This topic describes the cause of and solution to the issue that an error message similar to "As a security precaution, the user account has been locked because there were too many logon attempts or password change attempts" appears when you connect to a Windows Elastic Compute Service (ECS) instance by using Remote Desktop Protocol (RDP).
Problem description
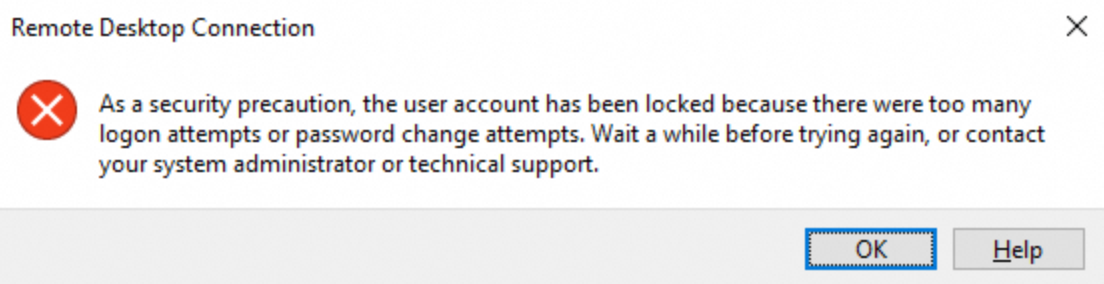
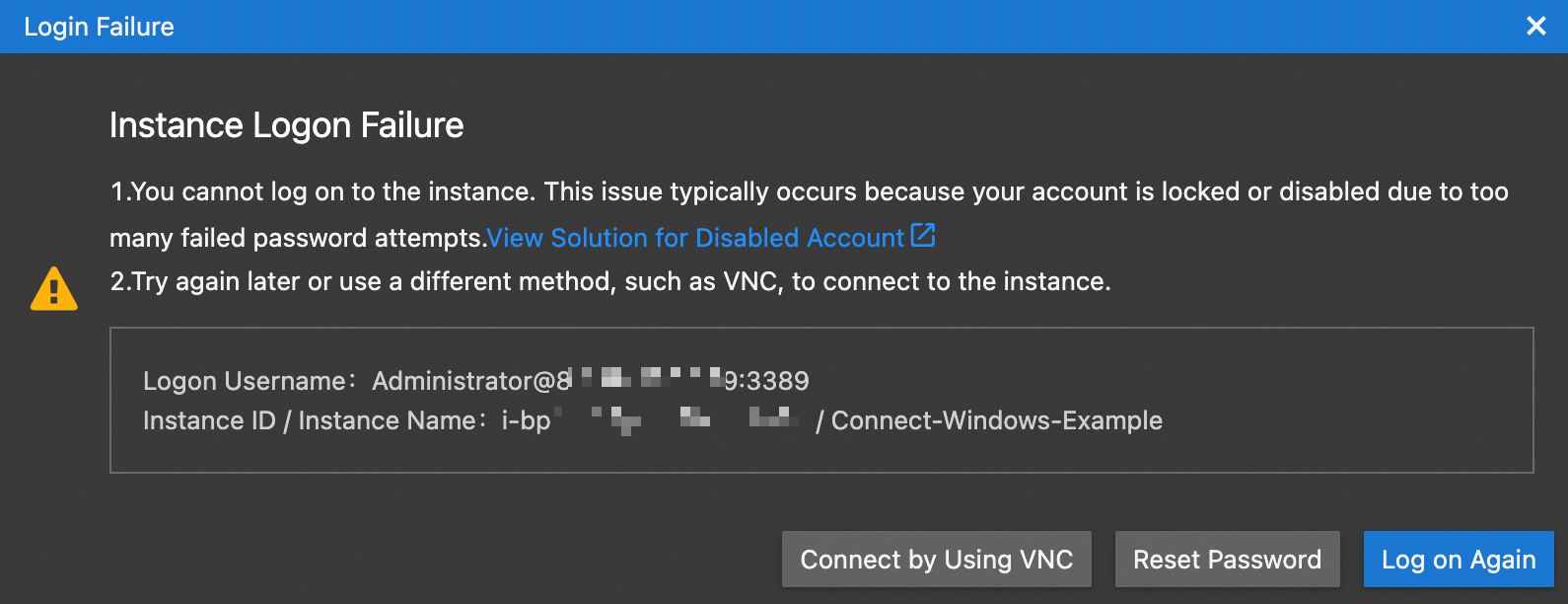
When you use an RDP client, such as Remote Desktop, Workbench, or Windows App, to connect to a Windows ECS instance, the "As a security precaution, the user account has been locked because there were too many logon attempts or password change attempts" error message or a similar error message appears. The following figures show the error messages reported by different RDP clients.
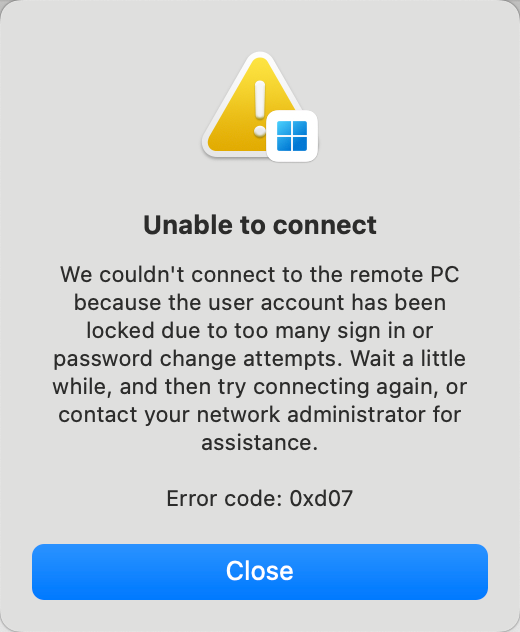
Cause
The account locking mechanism is a built-in security mechanism of Windows. The preceding issue may occur because you entered an incorrect password multiple times when you connect to the Windows ECS instance. The account locking mechanism is triggered to lock your account. This ensures system security and reduces the risk of password cracking.
If the preceding issue occurs when you connect to the Windows ECS instance, check whether you recently entered incorrect passwords multiple times. If you did not enter incorrect passwords multiple times, a hacker may be trying to crack the password of the Windows ECS instance.
Solution procedure
To resolve the preceding issue, you can use security groups to limit the IP addresses that can be used to connect to the Windows ECS instance.
The remote connection port (3389) of Windows is a high-risk port. If the port is open to all public IP addresses, security risks may occur. You must configure appropriate security group rules to prevent unexpected hosts from connecting to your ECS instance. Perform the following steps to resolve the preceding issue:
Modify the security group rules to prohibit all IP addresses from accessing the RDP service of the Windows ECS instance.
To prevent the preceding issue from reoccurring in subsequent operations, you must modify the security group rules associated with the Windows ECS instance to prohibit all IP addresses from accessing the RDP port on the instance. This prevents anyone from using an RDP client, such as Remote Desktop, Windows App, or Workbench, to connect to the instance over the Internet and resolves the issue of remote logons from unknown hosts.
Connect to the Windows ECS instance by using Virtual Network Computing (VNC) and unlock the account.
After you prohibit all users from accessing the RDP service on the Windows ECS instance, you can connect to the instance by using VNC in the ECS console. After you connect to the Windows ECS instance by using VNC, the account is automatically unlocked.
Modify the security group rules.
To ensure that you can use an RDP client to connect to the Windows ECS instance, modify the inbound rules in the security groups to which the instance belongs based on the principle of least privilege to limit the IP addresses that can access the RDP port.
Verify that you can use an RDP client to connect to the Windows ECS instance.
Connect to the Windows ECS instance by using an RDP client to verify that the security group rules that you configured are in effect and that the account is unlocked.
Step 1: Modify the security group rules to prohibit all IP addresses from accessing the RDP service of the Windows ECS instance
To prevent the preceding issue from reoccurring in subsequent operations, you must modify the security group rules associated with the Windows ECS instance to prohibit all IP addresses from accessing the RDP port on the instance. This prevents anyone from using an RDP client, such as Remote Desktop, Windows App, or Workbench, to connect to the instance over the Internet and resolves the issue of remote logons from unknown hosts. Perform the following steps:
In the ECS console, find the security groups to which the Windows ECS instance whose account you want to unlock belongs.
Log on to the ECS console.
In the left-side navigation pane, choose .
In the top navigation bar, select the region in which the Windows ECS instance that you want to manage resides and the resource group to which the instance belongs.

On the Instance page, find the Windows ECS instance whose account you want to unlock and click the instance ID to go to the instance details page.
Click the tab. The page that appears displays all security groups that are associated with the Windows ECS instance.
Modify security group rules to block the RDP port.
Click Manage Rules in the Operation column that corresponds to each security group to access the security group details page.
Find all rules whose Port Range parameter contains the RDP port (3389 by default). Delete the rules or change the action of the rules to Deny.
Before you modify the security group rules, we recommend that you back up the original security group rules. This allows you to restore the rules if required.
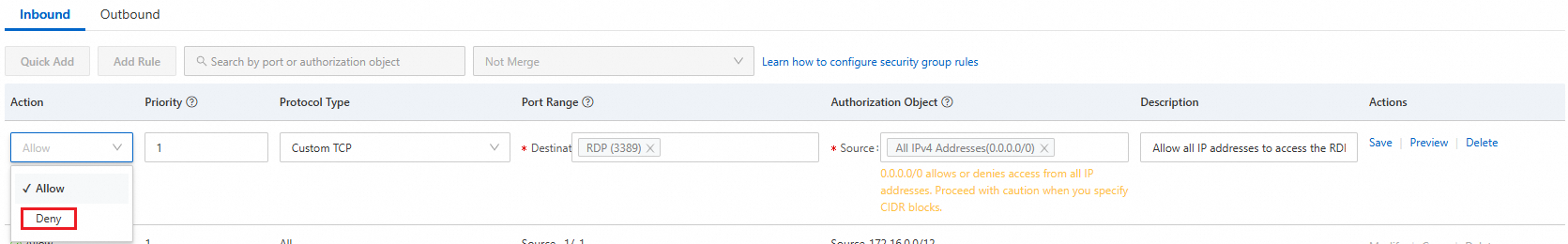
Verify that no host on the public network can connect to the Windows ECS instance by using RDP.
Step 2: Connect to the Windows ECS instance by using VNC and unlock the account
After you prohibit all users from accessing the RDP service on the Windows ECS instance, you can connect to the instance by using VNC in the ECS console. After you connect to the Windows ECS instance by using VNC, the account is automatically unlocked.
In the ECS console, find the Windows ECS instance whose account you want to unlock.
Log on to the ECS console.
In the left-side navigation pane, choose .
In the top navigation bar, select the region and resource group to which the resource belongs.

On the Instance page, find the Windows ECS instance whose account you want to unlock.
To go to the VNC connection page of the Windows ECS instance to which you want to connect, perform the following steps:
In the Actions column that corresponds to the instance, choose .
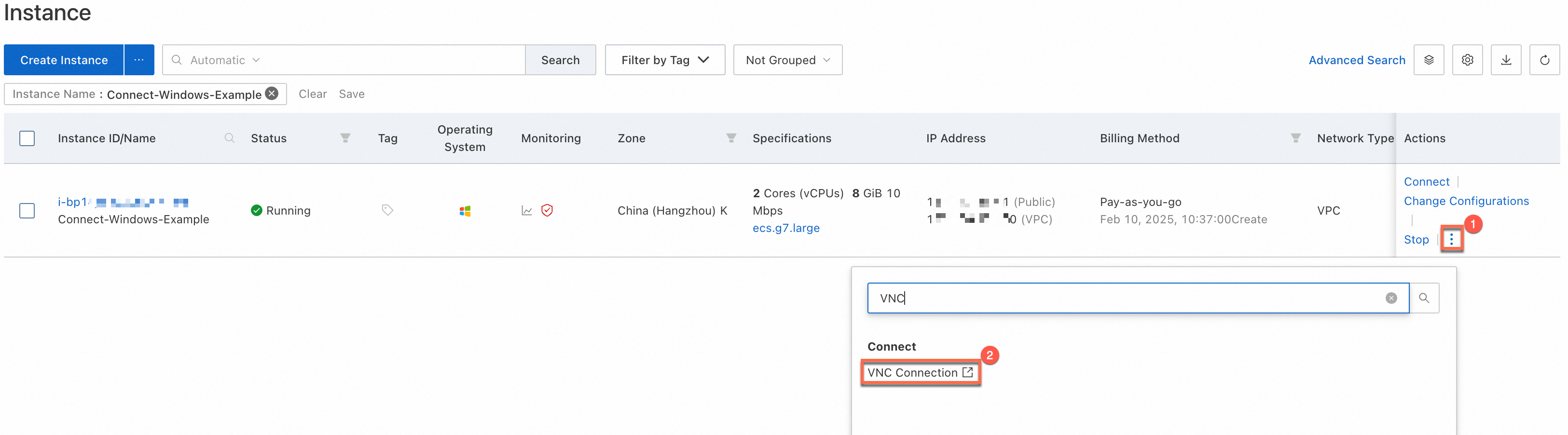
The following figure shows the VNC connection page.
In this example, an instance that runs Windows Server 2025 is used.
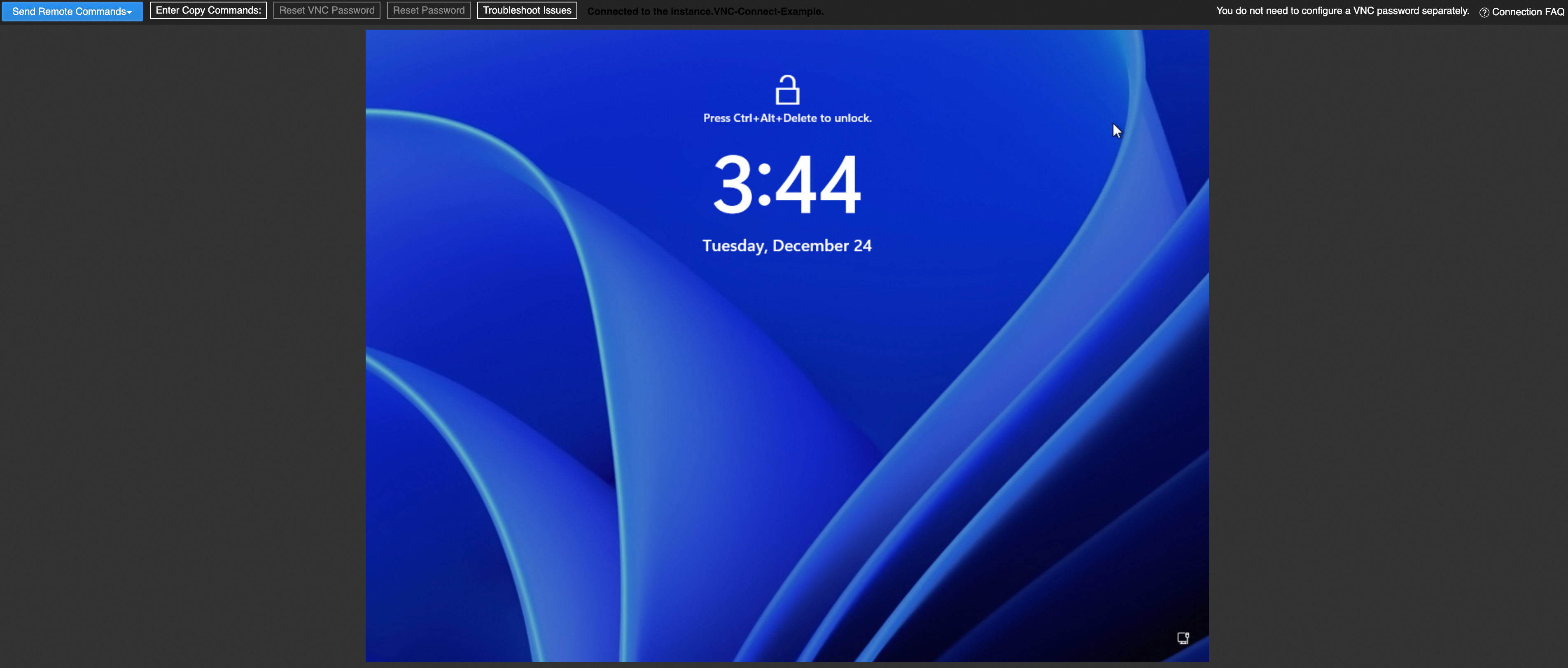
Log on to the Windows operating system. After you log on to the Windows operating system, the account is automatically unlocked.
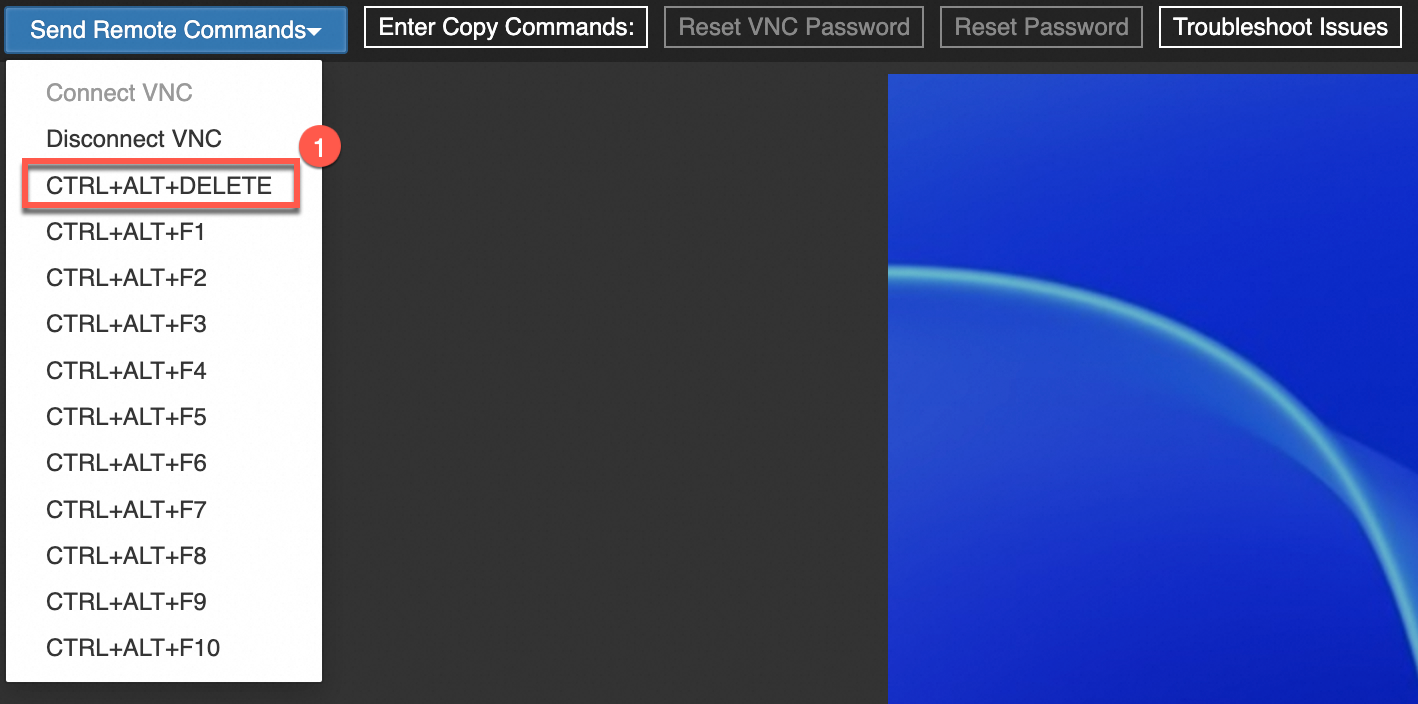
In the upper-left corner of the VNC connection page, choose to unlock the Windows operating system.
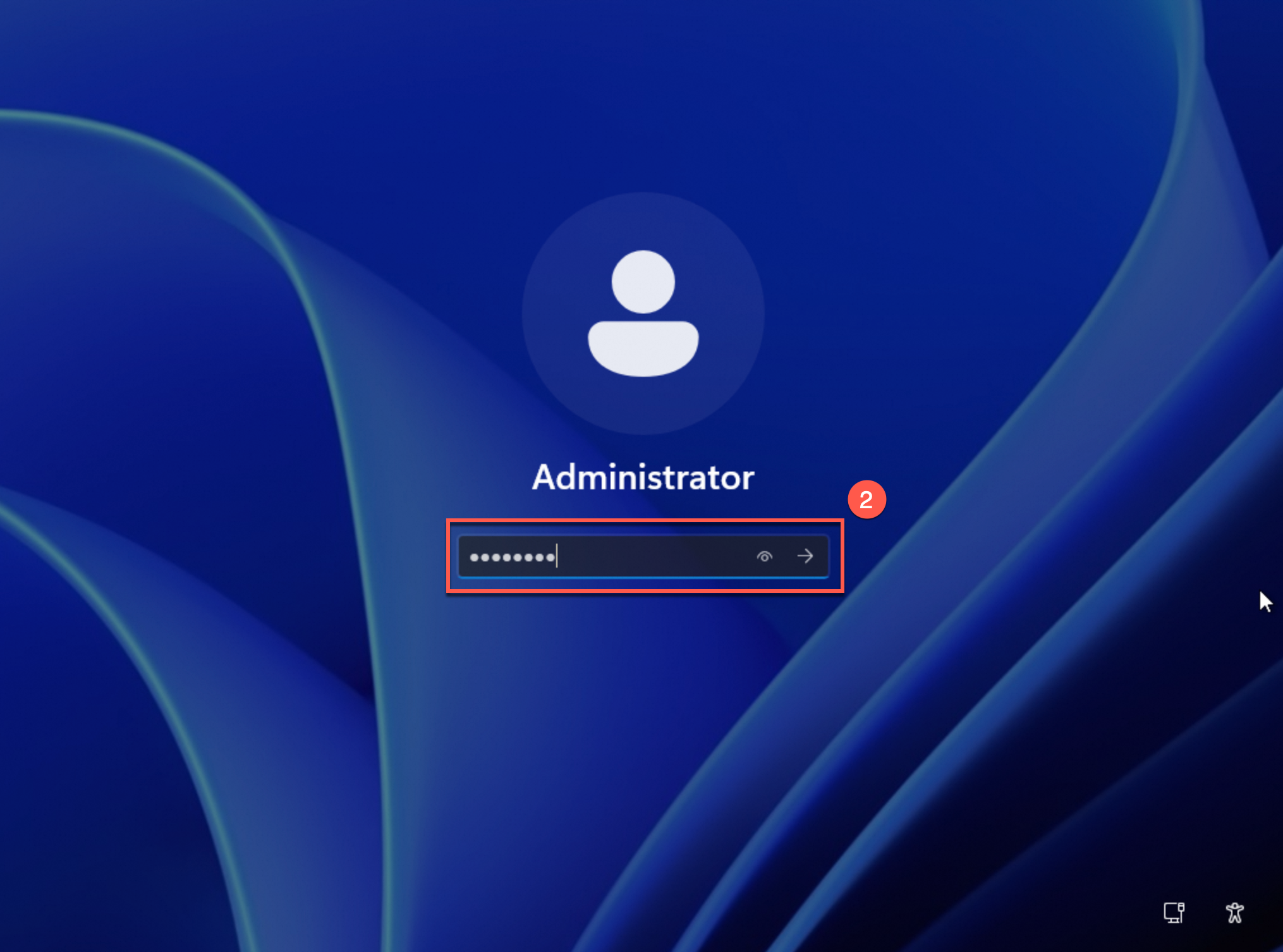
Select a username, enter the password, and then press the Enter key to log on to the operating system of the instance. The default username is Administrator.
If you do not know your username or password, or if you forget your password, reset the password first. For more information, see Reset the logon password of an instance.
Step 3: Modify security group rules
In Step 1, you prohibited all IP addresses from connecting to the Windows ECS instance by using RDP. To ensure that you can use an RDP client to connect to the instance, modify the inbound rules in the security groups to which the instance belongs based on the principle of least privilege to allow only the IP address of your host to connect to the instance by using RDP. To modify the inbound rules in the security groups to which the Windows ECS instance belongs, perform the following steps:
Plan security group settings. Determine the IP addresses or CIDR blocks of the hosts that are allowed to connect to the Windows ECS instance.
Before you modify security group rules, obtain the IP addresses or CIDR blocks of all hosts that need to connect to the Windows ECS instance. If you want to allow your on-premises host to connect to the Windows ECS instance, go to the https://cip.cc/ website to obtain the IP address of the host. For information about the best practices for configuring security group rules, see Best practices for security groups (inbound rules).
Modify security group rules.
Find the security groups that you modified in Step 1.
Click Manage Rules in the Operation column that corresponds to each security group. On the Inbound tab in the Access Rule section, click Add Rule to add a security group rule. The rule allows only the IP address of your host to access the RDP port of the Windows ECS instance. The following table describes the parameters.
Action
Priority
Protocol type
Port range
Authorization object
Action
Priority
Protocol type
Port range
Authorization object
Allow
1
Custom TCP
Select RDP (3389).
The default port number is 3389 when you connect to a Windows ECS instance by using RDP.
The port that you must configure varies based on the actual port used by RDP on the Windows ECS instance. If you changed the RDP port on the Windows ECS instance, specify the actual RDP port.
Specify the public IP address of your on-premises host or the CIDR block to which the public IP address belongs.
If you specify
0.0.0.0/0, access on the specified port is allowed for all IPv4 addresses. This poses security risks and may repeatedly cause the account locking issue to occur.You can obtain the public IP address of your on-premises host from
https://cip.cc/.
Step 4: Verify that you can use an RDP client to connect to the Windows ECS instance
Use an RDP client to connect to the Windows ECS instance, and check whether the rules in the security groups to which the instance belongs are in effect and the account of the instance is unlocked.
If the account is still locked when you connect to the Windows ECS instance, you can manually change the Windows account lockout policy. For more information, see the Change the Windows account lockout policy section of this topic.
Related operations
To change the Windows account lockout policy, such as the maximum number of password retries and account lockout events, perform the following steps.
Suggestions on how to improve Windows security
Configure security groups. Use security groups to restrict the hosts that can connect to a Windows ECS instance. For more information, see the Step 3: Modify security group rules section of this topic.
Change the RDP port. Change the RDP port to a non-default port to reduce the risk of port scanning attacks. For more information, see Change the default port used by an instance to accept connections.
Use strong passwords. Improve password strength, do not use common passwords, and change passwords on a regular basis. For more information, see Reset the logon password of an instance.