Create, modify, disable, or delete collection rules for cloud services in your associated project after enabling log collection in Log Audit Service.
Procedure
Console
Go to the collection rule page.
Log on to the Simple Log Service console. In the Log Application section, click the Audit & Security tab. Then, click Log Audit Service (New Version).
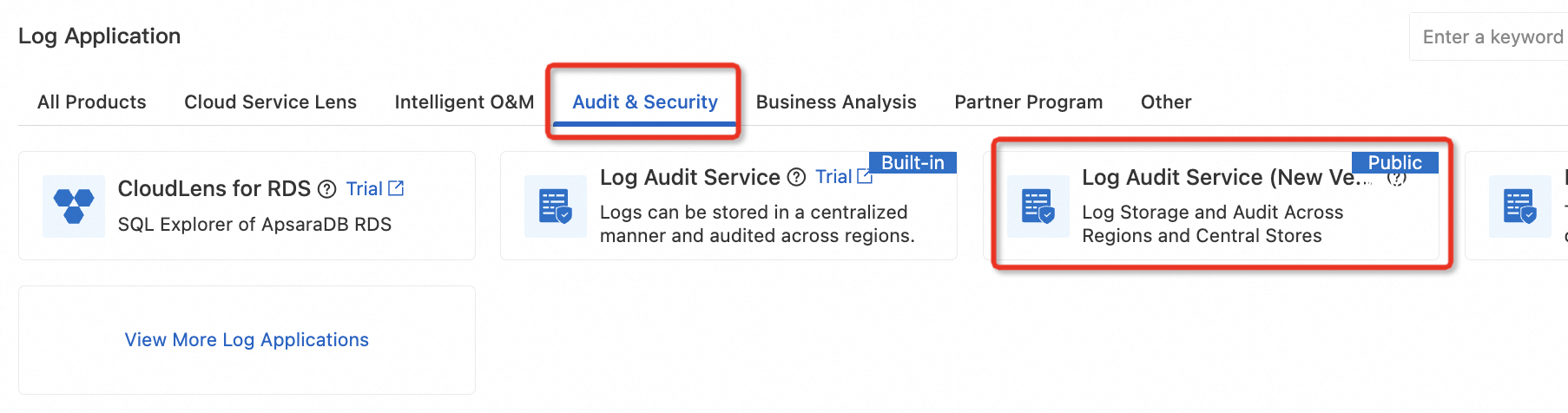
Click the target project name. On the Rules tab, click Create Collection Rule to create a collection rule.
Create, modify, disable, or delete collection rules as needed.
 Important
ImportantWhen modifying a collection rule, you cannot modify the Cloud Service Name or Log Type parameter. The Cloud Service Name parameter specifies the cloud service code.
Multiple collection rules of different log types can be created for a cloud service. The collection rules are merged and applied when the system collects logs from a cloud service instance. Log collection is disabled for the cloud service instance only when all collection rules of the cloud service are disabled or deleted.
If you disable or delete all collection rules of a cloud service, log collection is disabled only for the cloud service instances whose logs have been collected based on the collection rules. For other cloud service instances, log collection remains enabled if you have enabled log collection in the console of the cloud service or in the Simple Log Service console using a CloudLens application.
Collection rule parameters
Basic parameters
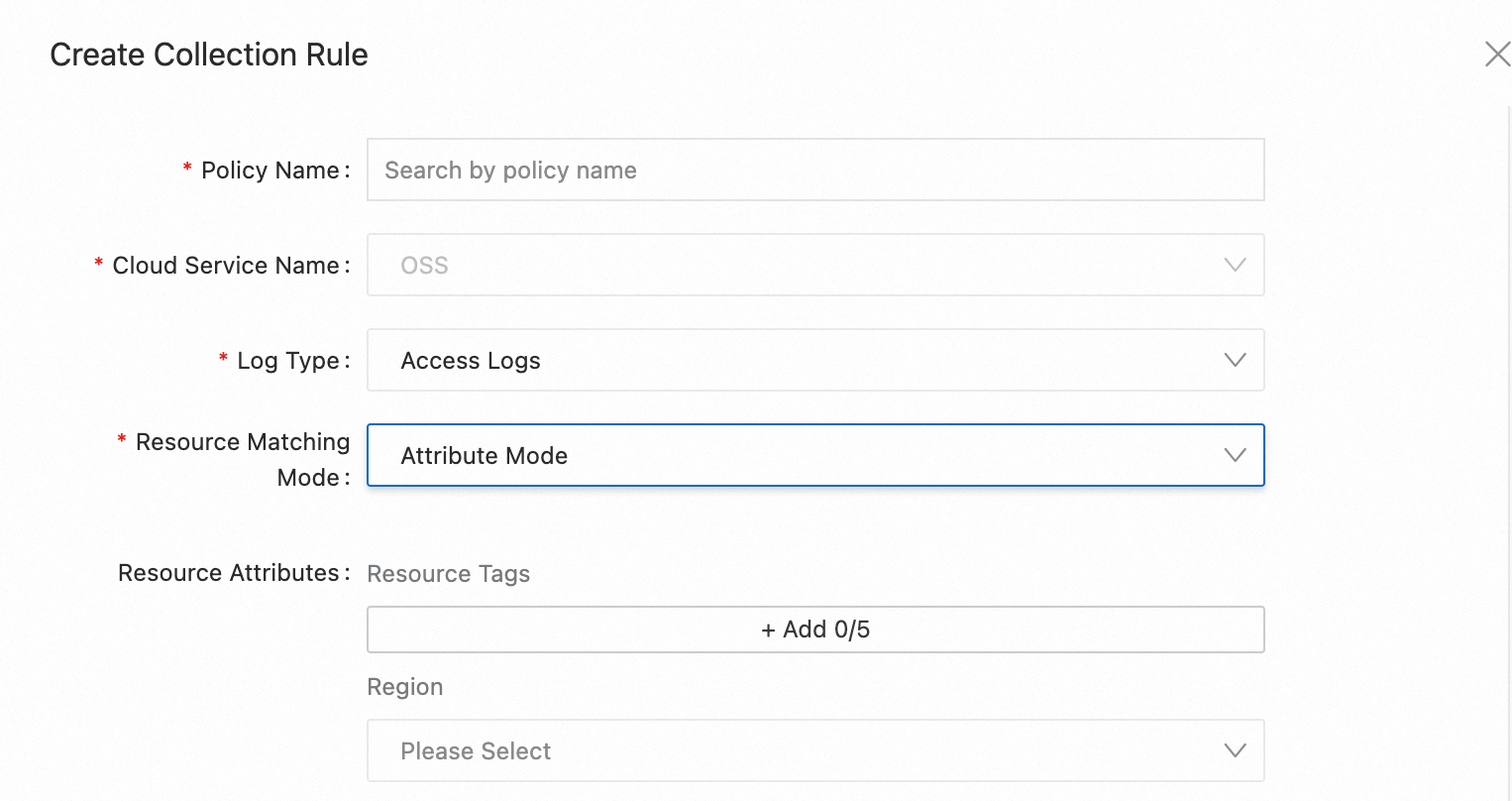
Parameter | Description |
Rule Name | The collection rule name. Must be globally unique within an Alibaba Cloud account, 3 to 63 characters, and start with a letter. |
Cloud Service Name | The name of the cloud service. For more information, see Usage notes of cloud service log collection. |
Log Type | The type of logs. For more information, see Usage notes of cloud service log collection. |
Resource Matching Mode |
|
Instances | The instances from which logs are collected. Effective only when Resource Matching Mode is set to Instance Mode. Logs are collected only from selected instances. Note If there are no options in the Instances drop-down list, manual input is allowed. When you create at least one collection rule for the cloud service, the drop-down list automatically displays the names of existing instances. |
Region, Resource Tags |
|
Global Log Storage Region | The destination region for global log collection. Available only when the Log Type parameter is set to a global log type. Configure this parameter if no region is specified for your project.
|
Centralized storage configuration
Logs are written to a centralized destination store after data transformation. When writing to multiple destination stores, ensure all stores exist. To delete a destination store, remove related collection rules first to avoid affecting other stores.
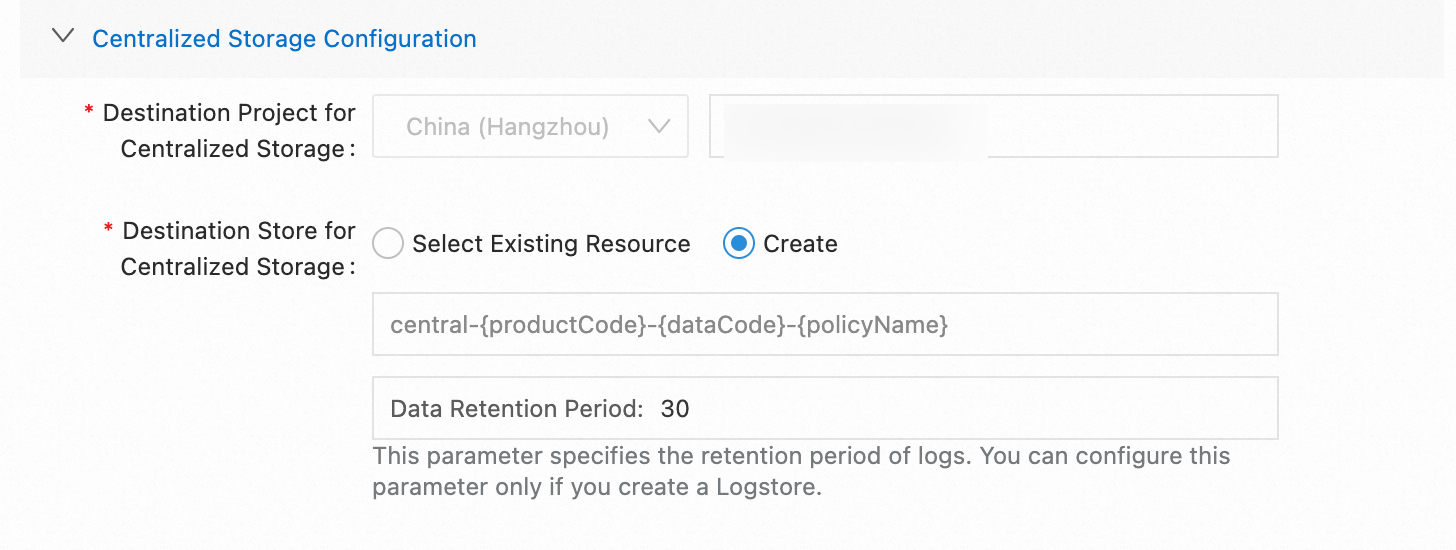
Parameter | Description |
Destination Project for Centralized Storage | The destination project for centralized storage. Fixed to the associated project of your collection rule. This parameter cannot be modified. |
Destination Store for Centralized Storage |
|
Data Retention Period | Takes effect only when creating a logstore. Specifies the log retention period. Configuring this parameter does not change retention periods of existing logstores. |
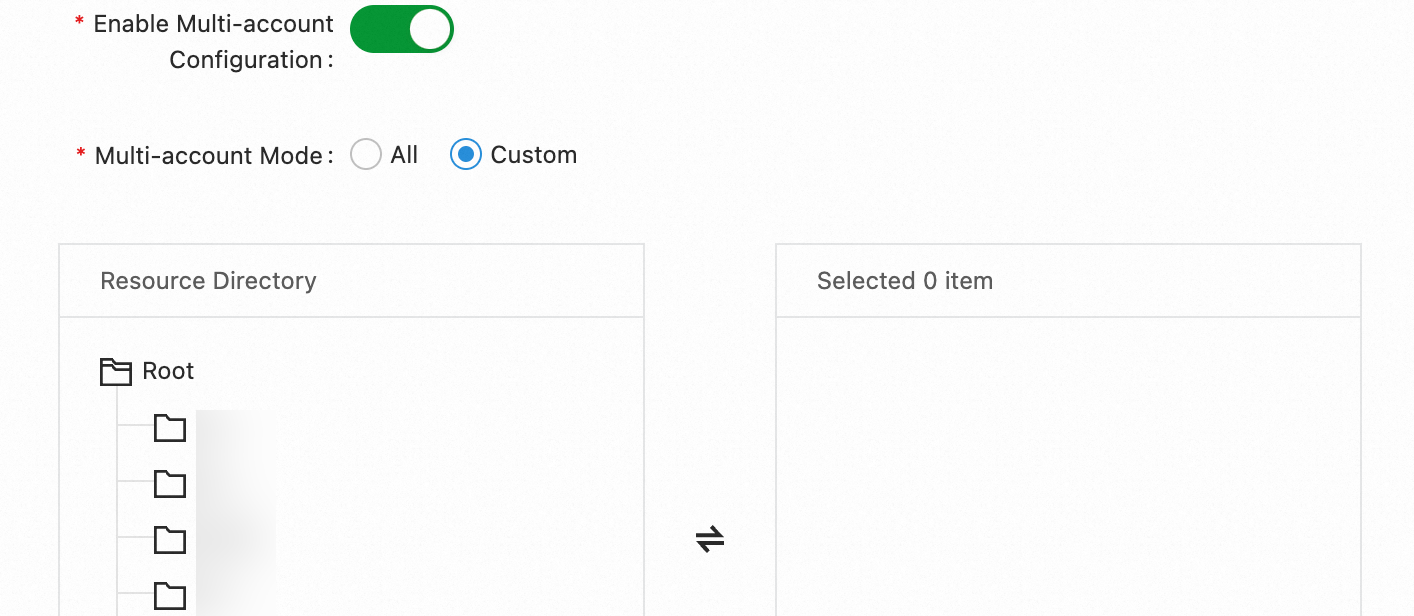
Multi-account configuration
Create a resource directory.
Only the management account of a resource directory or a delegated administrator account can enable the multi-account mode. For more information, see What is Resource Directory.
Use a management account to log on to the Resource Management console and enable a resource directory.
Create members in the resource directory or invite existing Alibaba Cloud accounts to join the resource directory. Then, move all members to the folders.
For more information, see Create a member, Invite an Alibaba Cloud account to join a resource directory, and Move a member.
Configure the Multi-account Mode parameter.
Multi-account Mode
Description
All
Collect the specified cloud service logs from all members in the resource directory.
If you use a management account or delegated administrator account to create the collection rule, all members in the resource directory are affected. If a member is added to the resource directory, the collection rule is automatically applied to the member. If a member is deleted from the resource directory, the application scope of the rule is adjusted.
Custom
Collect the specified cloud service logs from some members in the resource directory.
If you use a management account or delegated administrator account to create the collection rule, only the selected members in the resource directory are affected. Other members are not affected.
Common error codes, error messages, and descriptions
Error code | Error message | Description |
DeregisterDA.Deny.TrustedService | This operation cannot be performed because the management account is already configured for Resource Directory through the unified access API. Please update or delete the existing configuration first. | This error occurs when you try to remove a resource directory, trusted service, or delegated administrator account because collection rules still exist in the delegated administrator account. Solution:
|
NotMatch | productCode or dataCode are not match to current productCode or dataCode | When modifying a collection rule, you are not allowed to modify the Cloud Service Name or Log Type parameter in the rule. Otherwise, a mismatch error occurs. |
PolicyNotExist | the collection policy does not exist | The collection rule requested for a query or delete operation does not exist. |
InvalidSLR | SLR not exist or created failed | The service-linked role does not exist or fails to be created. When you create a collection rule in the new version of Log Audit Service, the system automatically creates a service-linked role named AliyunServiceRoleForSLSAudit in the current Alibaba Cloud account and the members of the resource directory created. For more information, see Manage the AliyunServiceRoleForSLSAudit service-linked role. |
InvalidRAM | RAM is not enough for execute this action, please check current account ram policy of this operation | The Resource Access Management (RAM) user does not have the permissions to manage the new version of Log Audit Service. For more information, see Grant a RAM user the permissions to use the new version of Log Audit Service. |
InvalidProductData | Invalid Product Code or Data Code | The Cloud Service Name or Log Type parameter is invalid. |
InvalidProductData | Invalid Policy Name | The Policy Name parameter is invalid. |
InvalidPolicyConfig | Policy Config : resourceMode should be all/instanceMode/attributeMode | You must set the Resource Matching Mode parameter to All Resources, Instance Mode, or Attribute Mode. |
InvalidPolicyConfig | Policy Config : resourceMode should be all for lens global log type | For global logs, you must set the Resource Matching Mode parameter to All Resources. |
InvalidPolicyConfig | Policy Config : resourceMode should be attribute mode for security log type | For security logs, you must set the Resource Matching Mode parameter to Attribute Mode. |
InvalidPolicyConfig | Policy Config : you should set at least one center region for security log type | For security logs, you must specify at least one region as the region attribute. |
InvalidPolicyConfig | Policy Config : this productCode and dataCode not allowed to config instance ids | For security logs, you cannot configure the Instances parameter. |
InvalidConfig | Please check if the project/logstore belongs to you or the project/logstore in right region | The destination project or logstore for centralized storage does not belong to the current account or the specified region is not the region where the current logstore resides. |
InvalidConfig | policyCode and dataCode is required when you need to list policy by instanceId that meet the filter conditions | If you want to query collection rules by instance ID, you must configure the Cloud Service Name and Log Type parameters. |
InvalidCentralizeConfig | when centralizeEnabled, you should set at least one centralize config | You must configure the Destination Store for Centralized Storage parameter after you enable centralized storage configuration. |
InvalidCentralizeConfig | centralize config is necessary for security product log collection | For security logs, you must enable centralized storage configuration. |
InvalidCentralizeConfig | dest project, dest logstore, dest region, dest ttl should not be empty when centralize enabled | You must configure the Destination Project for Centralized Storage, Destination Store for Centralized Storage, and Data Retention Period parameters after you enable centralized storage configuration. |
InvalidCentralizeConfig | dest project invalid for centralize config | The Destination Project for Centralized Storage parameter is invalid. |
InvalidCentralizeConfig | dest logstore invalid for centralize config | The Destination Store for Centralized Storage parameter is invalid. |
InvalidCentralizeConfig | dest region invalid for centralize config | The region where the destination project for centralized storage resides is invalid. |
InvalidResourceDirectoryConfig | Policy ResourceDirectory Config : when you set resource directory, you should set account group type first | When configuring a resource directory, you must configure the Multi-account Mode parameter. |
InvalidResourceDirectoryConfig | Policy ResourceDirectory Config: instance mode not allowed to set resource directory | If the multi-account mode is enabled, the Resource Matching Mode parameter cannot be set to Instance Mode. |
InvalidResourceDirectoryConfig | Policy ResourceDirectory Config : members should not be empty | If you set the Multi-account Mode parameter to Custom, you must specify members. |
InvalidResourceDirectoryConfig | Policy ResourceDirectory Config : centralize config enabled is required for resource directory | You must enable centralized storage when creating a resource directory because resource directories are specific to the new version of Log Audit Service. |
InvalidResourceDirectoryConfig | Policy ResourceDirectory Config : the account resource directory not in use | No resource directory is enabled in the current account. |
InvalidResourceDirectoryConfig | Policy ResourceDirectory Config : the account is neither a delegated admin nor a master, just a member account | The current account is not a management account or a delegated administrator account, but a member of the resource directory. A member cannot configure the multi-account mode in a collection rule. |
InvalidResourceDirectoryConfig | Policy ResourceDirectory Config : custom members include invalid account | After you set the Multi-account Mode parameter to Custom, invalid members are specified. |
InvalidDataConfig | Policy DataConfig: the data region is not valid | For global logs, the Global Log Storage Region parameter is invalid. |
InvalidDataConfig | Policy DataConfig: this kind of product is not allowed to set data config | You cannot configure the settings for non-global logs. |
InvalidDataConfig | Policy DataConfig: the data region already exist in other policy, you cannot change | For global logs, if you configure the Global Log Storage Region parameter, you cannot modify the parameter. |
References
If you use a RAM user to manage the new version of Log Audit Service, use an Alibaba Cloud account to grant the required permissions to the RAM user. For more information, see Grant a RAM user the permissions to use the new version of Log Audit Service.
For more information about the log types, default project and logstore names, and billing details of supported cloud services, see Usage notes of cloud service log collection.
If you want to collect cloud service logs from multiple Alibaba Cloud accounts, enable a resource directory. Then, use the management account of the resource directory or a delegated administrator account to configure collection rules for the required cloud services. After you configure the collection rules, the cloud service logs are collected from the members of the resource directory to a specified project. For more information, see Usage notes of cloud service log collection.