Application Load Balancer (ALB) Ingresses provide powerful traffic routing capabilities based on ALB instances. Compatible with NGINX Ingress, they support complex routing, automatic certificate discovery, and the HTTP, HTTPS, and QUIC protocols. ALB Ingresses are ideal for cloud-native applications that require high elasticity and Layer 7 load balancing for heavy traffic. This topic demonstrates how to deploy an ALB Ingress in a Container Service for Kubernetes (ACK) cluster to expose applications to external traffic.
Background information
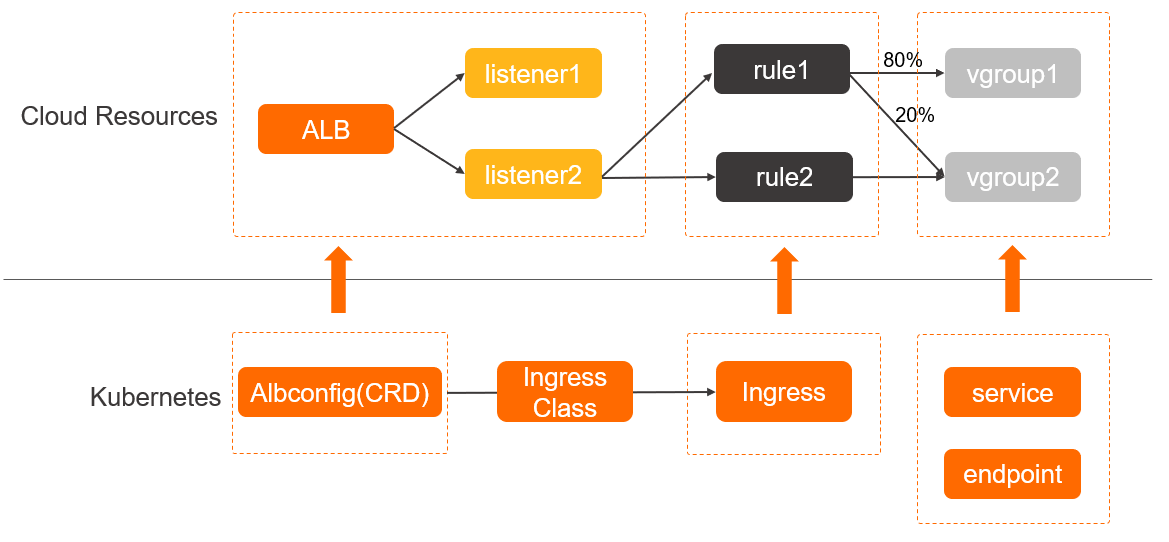
Terms related to ALB Ingresses:
ALB Ingress controller: a Kubernetes component that manages Ingresses. The ALB Ingress controller serves as an entry point in a cluster and routes external traffic to specific Services. It watches the Kubernetes API server for changes to Ingress resources and dynamically generates AlbConfigs to reflect those changes. The controller then creates or updates the corresponding ALB instances, listeners, routing rules, and backend server groups.
AlbConfig CRD: Custom resource definitions (CRDs) extend the Kubernetes API and allow you to create custom resources. An AlbConfig corresponds to one ALB instance.
IngressClass: An IngressClass is an attribute of a Kubernetes Ingress that defines the class or identifier of an Ingress controller. IngressClasses allow you to use multiple Ingress controllers in a cluster and specify a controller for each Ingress.
Ingress: An Ingress is a resource object in Kubernetes that defines the forwarding and access rules for external traffic. The Ingress Controller forwards traffic based on Ingresses. You can configure forwarding rules in ALB Ingresses by using annotations. After configuration, HTTP/HTTPS requests are forwarded to the corresponding Services based on the configured rules.
Service: In Kubernetes, a Service is an abstract resource object that defines a set of pods that have the same logical function and allows you to access the pods by using a fixed virtual IP address and port.
A Service provides access to an application and allows other applications or services to communicate with backend pods by accessing the virtual IP address and port of the Service. This eliminates the need to obtain the IP address and port of a specific pod. A single Service can represent multiple replicated Pods that perform the same function.
The following figure shows the relationship between an ALB instance and an ALB Ingress.
Limits
If you use the Flannel network plug-in, the backend Services of the ALB Ingress must be of the NodePort or LoadBalancer type.
The names of AlbConfigs, namespaces, Ingresses, and Services cannot start with aliyun.
Earlier NGINX Ingress controller versions cannot recognize the
spec: ingressClassNamefield of an Ingress. If both NGINX and ALB Ingress controllers are running in your ACK cluster, an older NGINX controller might incorrectly reconcile your ALB Ingresses. To prevent this, update your NGINX Ingress controller or use annotations to specify the IngressClass for your ALB Ingresses. For more information, see Update the NGINX Ingress controller or Advanced ALB Ingress configurations.
Scenarios
This topic demonstrates how to use an ALB Ingress to forward requests to different backend Services based on the URL path. In this example, two NGINX services (coffee and tea) are deployed across four pods.
Frontend request | Forwarded to |
|
|
|
|
Prerequisites
An ACK managed cluster or ACK dedicated cluster is created and the cluster runs Kubernetes 1.18 or later. For more information, see Create an ACK managed cluster and Create an ACK dedicated cluster (discontinued).
Optional. kubectl is used to connect to the cluster.
A domain name is registered, and an Internet content provider (ICP) number is obtained for the domain name. For more information, see Register a generic domain name and ICP filing process.
Step 1: Install the ALB Ingress controller
To use the ALB Ingress, install the ALB Ingress controller first.
Install when creating a cluster
During the creation of an ACK managed cluster or an ACK dedicated cluster, select ALB Ingress in the Ingress section.
You can set Gateway Source to New, Existing, or None.
Instance source | Description | Result | |
New (Recommended) |
| The controller will automatically create an AlbConfig named | |
Existing (Recommended) | You can select an existing ALB instance from the drop-down menu for reuse. Basic ALB instances are not supported. For more information, see Reuse an existing ALB instance. | ||
None (Optional) | Only the ALB Ingress controller is installed. No ALB instance is created. | Important The controller will not create the corresponding resources. You must manually create an AlbConfig and an IngressClass. | |
Install for an existing cluster
Log on to the ACK console. In the left navigation pane, click Clusters.
On the Clusters page, find the one you want to manage and click its name. In the left navigation pane, click Add-ons.
On the Add-ons page, click the Networking tab. In the Networking section, find the ALB Ingress Controller card and click Install in the lower-right corner.
In the Install ALB Ingress Controller dialog box, select New, Existing, or None for the Gateway Source as appropriate, and click OK.
Instance source
Description
Result
New (Recommended)
Network Type: You can create an ALB instance for Internet or Intranet as needed. For billing details, see Billing rules.
VPC: This value is the same as the VPC in which the cluster resides and cannot be modified.
vSwitch: The vSwitches corresponding to the zones supported by ALB under this VPC are displayed. You need to select two vSwitches in different zones. Otherwise, two available vSwitches will be automatically selected. You can also create a new vSwitch by clicking Create vSwitch.
The controller will automatically create an AlbConfig named
alband the corresponding IngressClass resource. In AlbConfig, a listener with port 80 and HTTP is configured by default. For more information about listener extensions, see Create an HTTP listener.Existing (Recommended)
You can select an existing ALB instance from the drop-down menu for reuse. Basic ALB instances are not supported. For more information, see Reuse an existing ALB instance.
None (Optional)
Only the ALB Ingress controller is installed. No ALB instance is created.
ImportantThe controller will not create the corresponding resources. You must manually create an AlbConfig and an IngressClass.
If you want to use an ALB Ingress to access Services deployed in an ACK dedicated cluster, you need to first authorize the cluster to access the ALB Ingress controller. For more information, see Authorize an ACK dedicated cluster to access the ALB Ingress controller.
Step 2: Deploy a backend Service
ACK console
Log on to the ACK console. In the left navigation pane, click Clusters.
On the Clusters page, find the cluster you want to manage and click its name. In the left navigation pane, choose .
Click Create from YAML.
Sample Template: Select Custom.
Template: Paste the following code to the code editor. This YAML file is used to deploy two Deployments named
coffeeandtea, and two Services namedcoffee-svcandtea-svc.
After you complete the configurations, click Create. The Created message appears.
Perform the following operations to verify that the Deployments and Services are created:
In the left-side navigation pane, choose Workloads > Deployments. The Deployments named coffee and tea are displayed.
In the left-side navigation pane, choose Network > Services. The Services named coffee-svc and tea-svc are displayed.
kubectl
Create a file named cafe-service.yaml. Copy and paste the following content to the file. The file is used to deploy two Deployments named
coffeeandteaand two Services namedcoffee-svcandtea-svc.Run the following command to deploy the Deployments and Services:
kubectl apply -f cafe-service.yamlExpected output:
deployment "coffee" created service "coffee-svc" created deployment "tea" created service "tea-svc" createdRun the following command to view the status of the Deployments and Services:
Run the following command to view the status of the Deployments:
kubectl get deploymentExpected output:
NAME READY UP-TO-DATE AVAILABLE AGE coffee 1/2 2 1 2m26s tea 1/1 1 1 2m26sRun the following command to query the status of the Services:
kubectl get svcExpected output:
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE coffee-svc NodePort 172.16.XX.XX <none> 80:32056/TCP 9m38s tea-svc NodePort 172.16.XX.XX <none> 80:31696/TCP 9m38s
Step 3: Create an AlbConfig
If you set Gateway Source to New or Existing in Step 1: Install the ALB Ingress controller, the controller automatically creates an AlbConfig named alb and an IngressClass named alb. In this case, skip this step.
ACK console
Log on to the ACK console. In the left navigation pane, click Clusters.
On the Clusters page, find the target cluster and click its name. In the navigation pane on the left, choose .
On the Custom Resources page, click the CRDs tab and click Create from YAML.
Sample Template: Select Custom.
Template: Paste the following code to the code editor.
The following table describes the parameters that you can configure.
Parameter
Required
Description
metadata.name
Yes
The name of the AlbConfig.
NoteThe name of the AlbConfig must be unique in the cluster. When you create an AlbConfig, make sure that the AlbConfig name is unique to prevent conflicts.
spec.config.name
No
The name of the ALB instance.
spec.config.addressType
No
The network type of the ALB instance. Valid values:
Internet (default): Internet-facing. The ALB instance provides services to the Internet and is accessible over the Internet.
NoteTo allow an ALB instance to provide Internet-facing services, the ALB instance needs to be associated with an EIP. If you use an Internet-facing ALB instance, you are charged EIP configuration fees (public IP retention fees) and bandwidth or data transfer fees for the EIPs. For more information, see Pay-as-you-go.
Intranet: internal-facing. An internal-facing ALB instance provides services within a VPC and cannot be accessed over the Internet.
spec.config.zoneMappings
Yes
The IDs of the vSwitches. For more information about how to create a vSwitch, see Create and manage vSwitches.
NoteThe specified vSwitch must be deployed in a zone supported by the ALB instance and deployed in the same VPC as the cluster. For more information about the regions and zones supported by ALB, see Regions and zones.
ALB supports multi-zone deployment. If the current region supports two or more zones, select vSwitches in at least two zones to ensure high availability.
spec.listeners
No
The listening port and protocol of the ALB instance. In this example, an HTTP listener that uses port 80 is configured.
A listener defines how ALB receives traffic. We recommend that you retain the listener configuration. Otherwise, you must create a listener before you can use ALB Ingresses.
After the configuration is complete, click Create. The Created message appears.
Check whether the ALB instance is created:
Log on to the ALB console.
In the top navigation bar, select the region in which the ALB instance is deployed.
On the Instances page, an ALB instance named alb-test is displayed in the instance list. This indicates that the ALB instance is created.
kubectl
Create a file named alb-test.yaml and copy the following content to the file. The file is used to create an AlbConfig.
The following table describes the parameters that you can configure.
Parameter
Required
Description
metadata.name
Yes
The name of the AlbConfig.
NoteThe name of the AlbConfig must be unique in the cluster. When you create an AlbConfig, make sure that the AlbConfig name is unique to prevent conflicts.
spec.config.name
No
The name of the ALB instance.
spec.config.addressType
No
The network type of the ALB instance. Valid values:
Internet (default): Internet-facing. The ALB instance provides services to the Internet and is accessible over the Internet.
NoteTo allow an ALB instance to provide Internet-facing services, the ALB instance needs to be associated with an EIP. If you use an Internet-facing ALB instance, you are charged EIP configuration fees (public IP retention fees) and bandwidth or data transfer fees for the EIPs. For more information, see Pay-as-you-go.
Intranet: internal-facing. An internal-facing ALB instance provides services within a VPC and cannot be accessed over the Internet.
spec.config.zoneMappings
Yes
The IDs of the vSwitches. For more information about how to create a vSwitch, see Create and manage vSwitches.
NoteThe specified vSwitch must be deployed in a zone supported by the ALB instance and deployed in the same VPC as the cluster. For more information about the regions and zones supported by ALB, see Regions and zones.
ALB supports multi-zone deployment. If the current region supports two or more zones, select vSwitches in at least two zones to ensure high availability.
spec.listeners
No
The listening port and protocol of the ALB instance. In this example, an HTTP listener that uses port 80 is configured.
A listener defines how ALB receives traffic. We recommend that you retain the listener configuration. Otherwise, you must create a listener before you can use ALB Ingresses.
Run the following command to create an AlbConfig object:
kubectl apply -f alb-test.yamlExpected output:
albconfig.alibabacloud.com/alb-demo created
Step 4: Create an IngressClass
We recommend that you create an IngressClass for each AlbConfig.
If you set Gateway Source to New or Existing in Step 1: Install the ALB Ingress controller, the controller automatically creates an AlbConfig named alb and an IngressClass named alb. In this case, skip this step.
ACK console
Log on to the ACK console. In the left navigation pane, click Clusters.
On the Clusters page, find the target cluster and click its name. In the navigation pane on the left, choose .
On the Custom Resources page, click the CRDs tab and click Create from YAML.
Sample Template: Select Custom.
Template: Paste the following code to the code editor.
The following table describes the parameters that you can configure.
Parameter
Required
Description
metadata.name
Yes
The name of the IngressClass.
NoteThe name of an IngressClass must be unique in the cluster. Therefore, when you create an IngressClass, make sure that the IngressClass name is unique to prevent conflicts.
spec.parameters.name
Yes
The name of the associated AlbConfig.
After the configuration is complete, click Create. The Created message appears.
Perform the following operations to check whether the IngressClass is created:
In the left-side navigation pane, choose Workloads> Custom Resources.
Click the Resource Objects tab.
In the API Group search box, enter IngressClass. The IngressClass is displayed.
kubectl
Create a file named alb.yaml and copy the following content to the file:
The following table describes the parameters that you can configure.
Parameter
Required
Description
metadata.name
Yes
The name of the IngressClass.
NoteThe name of an IngressClass must be unique in the cluster. Therefore, when you create an IngressClass, make sure that the IngressClass name is unique to prevent conflicts.
spec.parameters.name
Yes
The name of the associated AlbConfig.
Run the following command to create an IngressClass resource:
kubectl apply -f alb.yamlExpected output:
ingressclass.networking.k8s.io/alb created
Step 5: Create an Ingress
ACK console
Log on to the ACK console. In the left navigation pane, click Clusters.
On the Clusters page, find the cluster you want and click its name. In the left-side pane, choose .
Click Create from YAML.
Sample Template: Select Custom.
Template: Paste the following code to the code editor.
The following table describes the parameters that you can configure.
Parameter
Required
Description
metadata.name
Yes
The name of the Ingress.
NoteThe name of an Ingress must be unique in the cluster. Therefore, when you create an Ingress, make sure that the Ingress name is unique to prevent conflicts.
spec.ingressClassName
Yes
The name of the associated IngressClass.
spec.rules.host
No
The domain name of the HTTP host header. You must set this parameter to a custom domain name.
When you access the domain name, such as http://demo.domain.ingress.top, in a browser, the browser automatically adds the Host: demo.domain.ingress.top header when sending an HTTP request. This way, the server identifies the destination host based on the header. In Kubernetes, the host field in an Ingress rule is used to match the host header in a request. If the host header is matched, the request is sent to the corresponding backend Service.
NoteIf you specify a custom domain name, make sure that the domain name has an ICP number. Otherwise, the domain name may fail to be resolved. For more information, see ICP filing overview.
If this parameter is not configured, the Ingress rule matches all requests that are sent to the Ingress controller.
spec.rules.http.paths.path
Yes
The URL.
spec.rules.http.paths.pathType
Yes
The URL matching rule. For more information, see Forward requests based on URL paths.
spec.rules.http.paths.backend.service.name
Yes
The name of the Service that you created.
spec.rules.http.paths.backend.service.port.number
Yes
The port number of the backend Service. This port must be valid to ensure that requests are routed correctly.
After the configuration is complete, click Create. The Created message appears.
Check that the Ingress is created:
In the left-side navigation pane, choose Network > Ingresses. The Ingress named cafe-ingress is displayed.
In the Endpoint column of cafe-ingress, you can view the endpoint.
kubectl
Create a file named cafe-ingress.yaml and paste the following content to the file. The file is used to create an Ingress.
The following table describes the parameters that you can configure.
Parameter
Required
Description
metadata.name
Yes
The name of the Ingress.
NoteThe name of an Ingress must be unique in the cluster. Therefore, when you create an Ingress, make sure that the Ingress name is unique to prevent conflicts.
spec.ingressClassName
Yes
The name of the associated IngressClass.
spec.rules.host
No
The domain name of the HTTP host header. You must set this parameter to a custom domain name.
When you access the domain name, such as http://demo.domain.ingress.top, in a browser, the browser automatically adds the Host: demo.domain.ingress.top header when sending an HTTP request. This way, the server identifies the destination host based on the header. In Kubernetes, the host field in an Ingress rule is used to match the host header in a request. If the host header is matched, the request is sent to the corresponding backend Service.
NoteIf you specify a custom domain name, make sure that the domain name has an ICP number. Otherwise, the domain name may fail to be resolved. For more information, see ICP filing overview.
If this parameter is not configured, the Ingress rule matches all requests that are sent to the Ingress controller.
spec.rules.http.paths.path
Yes
The URL.
spec.rules.http.paths.pathType
Yes
The URL matching rule. For more information, see Forward requests based on URL paths.
spec.rules.http.paths.backend.service.name
Yes
The name of the Service that you created.
spec.rules.http.paths.backend.service.port.number
Yes
The port number of the backend Service. This port must be valid to ensure that requests are routed correctly.
Run the following command to configure an externally-accessible domain name and a
pathfor thecoffeeandteaServices separately:kubectl apply -f cafe-ingress.yamlExpected output:
ingress.networking.k8s.io/cafe-ingress created(Optional) Run the following command to query the domain name of the ALB instance:
kubectl get ingressExpected output:
NAME CLASS HOSTS ADDRESS PORTS AGE cafe-ingress alb demo.domain.ingress.top alb-m551oo2zn63yov****.cn-hangzhou.alb.aliyuncs.com 80 50s
Step 6: Create a DNS record
If you set the spec.rules.host parameter to a custom domain name when creating the Ingress, you must map the custom domain name to the ALB instance's public endpoint by adding a CNAME record. This allows you to access the Services through your custom domain name.
Log on to the ACK console.
Click the cluster name to go to the cluster details page.
In the left-side navigation pane, choose Network > Ingresses.
In the Endpoint column of cafe-ingress, copy the domain name.
To create a CNAME record, perform the following steps:
NoteIf your domain name is not registered by using Alibaba Cloud Domains, you must add your domain name to Alibaba Cloud DNS before you can configure a DNS record. For more information, see Manage domain names. If your domain name is registered on Alibaba Cloud, proceed with the following steps.
Log on to the Alibaba Cloud DNS console.
On the Public Zone page, find your domain name and click Settings in the Actions column.
On the Settings tab of the domain name details page, click Add Record.
In the Add Record panel, configure the parameters and click OK. The following table describes the parameters.
Parameter
Description
Record Type
Select CNAME from the drop-down list.
Hostname
Enter the prefix of the domain name. In this example, @ is entered.
NoteIf you use a root domain name, enter
@.Query Source
Select Default.
Record Value
Enter the CNAME, which is the domain name of the ALB instance.
TTL
Select a time-to-live (TTL) value for the CNAME record to be cached on the DNS server. In this example, the default value is used.
Step 7: Test traffic forwarding
This example uses demo.domain.ingress.top as the test domain. In a browser, enter the domain name followed by the URL path to test whether traffic is forwarded to the correct Service.
Enter
demo.domain.ingress.top/coffeein the address bar of a browser. The page for the coffee-svc Service appears.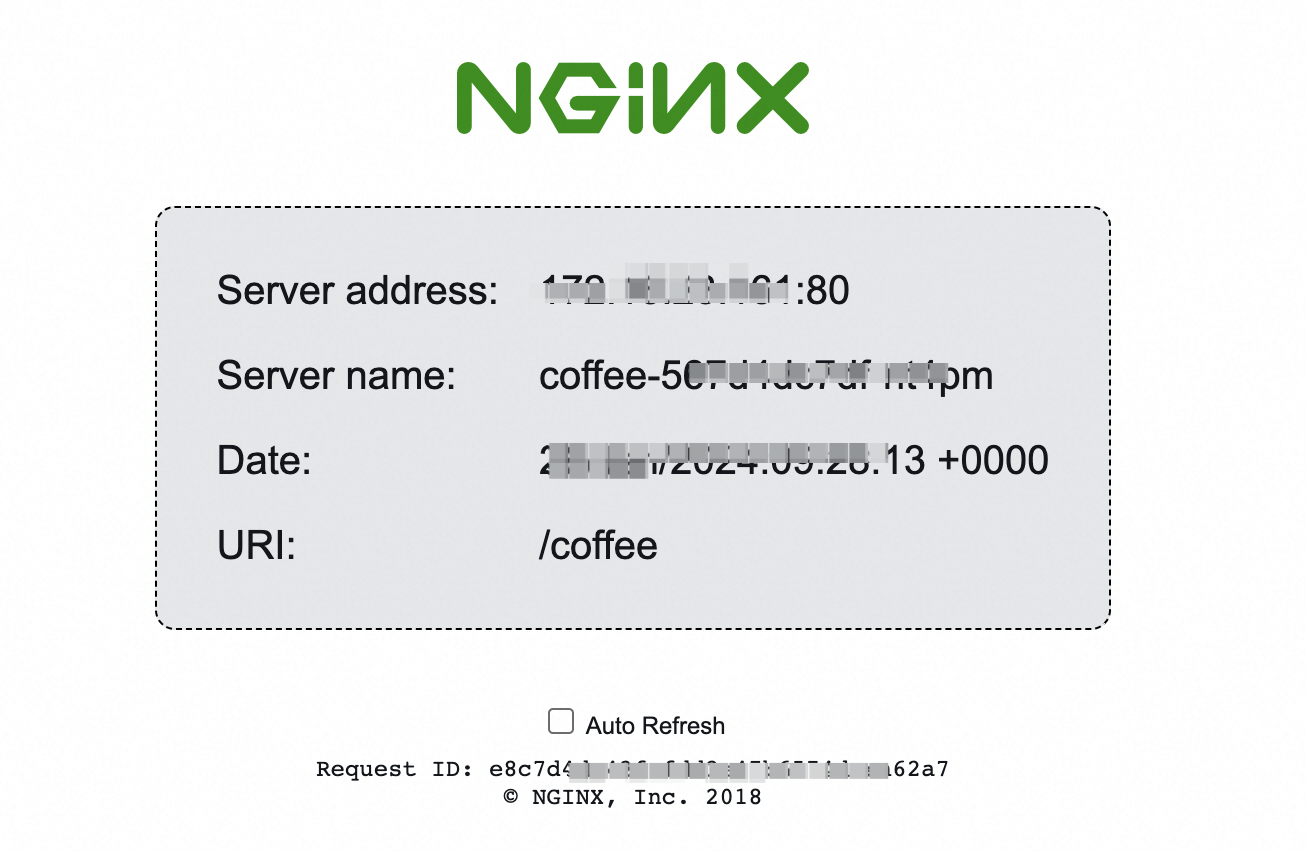
Enter
demo.domain.ingress.top/teain the address bar of a browser. The page for the tea-svc Service appears.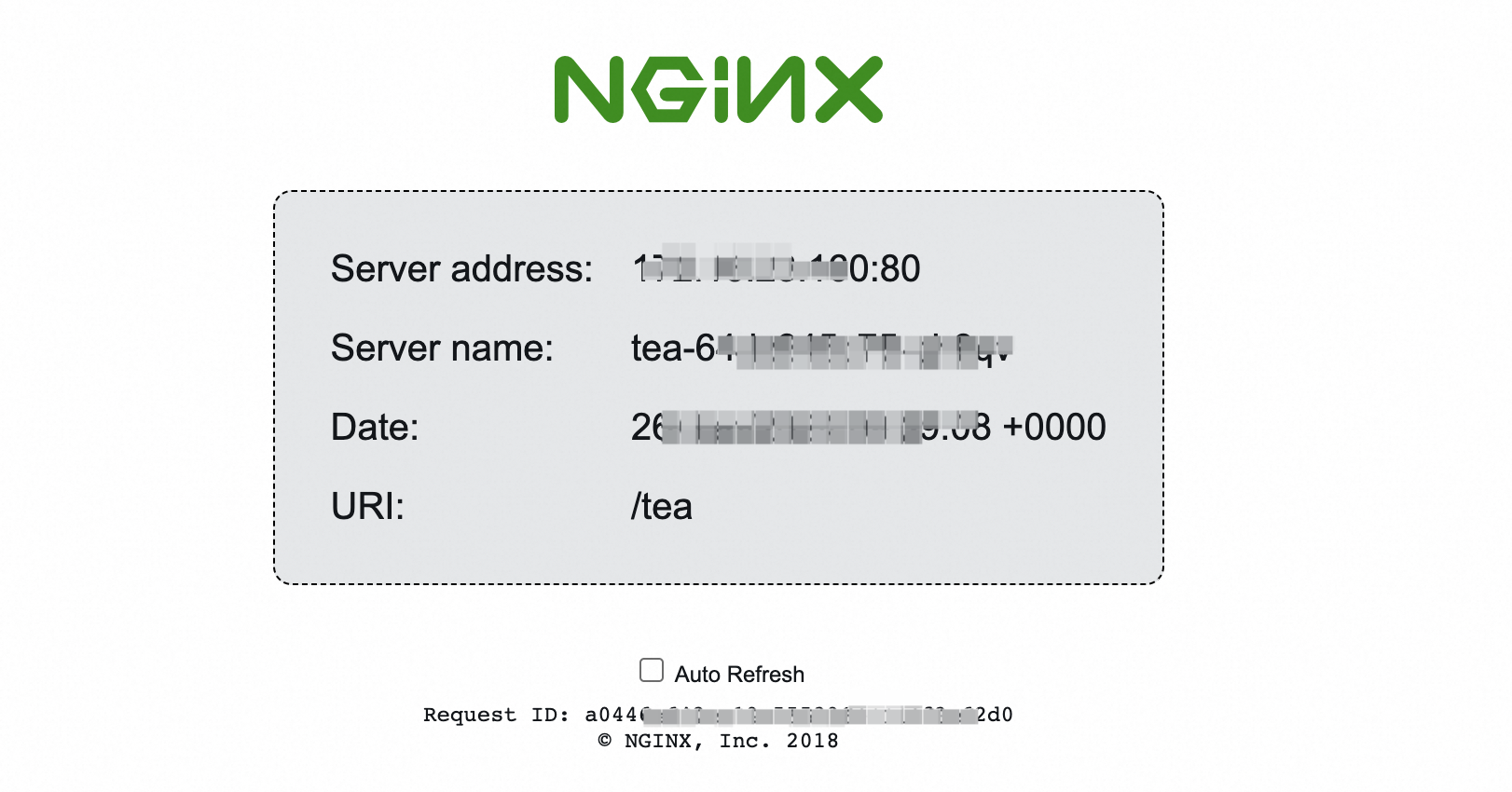
References
For more information about advanced ALB Ingress configurations, such as forwarding requests destined for different domain names or URLs to different backend server groups, health checks, redirecting requests from HTTP to HTTPS, canary releases, and custom listener ports, see Advanced ALB Ingress configurations.
For more information about how to configure custom ALB Ingress routing rules, routing conditions, and actions, see Customize the routing rules of an ALB Ingress.
For more information about how to use an HTTPS listener to forward HTTPS requests, see Use an ALB Ingress to configure certificates for an HTTPS listener.
For more information about how to troubleshoot ALB Ingress issues, see ALB Ingress troubleshooting and ALB Ingress FAQ.