This topic provides answers to some frequently asked questions about logs in Cloud Firewall.
Can I export traffic logs of Cloud Firewall to a third-party system?
Why are traffic logs of ICMP detection periodically sent by Cloud Firewall?
Why do traffic logs record traffic whose application type is Unknown?
Is log analysis data retained after I release Cloud Firewall?
How do I view the total number of attacks intercepted by Cloud Firewall in logs?
How do I reduce the storage occupied by logs?
You can reduce the storage occupied by logs by using one of the following methods: reduce the log storage period, reduce the types of logs for delivery, regularly deliver logs to an Object Storage Service (OSS) bucket, or delete logs.
Reduce the log storage period
After you enable the log analysis feature, logs are stored for 180 days by default. If you do not want to retain historical logs for a long period of time, you can modify the log storage period. For more information, see Change the log storage duration.
Reduce the types of logs for delivery
By default, the log delivery switches for all types of logs are turned on. If you want to deliver only specific types of logs, we recommend that you turn on the log delivery switches for only the specified types of logs. For more information, see Configure collected log types.
Regularly deliver logs to an OSS bucket
If you want to retain a large number of logs, we recommend that you deliver logs to an OSS bucket for storage. For more information, see Create an OSS data shipping job (new version).
Delete logs
If you do not need to retain a large number of logs that are generated in the test phase, we recommend that you delete the stored logs. For more information, see Manage log storage capacity.
Can I export traffic logs of Cloud Firewall to a third-party system?
Yes, you can use the log analysis feature of Cloud Firewall to export traffic logs and import the logs to a third-party system, such as your O&M center.
You can select a method to export logs based on your business requirements.
Export a small amount of log data
You can use the log analysis feature of Cloud Firewall to download logs to your computer and upload the log file to a third-party system. For more information about how to download logs, see Export logs.
Export a large amount of log data
You can use a programming method or the Simple Log Service console to export log data to a third-party system. For more information, see Use consumer groups to consume logs.
How do I view the remaining log storage of Cloud Firewall?
If you did not enable the log analysis feature of Cloud Firewall, you cannot view the log storage capacity. If you enabled the log analysis feature of Cloud Firewall, you can view the log storage usage and the remaining log storage in the Cloud Firewall console. For more information, see Manage log storage capacity.
Why are traffic logs of ICMP detection periodically sent by Cloud Firewall?
To ensure the quality of service, Cloud Firewall periodically sends Internet Control Message Protocol (ICMP) packets for network error detection. The detection is not a scanning attack and does not affect services.
You can log on to the Cloud Firewall console and click Source address for SLA monitoring on the Cloud Service Address Book tab to view the source IP addresses of ICMP packets. For more information, see Manage address books.
Why do traffic logs record traffic whose application type is Unknown?
If Cloud Firewall cannot identify the application type of traffic, the application type of the traffic is recorded as Unknown. The following list describes the possible causes:
The total number of inbound and outbound packets recorded in the traffic logs is less than 3, and no sessions are established. In this case, the traffic may be scan traffic.
Traffic is blocked by a Layer 4 access control policy. In this case, no sessions are established.
TCP reset traffic is interrupted by the intrusion prevention feature or due to other reasons. In this case, traffic characteristics are not matched.
Traffic is encrypted, or the application is a non-standard application, an internal application, or an application that is not supported by deep packet inspection (DPI).
If Cloud Firewall cannot identify the application or domain name of the traffic, Cloud Firewall allows the traffic by default to avoid impacts on your workloads. If you do not want to allow the traffic, you can enable the strict mode for the corresponding firewall. For more information, see Configure the access control engine mode or Configure the access control engine mode for NAT firewalls.
Is log analysis data retained after I release Cloud Firewall?
Log analysis data is not retained after you release Cloud Firewall that uses the subscription billing method, but it is retained after you release Cloud Firewall that uses the pay-as-you-go billing method.
After you release Cloud Firewall, your configuration data is retained for 15 days. The configuration data includes access control policies, attack prevention policies, and traffic analysis policies. If you want to retain log analysis data of Cloud Firewall that uses the subscription billing method, export the logs to your computer or deliver the logs to a third-party system before you release Cloud Firewall. For more information, see Export logs.
Can I directly export log audit records?
No, you cannot directly export log audit records. You can specify a query statement on the Log Analysis page to query and export raw logs.
For example, if you want to export the logs of the inbound traffic of the Internet firewall in the previous 24 hours and the application type of the traffic is HTTPS, you can perform the following steps:
Log on to the Cloud Firewall console.
In the left-side navigation pane, choose .
On the Log Analysis tab, enter a query statement in the search box and select 1 Day for Select Time Range. For more information, see Query and analyze logs.
Query statement:
log_type:internet_log and direction:"in" and app_name:"HTTPS"Export the query result. For more information, see Export logs.
How do I view the total number of attacks intercepted by Cloud Firewall in logs?
You can enter the rule_result:drop query statement and select a value for Time Range. Log Quantity in the query result indicates the total number of attacks intercepted by Cloud Firewall. For more information, see Query and analyze logs.
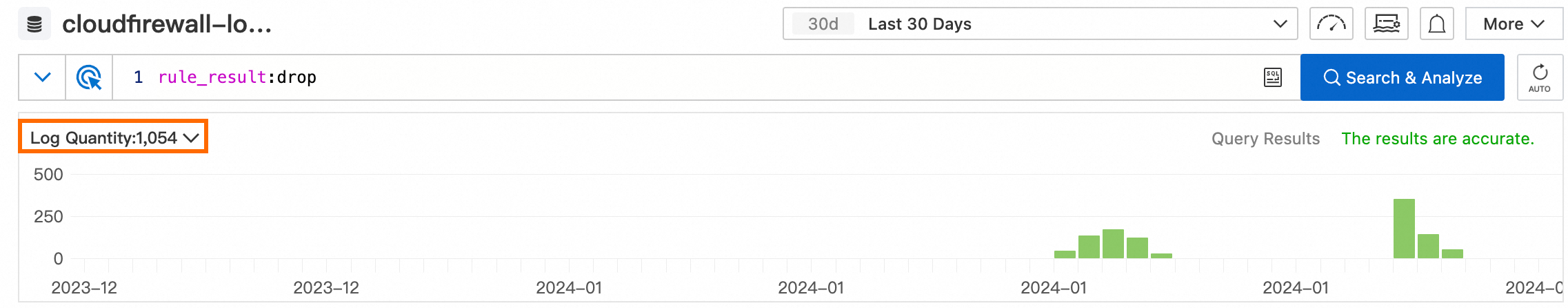
The total number of intercepted attacks in the query result may be different from the value of the Total Attacks Blocked parameter on the Overview page due to reasons such as the query time. The value of the Total Attacks Blocked parameter on the Overview page shall prevail.
Why is the total number of Cloud Firewall logs different from the total number of Anti-DDoS Proxy logs or WAF logs?
Cloud Firewall logs record inbound and outbound traffic at Layer 4. Logs of Anti-DDoS Proxy and Web Application Firewall (WAF) record HTTP requests at Layer 7.
Traffic logs at Layer 4 contain individual TCP or UDP connections and individual data packets. Traffic logs at Layer 7 contain complete HTTP requests and responses. An HTTP request or response may be transmitted over multiple TCP packets due to factors such as network conditions. Therefore, multiple logs may be generated for an HTTP request or response at Layer 4, but only one log is generated for an HTTP request or response at Layer 7.
In addition, logs generated for Layer 4 traffic are more complex and diversified than logs generated for Layer 7 traffic due to retransmission, network latency, fragmentation, and the features of application layer protocols, such as HTTP keepalive. You must consider the differences when you compare and analyze traffic logs at different layers.
Therefore, the total number of Cloud Firewall logs may be different from the total number of Anti-DDoS Proxy logs or WAF logs.
Why are traffic logs of specific persistent connections lost after the O&M upgrade of the Cloud Firewall engine?
The O&M upgrade of the Cloud Firewall engine does not affect your business. However, in specific O&M scenarios, such as engine upgrade and scaling, traffic logs of specific persistent connections are no longer reported and are lost.
You can perform the following operations to filter traffic logs that may be lost: Enable the log analysis feature. Go to the Log Analysis page, set the Select Time Range parameter to 1 Minute, and then enter new_conn=0 in the search box to filter the traffic logs of existing connections. After the connections are re-established, the system continues to record traffic logs.
For more information, see Enable the log analysis feature.
How do I query the events of operations that Cloud Firewall performs on other services by assuming a service-linked role?
Log on to the ActionTrail console.
In the left-side navigation pane, choose .
In the top navigation bar, select the region of the event that you want to query.
On the Event Query page, select Operator from the drop-down list, enter aliyunserviceroleforcloudfw in the search box, specify a time range, and then click the
 icon.
icon.Find the event that you want to query and click View Details in the Actions column to view the event details and event code. For more information, see Query events in the ActionTrail console.