Sensitive data may be leaked when your cloud assets initiate outbound connections. In this case, you can use the sensitive data leak detection feature of Cloud Firewall to identify and record the leaked sensitive data and the related payloads at the earliest opportunity. This helps prevent business losses. This topic describes how to use the sensitive data leak detection feature.
Supported editions and specifications
The feature does not compromise the protection of business traffic in Cloud Firewall.
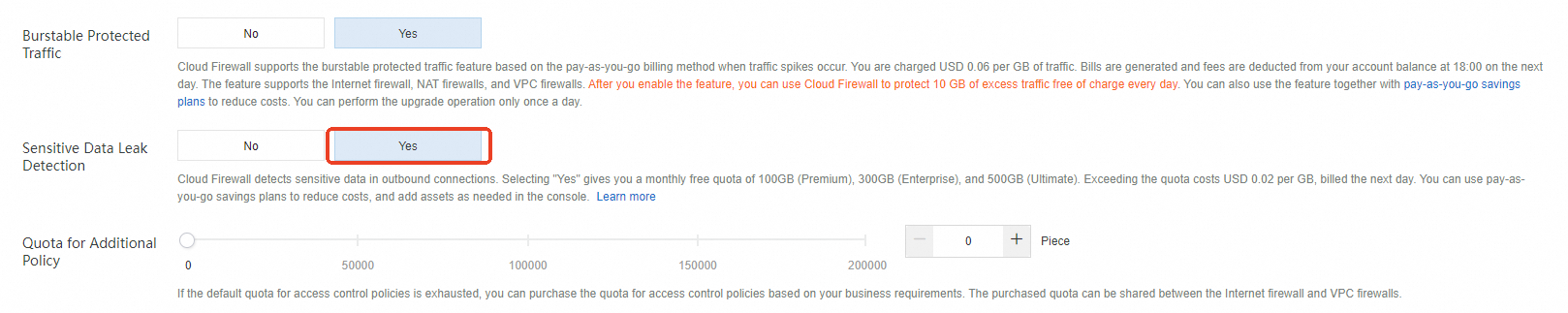
Cloud Firewall provides the sensitive data leak detection feature for outbound connections. After you select Yes for Sensitive Data Leak Detection on the buy page, you can obtain the following free quotas: 100 GB for Premium Edition, 300 GB for Enterprise Edition, 500 GB for Ultimate Edition, and 100 GB for Cloud Firewall that uses the pay-as-you-go billing method. If the free quotas are exhausted, you are charged USD 0.02 per GB based on the pay-as-you-go billing method for the excess traffic, and bills are generated on the next day. You can also use this feature together with pay-as-you-go savings plans to reduce costs. For more information, see Pay-as-you-go savings plan. You can enable the feature for your assets in the Cloud Firewall console.
For more information, see the "Enable the sensitive data leak detection feature" section in this topic.
Billing method | Edition | Free quota per month | Billing of excess traffic (pay-as-you-go) | Pay-as-you-go savings plan |
Subscription | Premium Edition | 100 GB | USD 0.02 per GB |
|
Enterprise Edition | 300 GB | |||
Ultimate Edition | 500 GB | |||
Pay-as-you-go | Cloud Firewall that uses the pay-as-you-go billing method | 100 GB | USD 0.02 per GB |
Supported sensitive data types
Cloud Firewall can detect the following types of sensitive data that may be leaked in the outbound connections of public IP addresses in Alibaba Cloud:
AccessKey ID
Passport number (Chinese mainland)
Debit card number
ID card number (Hong Kong, China)
Number of Exit-Entry Permit for Travelling to and from Hong Kong and Macao
ID card number (Chinese mainland)
Military ID number
Private key
To view the supported sensitive data types, you can perform the following operations: Go to the IPS Configuration page in the Cloud Firewall console, find the Data Leak Detection section, and then click View Supported Sensitive Data Types. For more information, see IPS configuration. You can enable or disable the sensitive data leak detection feature for a data type based on your business requirements. If Cloud Firewall detects sensitive data in the outbound connections of an asset, Cloud Firewall does not block the traffic of the asset. You can configure access control policies to block traffic.
Prerequisites
The Internet firewall is enabled. For more information, see Enable the Internet firewall.
Enable the sensitive data leak detection feature
Subscription
New users (users who did not purchase Cloud Firewall)
You can select Yes for Sensitive Data Leak Detection in the Cloud Firewall console or on the buy page to enable the feature.

Existing users (users who purchased Cloud Firewall but did not enable the feature)
You can enable the feature on the following pages:
Upgrade page
Select Yes for Sensitive Data Leak Detection
Feature page
Select Yes for Sensitive Data Leak Detection
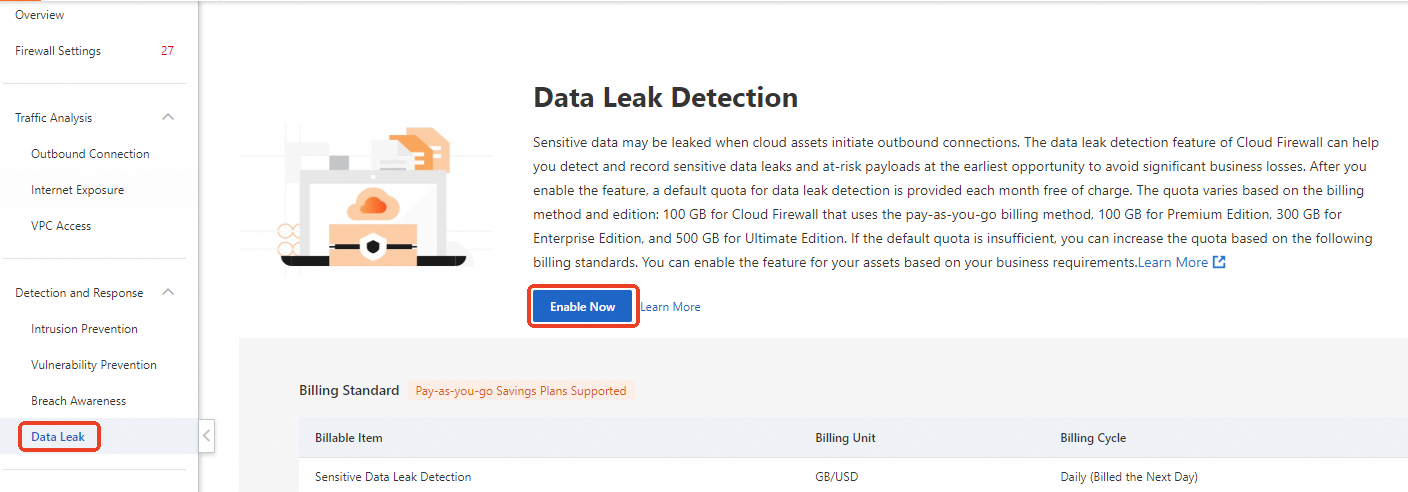

Pay-as-you-go
To enable the feature in Cloud Firewall that uses the pay-as-you-go billing method, go to the Data Leak Detection page and click .
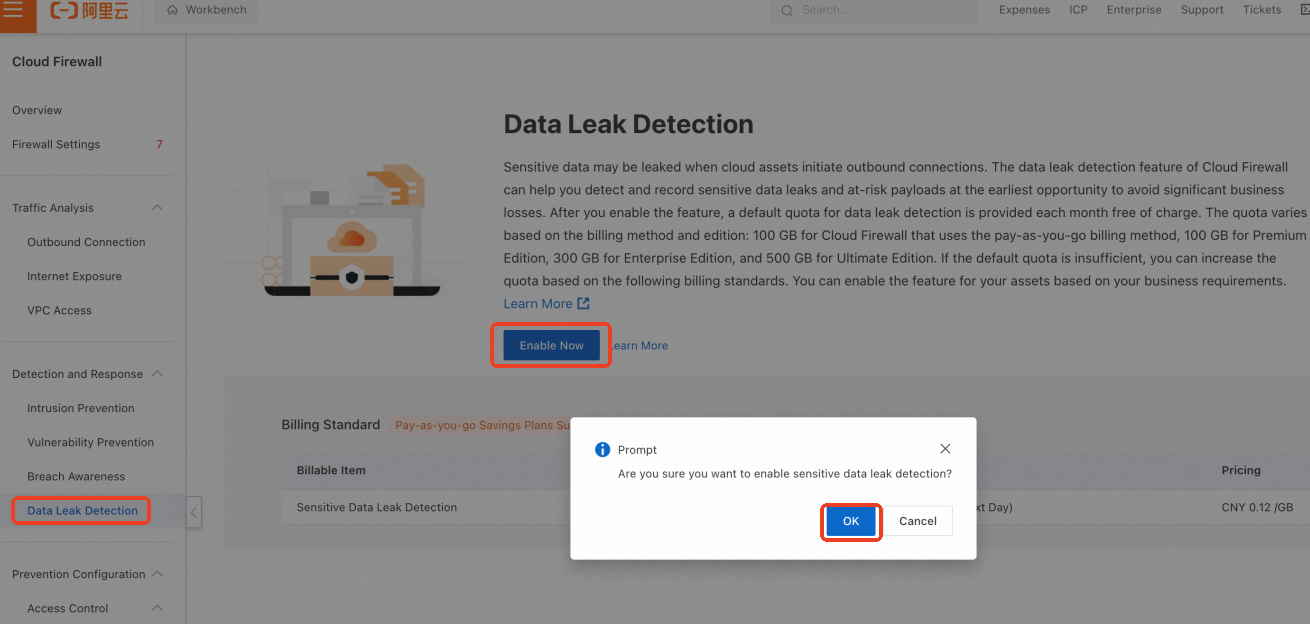
Enable sensitive data leak detection for cloud assets
To allow Cloud Firewall to detect sensitive data in outbound connections of your cloud assets and identify the related risks, you must enable the sensitive data leak detection feature for the assets. An outbound connection refers to the connection from your assets to the Internet.
Sensitive data leak detection is available for connections over protocols such as HTTP that are used to transmit data in plaintext. Protocols such as HTTPS that are used to transmit encrypted data are not supported.
Log on to the Cloud Firewall console. In the left-side navigation pane, choose .
In the upper-right corner of the Data Leak Detection page, click Asset Configuration.
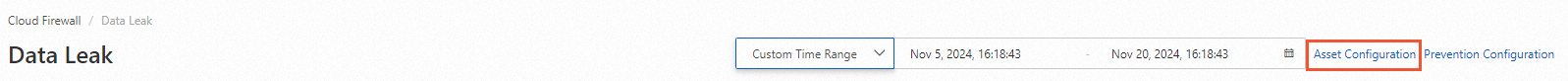
In the Asset Configuration panel, find the public IP address that you want to manage and click Enable Data Leak Detection in the Operation column.
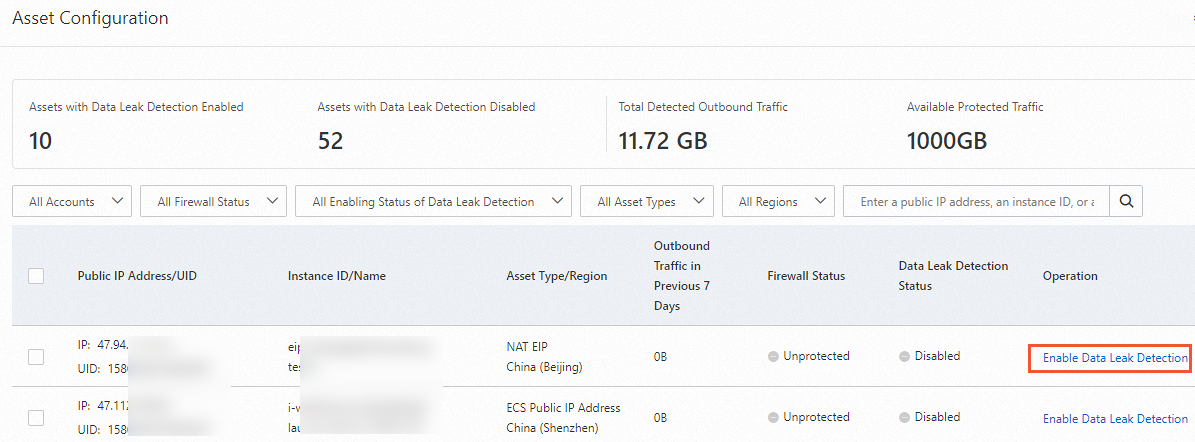
In the Asset Configuration panel, click Daily Limit on Detected Traffic in the upper-right corner. In the dialog box that appears, specify the maximum amount of traffic that can be processed each day.
NoteYou must specify a value that is within the supported range and is no less than the amount of traffic processed on the current day.
You can also refer to the amout of traffic in your outbound connections. You can view the amount of traffic in the previous seven days in the Asset Configuration panel.
View or configure sensitive data types
Entry points of the IPS Configuration page
You can use one of the following methods to go to the View Sensitive Data Types page:
Data Leak

Data Leak
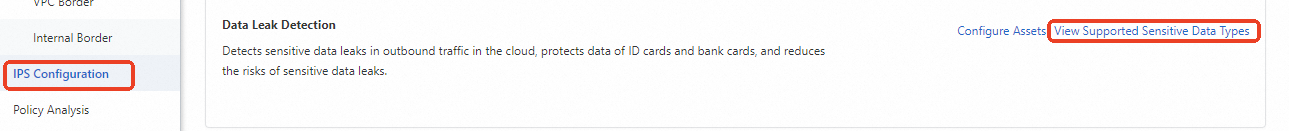
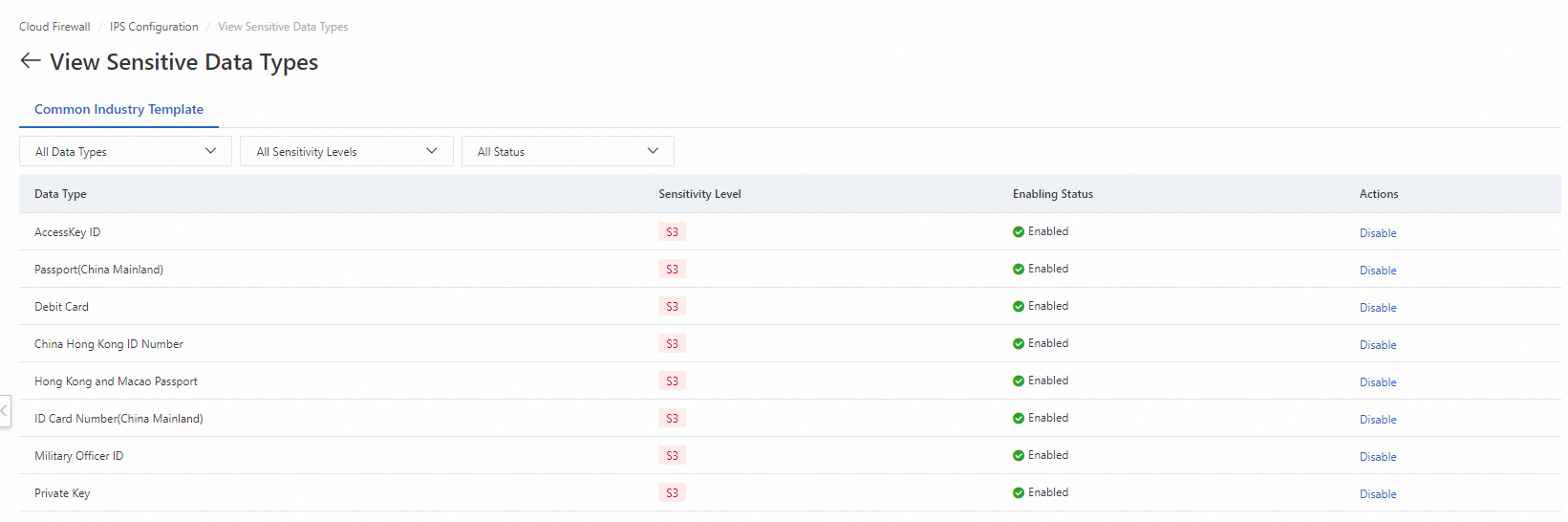
View or disable data types
On the View Sensitive Data Types page, you can view information such as Data Type and Enabling Status.
If you no longer want to detect a specific type of data, find the data type and click Disable in the Actions column.
View statistics on sensitive data in outbound connections
In the Sensitive Data of Outbound Traffic section, you can view sensitive data statistics within the time range that you specify. The statistics provides you with an overview of the sensitive data leaks of your assets.
In the Distribution of Leaked Sensitive Data by Type section, you can view the distribution of leaked sensitive data within the time range that you specify. This helps you audit the behavior of your assets and protect your business from losses.

View the details of a sensitive data leak event
You can specify a time range to query sensitive data leak events. In the lower part of the Data Leak Detection page, you can find the sensitive data leak event that you want to manage and click View Details in the Operation column. In the Data Leak Details panel, view the related details, including Leaked Information, Risk Payload, Sensitive Data, and Events. In the panel, you can also view the intelligence profile of the destination IP address or domain name to evaluate the security of the destination to which the sensitive data is sent.
Cloud Firewall provides suggestions on how to handle a sensitive data leak event. For example, you can configure access control policies based on the event details to avoid sensitive data leaks. You can handle the event based on your business requirements to minimize the risk of sensitive data leaks.
View bills
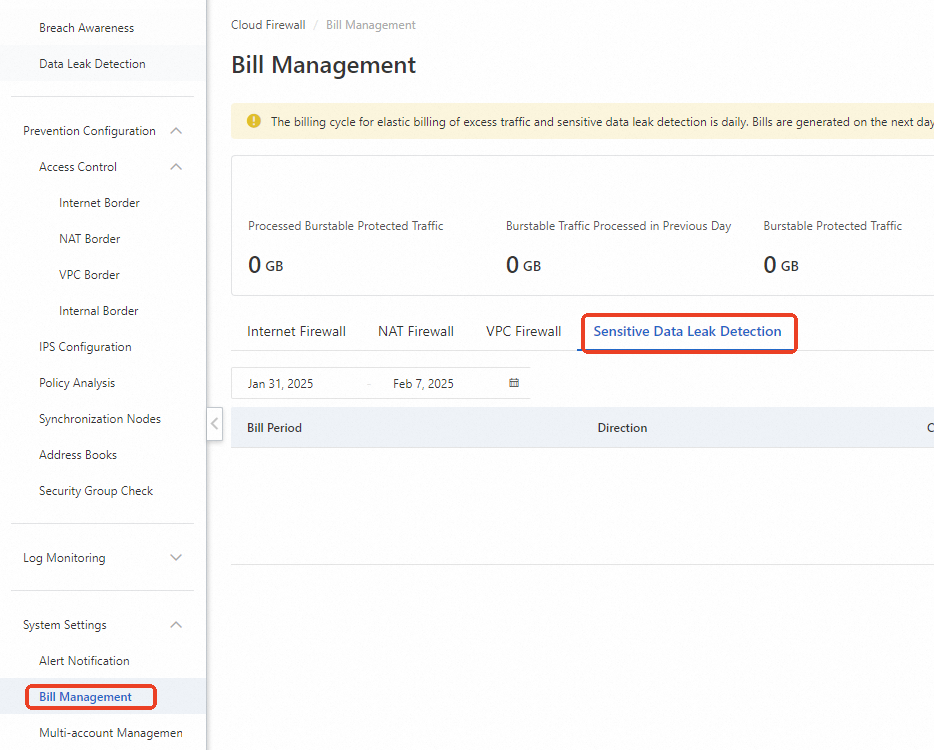
Entry points of the Bill Management page
You can use one of the following methods to go to the Bill Management page to view the traffic consumed by sensitive data leak detection:
In the upper-right corner of the Data Leak Detection page, click Bill Management to go to the Bill Management page.

In the left-side navigation pane, click Bill Management. On the Bill Management page, click the Sensitive Data Leak Detection tab.
View traffic and bills
On the Sensitive Data Leak Detection tab of the Bill Management page, you can view the billed traffic.
The billing cycle of sensitive data leak detection is one day. Data of Day T is displayed on the Bill Management page on Day T+1. The bill for the previous day is generated and settled at approximately 18:00 every day. If you disable sensitive data leak detection, the bill for the current day is generated after 18:00 on the next day.
In the upper-right corner of the list, you can click View Offset Details or View Bill Details to go to the Expenses and Costs console to view the offset details of pay-as-you-go savings plans or the generated bills.
