Resource Access Management (RAM) ユーザーまたは RAM ロールを介して Realtime Compute コンソールにアクセスし、ワークスペースの表示、購入、削除などの操作を実行する場合、適切な権限が必要です。操作のセキュリティを確保するために、すべてのアクセスプリンシパルは、Flink ワークスペースを購入した Alibaba Cloud アカウントの管理者が RAM コンソールで対応する権限付与ポリシーを付与する必要があります。このトピックでは、サポートされている権限付与ポリシーと特定の権限付与設定方法について説明します。
権限付与シナリオ
シナリオ | インターフェース | 説明 |
Realtime Compute 管理コンソールにアクセスできない | ワークスペース情報が表示されず、次のエラーが表示されます。
| これは、Realtime Compute 管理コンソールにアクセスする権限がないことを示します。ワークスペースを購入した Alibaba Cloud アカウントの管理者に連絡し、権限付与手順 に従って、お使いのアカウントに少なくとも Stream サービス (AliyunStreamReadOnlyAccess) への読み取り専用アクセス権を付与してください。権限付与が完了したら、ページを再入力または更新して正常にアクセスします。 |
特定の操作を実行できない |
| これは、現在のアカウントにこの操作を実行する権限がないことを示します。操作を実行するには、ワークスペースを購入した Alibaba Cloud アカウントの管理者に連絡し、特定の要件に従ってカスタム権限ポリシーを調整し、権限付与手順 に従って対応する権限付与を完了してください。たとえば、左の画像に示すように、お使いのアカウントには、サブスクリプションワークスペースのリソース割り当てに関連する権限を付与する必要があります。 |
ポリシータイプ
権限付与ポリシーは、権限付与されたリソースセット、操作セット、および権限付与条件を正確に記述する構文構造で記述された権限のセットです。RAM コンソールでは、次の 2 種類の権限付与ポリシーがサポートされています。
[システムポリシー]: システムポリシーは Alibaba Cloud によって作成および更新されます。システムポリシーは使用できますが、変更はできません。ポリシーのバージョンは Alibaba Cloud によって維持されます。Flink でサポートされているシステムポリシーは次のとおりです。
権限セット
名前
説明
Realtime Compute for Apache Flink のすべての権限
AliyunStreamFullAccess
「カスタムポリシー」のすべての権限が含まれます。
読み取り専用モードで Realtime Compute for Apache Flink にアクセスする権限
AliyunStreamReadOnlyAccess
HasStreamDefaultRole と、「Realtime Compute for Apache Flink 権限ポリシー」の Describe、Query、Check、List、Get、Search で始まるすべての権限が含まれます。
費用とコスト (BSS) で注文を表示および支払う権限
AliyunBSSOrderAccess
費用とコストコンソールで注文を表示および支払うことができます。
費用とコスト (BSS) でサブスクライブを解除する権限
AliyunBSSRefundAccess
費用とコスト (BSS) で注文をサブスクライブ解除する権限。
[カスタムポリシー]: カスタムポリシーを作成、更新、削除できます。ポリシーのバージョンはご自身で管理します。Flink でサポートされているカスタムポリシーとその作成方法の詳細については、「Realtime Compute for Apache Flink 権限ポリシー」および「(オプション) ステップ 1: カスタムポリシーを作成する」をご参照ください。
前提条件
「権限付与に関する注意事項」を理解していること。
権限付与手順
(オプション) ステップ 1: カスタムポリシーを作成する
AliyunStreamFullAccess システムポリシーを直接使用する場合は、このステップをスキップできます。
カスタム権限付与ポリシーを作成する場合、Realtime Compute (Stream) サービスを基盤として使用し、実際のニーズに基づいてより詳細な制御ポイントを設計することをお勧めします。これらの制御ポイントには、Realtime Compute for Apache Flink でサポートされている「カスタム権限ポリシー」と「関連プロダクトの権限操作」が含まれます。以下は、Realtime Compute (Stream) サービスへの読み取り専用アクセスのためのカスタム権限付与ポリシーの詳細な内容です。これは、AliyunStreamReadOnlyAccess システムポリシーと同じ権限範囲を持ちます。
{
"Version": "1",
"Statement": [
{
"Action": [
"stream:Describe*",
"stream:Query*",
"stream:Check*",
"stream:List*",
"stream:Get*",
"stream:Search*",
"stream:HasStreamDefaultRole"
],
"Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId}/vvpnamespace/{#namespace}",
"Effect": "Allow"
}
]
}カスタム権限付与ポリシーを作成するためのステップと例: 「カスタム権限ポリシーの作成」および「カスタム権限ポリシーの例」。
権限付与ポリシーでは、Action は実行する操作を示し、Resource は操作が実行されるオブジェクトを示し、Effect は権限付与の効果が許可か拒否かを示します。権限付与ポリシーの構文と構造の詳細については、「権限ポリシーの基本要素」および「権限ポリシーの構文と構造」をご参照ください。ポリシーの内容にある次のパラメーターを実際の値に置き換える必要があります。
{#regionId}: ターゲット Flink ワークスペースが配置されているリージョン。
{#accountId}: Alibaba Cloud アカウントの UID。
{#instanceId}: ターゲット Realtime Compute for Apache Flink 注文インスタンスの ID。
{#namespace}: ターゲットプロジェクトスペースの名前。
ステップ 2: ターゲットポリシーをメンバーにアタッチする
RAM ユーザーまたは RAM ロールに権限付与ポリシーをアタッチすることで、権限付与ポリシーで指定されたアクセス権限を付与できます。このトピックでは、RAM ユーザーに権限を付与する方法について説明します。RAM ロールに権限を付与する手順も同様です。詳細については、「RAM ロールに権限を付与する」をご参照ください。
RAM 管理者として RAM コンソールにログインします。
左側のナビゲーションウィンドウで、 を選択します。
[ユーザー] ページで、目的の RAM ユーザーを見つけ、[操作] 列の [権限の追加] をクリックします。

複数の RAM ユーザーを選択し、ページ下部の [権限の追加] をクリックして、一度に RAM ユーザーに権限を付与することもできます。
[権限の付与] パネルで、RAM ユーザーの権限を追加します。
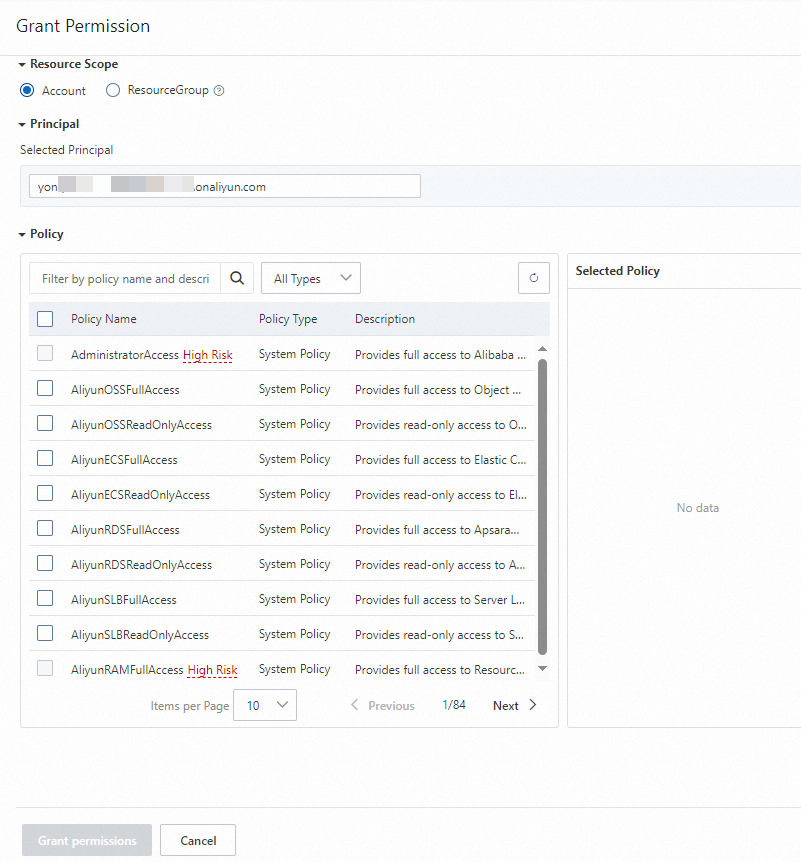
パラメーター
説明
リソース範囲
必要なアプリケーション範囲を選択します:
[アカウント]: 権限は現在の Alibaba Cloud アカウントに付与されます。
[リソースグループ]: 権限は特定のリソースグループに対して有効です。
プリンシパル
プリンシパルは、権限を付与する RAM ユーザーです。デフォルトでは、現在の RAM ユーザーがプリンシパルとして指定されます。別の RAM ユーザーを指定することもできます。
ポリシー
システムポリシーまたは既に作成したカスタムポリシーを選択します。
[権限の付与] をクリックします。
[閉じる] をクリックします。
ステップ 3: 権限付与後にログインして使用する
権限付与が完了すると、RAM ユーザーまたは RAM ロールは、現在の Realtime Compute 管理コンソールのログインページにログインまたは更新して、関連する操作を実行できます。
ログインタイプ | ログイン方法 | ログイン方法 |
Alibaba Cloud RAM ユーザー | RAM ユーザーログイン | |
Alibaba Cloud RAM ロール | メインアカウント A の RAM ユーザーが A のロールを偽装してログインする | |
メインアカウント B の RAM ユーザーが A のロールを偽装してログインする | ||
リソースディレクトリメンバー | 管理アカウントの RAM ユーザーがメンバーの RAM ロールを偽装してログインする | |
メンバーの RAM ユーザーを介してログインする | ||
クラウドアカウント (ルートユーザー) を介してログインする (非推奨) | ||
CloudSSO ユーザーが RAM ロールを介してログインする | ||
CloudSSO ユーザーが RAM ユーザーを介してログインする |
カスタム権限ポリシーの例
RAM ユーザーが Realtime Compute for Apache Flink をアクティブ化する (オプション 1)
RAM ユーザーが Realtime Compute for Apache Flink をアクティブ化する (オプション 2)
RAM ユーザーがサブスクリプションの Flink ワークスペースをリリースする
RAM ユーザーが従量課金の Flink ワークスペースをリリースする
RAM ユーザーがプロジェクトスペースのリソース割り当てを実行する
カスタムポリシー
Realtime Compute for Apache Flink 権限ポリシー
プロジェクトスペースの権限情報を設定する前に、まず作成されたワークスペースを表示する権限 (DescribeVvpInstances) を設定する必要があります。そうしないと、権限が不足しているというエラーが報告されます。
Flink ワークスペース
{
"Version": "1",
"Statement": [
{
"Action": [
"stream:CreateVvpInstance",
"stream:DescribeVvpInstances",
"stream:DeleteVvpInstance",
"stream:RenewVvpInstance",
"stream:ModifyVvpPrepayInstanceSpec",
"stream:ModifyVvpInstanceSpec",
"stream:ConvertVvpInstance",
"stream:QueryCreateVvpInstance",
"stream:QueryRenewVvpInstance",
"stream:QueryModifyVvpPrepayInstanceSpec",
"stream:QueryConvertVvpInstance"
],
"Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#InstanceId}",
"Effect": "Allow"
}
]
}action | 説明 |
CreateVvpInstance | Realtime Compute for Apache Flink を購入します。 |
DescribeVvpInstances | ワークスペースを表示します。 |
DeleteVvpInstance | Flink ワークスペースをリリースします。 |
RenewVvpInstance | ワークスペースを更新します (サブスクリプション)。 |
ModifyVvpPrepayInstanceSpec | サブスクリプションワークスペースをスケールします。 |
ModifyVvpInstanceSpec | 従量課金ワークスペースの最大クォータを調整します。 |
ConvertVvpInstance | ワークスペースの課金方法を変更します。 |
QueryCreateVvpInstance | ワークスペース作成の価格をクエリします。 |
QueryRenewVvpInstance | ワークスペース更新の価格をクエリします。 |
QueryModifyVvpPrepayInstanceSpec | ワークスペースのスケーリング価格をクエリします。 |
QueryConvertVvpInstance | 従量課金からサブスクリプションへの変換価格をクエリします。 |
Realtime Compute for Apache Flink の購入とワークスペースの表示については、Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId} を "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/*" に変更できます。
Flink プロジェクトスペース
{
"Version": "1",
"Statement": [
{
"Action": [
"stream:CreateVvpNamespace",
"stream:DeleteVvpNamespace",
"stream:ModifyVvpPrepayNamespaceSpec",
"stream:ModifyVvpNamespaceSpec",
"stream:DescribeVvpNamespaces"
],
"Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId}/vvpnamespace/{#namespace}",
"Effect": "Allow"
}
]
}action | 説明 |
CreateVvpNamespace | プロジェクトスペースを作成します。 |
DeleteVvpNamespace | プロジェクトスペースを削除します。 |
ModifyVvpPrepayNamespaceSpec | サブスクリプションプロジェクトスペースのリソースを変更します。 |
ModifyVvpNamespaceSpec | 従量課金プロジェクトスペースのリソースを変更します。 |
DescribeVvpNamespaces | プロジェクトのリストを表示します。 プロジェクトスペースのリストを表示します。
このポリシーを設定した後、ターゲットワークスペース ID の左側にある |
プロジェクトスペースの作成とプロジェクトスペースリストの表示については、"Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId}/vvpnamespace/{#namespace}", を "Resource": "acs:stream:{#regionId}:{#accountId}:vvpinstance/{#instanceId}/vvpnamespace/*", に変更できます。
関連サービスの権限操作
ECS 関連の操作
OSS 関連の操作
ARMS 関連の操作
VPC 関連の操作
RAM 関連の操作
TAG 関連の権限ポイント
DLF 関連の権限操作
関連資料
複数のユーザーが Flink プロジェクトスペースを共同で使用して、Realtime Compute 開発コンソールでジョブ開発、運用、メンテナンス、その他の関連操作を実行する場合は、プロジェクトスペースの権限を付与する必要があります。詳細については、「開発コンソールの権限付与」をご参照ください。
誤ってロールを削除したり、権限付与ポリシーを変更したりして、Realtime Compute for Apache Flink サービスが利用できなくなった場合はどうすればよいですか?
「現在のアカウントには権限がありません。ロール管理者に連絡してください」というメッセージをどのように処理すればよいですか?


 アイコンをクリックして、そのワークスペースで作成されたプロジェクトスペースのリストを表示できます。特定のプロジェクトスペースの開発コンソールにもアクセスする必要がある場合は、対応するプロジェクトスペースのジョブ開発権限を付与される必要があります。詳細については、「
アイコンをクリックして、そのワークスペースで作成されたプロジェクトスペースのリストを表示できます。特定のプロジェクトスペースの開発コンソールにもアクセスする必要がある場合は、対応するプロジェクトスペースのジョブ開発権限を付与される必要があります。詳細については、「