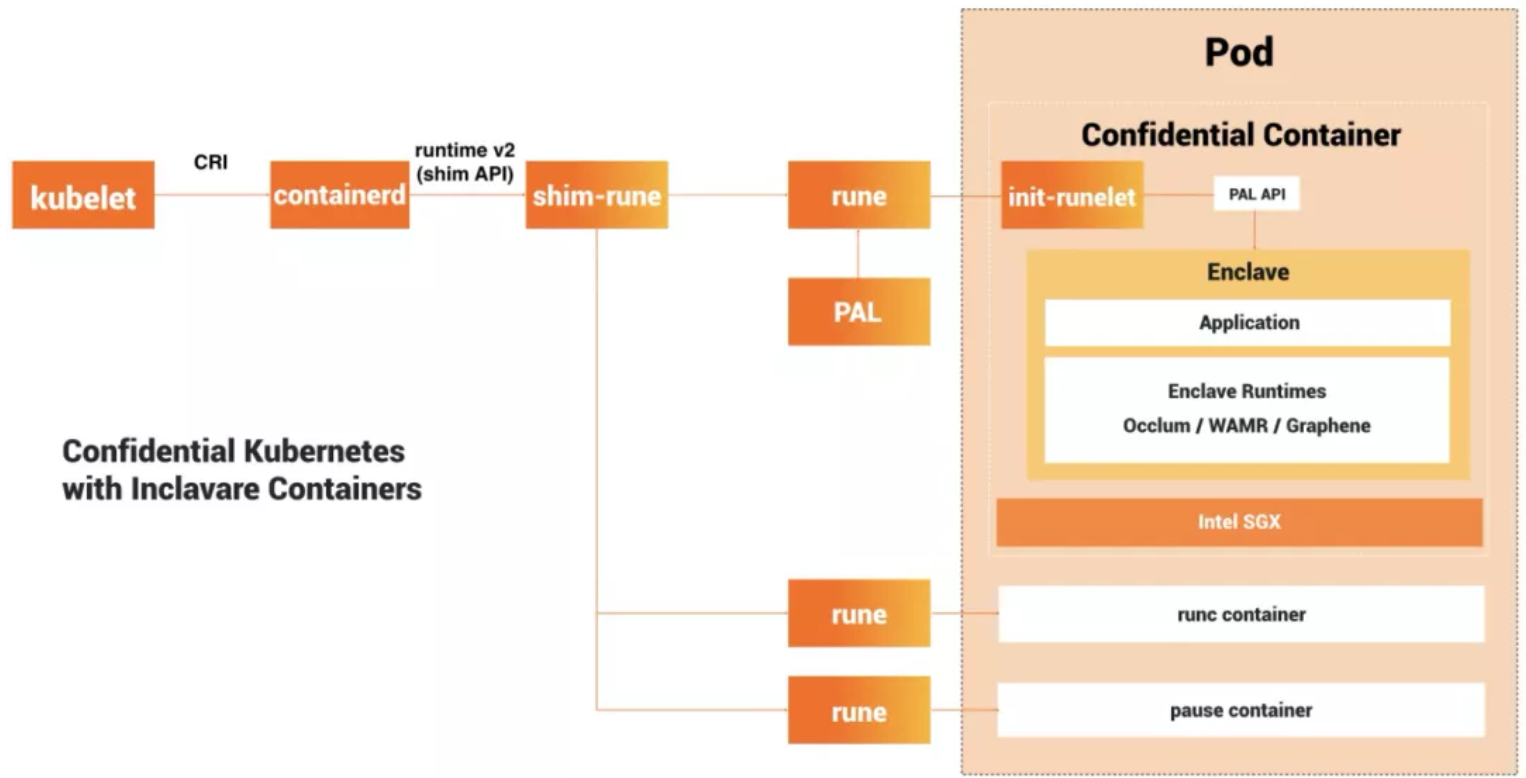
Inclavare Containers have the following features:
It is difficult for a common user to know how to run a confidential container. You need to master the field of confidential computing and develop and build images by the SGX application development specifications. Inclavare Containers designed and implemented a new type of OCI run time rune that conforms to the OCI run time specifications to be consistent with the existing cloud-native ecosystem and realize the confidential container form. It can help you eliminate these complicated processes and enables you to use confidential containers like ordinary containers.
Inclavare Containers can be integrated with dockerd. Specifically, you need to build the container image, install the Enclave Runtime, and add the rune configurations in docker configuration files, such as /etc/docker/daemon.json.
{
"runtimes": {
"rune": {
"path": "/usr/local/bin/rune",
"runtimeArgs": []
}
}
}Then, restart the docker service.
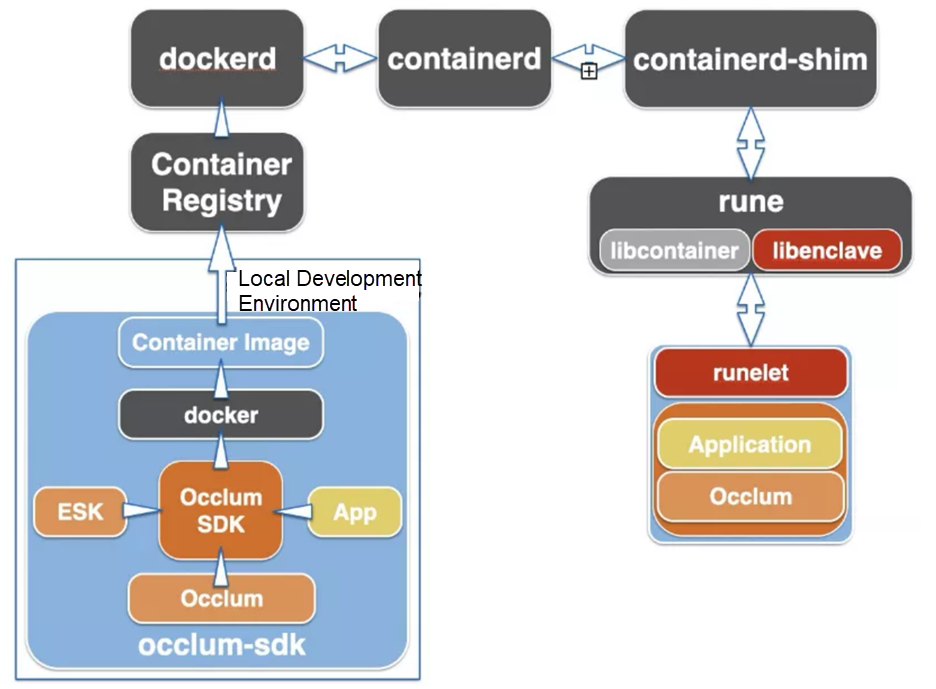
Since the rune is developed based on the runc code, the rune can create a runc container or an Enclave container. In a Docker cluster, the process of creating a runc container and an Enclave container are the same. The difference is the image. Common runc container images cannot create an Enclave. Users must generate a special image based on the requirements of the Enclave Runtime. As shown in the preceding figure, the process of using Docker to start an Occlum confidential container is listed below:
Enclave containers can run in Docker clusters, but there are some shortcomings:
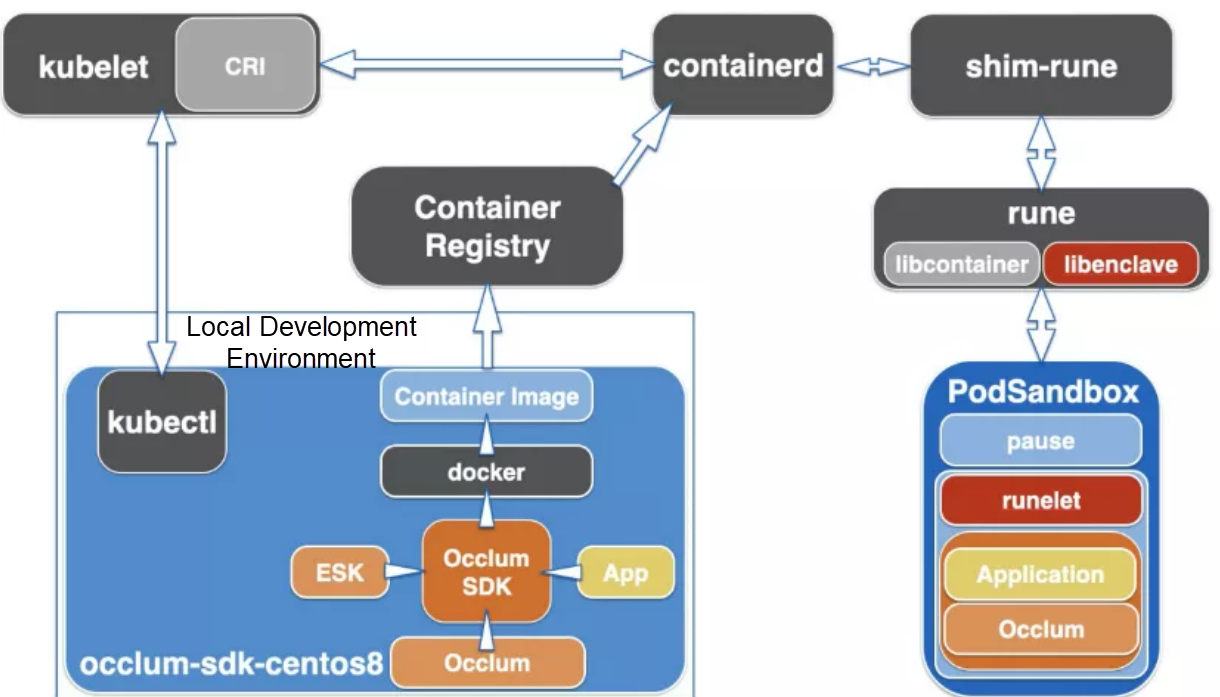
Therefore, Inclavare Containers provide shim-rune for creating Enclave containers in a Kubernetes confidential computing cluster on the cloud. In this scenario, shim-rune and rune can form an enclave containerized stack, and you are provided with the same experience as ordinary containers without installing Enclave Runtime when building container image.
Inclavare Containers has been added to the adopter list of containerd: https://github.com/containerd/containerd/blob/master/ADOPTERS.md
In addition, shim-rune supports the containerd shim v2 API: https://github.com/containerd/containerd/blob/master/runtime/v2/task/shim.proto
Therefore, you can add the shim-rune configuration to the containerd configuration file (such as /etc/containerd/config.toml) on the system.
[plugins.cri.containerd]
...
[plugins.cri.containerd.runtimes.rune]
runtime_type = "io.containerd.rune.v2"Then, restart the containerd.
As shown in the preceding figure, the workflow of creating an Occlum confidential container in a Kubernetes confidential computing cluster on the cloud is listed below:
1. kubelet initiates a Container Runtime Interface (CRI) request to containerd, such as creating a Pod.
2. One cri-containerd plug-in implements the CRI interface in Containerd. Containerd receives the request and forwards the request to the shim-rune.
3. shim-rune can create a runc container or a rune container. When creating runc and rune containers, the process is different:
4. Create a rune process for each container. This process is responsible for creating a container. The process of creating a runc container and an Enclave container is different:
rune loads liberpal.so on the Host, creates the container as runc, and starts the first process init-runelet in the container. Init-runelet loads and creates the Enclave after receiving the rune request. Enclave includes two parts: LibOS and App/Language Runtime. LibOS is an operating system library provided by Enclave Runtime to support the running of applications. App/Language Runtime is the application itself, and some languages also have language Runtime. For example, running OpenJDK 11 applications requires JVM.5. The rune process exits and sets the parent process of process 1 in the Enclave container to shim-rune.
6. Shim-rune requests rune to start Enclave. At this point, a trusted application is running.
Inclavare Containers designed a set of common and cross-platform remote attestation architecture Enclave Attestation Architecture (EAA) to further meet the security requirement that the security of sensitive data of users can no longer rely on cloud vendor on the transmission link. The EAA uses the TLS certificate that is associated with remote proof of evidence with a hardware executable environment as the root of trust to ensure the security of the communication channels of the communicating parties is based on the hardware trusted execution environment.
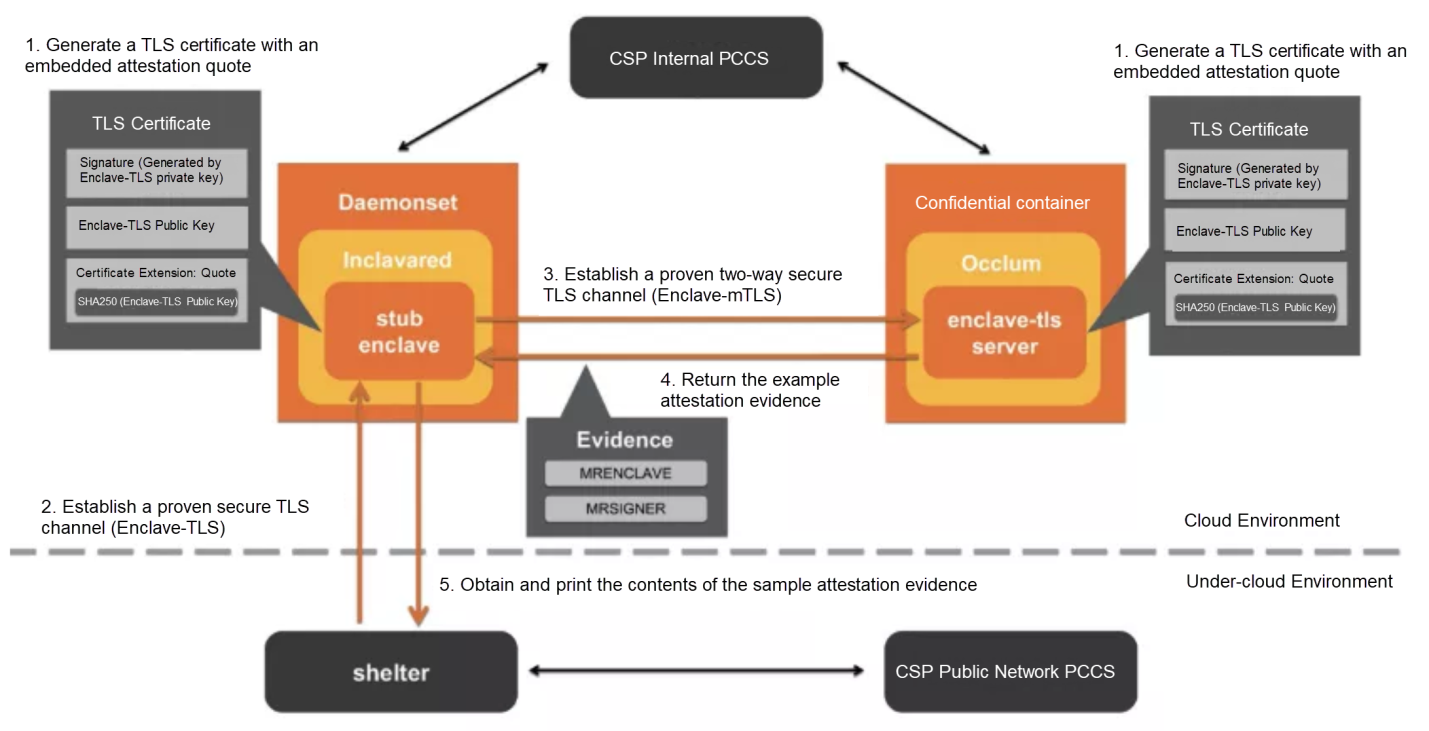
The main components of the EAA are listed below:
Enclave-TLS enhances standard TLS to support trusted communication between heterogeneous hardware TEE based on confidential computing technology. Enclave-TLS is a kind of security protocol with a bidirectional transfer layer (Transport Layer Security or TLS), which supports a heterogeneous hardware environment. Non-hardware TEE platforms can communicate with hardware TEE (such as SGX Enclave) over an authenticated secure channel to transmit sensitive information using Enclave-TLS. In general, TCB's boundaries extend from the execution environment to network transport using the Enclave-TLS. In addition, Enclave-TLS has an extensible model to support various hardware TEE.
Confidential container plays the role of certifiers. It responds to the request from the Inclavared and returns the attestation evidence (mrenclave and mrsigner values) of the confidential container.
Inclavared forwards traffic between downstream confidential containers and the upstream client verifier programs Shelter. The communication process is protected by the proven Enclave-TLS channel.
As a remote attestation validator deployed on the cloud, Shelter records the runtime startup metrics of Enclave and establishes a trusted channel based on Enclave-TLS with Inclavared for communication. Finally, Shelter validates the runtime metric values of the Enclave so tenants can know if their workloads are being loaded in the environment of the TEE.
The following is the specific workflow:
If the user wants to verify that the workload is running on a trusted platform, they can start the Shelter to send a validation request to the Inclavared.
Inclavare Containers provides container runtime compatible with the OCI Runtime. Users can run Enclave containers in Docker clusters or Kubernetes clusters as needed. The Enclave Runtime erases the threshold for users to use confidential computing technologies. In Kubernetes clusters, the experience is consistent with common containers. Enclave Runtime PAL API can provide a variety of Runtime to give the user more Enclave choices between safety and costs.
The technical innovations of Inclavare Containers are reflected in the following:
1. The standard technology of enclave is implemented.
2. A flexible and scalable Kubernetes cluster-level remote attestation architecture Based on Enclave-TLS, Shelter and Inclavared
3. Develop a common PAL API, standardize the interface between enclave runtime and Inclavare Containers, and create an ecosystem of Inclavare Containers
4. Construct a confidential computing cluster infrastructure based on the zero-trust model
5. Seamless integration with the Kubernetes ecosystem
As the industry's first open-source container runtime for confidential computing scenarios, Inclavare Containers provides best practices for the ACK-Trusted Execution Environment (ACK-TEE) to use confidential containers. ACK-TEE relies on Inclavare Containers to seamlessly run confidential container made by users and maintain the same sense of use as ordinary containers. ACK-TEE can be widely used in various privacy computing scenarios, including blockchain, secure multi-party computing, key management, genetic computing, financial security, AI, and data leasing.
In the future, Inclavare Containers will continue to provide confidential computing container technology, confidential computing cluster technology, and security architecture for cloud-native scenarios for the open-source community and become the standard in this field. We will improve the user experience of developers and users and eliminate the difference in using somatosensory with running ordinary containers while deepening the implementation of the principle of the zero-trust model. Inclavare Containers will participate in the joint construction of cloud-native communities, join hands with upstream and downstream partners to promote the progress of cloud-native security technology, and make unremitting efforts to create a safer cloud-native environment.
Faster Container Image Loading Speed with Nydus, RAFS, and EROFS

101 posts | 6 followers
FollowOpenAnolis - March 7, 2022
OpenAnolis - June 30, 2022
Alibaba Clouder - October 10, 2020
Alibaba Container Service - February 24, 2021
OpenAnolis - July 8, 2022
Alibaba Cloud Community - June 10, 2022

101 posts | 6 followers
Follow Managed Service for Prometheus
Managed Service for Prometheus
Multi-source metrics are aggregated to monitor the status of your business and services in real time.
Learn More ACK One
ACK One
Provides a control plane to allow users to manage Kubernetes clusters that run based on different infrastructure resources
Learn More Apsara Stack
Apsara Stack
Apsara Stack is a full-stack cloud solution created by Alibaba Cloud for medium- and large-size enterprise-class customers.
Learn More Cloud-Native Applications Management Solution
Cloud-Native Applications Management Solution
Accelerate and secure the development, deployment, and management of containerized applications cost-effectively.
Learn MoreMore Posts by OpenAnolis