The weakness detection feature can detect defects or vulnerabilities in an application. The feature can detect vulnerable configurations during application runtime, including inappropriate configurations of mainstream Java frameworks and weak passwords configured for applications and databases. You can use the feature to identify weaknesses that can be exploited by attackers. This topic describes how to detect application weaknesses.
Limits
If your processes are added to the application protection feature and the version of the RASP agent that is installed on the processes is 0.5.0 or later, the weakness detection feature is supported. You can perform the following operations to view the version of the RASP agent that is installed on the processes: Go to the Application Configurations tab. Find the application group to which the processes belong and click the number in the Access instance column to go to the Instance details panel. If the version of the RASP agent is earlier than 0.5.0, you can restart the application. Then, the RASP agent is automatically updated.
View weakness detection results
Log on to the Security Center console. In the top navigation bar, select the region of the asset that you want to manage. You can select China or Outside China.
In the left-side navigation pane, choose .
On the Weakness Detection tab, view the data displayed in the following sections: Vulnerability Overview, Vulnerability Detection Trend, Vulnerability Distribution by Type, and Distribution of Vulnerability Detection Events by Quantity.
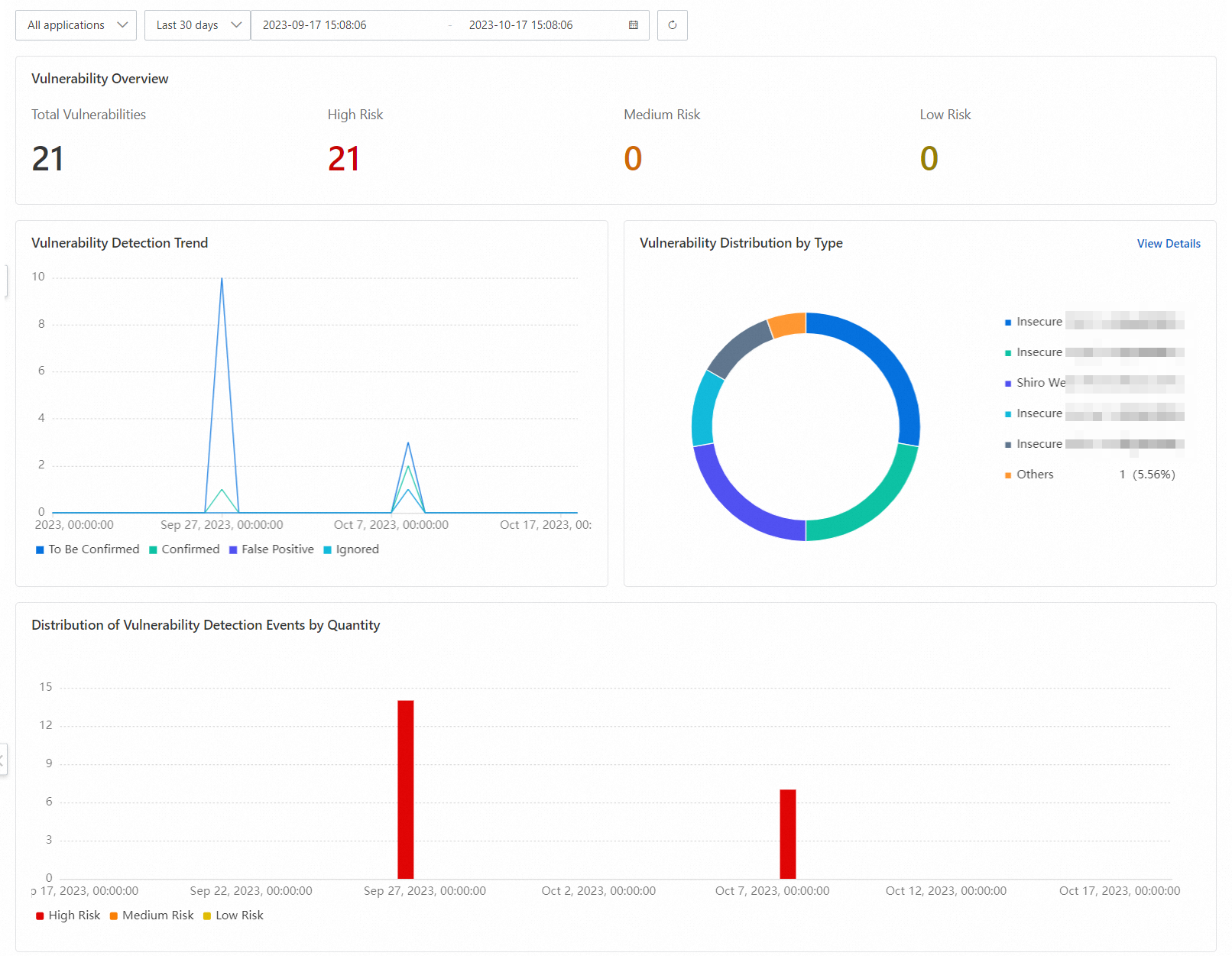
In the lower part of the Weakness Detection tab, view the applications on which weaknesses are detected.
Application Startup ID: Each ID is unique in a startup cycle of an application and can be used to distinguish between weaknesses that are detected during multiple startup processes of the application.
Status: You can view the handling status of weaknesses that are detected during the startup of an application. If a weakness detected on the application is not confirmed, the status is To Be Confirmed. If all weaknesses are handled, the status is Confirmed.
Click the
 icon to the left of an application startup ID to view the detected weaknesses. Find the required weakness in the weakness list and click Details in the Actions column to view the details about the weakness.
icon to the left of an application startup ID to view the detected weaknesses. Find the required weakness in the weakness list and click Details in the Actions column to view the details about the weakness. You can view the cause of a weakness and determine whether to fix the weakness based on the weakness description, fixing suggestion, and weakness location.
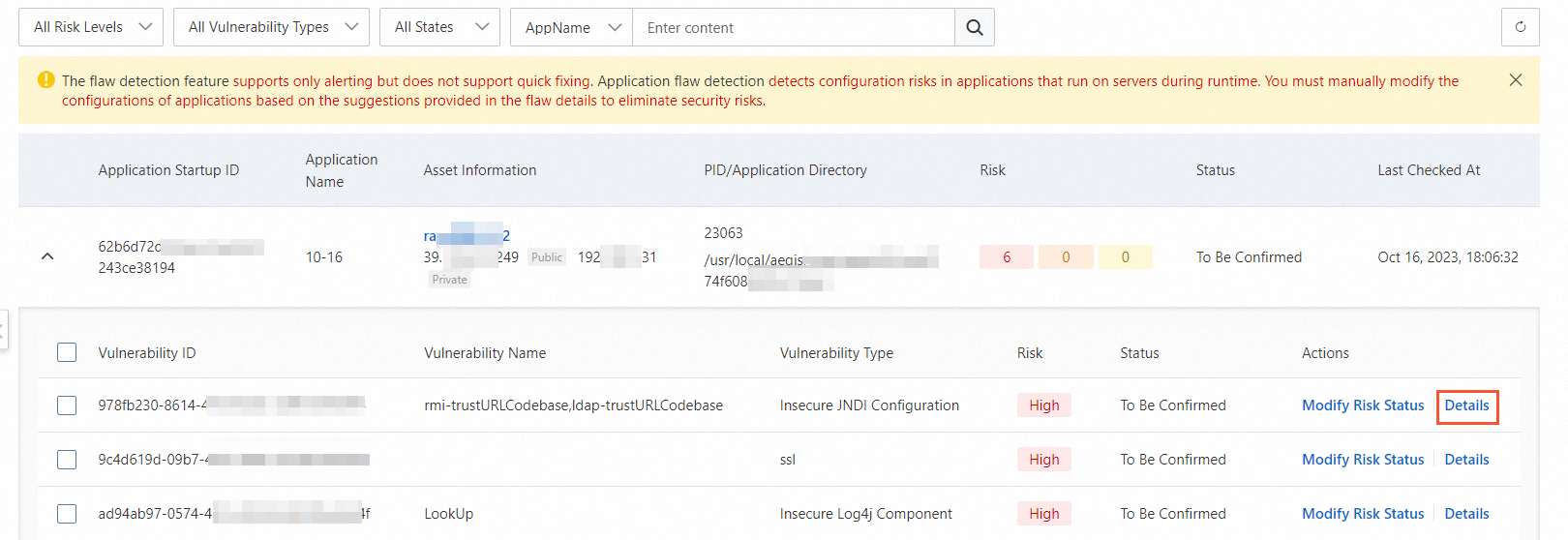
Return to the weakness list after you confirm whether to fix the weakness. Find the required weakness and click Modify Risk Status in the Actions column. In the Modify Risk Status dialog box, configure the Risk Status and Remarks parameters and click OK.
The following risk states are supported:
To Be Confirmed: If you cannot confirm how to handle the weakness, select this state.
Confirmed: If you have confirmed how to handle the weakness, select this state.
False Positive: If the weakness does not exist or the information about the weakness is incorrect, select this state.
Ignore: If you want to ignore the weakness, select this state.