This topic describes how to configure and use custom domain names.
Introduction
The custom domain name feature lets you use your own domain name for IDaaS EIAM pages, such as the logon page and user portal. This helps maintain brand consistency.
By setting up a domain proxy service, you can also manage user access permissions to IDaaS EIAM. For example, you can allow only users with specific IP addresses to log on to the application portal.
Terms
Term | Description |
Initialization domain name | The domain name generated by the system when you create an IDaaS EIAM instance, such as xxxx.aliyunidaas.com. |
Custom domain name | A domain name that you own and add to your IDaaS EIAM instance, such as xxxx.example.com. |
Default domain name | The domain name that the IDaaS EIAM instance uses by default. You must select either an initialization domain name or a custom domain name. If you enable automatic redirection, accessing the initialization domain name redirects you to the default domain name. |
Affected features
Custom domain names affect the following features. You must adjust their configurations before or after you set up a custom domain name.
Affected object | Feature | Description |
User portal | Logon page | The logon page address involves a domain name. |
Application portal | The application portal address involves a domain name. | |
DingTalk identity provider - Outbound | QR code logon/Workbench SSO | The DingTalk callback domain involves a domain name. Always use the initialization domain name. |
SSO to IDaaS application portal or applications | The application home page address involves a domain name. | |
WeCom identity provider - Inbound | QR code logon | The domain that users access (the user portal or the address for direct access to custom/OIDC/SAML applications) must be the same as the WeCom authorization callback domain. Otherwise, users cannot log on using a WeCom QR code. |
Webpage authorization logon (Workbench SSO) and sensitive data synchronization | The domain that users access (the user portal or the address for direct access to custom/OIDC/SAML applications) must be the same as the WeCom trusted domain. Otherwise, WeCom webpage authorization logon and sensitive data synchronization will not work. | |
OIDC applications/Custom applications | Authorization endpoint | If the instance only needs one custom domain name, use the initialization domain name. Set the custom domain name as the default domain name and enable automatic redirection. If you do not enable redirection, users might need to log on again during single sign-on. If the instance needs multiple custom domain names, they must be consistent with the user's logon page domain. Otherwise, users might need to log on again during single sign-on. |
Logout endpoint | ||
SAML applications | IdP metadata address | If the instance only needs one custom domain name, use the initialization domain name. Set the custom domain name as the default domain name and enable automatic redirection. If you do not enable redirection, users might need to log on again during single sign-on. If the instance needs multiple custom domain names, they must be consistent with the user's logon page domain. Otherwise, users might need to log on again during single sign-on. |
SSO address | ||
WebAuthn | Register authenticator | WebAuthn only works on the domain where the authenticator was registered. For example, if a user registers authenticator A1 on domain A, they cannot use authenticator A1 to log on to domain B. They must register a new authenticator on domain B. A user can have multiple authenticators for different domains. |
Prerequisites
Prepare the following items in advance to ensure a smooth configuration process for your custom domain name:
Prerequisites | Description |
Domain name | Prepare a dedicated domain name for IDaaS EIAM. A top-level or second-level domain is recommended. |
Permissions to manage the domain's DNS | You must add one or two DNS records with your DNS provider, such as Alibaba Cloud DNS, to verify domain ownership. |
ICP filing number | If your website is hosted in the Chinese mainland, you must provide the domain's ICP filing number. |
Permissions to manage the domain's proxy service | You must configure the domain's HTTPS certificate, back-to-origin HOST, and other information with your domain's proxy service, such as Alibaba Cloud DCDN. |
Trial or upgraded instance | Only trial and Enterprise instances support the custom domain name feature. Try an instance or upgrade your instance. |
Add a custom domain name - Domain configuration
Click to start.
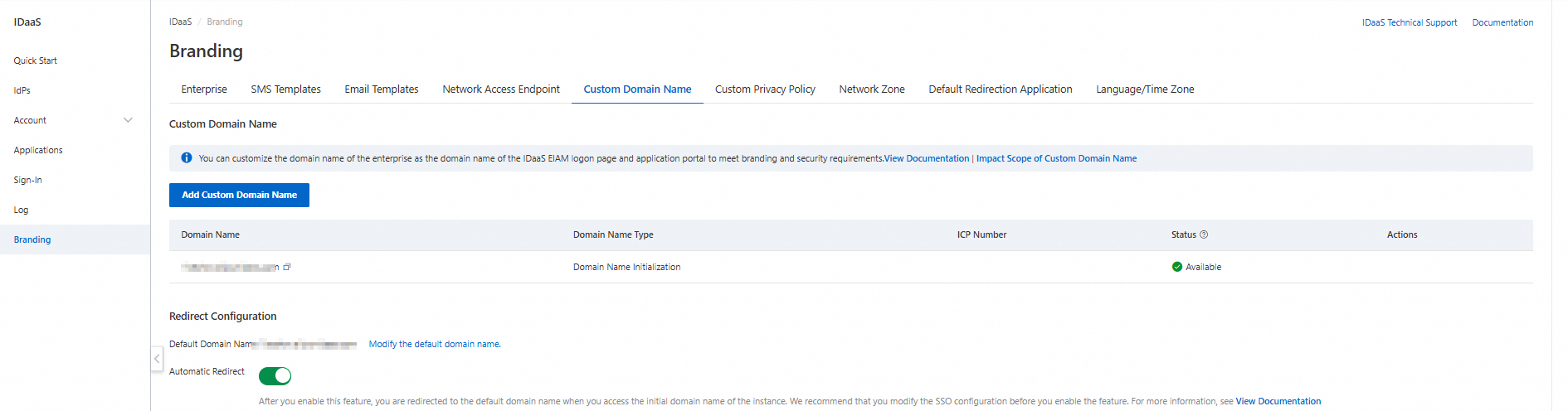
Custom domain names can affect features such as logon, single sign-on, and data synchronization. To avoid disrupting your business, understand the affected features before you proceed.
Step 1: Enter the domain name
Enter the custom domain name, such as login.example.com. This domain name must be globally unique across all IDaaS EIAM instances. Enter only the domain name itself, without any path or parameters. The domain name can contain lowercase letters, digits, hyphens (-), and periods (.). The maximum length is 128 characters.
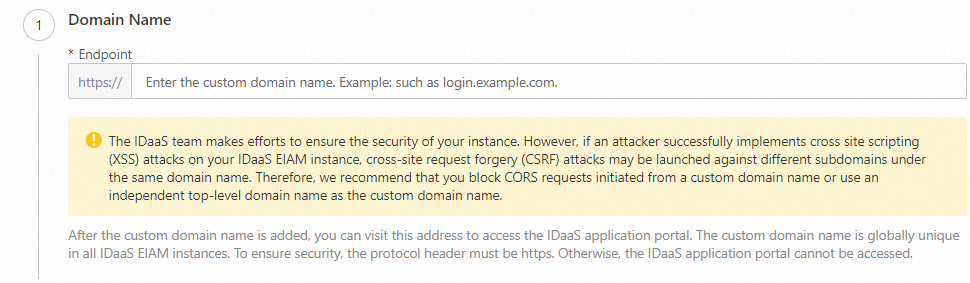
The IDaaS team is committed to securing your instance. However, if an attacker successfully launches a Cross-Site Scripting (XSS) attack on your IDaaS EIAM instance, it could lead to a Cross-Site Request Forgery (CSRF) attack on other subdomains under the same domain. Therefore, block Cross-Origin Resource Sharing (CORS) requests from the custom domain name, or use a separate top-level domain as your custom domain name.
Step 2: Add a DNS record
Go to your domain's DNS provider, such as Alibaba Cloud DNS, to add a record. This step verifies your ownership of the domain. For the same IDaaS EIAM instance and custom domain name, the record type, name, and value are fixed. If you do not have permission to manage DNS, you can ask an authorized user to add the DNS record. You can then add the custom domain name after the record is created.
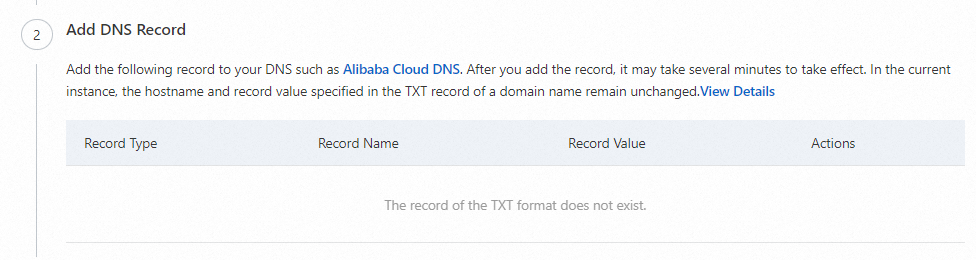
The following topics explain how to add DNS records with different DNS providers:
Step 3: Enter the ICP filing number
According to the Administrative Measures on Internet Information Services, if your website is hosted in the Chinese mainland, you must provide an entity or website ICP filing number. To meet compliance requirements, all IDaaS EIAM instances in Alibaba Cloud regions in the Chinese mainland must have this number to use the custom domain name feature. The ICP filing number will be displayed on the instance's logon page.
Step 4: Complete the process
After you confirm that the information is correct, click Complete. You must also complete the proxy configuration to enable the custom domain name.
Add a custom domain name - Proxy configuration
When your users or applications access IDaaS EIAM through a custom domain name, your domain proxy service forwards the requests. You must ensure the availability of the proxy. The following sections describe how to configure the proxy service.
Alibaba Cloud DCDN
Step 1: Add a domain name
Add a domain name on the Domain Names page of the Alibaba Cloud DCDN console.
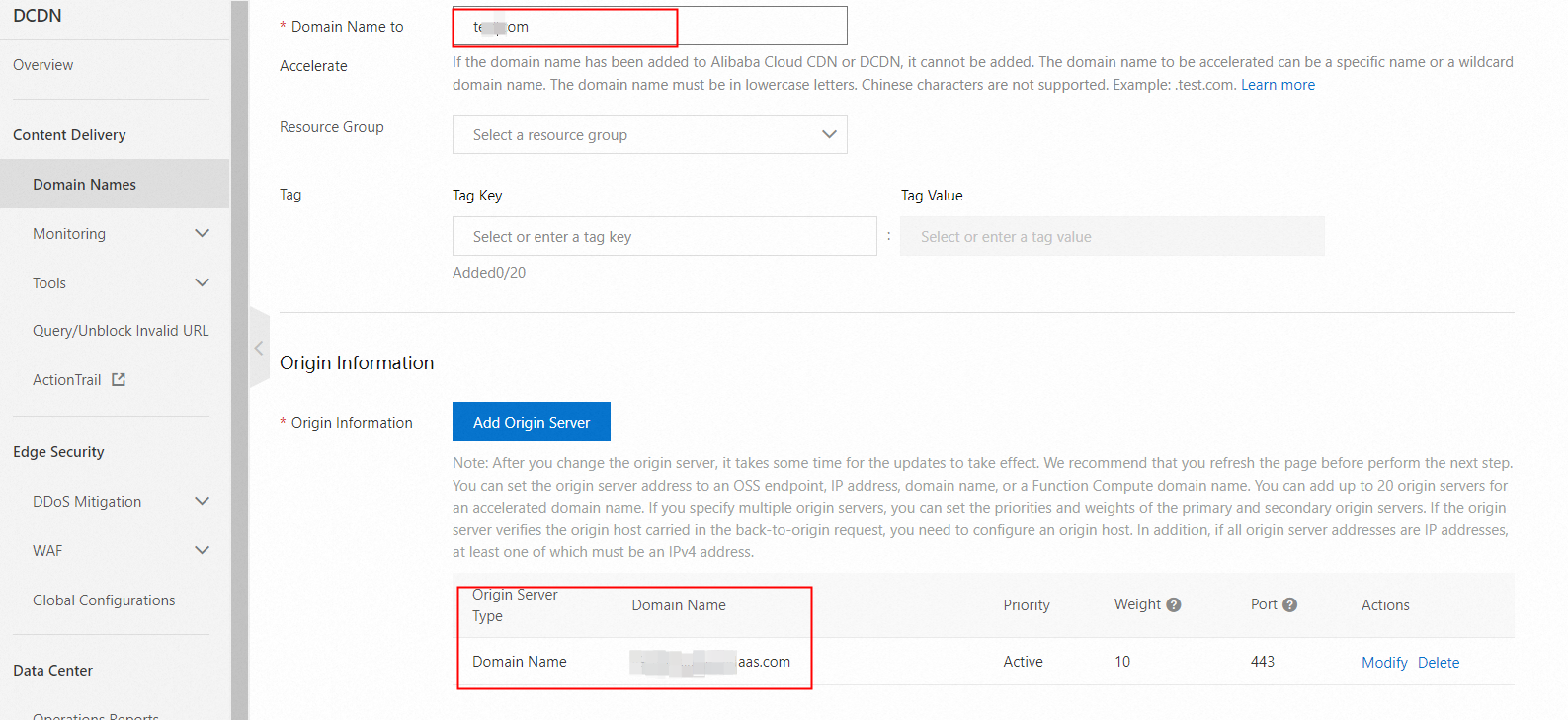
Accelerated Domain Name: Your custom domain name.
Origin Info:
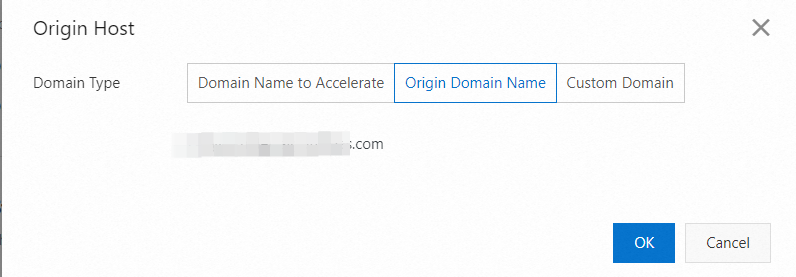
Set Origin Type to Origin Domain Name.
Enter the domain name from the origin information on the proxy configuration page. This is the initialization domain name of your IDaaS EIAM instance. Do not include the https:// protocol header.
Set Port to 443.
After you add the domain name, copy the CNAME record provided by DCDN. Then, add this CNAME record to your domain's DNS settings. For more information, see Configure a CNAME record.
Step 2: Configure an HTTPS certificate
In the Alibaba Cloud DCDN console, from the Domain Names page, navigate to the Domain Details Page. On the SSL Certificate tab, configure an HTTPS certificate. For more information, see Configure an HTTPS certificate.
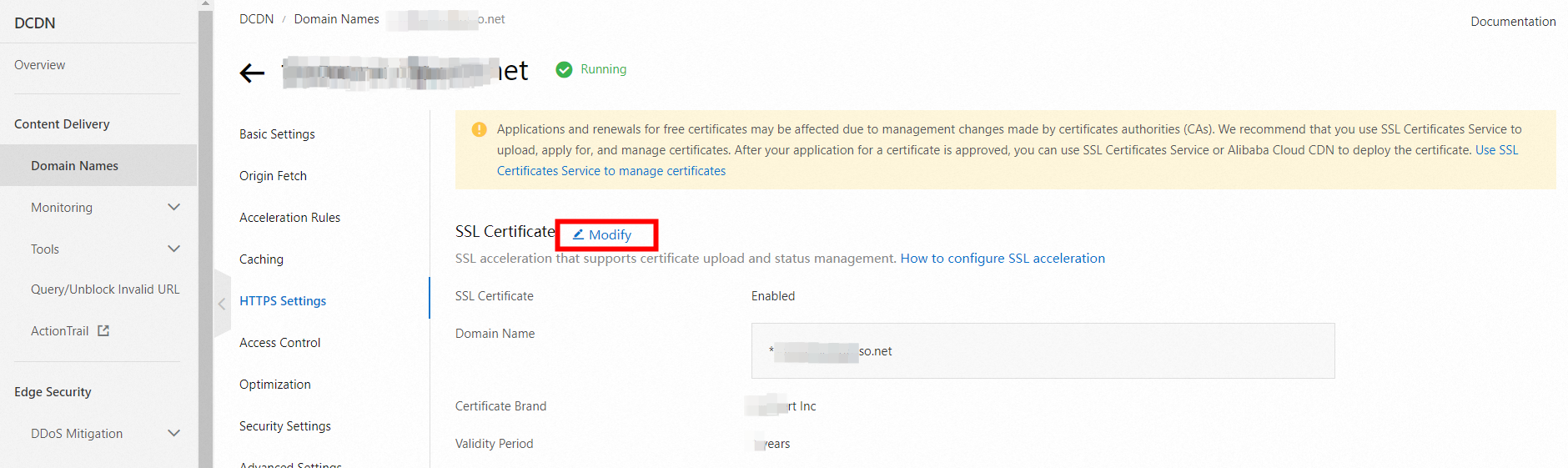
Step 3: Enable back-to-origin HOST
On the domain details page, on the Origin Fetch tab, enable Origin HOST.
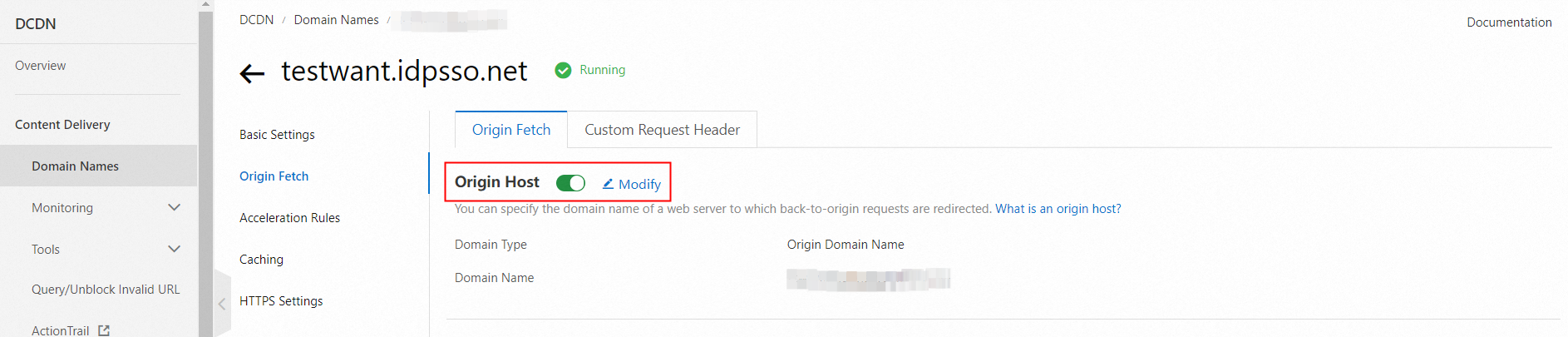
Set Domain Name Type to Origin Domain Name. The initialization domain name of the IDaaS EIAM instance is automatically selected.
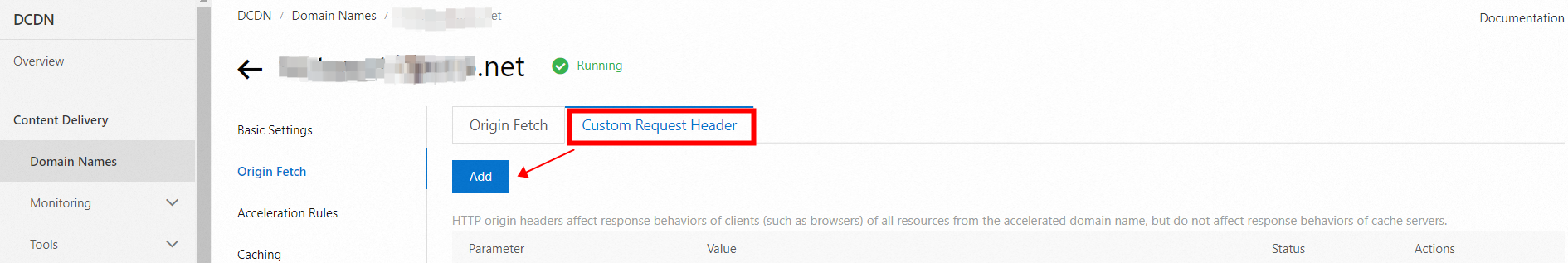
Step 4: Add a back-to-origin HTTP header
On the domain details page, on the Origin Fetch tab, click Custom Request Header. Add the IP, Host, Token, and other information provided by IDaaS EIAM. This information helps prevent IP address spoofing and improves access security.
After the configuration is complete, you can use the Test Connectivity feature in the IDaaS EIAM console to simulate access to your custom domain name. Note that you can set access policies for the domain itself, such as allowing access only from specific IP addresses. Therefore, the test results from IDaaS EIAM are for reference only. You must test the setup in a simulated user environment.

After the test is successful, confirm and adjust the relevant configurations based on the affected features. Then, roll out the custom domain name to your users. If you expect users to continue accessing the initialization domain name, enable automatic redirection.
Nginx configuration guide
Step 1: Install a self-managed Nginx service
Install from source code
# Download the installation package
wget http://nginx.org/download/nginx-1.18.0.tar.gz
# Decompress the package
tar -zxvf nginx-1.18.0.tar.gz
cd nginx-1.18.0
# Configure: Specify the Nginx installation directory
./configure --prefix=/usr/local/nginx
# Compile and install
make && make install
# After installation, verify that it was successful
cd /usr/local/nginx/sbin
./nginx -t After the installation is complete, the following output indicates success:
nginx: the configuration file /usr/local/nginx//conf/nginx.conf syntax is ok
nginx: configuration file /usr/local/nginx//conf/nginx.conf test is successful
Install on CentOS/AlmaLinux/RHEL
# Install the EPEL repository (required for some systems)
sudo yum install epel-release -y
# Install Nginx
sudo yum install nginx -y
# Start the Nginx service
sudo systemctl start nginx
# Enable Nginx to start on boot
sudo systemctl enable nginx
# Check the service status
sudo systemctl status nginxInstall on Ubuntu/Debian
# Update the package list
sudo apt update
# Install Nginx
sudo apt install nginx -y
# Start the Nginx service
sudo systemctl start nginx
# Enable Nginx to start on boot
sudo systemctl enable nginx
# Check the service status
sudo systemctl status nginxStep 2: Modify the Nginx configuration file
View the path of the Nginx configuration file.
nginx -tConfigure the domain proxy.
Modify the server node under the http node in the
nginx.confconfiguration file.Modify the reverse proxy configuration to forward requests from the custom domain name, such as
www.example.com, to the IDaaS EIAM initialization domain name*****.aliyunidaas.com.server { # Listen on the HTTPS port and enable SSL listen 443 ssl; # Domain configuration (the domain to be forwarded, which is the user's custom domain name) server_name www.example.com; location / { # Reverse proxy target address (the configured IDaaS user portal domain address) proxy_pass https://*****.aliyunidaas.com; } }
Configure HTTP to HTTPS redirection.
This automatically redirects HTTP access to your custom domain name to HTTPS, which improves security and search engine optimization (SEO).
# HTTP server block (listens on port 80) server { listen 80; server_name www.example.com; # Configure redirection of HTTP requests to HTTPS location / { return 301 https://$host$request_uri; } }Configure an SSL certificate.
Prepare the certificate file and upload it to the Nginx server.
Modify the Nginx configuration file.
server { # HTTPS server block (listens on port 443) listen 443 ssl; server_name www.example.com; # SSL certificate path (replace with the actual path) ssl_certificate /usr/local/nginx/ssl/www.example.com.crt; ssl_certificate_key /usr/local/nginx/ssl/www.example.com.key; # SSL configuration (optional optimization) ssl_protocols TLSv1.2 TLSv1.3; ssl_ciphers HIGH:!aNULL:!MD5; }
Configure IDaaS EIAM back-to-origin request headers.

Modify the server node under the http node in the nginx.conf configuration file.
Use proxy_set_header to set the back-to-origin request headers.
# Configure IDaaS back-to-origin request headers location / { proxy_pass http://***.aliyunidaas.com; # Pass the client's real IP address proxy_set_header X-IDaas-Client-IP $remote_addr; # Pass the host header (confirm the Host value expected by the target service) proxy_set_header X-IDaas-Host eiam-idaas.idpsso.net; # Proxy authentication token (must be consistent with the IDaaS server-side configuration) proxy_set_header X-IDaas-Proxy-Token PTC*****************************6j; # Preserve the original Host header (optional) proxy_set_header Host $host; }
Step 3: Restart the Nginx service
Restart for installation from source code
sudo /usr/local/nginx/sbin/nginx -s reloadRestart for CentOS/AlmaLinux/RHEL installation
sudo service nginx restartRestart for Ubuntu/Debian installation
sudo systemctl restart nginxDomain status
Because you can set access policies for the domain itself, such as allowing access only from office network IP addresses, IDaaS EIAM cannot confirm whether the custom domain name is running properly. Therefore, the availability status in the IDaaS EIAM console only indicates that the custom domain name feature is enabled for the instance. It does not guarantee that the domain is accessible. You must verify that the custom domain name is running properly.
Modify the default domain name
The default domain name is the domain that the instance uses by default. It has two purposes:
If you enable the Automatic Redirection feature, your users or applications are automatically redirected to the default domain name when they access the initialization domain name.
It is displayed in multiple places in the console, such as the user portal address and the logon address.

If you select a custom domain name as the default domain name and enable automatic redirection, you must manually change the default domain name if the custom domain name becomes unavailable, for example, when the instance expires. Otherwise, your users and applications may be unable to access the instance.
Enable automatic redirection
Automatic redirection means that when a user or application accesses the instance's initialization domain name, they are automatically redirected to the default domain name. Accessing a custom domain name does not trigger a redirection to the default domain name. If you only need to use one custom domain name, set it as the default domain name and enable automatic redirection. This allows your users to seamlessly use single sign-on for applications, whether they access the initialization domain name or the custom domain name, without needing to modify the application's single sign-on configuration.
If you do not enable this feature or need to use multiple custom domain names, you must adjust the application's single sign-on and other configurations (see Affected features) to work with the custom domain name. Otherwise, users may experience issues. For example, users might need to log on again during single sign-on, or they might not be able to log on using a WeCom QR code.
Delete a custom domain name
Before you delete a custom domain name, check if it is in use, for example, in identity provider or application single sign-on configurations. The last used time for the domain shown in the pop-up window can be used as a reference. This time corresponds to the last used time of the proxy_token, which you can view directly in the proxy configuration.
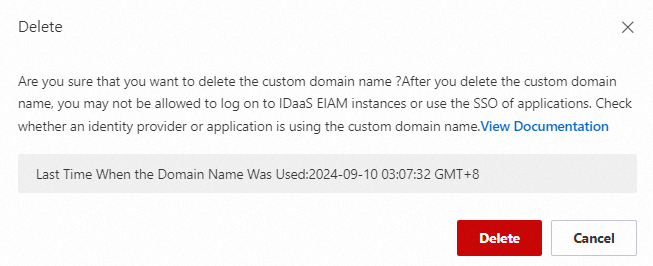
After you delete a custom domain name, it can no longer be used to access the IDaaS EIAM instance. To prevent incorrect domain forwarding, you must also remove the related configurations from your DNS provider and proxy service.