Catch the replay of the Apsara Conference 2020 at this link!
By Alibaba Cloud Open Platform
With the rapid development of cloud technology in recent years, the concept of Cloud-Native is generally understood and accepted. More enterprises are choosing to migrate to the cloud to implement digital transformation. From moving traditional applications to the cloud or developing new products and businesses based on Cloud-Native technology, enterprises hope to utilize cloud technology for flexible innovation of their business at a low cost and to maximize the value of cloud migration.
However, with the increasing adoption of cloud technology, business and resource types and scales are increasing. Enterprises are also encountering new problems:
These problems can affect the stability and development speed of business, cause security risks, and endanger the foundation of enterprises' survival. Therefore, before migrating to the cloud, enterprises need to plan and create a secure, controllable, and compliant "Landing Zone" for each business to be migrated to the cloud, except for adapting business applications to the cloud environment. By doing so, business developers are allowed to focus on their own business for quick iteration and innovation of the business based on cloud capabilities in the Landing Zone. Developers can take efficiency and controllability into account to achieve the maximum value of cloud migration.
The key procedure of this part of the work lies in the improvement of enterprises' IT governance infrastructure.
Enterprise IT Governance is a series of strategies, principles, and implementation processes that guide enterprise IT planning and operation, which allows IT personnel to control business risks at the IT level. In addition, Enterprise IT Governance can also ensure efficient and stable operation of enterprise business. A complete set of on-cloud Enterprise IT Governance infrastructure includes the following features:
To maximize the value of cloud migration, enterprises don't need to spend a lot of effort into learning on-cloud capabilities. More importantly, they need to conduct unified planning and implementation in the early stage. Instead of creating a poor "roughcast house," this way, a secure and controllable Landing Zone can be created for business on the cloud. In recent years, many enterprise customers of Alibaba Cloud have also been troubled by these problems and they turned to Alibaba Cloud for the best practices. For helping these enterprises quickly access Alibaba Cloud, the Alibaba Cloud Open Platform Team summarized the best practices based on several enterprises IT governance capabilities and pain points in enterprises' cloud migration. The team released the Enterprise IT Governance solution and three sets of specific implementation plans for enterprises in different sizes, as well as automated tools for quick implementation. Now, let's take medium- and large-sized enterprises and multinationals as examples to learn the design concept of the Enterprise IT Governance solution.
This solution serves as a model for enterprise users to construct a complex cross-account enterprise IT governance system on Alibaba Cloud. The framework includes the following aspects:
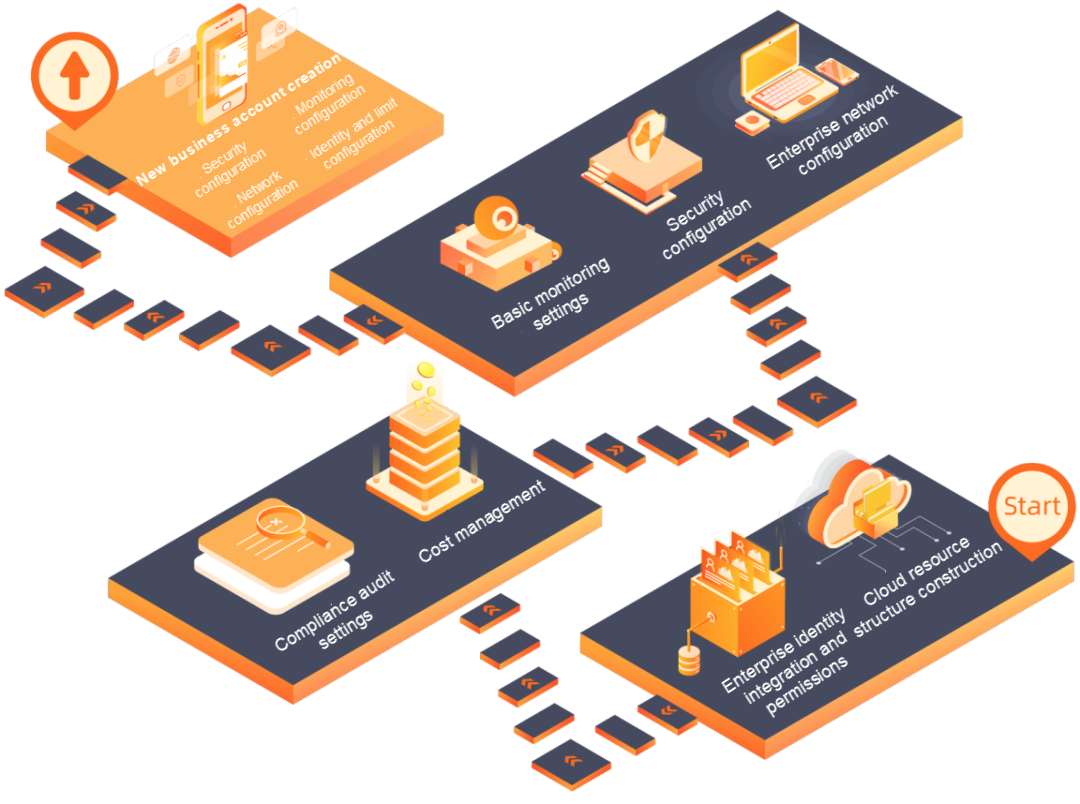
Compliance and audit can be implemented in three ways:
With the design concept of the solution, the next step is how to construct and implement the infrastructure according to the characteristics and development stages of enterprises, assisting enterprises to quickly turn the "roughcast house" into a "fine-decoration house". It is impossible for an implementation solution to perfectly match the demands of every enterprise in real practices. Enterprises must customize and combine different solutions based on their own demands and design principles. These three representative solutions mentioned above are the best solutions proposed by Alibaba Cloud for start-ups, medium- and large-sized enterprises, and multinationals. For more information, you can visit the Alibaba Cloud Open Platform website. For start-ups, operation steps and codes that are automatically generated can be obtained on the official website to implement such a solution. As for other enterprises, please contact your Alibaba Cloud sales representative or service manager.
During the implementation process, the ideal state is full automation. Based on the concept of Infrastructure as Code (IaC) and several tools, including Terraform, the Alibaba Cloud Open Platform provides automated deployment scripts and codes and makes them available open on the Aliyun Landing Zone Github to help you quickly deploy a solution or integrate it into the internal automation process system.
With the arrival of the Cloud-Native era, enterprises will face more new challenges on the cloud. The Alibaba Cloud Open Platform Team will continue to optimize products and solutions, accumulate additional best practices, and help enterprises manage and make good use of the cloud, allowing enterprises to innovate more quickly based on Cloud-Native capabilities.
If you encounter any problem or have any suggestions when migrating to the cloud, please feel free to contact us. You are also welcome to follow the latest development of our team and learn the latest best practices for cloud migration.
Alibaba Cloud Starts a "New Long March" of Technical Services
Management Automation – Enterprises' Inevitable Approach to Cloud Migration

2,597 posts | 773 followers
FollowAlibaba Clouder - October 13, 2020
Alibaba Cloud Community - September 17, 2021
Alibaba EMR - June 8, 2021
Alibaba Clouder - October 14, 2020
Alibaba Cloud MaxCompute - July 14, 2021
Alibaba Cloud Community - March 29, 2022

2,597 posts | 773 followers
Follow Cloud-Native Applications Management Solution
Cloud-Native Applications Management Solution
Accelerate and secure the development, deployment, and management of containerized applications cost-effectively.
Learn More Function Compute
Function Compute
Alibaba Cloud Function Compute is a fully-managed event-driven compute service. It allows you to focus on writing and uploading code without the need to manage infrastructure such as servers.
Learn More Managed Service for Prometheus
Managed Service for Prometheus
Multi-source metrics are aggregated to monitor the status of your business and services in real time.
Learn More Lindorm
Lindorm
Lindorm is an elastic cloud-native database service that supports multiple data models. It is capable of processing various types of data and is compatible with multiple database engine, such as Apache HBase®, Apache Cassandra®, and OpenTSDB.
Learn MoreMore Posts by Alibaba Clouder
Start building with 50+ products and up to 12 months usage for Elastic Compute Service
Get Started for Free Get Started for Free