Simple Log Service allows you to use Key Management Service (KMS) to encrypt data for secure storage. Static data protection is provided. This topic describes the data encryption mechanism of Simple Log Service and how to use KMS to encrypt data.
Prerequisites
KMS is activated. For more information, see Purchase a dedicated KMS instance.
Data encryption mechanism
Simple Log Service allows you to encrypt data by using the following methods:
Use the service key of Simple Log Service
Characteristics:
Ease-of-use: Simple Log Service is fully responsible for data encryption and key management. No additional operations are required, which reduces the management burden on users.
Key independence: An independent data encryption key is generated for each Logstore, which enhances data security.
Persistence: Data encryption keys do not expire, which ensures stable and durable data encryption.
Supported data encryption algorithms: Advanced Encryption Standard (AES) and SM4. By default, the AES algorithm is used.
Scenarios:
You want to implement data encryption in an efficient manner without the need to manage keys.
You do not have specific requirements for key management. You want service providers to manage keys.
You want to ensure the long-term validity and stability of data encryption keys.
Intended customers:
This method is suitable for small-sized enterprises and individual users who do not want to perform complex key management tasks and only want to encrypt data in a secure and simple manner.
Use the Bring Your Own Key (BYOK) feature
Characteristics:
Controllability: You can have full control over the lifecycle management of keys. You can create, rotate, and delete keys.
Flexibility: You can easily update or replace keys based on your business requirements, which improves data security and flexibility.
Proactivity: You must proactively manage keys. For example, you must create a customer master key (CMK) and grant users the permissions to use the CMK in the KMS console.
Scenarios:
An organization has strict security compliance requirements and wants to manage data encryption keys.
You want to manage and rotate data encryption keys to meet high security requirements.
You want to replace or delete keys in an efficient manner to protect data security when the keys are leaked or when other risks exist.
Intended customers:
This method is suitable for large-sized enterprises or financial institutions that have strict requirements for data protection and compliance, want to use custom key management policies, and have a dedicated support team that manages keys.
If your CMK is deleted or disabled, the related BYOK key becomes invalid.
If your CMK becomes invalid, all read and write requests to the related Logstore fail.
Limits
If you specify a data encryption method when you configure data encryption settings, you cannot switch to the other method after the configuration. In addition, you cannot change the encryption algorithm or the encryption type. You can only enable or disable the encryption feature by using the enable parameter. You must include the encrypt_conf parameter each time you request to update your Logstore.
For example, if you specify the encryption method based on the service key of Simple Log Service when you configure data encryption settings, you cannot switch to the encryption method based on the BYOK feature after the configuration.
Use the service key of Simple Log Service for encryption
When you call the CreateLogStore operation to create a Logstore or call the UpdateLogStore operation to modify a Logstore, add the encrypt_conf parameter to configure the encryption settings. For more information, see CreateLogStore or UpdateLogStore.
The following table describes the fields in the encrypt_conf parameter. Do not specify the user_cmk_info field.
| Parameter | Type | Description | Example |
|---|---|---|---|
| object | The data structure of the encryption configuration. | ||
| enable | boolean | Specifies whether to enable data encryption. Valid values:
| true |
| encrypt_type | string | The encryption algorithm. Valid values: default and sm4. If enable is set to true, you must configure this parameter. | default |
| user_cmk_info | EncryptUserCmkConf | Optional. If you configure this parameter, the bring-your-own-key (BYOK) key is used. If you do not configure this parameter, the service key of Simple Log Service is used. | { "cmk_key_id" : "f5136b95-2420-ab31-xxxxxxxxx" "arn" : "acs:ram::13234:role/logsource" "region_id" : "cn-hangzhou" } |
Use the BYOK feature for encryption
Prerequisites
KMS is activated. For more information, see Purchase a dedicated KMS instance.
Step 1: Complete authorization
Before you can use this encryption method, you must authorize Simple Log Service to access KMS.
Log on to the Resource Access Management (RAM) console.
Create a RAM role whose trusted entity is an Alibaba Cloud service based on the following figure.
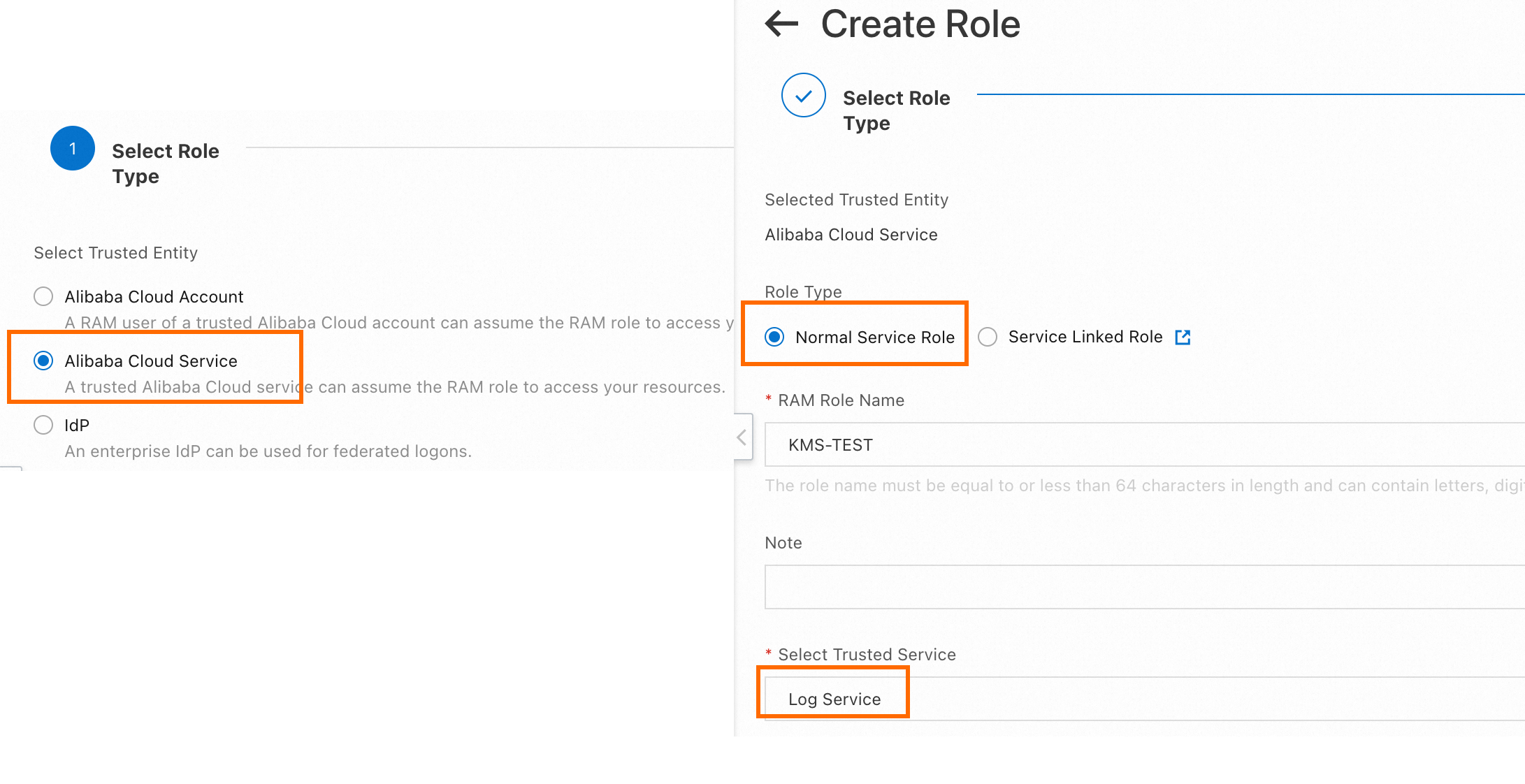
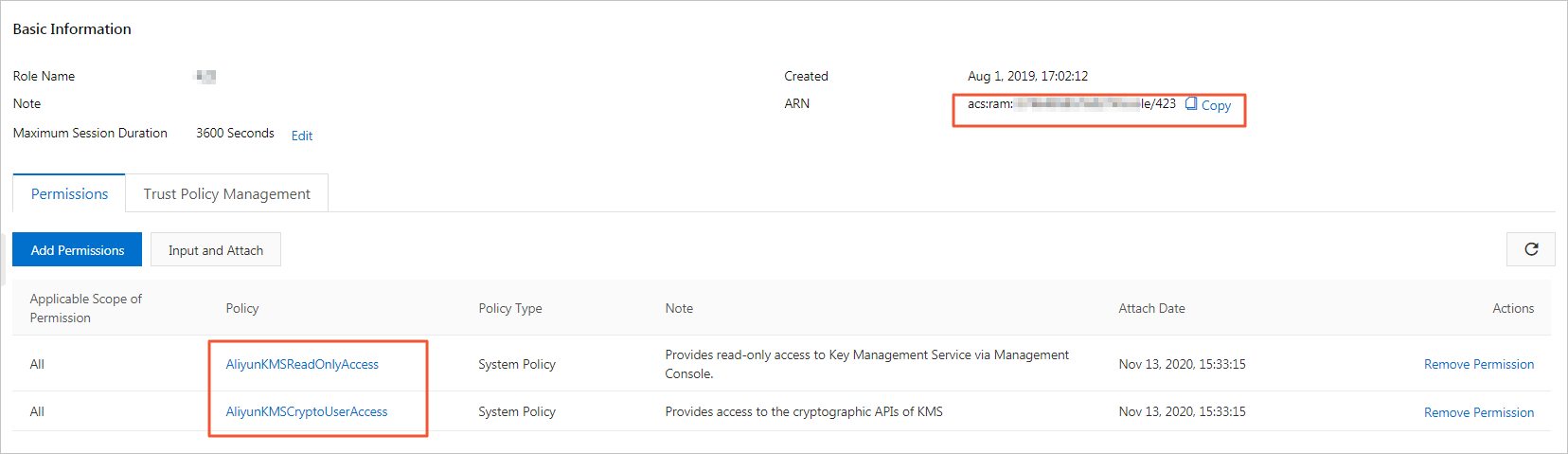
Grant the AliyunKMSReadOnlyAccess and AliyunKMSCryptoUserAccess permissions to the RAM role. For more information, see Grant permissions to a RAM role.
If you use a RAM user to encrypt data, you must create a custom policy and grant permissions to the RAM user.
In the following policy, replace <role-name> in the Resource element with the Alibaba Cloud Resource Name (ARN) of the RAM role that is created. For more information about how to view the ARN of a RAM role, see How do I view the ARN of a RAM role?
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": "ram:PassRole", "Resource": "acs:ram::<account-id>:role/<role-name>" } ] }
Step 2: Configure data encryption settings
After you configure data encryption settings, you cannot change the encryption algorithm or the encryption type. You can only enable or disable the encryption feature by using the enable parameter. You must include the encrypt_conf parameter each time you request to update your Logstore.
For an existing Logstore, you must call the UpdateLogStore operation and include the encrypt_conf parameter to configure data encryption settings.
Before you call the UpdateLogStore operation, you must call the GetLogStore operation to obtain the original configurations of the Logstore. After you modify the configurations, add the configurations after modification to the UpdateLogStore operation.
The following table describes the fields in the encrypt_conf parameter. The user_cmk_info field is required.
| Parameter | Type | Description | Example |
|---|---|---|---|
| object | The data structure of the encryption configuration. | ||
| enable | boolean | Specifies whether to enable data encryption. Valid values:
| true |
| encrypt_type | string | The encryption algorithm. Valid values: default and sm4. If enable is set to true, you must configure this parameter. | default |
| user_cmk_info | EncryptUserCmkConf | Optional. If you configure this parameter, the bring-your-own-key (BYOK) key is used. If you do not configure this parameter, the service key of Simple Log Service is used. | { "cmk_key_id" : "f5136b95-2420-ab31-xxxxxxxxx" "arn" : "acs:ram::13234:role/logsource" "region_id" : "cn-hangzhou" } |
EncryptUserCmkConf data structure
Parameter | Type | Description | Example |
cmk_key_id | string | The ID of the customer master key (CMK) if you use the bring-your-own-key (BYOK) key. | f5136b95-2420-ab31-xxxxxxxxx |
arn | string | The ARN of the RAM role created in Step 1. | acs:ram::13234:role/logsource |
region_id | string | The ID of the region where the CMK resides. | cn-hangzhou |
| Parameter | Type | Description | Example |
|---|---|---|---|
| object | The data structure of the user-defined encryption configuration. | ||
| cmk_key_id | string | The ID of the customer master key (CMK) if you use the bring-your-own-key (BYOK) key. | f5136b95-2420-ab31-xxxxxxxxx |
| arn | string | The Alibaba Cloud Resource Name (ARN) of the Resource Access Management (RAM) role. | acs:ram::13234:role/logsource |
| region_id | string | The ID of the region where the CMK resides. | cn-hangzhou |
encrypt_conf = {
"enable" : True, # Specifies whether to enable data encryption.
"encrypt_type" : "default", # The encryption algorithm. Valid values: default and m4.
"user_cmk_info" : # Optional. If you configure this field, a BYOK key is used. If you do not configure this field, the service key of Simple Log Service is used.
{
"cmk_key_id" : "" # The ID of the CMK to which the BYOK key belongs. Example: f5136b95-2420-ab31-xxxxxxxxx.
"arn" : "" # The ARN of the RAM role created in Step 1.
"region_id" : "" # The ID of the region where the CMK resides.
}
}References
For more information, refer to the following operations of Simple Log Service: