Use the Internet firewall for fine-grained control over traffic between your public assets and the Internet. This reduces the Internet exposure of your public assets and lowers security risks for your service traffic. When you enable the Internet firewall, you do not need to change your current network topology. You can protect your resources with one-click protection that takes only seconds to apply. This lets you quickly implement features such as visual analytics, attack prevention, access control, and log auditing for inbound and outbound Internet traffic.
Features
How it works
After you enable the Internet firewall for your public assets, Cloud Firewall filters outbound and inbound traffic using technologies such as deep packet inspection (DPI) traffic analysis, intrusion prevention system (IPS) rules, threat intelligence, virtual patching, and access control policies. This process determines whether to allow the traffic, effectively blocks malicious access, and ensures the security of traffic between your public assets and the Internet.
Protected public assets (outbound and inbound): Assets such as ECS, EIP (including L2 EIP), load balancing, Bastionhost, NAT Gateway, HaVip, and GA EIP, which support both IPv4 and IPv6.
The following figure shows an example of a protection scenario for the Internet firewall.

Impact on services
Creating, enabling, or disabling the Internet firewall does not require changes to your network topology. You can enable or disable protection for resources with one click in seconds, which does not impact your services. We recommend that you enable the Internet firewall during off-peak hours.
Protection specifications
Starting from October 15, 2025, Cloud Firewall will release Billing Method 2.0. New users use Billing Method 2.0 by default. Existing users continue to use Billing Method 1.0. The protection specifications for the Internet firewall differ between the two billing methods.
Billing Method 2.0
Protection specification | Description | Cloud Firewall Subscription (Premium, Enterprise, and Ultimate Editions) | Cloud Firewall Pay-As-You-Go |
Number of firewall instances | The number of protectable regions. Each protected region corresponds to one Internet firewall instance. | Depends on the number of purchased instances and bandwidth. For information about the number of instances and bandwidth provided by different editions, see Subscription 2.0. If the quota is insufficient, you can upgrade the specifications. For more information, see View the protection status of assets. | You are charged based on the actual number of firewall instances and the total traffic processed. The maximum supported peak bandwidth is 10 Gbps. To request a higher specification, contact your account manager or architect. For more information about billing, see Pay-as-you-go 2.0. |
Protected Internet Traffic | The peak of the total Internet traffic processed by the firewall. The billing is based on the sum of inbound and outbound Internet traffic bandwidth. |
Billing Method 1.0
Protection specification | Description | Cloud Firewall Subscription (Premium, Enterprise, and Ultimate Editions) | Cloud Firewall Pay-As-You-Go |
Number of protectable public IP addresses | The number of public IP addresses for which the Internet firewall can be enabled. | Depends on the number of protectable public IP addresses you purchased and the peak of the total traffic that can be processed. If the quota is insufficient, you can upgrade the specifications. Different Cloud Firewall editions have different public IP address quota limits. For more information, see Subscription 1.0. Note If your service traffic exceeds the purchased processing capacity of Cloud Firewall, the Service-Level Agreement (SLA) is not guaranteed. This may trigger downgrade rules, such as disabling security features (access control list (ACL), IPS, log auditing), shutting down the firewall for assets with excessive traffic, or rate limiting and packet loss. If your service traffic is at risk of exceeding the limit, see Pay-as-You-Go for Elastic Traffic on Subscription. | You are charged based on the actual number of protected public IP addresses and the peak of the total traffic processed. There is no quota limit. For more information about billing, see Pay-as-you-go 1.0. |
Protected Internet Traffic | The peak of the total Internet traffic processed. The billing is based on the higher value between the inbound and outbound Internet traffic bandwidth. |
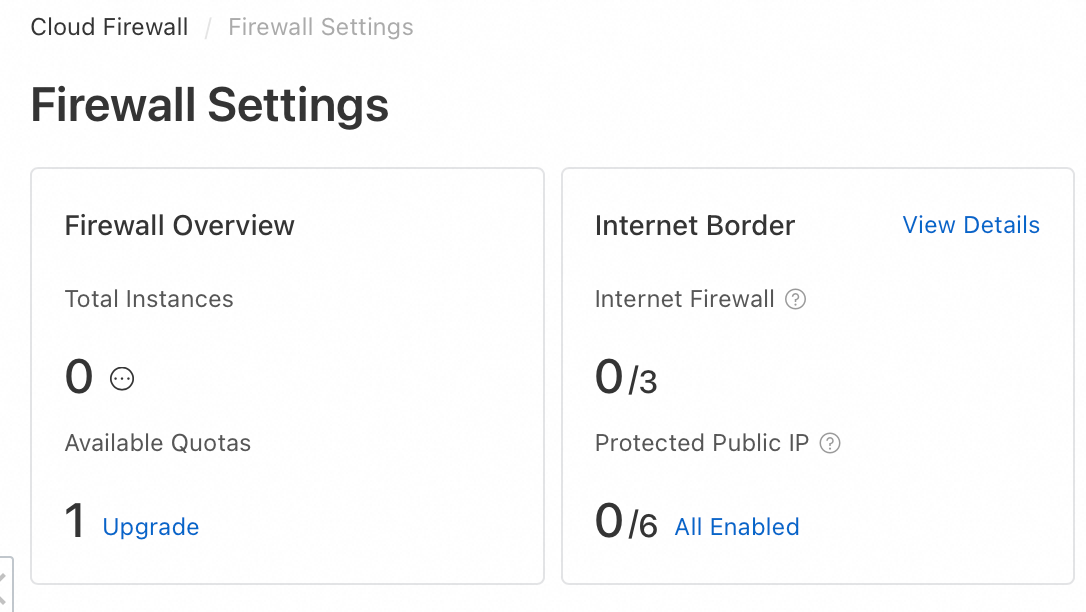
View the protection status of assets
Enable the firewall
Manually enable protection for assets
If you have not enabled the Automatic Protection for New Assets feature, you can manually enable Internet Border protection for public assets.
Log on to the Cloud Firewall console.
In the navigation pane on the left, click Firewall Settings.
On the Internet Firewall tab, click the IPv4 or IPv6 tab to manually enable protection for public assets.
If the asset that you want to protect is not in the public asset list, click Synchronize Assets in the upper-right corner of the list. This synchronizes the asset information from your Alibaba Cloud account and its member accounts. The synchronization process takes 1 to 2 minutes.
Enable protection for a single asset: In the public asset list, find the public asset that you want to protect. In the Actions column, click Enable Protection.
Enable protection for multiple assets in a batch: In the public asset list, select the public assets that you want to protect. Below the list, click Enable Protection.
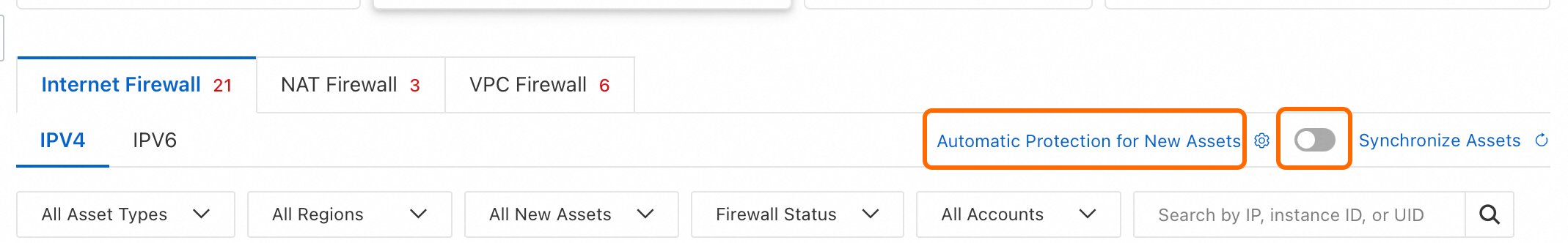
Enable automatic protection for new assets
After you enable Automatic Protection for New Assets, if new public assets are added to the current Alibaba Cloud account or its member accounts, Cloud Firewall automatically enables Internet Border protection for the new assets.
Log on to the Cloud Firewall console.
In the navigation pane on the left, click Firewall Settings.
Enable the Automatic Protection for New Assets feature: On the Internet Firewall tab, turn on the switch next to Automatic Protection for New Assets.
Select the types of new assets to automatically protect: Click Automatic Protection for New Assets. In the configuration panel that appears, select the new assets to protect based on asset type and region. After you complete the configuration, click Save.
What to do next
After you create an Internet firewall, you can configure access control policies and view access logs for public assets to better manage traffic between your public assets and the Internet.
Configure access control policies
If you do not configure any access control policies, Cloud Firewall allows all traffic by default. You can create Internet firewall access control policies for fine-grained control over traffic between your public assets and the Internet.
On the page, find the target Internet firewall. In the Actions column, click Configure Policy and select whether to configure an outbound or inbound access control policy for the public asset. For more information, see Configure access control policies for the Internet firewall.
Query audit logs
On the tab of the page, you can set filter conditions to view access logs for traffic between public assets and the Internet. For more information, see Log auditing.
View traffic analysis
On the page, you can view traffic data for assets that actively access the Internet. This includes data for outbound unusual traffic tracing, Internet destinations accessed by assets, outbound connections from public assets, and outbound connections from private network assets. This helps you identify suspicious assets and secure your services. For more information, see Outbound connections.
On the page, you can view data about Internet access to your service assets. This includes data for inbound unusual traffic tracing, open public IP addresses, open ports, open applications, and the number of public IP addresses for cloud products. This helps you identify suspicious assets and secure your services. For more information, see Internet Exposure.
View attack prevention data
On the page, find the target Internet firewall. In the Actions column, click View Attacks and select to view outbound or inbound attack prevention data for the public asset. For more information, see Intrusion prevention.
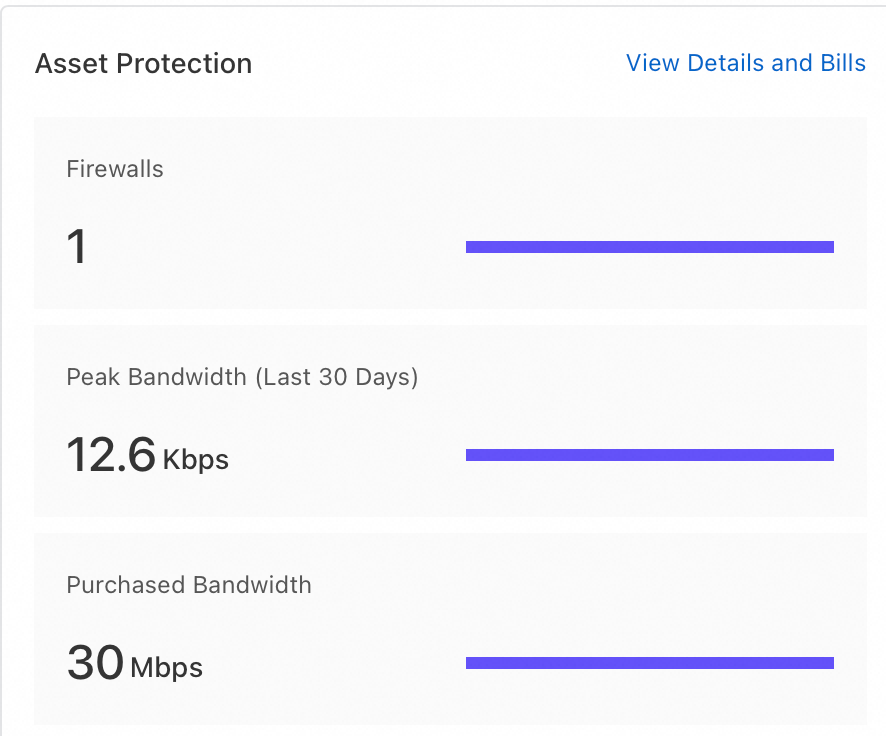
View Internet traffic processing status
In the navigation pane on the left, click Overview. Then, in the Asset Protection section of the Overview page, you can view the number of firewall instances, purchased traffic, and recent peak bandwidth.