To regulate access from requests, you can configure a security group to implement access control based on protocols, ports, and IP addresses. Security groups provide finer-grained access control than access control lists. Security groups not only support access control based on protocols and ports, but also support access control policies that regulate access from IPv6 addresses.
Upgraded ALB instances support both security groups and access control lists (ACLs) to control incoming traffic, while non-upgraded ALB instances support only ACLs. To use security groups, either create new ALB instances or contact your account manager to upgrade existing ALB instances.
For an overview of security groups and security group rules, including their limitations and considerations, see Add an ALB instance to a security group.
Scenario
The following table describes how to enable access control on ports for the ALB instance by configuring a security group in three different scenarios. In the scenarios, an HTTP listener that listens on port 80 and an HTTP listener that listens on port 81 are configured for the ALB instance.
Scenario | Security group rule | Expected result | References |
Before the ALB instance is added to a security group | By default, the listener ports of the ALB instance allow all requests. |
| Step 5: Test network connectivity before the ALB instance is added to the security group |
Add the ALB instance to a security group | Block requests to HTTP port 81 Note This section describes only the security group rules that are relevant to this topic. Other default rules are not described. |
| Step 6: Add the ALB instance to a security group and verify the result |
Modify the security group rules |
Note This section describes only the security group rules that are relevant to this topic. Other default rules are not described. |
| Step 7: Modify the security group rules and verify the result |
Prerequisites
A virtual private cloud (VPC) named VPC1 is created. For more information, see Create and manage a VPC.
Two Elastic Compute Service (ECS) instances named ECS01 and ECS02 are created in VPC1. ECS01 and ECS02 function as backend servers of the ALB instance. Different applications are deployed on ECS01 and ECS02.
For more information about how to create an ECS instance, see Create an instance on the Custom Launch tab.
If you need to verify ALB's access control on IPv6 requests with security groups, ensure that IPv6 has been enabled for ECS01 and ECS02.
The following sample code show how to deploy test applications on ECS01 and ECS 02.
A domain name is registered, and an Internet content provider (ICP) number is obtained for the domain name. For more information, see Register a domain name on Alibaba Cloud and Overview.
Procedure
Step 1: Create a server group for the ALB instance
Log on to the ALB console.
In the top navigation bar, select the region in which you want to create a server group. In this example, China (Hangzhou) is selected.
In the left-side navigation pane, choose .
On the Server Groups page, click Create Server Group.
In the Create Server Group dialog box, configure the parameters and click Create.
The following table describes the parameters that are relevant to this topic. Use the default values for the other parameters. For more information, see Create and manage server groups.
Parameter
Description
Server Group Type
Select a type of server group. In this example, Server is selected.
Server Group Name
Enter a name for the server group.
VPC
Select the VPC in which you want to create the server group. In this example, VPC1 is selected.
Backend Server Protocol
Select a backend protocol. In this example, HTTP is selected
Scheduling Algorithm
Select a scheduling algorithm. In this example, Weighted Round-robin is selected.
In the The server group is created dialog box, click Add Backend Server.
On the Backend Servers tab, click Add Backend Server.
In the Add Backend Server panel, select ECS01 and ECS02 and click Next.
Specify ports and weights for the backend servers and click OK.
Step 2: Create an ALB instance and configure listeners
Log on to the ALB console.
On the Instances page, click Create ALB.
On the buy page, configure the following parameters.
The following section describes only some of the parameters. Other parameters use the default values. For more information, see Create and manage an ALB instance.
Region: the region in which you want to create the ALB instance. In this example, China (Hangzhou) is selected.
Network Type: the network type of the ALB instance. In this example, Internet is selected.
VPC: the VPC in which you want to create the ALB instance. In this example, VPC1 is selected.
IP Version: IPv4 by default. If you require ALB to support both IPv4 and IPv6 client requests, select Dual-stack.
Click Buy Now and complete the payment.
Return to the Instances page and click the ID of the ALB instance.
Click the Listener tab and then click Quick Create Listener.
In the Quick Create Listener dialog box, configure the parameters and click OK. In this example, an HTTP listener that listens on port 80 is created. The following table describes the parameters.
Parameter
Description
Listener Protocol
Select a listener protocol. In this example, HTTP is selected.
Listener Port
Enter a listener port. In this example, 80 is specified.
Server Group
Select a server group type from the left-side drop-down list and select a server group from the right-side drop-down list. In this example, the server group created in Step 1 is selected.
On the Listener tab, click Quick Create Listener.
In the Quick Create Listener dialog box, configure the parameters and click OK. In this example, an HTTP listener that listens on port 81 is created. The following table describes the parameters.
Parameter
Description
Listener Protocol
Select a listener protocol. In this example, HTTP is selected.
Listener Port
Enter a listener port. In this example, 81 is specified.
Server Group
Select a server group type from the left-side drop-down list and select a server group from the right-side drop-down list. In this example, the server group created in Step 1 is selected.
Step 3: Configure a CNAME record
In actual business scenarios, we recommend that you use CNAME records to map custom domain names to the domain name of your ALB instance.
In the left-side navigation pane, choose .
On the Instances page, copy the domain name of the ALB instance.
Perform the following steps to create a CNAME record:
NoteIf your domain name is not registered by using Alibaba Cloud Domains, you must add your domain name to Alibaba Cloud DNS before you can configure a DNS record. For more information, see Manage domain names.
Log on to the Alibaba Cloud DNS console.
On the Public Zone page, find your domain name and click Settings in the Actions column.
On the Settings tab of the domain name details page, click Add Record.
In the Add Record panel, configure the parameters and click OK. The following table describes the parameters.
Parameter
Description
Record Type
Select CNAME from the drop-down list.
Hostname
Enter the prefix of the domain name. In this example, @ is entered.
NoteIf you use a root domain name, enter
@.Query Source
Select Default.
Record Value
Enter the CNAME, which is the domain name of the ALB instance.
TTL
Select a time-to-live (TTL) value for the CNAME record to be cached on the DNS server. In this example, the default value is used.
Step 4: Create a security group
Before you can add the ALB instance to a security group, you need to create a security group in the ECS console.
Log on to the ECS console.
In the left-side navigation pane, choose .
In the top navigation bar, select the region in which you want to create a security group. In this example, China (Hangzhou) is selected.
On the Security Groups page, click Create Security Group.
On the Create Security Group page, configure the parameters in the Basic Information section.
The following section describes only the parameters that are relevant to this topic. For more information about other parameters, see Create a security group.
Network: In this example, VPC1 is selected.
Security Group Type: In this example, Basic Security Group is selected.
Add an access rule to the security group.
On the Inbound tab, click Add Rule.
Configure the parameters and click Create Security Group. The following table describes the parameters.
Parameter
Description
Action
Select Deny.
Priority
The default value 1 is used.
Protocol Type
Select Custom TCP.
NoteTo add a security group rule for a QUIC listener, select Custom UDP.
Port Range
Enter the port number 81.
Authorization Object
Select
All IPv4 Addresses (0.0.0.0/0)andAll IPv6 Addresses ((::/0).Description
Enter a description for the security group rule.
Step 5: Test the network connectivity before the ALB instance is added to the security group
Test the network connectivity between a client and ECS01 and ECS02.
In this example, a client that has Internet access is used. If you need to verify ALB's access control on IPv6 requests with security groups, ensure that IPv6 has been enabled the testing client.
Open a command line interface and run
curl -4 http://<Custom_domain_name>:80. The command output shown in the following figure indicates that the client's IPv4 requests can access the backend server via HTTP:80 through the ALB instance.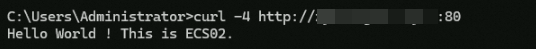
Run
curl -4 http://<Custom_domain_name>:81. The command output shown in the following figure indicates that the client's IPv4 requests can access the backend server via HTTP:81 through the ALB instance.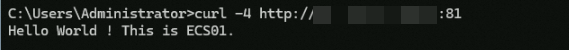
(Optional) Run curl -6 http://<Custom_domain_name>:80. The command output shown in the following figure indicates that the client's IPv6 requests can access the backend server via HTTP:80 through the ALB instance.

(Optional) Run
curl -6 http://<Custom_domain_name>:81. The command output shown in the following figure indicates that the client's IPv6 requests can access the backend server via HTTP:81 through the ALB instance.
Step 6: Add the ALB instance to the security group and verify the result
Add the ALB instance to the security group and test whether the security group rule takes effect on the ports.
Log on to the ALB console.
On the Instances page, click the ID of the ALB instance that you want to manage. On the instance details page, click the Security Groups tab.
On the Security Groups tab, click Create Security Group. In the Add ALB to Security Group dialog box, select the security group created in Step 4: Create a security group, and click OK.
In the left-side panel, click the ID of the security group that you want to manage. You can click the Inbound Policies or Outbound Policies tab to view the security group rules.
The following table describes only the inbound rules that are relevant to this topic. The ALB instance uses the following security group rules.
Policy
Priority
Protocol Type
Port Range
Authorization Object
Allow
1
Custom TCP
Destination: 80/80Source: All IPv4 Addresses (0.0.0.0/0)Allow
1
Custom TCP
Destination: 80/80Source: All IPv6 Addresses (::/0)Deny
1
Custom TCP
Destination: 81/81Source: All IPv4 Addresses (0.0.0.0/0)Deny
1
Custom TCP
Destination: 81/81Source: All IPv6 Addresses (::/0)After you add the ALB instance to the server group, test the accessibility of the ports.
In the client command line interface, run
curl -4 http://<Custom_domain_name>:80. The command output shown in the following figure indicates that the client's IPv4 requests can access the backend server via HTTP:80 through the ALB instance.
(Optional) Run
curl -6 http://<Custom_domain_name>:80. The command output shown in the following figure indicates that the client's IPv6 requests can access the backend server via HTTP:80 through the ALB instance.
Run
curl -4 http://<Custom_domain_name>:81. The command output shown in the following figure indicates that the client's IPv4 requests cannot access the backend server via HTTP:81, which indicates that the rules on port 81 in the ALB instance's security group take effect.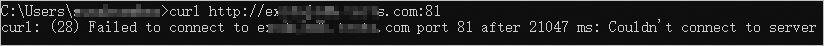
(Optional) Run
curl -6 http://<Custom_domain_name>:81. The command output shown in the following figure indicates that the client's IPv6 requests cannot access the backend server via HTTP:81, which indicates that the rules on port 81 in the ALB instance's security group take effect.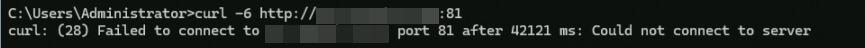
Step 7: Modify the security group rules and verify the result
Modify the security group rules and test whether the security group rules can take effect on the ports.
Return to the Instances page and click the ID of the ALB instance. On the Instance Details tab, click the Security Groups tab.
In the Basic Information section, click the ID of the security group. You can also click ECS Console in the upper-right corner of the Security Groups tab to go to the Security Group Details page.
On the Security Group Detail page, find the security group rule that allows access to TCP port 80 and click Modify in the Actions column. Set Action to Deny and click Save.
The following table describes only the security group rules that are relevant to this topic. The following table describes the new security group rules.
Policy
Priority
Protocol Type
Port Range
Authorization Object
Deny
1
Custom TCP
Destination: 80/80Source: All IPv4 Addresses (0.0.0.0/0)Deny
1
Custom TCP
Destination: 80/80Source: All IPv6 Addresses (::/0)Deny
1
Custom TCP
Destination: 81/81Source: All IPv4 Addresses (0.0.0.0/0)Deny
1
Custom TCP
Destination: 81/81Source: All IPv6 Addresses (::/0)After you modify the security group rules, test the accessibility of the ports.
In the client command line interface, run
curl -4 http://<Custom_domain_name>:80. The command output shown in the following figure indicates that the client's IPv4 requests cannot access the backend server via HTTP:80, which indicates that the rules on port 80 in the ALB instance's security group take effect.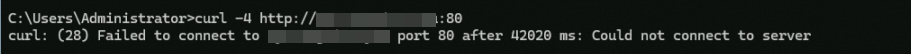
(Optional) Run
curl -6 http://<Custom_domain_name>:80. The command output shown in the following figure indicates that the client's IPv6 requests cannot access the backend server via HTTP:80, which indicates that the rules on port 80 in the ALB instance's security group take effect.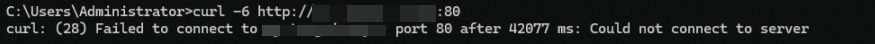
Run
curl -4 http://<Custom_domain_name>:81. The command output shown in the following figure indicates that the client's IPv4 requests cannot access the backend server via HTTP:81, which indicates that the rules on port 81 in the ALB instance's security group take effect.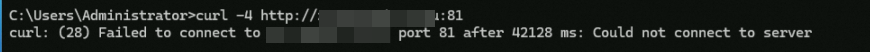
(Optional) Run
curl -6 http://<Custom_domain_name>:81. The command output shown in the following figure indicates that the client's IPv6 requests cannot access the backend server via HTTP:81, which indicates that the rules on port 81 in the ALB instance's security group take effect.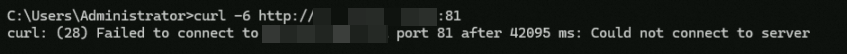
References
Console
For more information about how to add an ALB instance to and remove an ALB instance from a security group, see Add an ALB instance to a security group.
For allowing or denying access from specific IP addresses to ALB, see Use security groups as blacklists or whitelists.
For more information about basic security groups and advanced security groups, see Basic security groups and advanced security groups.
API
LoadBalancerJoinSecurityGroup: adds an ALB instance to a security group.
LoadBalancerLeaveSecurityGroup: removes an ALB instance from a security group.