You may need to migrate an Elastic Compute Service (ECS) instance from one virtual private cloud (VPC) to another to meet changing business needs, organizational changes, or updated security policies. This operation helps you achieve network isolation, redesign your network architecture, or resolve IP address conflicts. You can change an instance's VPC without changing its region or availability zone.
Changing the VPC causes a temporary service interruption. We recommend that you perform this operation during off-peak hours. Before you start, create a snapshot to back up your data.

Impacts and risks
Service interruption: The operation requires the instance to be in the Stopped state, which interrupts services.
Private IP address change:
The instance's primary private IP address changes to a new IP address from the CIDR block of the destination vSwitch. You can either specify the new IP address or let the system assign one automatically. Applications or services with the original private IP address hard-coded (for example, in database connection strings, firewall allowlists, or other service configurations) will fail. You must manually update these configurations after changing the VPC.
The public IP address remains unchanged.
Network connection lost: The instance will lose private network connectivity to all other resources in the original VPC, such as ApsaraDB RDS instances, Server Load Balancer (SLB) instances, and other ECS instances.
OS network configuration: If the instance's operating system (OS) is configured with a static IP address, its network settings (IP address, gateway, DNS) will not match the new network environment after the VPC change. This will prevent the instance from communicating over the network and may block remote access.
Procedure
Step 1: Preparations
Create a snapshot backup
To prevent data loss from accidental operations, create a snapshot of the instance's system and data disks. These snapshots are required for the rollback procedure.
Stop the instance
The instance must be in the Stopped state. In the console, its status cannot be Locked. If the instance is running, stop it.
Perform prerequisite checks
Secondary Elastic Network Interfaces (ENIs): Detach any secondary ENIs attached to the instance.
Additional IP addresses: If the primary ENI has any secondary private IP addresses or IPv6 addresses, you must first unassign the secondary private IP addresses or delete the assigned IPv6 address.
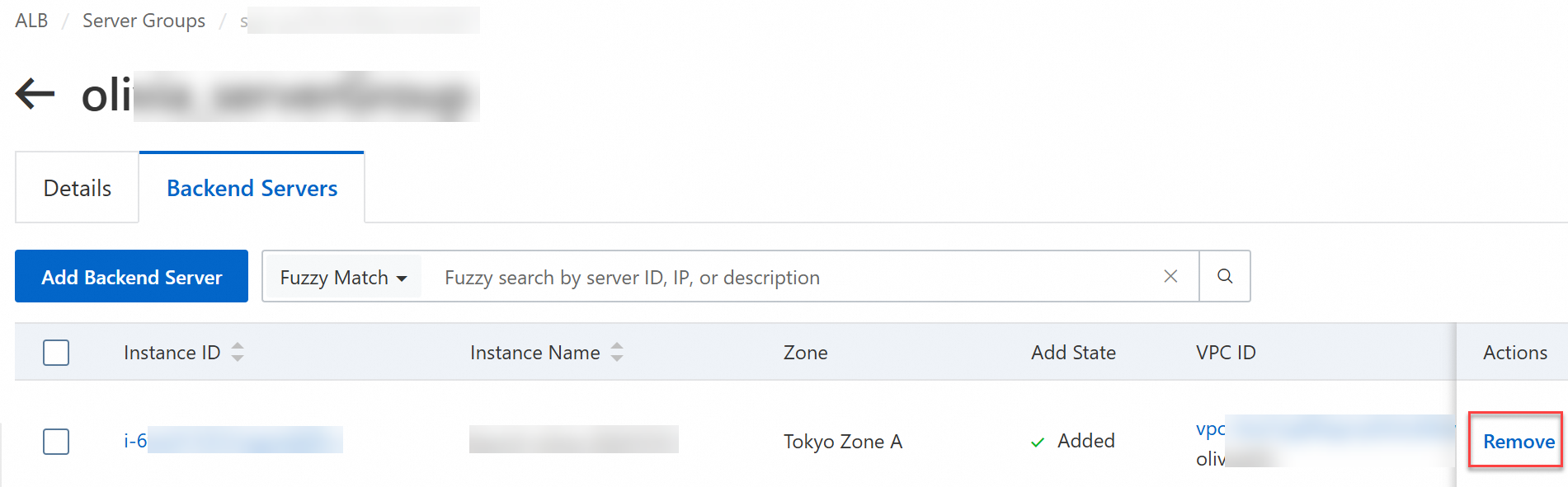
SLB: Remove the instance from any SLB server groups of which it is a member.
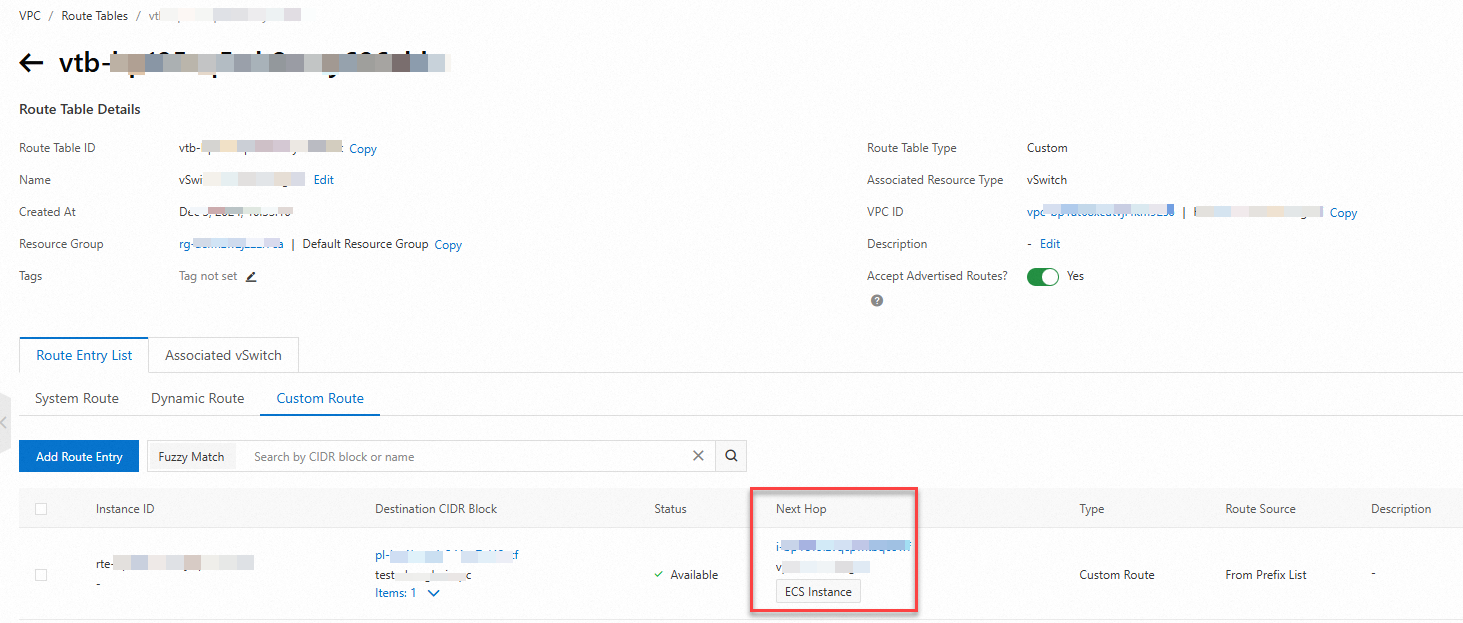
Custom route entries: If the instance is configured in a custom route table, you must delete the relevant route entries.
High-availability virtual IP address (HaVip): If the instance has an associated HaVip, you must disassociate it.
Global Accelerator (GA): If the instance serves as an endpoint in a GA instance, you must delete the endpoint.
(Optional) IP address acquisition method in the instance: If the instance's OS uses a static IP configuration, we strongly recommend you reconfigure it to use Dynamic Host Configuration Protocol (DHCP) before changing the VPC. This lets the OS automatically retrieve the new IP address, subnet mask, and default gateway from the destination VPC.
Linux
For instructions, see Configure DHCP for a Linux instance.
Windows
The following steps use Windows Server 2022 as an example:
Connect to the Windows ECS instance.
For more information, see Use Workbench to connect to a Windows instance over RDP.
Open Network and Sharing Center.
Click Change adapter settings.
Double-click the primary ENI named Ethernet. Then, click Properties in the Ethernet Status dialog box.
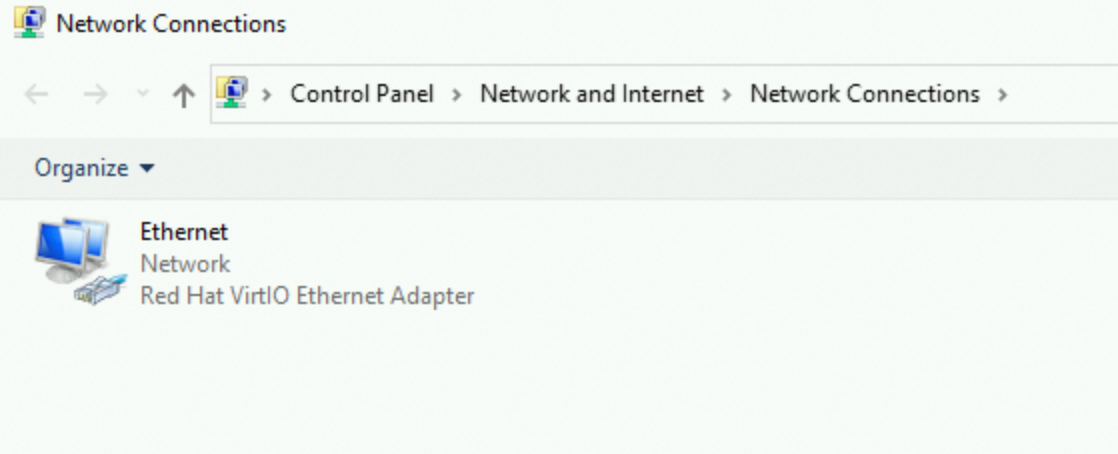
In the Ethernet Properties dialog box, double-click Internet Protocol Version 4 (TCP/IPv4).
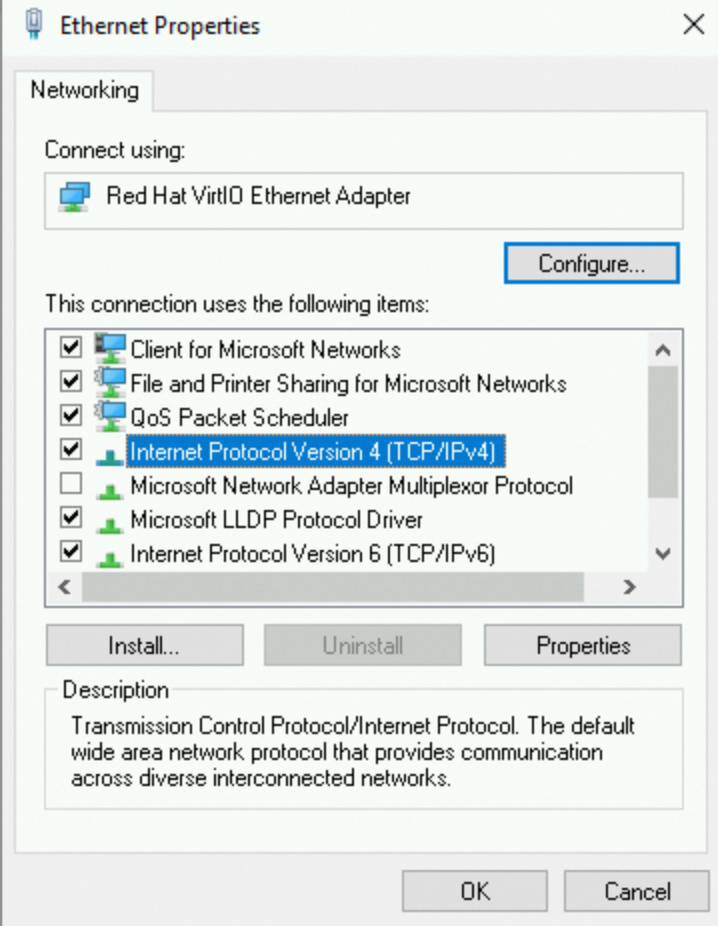
In the Internet Protocol Version 4 (TCP/IPv4) Properties dialog box, select Obtain an IP address automatically.

Prepare destination network resources
VPC and vSwitch: In the destination VPC, ensure a VPC and a vSwitch exist in the same availability zone as the ECS instance.
Security group: In the destination VPC, create or identify the security group that you want to associate with the instance. You can clone a security group to the destination VPC to copy existing rules.
Step 2: Change the VPC
Console
Go to the ECS console. In the top navigation bar, select the region and resource group of the instance.
On the Instances page, click the ID of the instance to go to its details page. In the upper-right corner of the page, choose All Actions > Change VPC.
Change the VPC:
Preparation: View the network information and notes before you make the change.
Select VPC: Set Destination VPC, Destination vSwitch, and Destination Security Group.
You can select one to five destination security groups. The selected security groups must be of the same type: either all basic security groups or all advanced security groups.
(Optional) Configure Primary Private IP Address: You can specify a primary private IP address for the instance. The IP address must be within the CIDR block of the destination vSwitch and must not be in use. If you do not specify an IP address, the system automatically assigns one.
View the change result:
On the Instance Details page, view the new VPC and vSwitch in the Configuration Information section.
After the VPC is changed, the instance does not automatically start. You must manually start the instance.
API
Call the ModifyInstanceVpcAttribute operation to change the VPC.
After the modification is complete, call the DescribeInstances operation to query the new VPC, vSwitch, and security group information of the instance.
After the VPC is changed, the instance does not automatically start. You must call the StartInstance operation to manually start it.
FAQ
How do I change the VPCs for multiple ECS instances in a batch?
Refer to Perform batch operations on the Instances page. You can change the VPCs for up to 20 ECS instances at a time.
How do I convert a CIDR block to an IP address range?
Refer to Examples of converting CIDR blocks to IP address ranges. You can also use the
ipcalccommand-line interface on an instance in the destination vSwitch to view the IP address range of a CIDR block.How do I subscribe to event notifications for the results of a VPC change operation?
Subscribe to ECS system events through CloudMonitor. After you subscribe to ECS system event notifications, you can receive vSwitch event notifications.
Subscribe to ECS events through EventBridge.
Error:
InvalidDependence.GrantAccess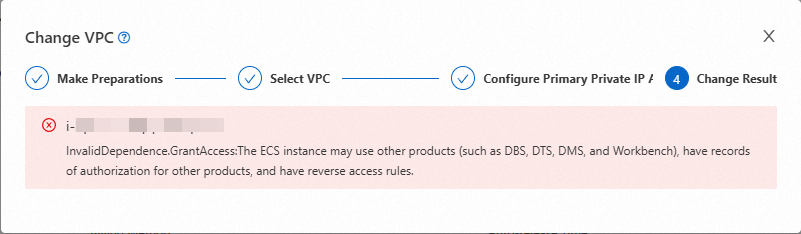
Cause: When you change the VPC, the instance cannot be used by other cloud services. The error indicates that the ECS instance may be associated with another product.
Solution: Release the reverse authorization link. Delete the authorization for other products and try again.
If a private link is generated for the instance through a private remote connection in Workbench, perform the following steps to release the authorization link:
Log on to the Workbench console. On the Private Links page, check whether a reverse authorization link exists for the ECS instance. If a link exists, click Release Link in the Actions column.
In the dialog box that appears, click OK to release the link. Then, try to change the VPC again.
Error:
InvalidDependence.NextHopOfCustomRouter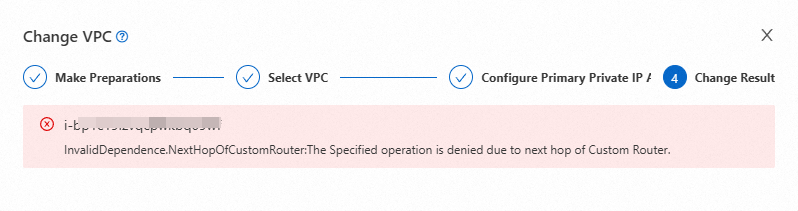
Cause: The ECS instance serves as the next hop in a route entry of a custom route table. This error occurs even if the route table is not associated with the vSwitch where the instance resides.
Solution: Delete the route entry that contains the instance. Perform the following steps:
Log on to the Route Table console. In the top navigation bar, select the region of the instance's original VPC.
On the Route Tables page, find the route table that contains the custom route entry pointing to the instance. Delete the route entry and then retry the VPC change.
Error:
InvalidDependence.SLB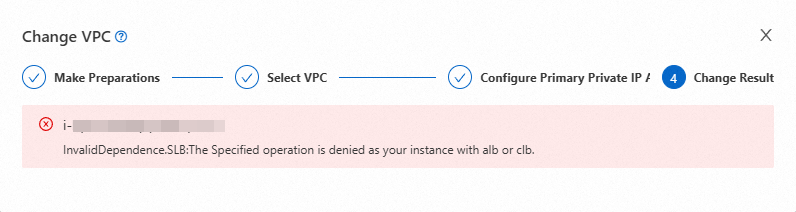
Cause: The ECS instance is a member of a SLB server group.
Solution: Remove the instance from the SLB server group. For more information, see Remove a backend server.
Error:
EnterpriseGroupLimited.MutliGroupType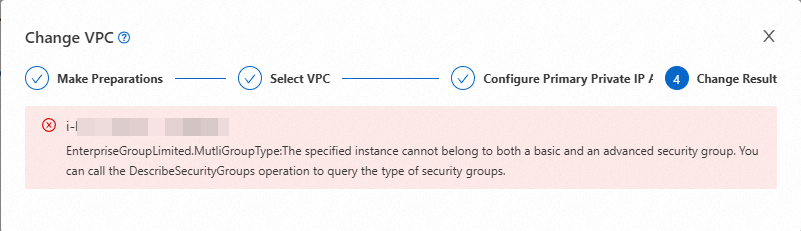
Cause: When you select multiple security groups (one to five) in the destination VPC, their types are inconsistent. You must select either all basic security groups or all advanced security groups.
Solution: Select security groups of the same type.
Error:
Invalidinstance.AttachedEni
Cause: The ECS instance has one or more secondary ENIs attached.
Solution: Detach all secondary ENIs from the ECS instance.
Error:
PrimaryEniHasSubIp
Cause: The primary ENI of the ECS instance has one or more secondary private IP addresses.
Solution: Unassign secondary private IP addresses from the primary ENI.
References
To interconnect VPCs for ECS instances across different accounts, you can use a VPC peering connection or Cloud Enterprise Network (CEN).
To migrate an ECS instance to another zone in the same region, see Cross-zone migration.
To migrate an ECS instance from one account or region to another for reasons such as insufficient resources, cost optimization, disaster recovery, or disk scaling, see Migrate data between ECS instances that belong to the same Alibaba Cloud account or different Alibaba Cloud accounts.