In-memory webshells are malicious programs that exclusively run in memory and do not write to disks. This characteristic allows them to launch stealthy attacks and bypass detection by conventional antivirus methods. The application protection feature uses the Runtime Application Self-Protection (RASP) technology to detect in-memory webshells by analyzing memory data and block injection and execution of in-memory webshells. This topic describes how to use the in-memory webshell prevention feature.
Prerequisites
Java applications are added to the application protection feature, and application instances are in the Authorized state. For more information, see Use the application protection feature.
How it works
The in-memory webshell prevention feature can check whether in-memory webshells exist on authorized application instances within the required application group and whether the in-memory webshells are injected and executed. The feature provides protection by using the following detection engines:
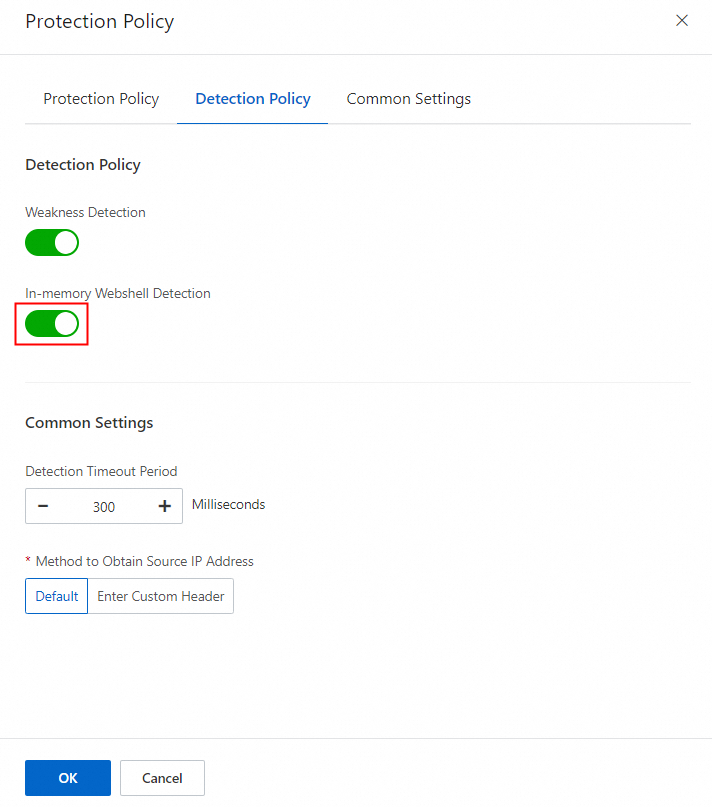
In-memory webshell detection: This engine scans the memory for malicious code to help you detect hidden threats and displays alerts that are generated for detected in-memory webshells in the Security Center console. To enable this engine for an application group, turn on In-memory Webshell Detection.
In-memory webshell injection: This engine performs monitoring and blocks behavior caused by in-memory webshells in real time, such as injection and execution of in-memory webshells. If In-memory Webshell Injection is included in the threat types specified in the protection policy of an application group, you can enable this engine for the application group. If you enable this engine and set the Protection Mode parameter of the application group to Monitor, this engine generates alerts when threats are detected but does not block the threats. If you enable this engine and set the Protection Mode parameter of the application group to Block, this engine generates alerts when suspicious calls are detected and blocks the calls. To protect various types of middleware against in-memory webshells, this engine provides the following methods:
Blocking before in-memory webshells are injected: The application protection feature monitors sensitive API functions to identify and block injection attempts in real time. For example, the feature blocks attacks when attackers execute expressions or launch deserialization attacks. This prevents in-memory webshells from infiltrating the application context.
Blocking before in-memory webshells are executed: If in-memory webshells bypass the initial blocking phase and attempt to run in memory, the application protection feature uses deep learning and behavior recognition technologies to detect and block the execution of in-memory webshells. The technologies precisely identify and prevent the activation and execution of in-memory webshells by comparing against a database of known malicious characteristics. During the process, normal business operations are not disrupted. Even if in-memory webshells are injected into the system, attackers cannot control the system.
View and handle alerts
By default, the application protection feature enables in-memory webshell detection for all application groups. After you add an application to the feature, you can perform the following operations to view and handle alerts that are generated for in-memory webshells.
Log on to the Security Center console. In the top navigation bar, select the region of the asset that you want to manage. You can select China or Outside China.
In the left-side navigation pane, choose .
On the In-memory Webshell Prevention tab of the Application Protection page, specify the required application group and time range.
View statistics in the In-memory Webshell Alert Trend and In-memory Webshell Distribution sections and view alerts on the following tabs:
Alert for In-memory Webshell Detection: displays alerts generated for the static in-memory webshell files that are detected by the in-memory webshell detection engine. The following list describes the alert status:
Unhandled: indicates that an in-memory webshell file is detected by the in-memory webshell detection engine. You must manually handle the alert at the earliest opportunity.
Automatic: labeled as Blocked. This status indicates that the in-memory webshell injection engine detects running of in-memory webshell files and blocks execution of the in-memory webshells. The application protection feature precisely blocks in-memory webshells and blocks subsequent executions. You can restart the affected applications to clear detected in-memory webshell files.
Unhandled: labeled as Monitored. This status indicates that the in-memory webshell injection engine detects running of the in-memory webshell files that trigger the alert and blocks execution of the in-memory webshells based on the protection mode specified for the application group. You can enable the in-memory webshell prevention feature for the application group.
The following list describes the Active and Inactive states of alerts:
Active: The application instance on which alerts are generated is online.
Inactive: The application instance on which alerts are generated is offline.
Alert for In-memory Webshell Insertion: displays alerts for threats that are detected by the in-memory webshell insertion engine.
Find an alert that you want to manage, click Details in the Actions column to view Details and Alert Analysis of the detected in-memory webshells, and decide whether you need to handle the in-memory webshells.
On the Details tab, you must enable the Decompiled Java File switch to view the source code of Java programs running in the memory. If this switch is turned off, Security Center will not display the decompiled code.
On the Alert Analysis tab, you can find the AI-powered analysis of the code running in the memory, along with the clear evidence of the presence of in-memory webshells. This information allows for a precise evaluation of whether the identified in-memory webshell poses a significant threat, enhancing detection capability and response efficiency.
ImportantYou must enable the Decompiled Java File switch to access the Alert Analysis tab. The alert analysis feature may process the decompiled Java files.
You can use one of the following methods to handle the alert:
Manually handle detected in-memory webshells: Restart the affected application during off-peak hours to clear in-memory webshells. After you clear the in-memory webshells, set the handling method of the alert to Mark as Handled.
Enable protection with a few clicks: Change the protection mode of the application group to which the affected server belongs to Block. After you enable the Block protection mode, the system automatically blocks all injection and execution of in-memory webshells in the application group in subsequent detection.
Ignore: If you do not want to handle the alert, you can set the handling method of the alert to Ignore in the Security Center console.
Add the alert to the whitelist: Go to the Attack Alerts tab, find the required alert, and then click Handle in the Actions column to add the alert to the whitelist. For more information, see Add an attack alert to a whitelist.
NoteAlert for In-memory Webshell Detection cannot be added to the whitelist.
Enable or disable the in-memory webshell prevention feature
You can enable or disable the in-memory webshell prevention feature for an application group. To enable and disable the feature, perform the following operations:
Log on to the Security Center console. In the top navigation bar, select the region of the asset that you want to manage. You can select China or Outside China.
In the left-side navigation pane, choose .
On the Application Configurations tab of the Application Protection page, find the application group that you want to manage and click Protection Policy in the Actions column.
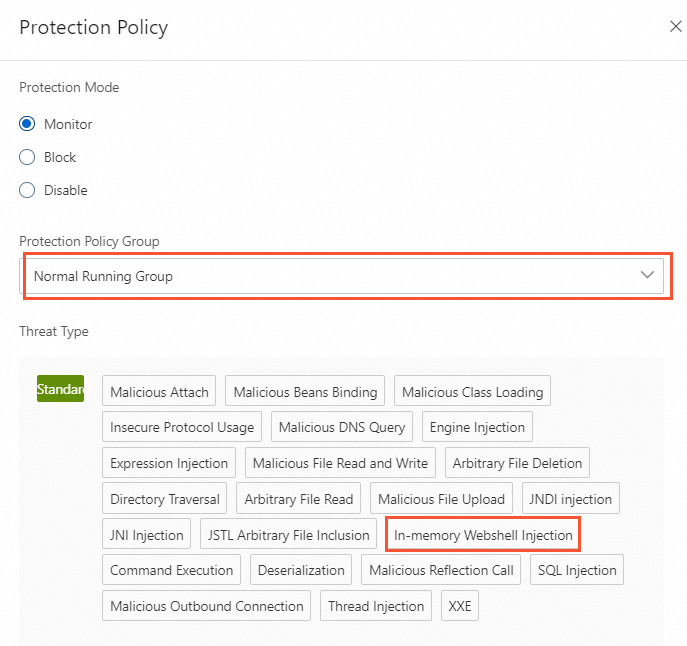
On the Protection Policy tab of the Protection Policy panel, select a protection policy group whose threat detection types include In-memory Webshell Injection or a protection policy group whose threat detection types do not include In-memory Webshell Injection.
If you select a protection policy group whose threat detection types include In-memory Webshell Injection, the in-memory webshell injection engine is enabled. If you set the Protection Mode parameter to Monitor, the system generates alerts but does not block threats. If you set the Protection Mode parameter to Block, the system generates alerts for and blocks injection and execution of in-memory webshells.
On the Detection Policy tab of the Protection Policy panel, turn on or turn off In-memory Webshell Detection and click OK.
After you turn on In-memory Webshell Detection, the system can detect in-memory webshells in the application group.