The application protection feature is developed based on the runtime application self-protection (RASP) technology. This feature can detect attacks and provide self-protection during application runtime. You do not need to modify code to use the application protection feature. You need to only install the RASP agent on the servers or containers on which your applications run. The feature can protect your applications against attacks that are launched by exploiting most unknown vulnerabilities.
How it works
The application protection feature adopts the RASP technology. The feature uses hooks to monitor the interactions between applications and other systems in real time. When suspicious behavior is detected in an application, the feature identifies and blocks attacks based on the context. This helps protect against application vulnerabilities, zero-day vulnerabilities, and in-memory webshells that are detected in the web processes on your servers.
Scenarios and benefits
Protects the internal security of applications: The feature monitors only the behavior of the applications that you want to protect and protects the application against threats from north-south and east-west traffic regardless of traffic sources. The feature takes effect immediately after application startup. The feature serves as the last line of defense for applications.
Easily handles complicated code and encrypted traffic: The feature can parse the context of applications. It monitors the ultimate actions of applications even when requests are malformed. The feature can detect anomalies when the identity of a request sender and the expected actions do not match. Unlike network boundary devices that cannot audit encrypted traffic, the feature can access fully decrypted request data within applications.
Defends against zero-day vulnerabilities with low false positives and false negatives: The feature analyzes the execution of critical functions applications. It can identify and ignore vulnerabilities that are not easily exploitable to reduce a large number of false positives and false negatives. RASP can detect and block zero-day vulnerabilities by monitoring the execution process of critical functions that attackers cannot bypass even if they change attack portals or use sophisticated attack methods.
Traces attack sources and fix vulnerabilities: The feature provides security personnel and developers with detailed attack paths, including the original attack payloads and code call stacks. This allows them to identify, reproduce, and fix vulnerabilities.
Reduces O&M costs: The deployment of the feature is simple. You need to only connect your applications in the Security Center console. You do not need to maintain or update specific rules.
Limits
The feature is available only for Java and PHP applications. You can use the feature on servers on which the Security Center agent is installed. The server can be an Elastic Compute Service (ECS) instance, a cloud server of a third-party cloud service provider, or a server in a data center. The following table describes the operating systems that are supported by the Security Center agent.
Operating system | Supported system version |
Windows (64-bit) |
|
Linux (64-bit) |
|
Capabilities
Attack detection (Java applications)
The following table describes the types of attacks that the application protection feature can detect and defend, and the solutions to defend against each type of attack.
Attack Type | Description | Solution |
JNI injection | Java Native Interface (JNI) injection is a common method to bypass the RASP technology. After an attacker obtains the permissions to execute code, the attacker can use JNI functions to call external malicious dynamic-link libraries. This way, the attacker can bypass the security protection at the Java layer and conceal specific malicious behavior. | Your server may have a code execution vulnerability. Check the location of the vulnerability and limit the permissions to execute code. |
SQL Injection | An SQL injection attack inserts SQL statements into the query strings of web requests or web forms and induces the server to execute the SQL statements. An attacker can obtain the data on websites on which security vulnerabilities exist by inserting SQL statements into web forms. | SQL injection is caused by concatenating SQL statements. Precompile input parameters or use whitelists and blacklists to limit concatenated parameters. |
XXE | XXE injection is short for XML external entity injection. If an XML file references an external entity, an attacker can construct malicious content to cause arbitrary file reads, command execution, and internal network attacks. | Check whether your application needs to load external entities when it parses XML files. If not, disable external entities in the XML parsing configurations. |
Malicious DNS query | An attacker can use multiple methods to exploit malicious Domain Name System (DNS) queries. An attacker is likely to use the DNS protocol to bring sensitive information out of internal networks. The attacker may also use the DNS protocol to check whether an internal network system has vulnerabilities such as Server-Side Request Forgery (SSRF) and Java Naming and Directory Interface (JNDI) injection. | Malicious DNS queries are caused by server requests for user-controlled parameters. Check parameter settings and configure whitelists. |
Malicious reflection call | The self-protection module of RASP prohibits attackers from using reflection to modify RASP data during runtime. | Your server may have a code execution vulnerability. Check the location of the vulnerability and limit the permissions to execute code. |
SSRF | SSRF is a web vulnerability that allows an attacker to attack the internal system of a website by inducing a server-side application to make HTTP requests. | To fix SSRF vulnerabilities, restrict the target IP addresses of server requests, allow access only to secure internal resources through whitelists, and disable unnecessary external network access. |
Malicious file read and write | Java provides the RandomAccessFile class for file read and write operations. If you use this class to read and write files but you do not restrict the file path or file content, an attacker may read sensitive system files or upload trojan files. | Check whether you can read and upload files as expected. If an exception occurs, check the function code and configure blacklists. |
Malicious file upload | For the file upload feature provided by a website, if the types of files are not restricted, an attacker may obtain higher permissions on the server by uploading trojan files. This causes serious harm. | Restrict the types of files that can be uploaded and prohibit uploading files with execute permissions, such as Jakarta Server Pages (JSP) files. |
Command injection | A command execution vulnerability allows an attacker to execute arbitrary system commands on a server. | In most cases, remote command execution is caused by webshells or the risky code of a server. Check the location in which commands are executed. If command execution is caused by webshells, delete the webshells in time. If commands are executed to implement normal features on a server, configure whitelists to limit the commands that can be executed. |
Directory traversal | The directories of a website may be browsed arbitrarily due to the configuration defects of the website. This results in the disclosure of privacy information. An attacker can use the disclosed information to attack the website. | Check whether the website directories can be traversed as expected. If an exception occurs, check the function code and configure blacklists to restrict related commands, such as "./" and "../". |
Memory horse injection | In-memory webshells are an emerging trojan horse technique. An attacker can inject trojans into memory by using technical approaches that help effectively bypass the detection of Web Application Firewall (WAF) and host defense. | Your server may have a code execution vulnerability. Check the location of the vulnerability and limit the permissions to execute code. |
Arbitrary file read | For the file download and read feature provided by a website, if files are read and downloaded by using an absolute path or a directory traversal character and file paths are not restricted, an attacker can exploit this vulnerability to obtain sensitive information and attack the server. | Check whether you can read files as expected. If an exception occurs, check the function code and configure blacklists to restrict the input parameters, such as "./" and "../". |
Thread injection | Thread injection is a common method to bypass the RASP technology. If an attacker obtains the permissions to execute code, the attacker can create a thread to cause RASP to lose the context of the runtime environment. In this case, the defense capability of RASP is compromised. | Your server may have a code execution vulnerability. Check the location of the vulnerability and limit the permissions to execute code. |
Malicious Attach API | The Attach API is a Java technology that can be used to dynamically modify the bytecode of running applications. An attacker can use the technology to inject agent-type memory horses. This method is highly deceptive. | Your server may have a code execution vulnerability. Check the location of the vulnerability and limit the permissions to execute code. |
JNDI injection | If an application initiates a JNDI query but the query URL is controlled by an attacker, the attacker can induce the server on which the application runs to query malicious links and load malicious classes. This results in arbitrary code execution on the server. |
|
Usage of vulnerable protocols | If the URL that a server accesses is user-controllable and the URL protocol is not restricted on your application, an attacker can read sensitive files on the server over insecure protocols such as File and NetDoc. | Restrict URL protocols. |
Deserialization attack | Java deserialization is a process of restoring a sequence of bytes into a Java object. If the Java object contains code that can cause high risks, an attacker can control the member variables of the Java object to initiate attacks during the deserialization process. |
|
Arbitrary file deletion | For the file deletion feature provided by a website, if file paths are not restricted, an attacker can delete any file by using an absolute path or a directory traversal character, and then attack the server. | Check whether file delete operations are normal. If an exception occurs, check the function code and configure blacklists to restrict the input parameters, such as "./" and "../". |
Expression language (EL) injection | Expressions provide a wide range of features, such as data query and processing during runtime. Multiple expressions also provide features that require advanced permissions such as function calls. If the features are not restricted, attackers can modify the content of expressions and execute arbitrary code. | Strictly restrict the content of expressions and disable Java function calls. If this vulnerability is caused by third-party components, you must upgrade the components at the earliest opportunity. |
Engine injection | Java provides various third-party JavaScript engines, such as Rhino and Nashorn, and template engines, such as Apache Velocity and FreeMarker. In most cases, these engines provide features that require advanced permissions such as function calls. If the features are not restricted, attackers can modify the content executed by the engines and execute arbitrary code. | Strictly restrict the content imported to the engines and disable Java function calls. If this vulnerability is caused by third-party components, you must upgrade the components at the earliest opportunity. |
Malicious beans binding | Some Java frameworks support bean property binding when applications are running. If the types of bean properties that can be bound are not restricted, attackers can modify the values of sensitive bean properties to disrupt the running of applications or even execute arbitrary code. | Restrict the types of bean properties that can be bound to prevent the values of bean properties such as class and class loaders from being changed. If this vulnerability is caused by third-party components, you must upgrade the components at the earliest opportunity. |
Malicious class loading | Zero-day vulnerabilities and web shells depend on the loading of malicious classes. If malicious classes are loaded, attackers can initialize malicious classes, obtain the permissions to execute code, and perform malicious operations. |
|
JSTL file inclusion | The JavaServer Pages Standard Tag Library (JSTL) is a set of JavaServer Pages (JSP) tags, which encapsulates the common core features of JSP applications. If a user-controllable parameter is directly concatenated into JSTL without any restrictions on the parameter, attackers can construct a special script that causes arbitrary file reads and SSRF attacks. | We recommend that you do not directly concatenate user-controllable parameters into JSTL. If you need to do this, you must exercise strict whitelist control on the content of the parameters. |
Attack detection (PHP applications)
Attack Type | Description | Solution |
Malicious file inclusion | File inclusion vulnerabilities in PHP, which are common security issues, allow attackers to include and execute arbitrary files by manipulating input. These vulnerabilities typically occur when using functions like | Validate and restrict file paths to ensure only predefined files within the application directory are accessible, thus preventing attackers from inserting malicious paths. |
SSRF | SSRF is a web vulnerability that allows an attacker to attack the internal system of a website by inducing a server-side application to make HTTP requests. | To fix SSRF vulnerabilities, restrict the target IP addresses of server requests, allow access only to secure internal resources through whitelists, and disable unnecessary external network access. |
Deserialization | Deserialization vulnerabilities in PHP are critical security issues that allow attackers to execute arbitrary functions by manipulating serialized data. These vulnerabilities often occur when using the | Avoid directly deserializing untrusted data. Instead, use |
Callback function execution | Callback functions in PHP, such as | To prevent the misuse of PHP callback functions, ensure that the names of callback functions passed to |
Malicious file read and write | Attackers may read sensitive system files or upload trojan files if file read and write functions are called without restrictions on file paths or content. | To prevent vulnerabilities related to file read and write, strictly validate and restrict file paths. Allow access only to predefined directories and perform security checks on file content to prevent malicious uploads. |
Arbitrary code execution | An arbitrary code execution vulnerability is a critical security issue that allows attackers to execute arbitrary code snippets on a server, potentially gaining control of the server or reading and modifying sensitive data. Such vulnerabilities typically arise from inadequate validation of user input, allowing attackers to inject malicious code. If exploited, this vulnerability may lead to data breaches, website defacement, or malware insertion. | Employ strict input validation and output encoding. Avoid using functions like |
Arbitrary file read | Attackers can exploit file read interfaces to access files using absolute paths or directory traversal characters, which allows them to obtain sensitive information and attack the server. | Enforce strict input validation and path restrictions for file read interfaces. Limit access to files verified by a whitelist and restrict input parameters like "./" and "../" with a blacklist. |
Arbitrary file deletion | Attackers can exploit file deletion interfaces to delete arbitrary files using absolute paths or directory traversal characters to delete arbitrary files, thereby attacking the server. | Apply strict input validation and path restrictions for file deletion interfaces. Ensure that only verified files can be deleted and restrict input parameters like "./" and "../" with a blacklist. |
Command execution | Command execution vulnerabilities allow attackers to remotely inject operating system commands or code into the backend server, gaining control of the backend system. | Rigorously validate and filter all user inputs. Avoid using unprocessed inputs to construct operating system commands, and prefer secure APIs over executing system commands whenever possible. |
Directory traversal | Configuration defects in a website may allow arbitrary browsing of directories, leading to the disclosure of sensitive information. Attackers can use this information to attack the website. | Set appropriate server permissions and use files like |
Malicious file upload | Attackers may upload trojan files to gain higher permissions on the server, causing severe harm if the file upload feature does not restrict the types of files that can be uploaded. | Strictly restrict and validate the types of files that can be uploaded. Permit only safe file types and prohibit files with executable extensions like php. Recheck file content on the server to ensure security. |
Application vulnerability prevention
The application protection feature can effectively defend against application vulnerabilities, zero-day vulnerabilities, and in-memory webshells. The diagram below illustrates how it works. During the emergency response to application vulnerabilities, the application protection feature immediately blocks attacks to grant you extra time to fix the vulnerabilities. The application protection feature also helps you quickly identify the source and scope of risks. For more information, see View and handle vulnerabilities.
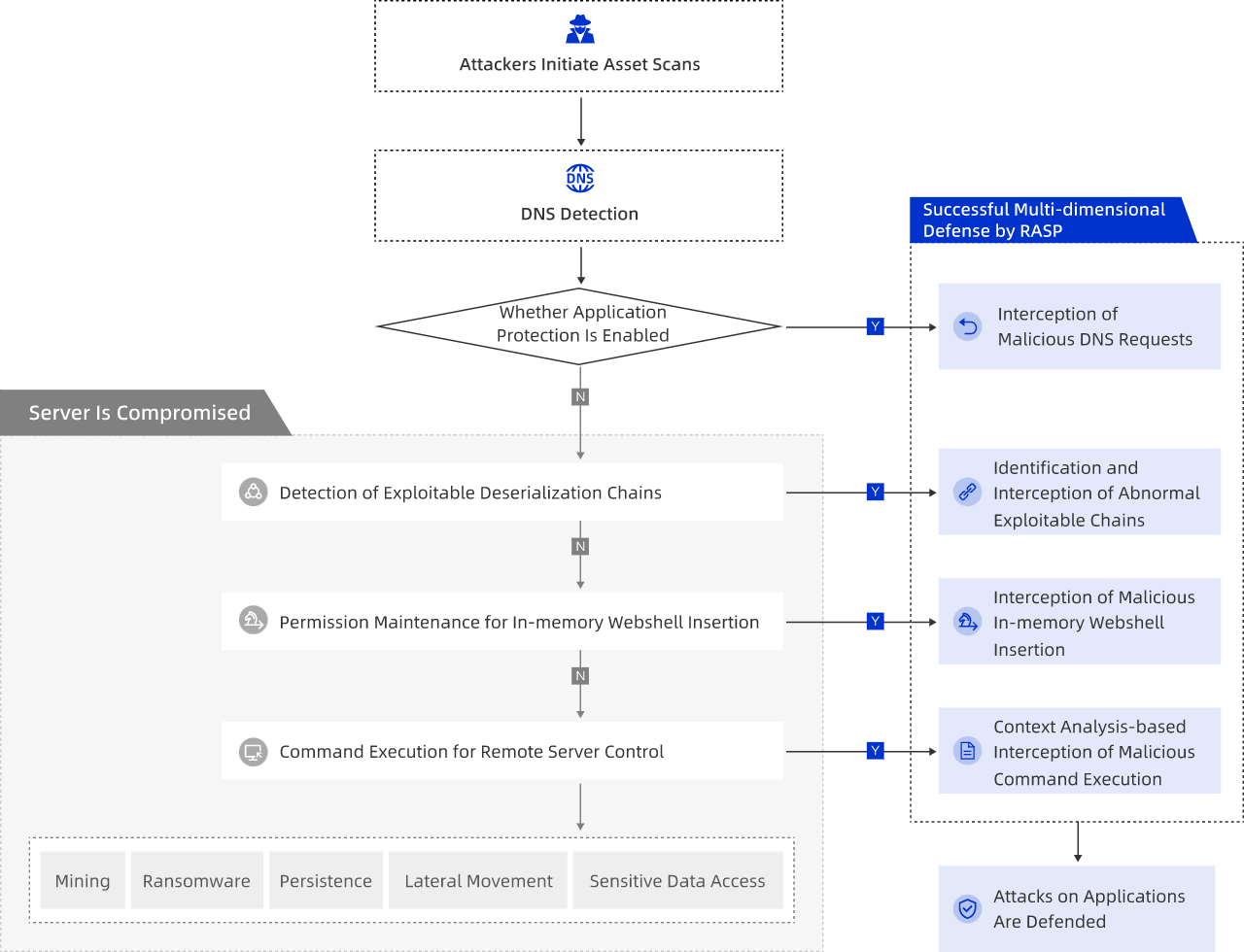
If application vulnerabilities cannot be fixed, you can add application processes to the application protection feature for protection. To add applications in which vulnerabilities are detected, perform the following steps:
Log on to the Security Center console. In the top navigation bar, select the region of the asset that you want to manage. You can select China or Outside China.
In the left-side navigation pane, select .
On the Application Vulnerability tab, find a vulnerability that is marked with the RASP supports real-time protection. tag. This tag indicates that the application protection feature can defend against the vulnerability. Then, click Enable Protection Now in the Actions column.
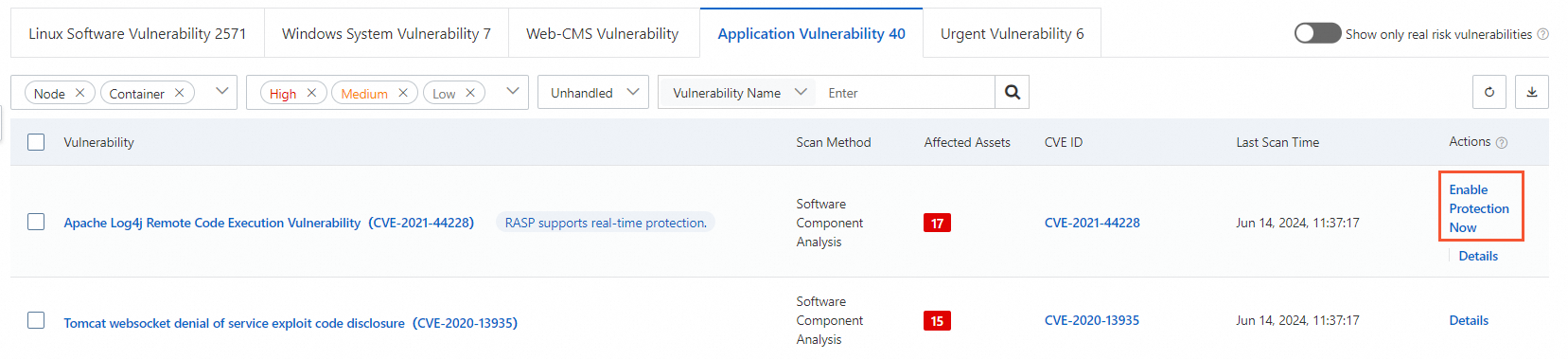
In the Access Management panel, choose the desired application group from the Application Group Name drop-down list, select the relevant asset, and then click OK.
If the required application group does not exist, you can select Create Application Group from the drop-down list, enter the name of the application group, and click OK. The protection mode of the new application group is Block, and the associated protection policy group is Normal Running Group.
After an application in which the vulnerability is detected is added to the application protection feature and an application vulnerability scan is complete, the status of the server on which the application runs changes to Protected on the Unhandled Vulnerabilities tab in the details panel of the vulnerability.
Application behavior analysis
The application behavior analysis feature monitors connected applications in real time, collects and analyzes application behavior data, and generates and visualizes reports. This feature helps you understand the attack and defense details of applications and reinforce system security. For more information, see Use the application analysis feature.
In-memory webshell defense (Java applications)
The application protection feature uses the RASP technology to detect in-memory webshells by analyzing memory data and block injection and execution of in-memory webshells. For more information, see Use the in-memory webshell prevention feature.
Weakness detection (Java applications)
The following table describes the types of application weaknesses that can be detected by the application protection feature and the related fixing suggestions.
Weakness type | Risk level | Description | Fixing suggestion |
Vulnerable Fastjson configurations | High | The deserialization feature is enabled for the Fastjson library of an application. This feature may be exploited by attackers to cause remote command execution. We recommend that you disable the feature unless otherwise required. | Set safeMode of Fastjson to true or autoType to false. |
Vulnerable Log4j configurations | High | The lookup feature is enabled for your Log4j component. This feature may be exploited by attackers to initiate JNDI injections and cause remote code execution. | Update Log4j to the latest version or remove the org/apache/logging/log4j/core/lookup/JndiLookup.class file from the JAR package. |
Vulnerable startup parameters | High | If attackers can access the Java Debug Wire Protocol (JDWP) debugging port, the attackers can execute arbitrary code and cause remote code execution. | If the JDWP port is no longer required, disable the JDWP port at the earliest opportunity. Do not expose the JDWP port on the Internet. Monitor the JDWP port for applications that run for a long period of time. If the JDWP port is enabled, disable the port. |
Weak keys in Shiro | High | If Shiro applications use weak keys for encryption, attackers can initiate deserialization attacks by cracking the keys and cause remote code execution. | Change the encryption keys in Shiro applications at the earliest opportunity. |
Vulnerable JMX configurations | Medium | If remote JMX connection is enabled and authentication risks exist, attackers can remotely connect to the JMX service of an application and cause command execution. | Disable remote JMX connection, or use a secure password for authentication. |
Vulnerable Rhino configurations | Medium | Rhino contains insure properties that attackers can exploit to achieve remote code execution. | Update Rhnio to the latest version. Use SafeStandardObjects to define the context of Rhnio and prevent the JavaScript engine from calling Java code. The following sample code provides an example on how to use SafeStandardObjects to define the context of Rhino: |
Vulnerable Spring configurations | Medium | Several endpoints are enabled in the Spring Boot Actuator module, such as heapDump, env, restart, refresh, trace, jolokia, and h2-console. This may cause sensitive information leaks or remote code execution. | Disable the endpoints unless otherwise required. |
Vulnerable logon password | Medium | The password of the account that is used to log on to your application is weak. Attackers can crack the password to log on to your system and obtain sensitive information and server permissions. | Change the password to a complex password at the earliest opportunity. |
Vulnerable JNDI configurations | Low | Your application uses vulnerable configurations related to useCodebaseOnly, rmi-trustURLCodebase, and ldap-trustURLCodebase, which may cause JNDI injections. | Update the JDK to the latest version. If you cannot update the JDK, add the following startup parameters when you start the application: |
Insure XML entity configurations | Low | XML parsing is enabled for external entities, which can cause XXE attacks on applications. | Do not use external entities unless otherwise required. |
Weak database password | Low | If the password of the account that is used by an application to connect to a database is weak, attackers can exploit the password to access the database and obtain sensitive information or achieve remote code execution. | Change the password to a complex password at the earliest opportunity. |