If a server is compromised, the Breach Detection feature of Cloud Firewall helps you quickly detect and identify intrusion events to prevent major business losses. This topic describes how to check for security threats on a server and configure the prevention mode.
Prerequisites
The Internet firewall is enabled. For more information, see Enable the firewall switch.
Block Mode is enabled for the threat engine. For more information, see IPS Configuration.
Procedure
Log on to the Cloud Firewall console.
In the navigation pane on the left, choose .
On the Breach Detection page, view the details of intrusion events.
On the Breach Detection page, you can perform the following operations as needed.
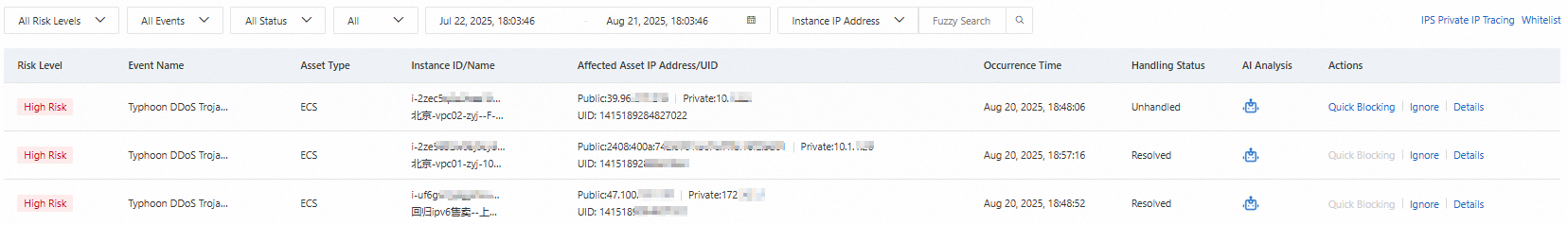
View the event list
In the intrusion event list, you can view the details of intrusion events, including the risk level, the IP address and UID of the affected asset, and the processing status.
Find a specific event
In the menu bar, you can filter events by risk level, time type, processing status, or detection time range. You can also perform a fuzzy search by entering an instance IP address, ID, name, or UID to find a specific intrusion event.
Enable Block Mode for the threat engine
After you enable the Internet firewall, Block Mode is enabled for the threat engine by default. If you disable Block Mode, the Breach Detection page can detect risk events but cannot block them. In the Actions column, click Quick Blocking to enable Block Mode for the threat engine in the Mitigation Settings.
ImportantThe Quick Blocking switch does not control individual events. Enabling or disabling Quick Blocking enables or disables the intrusion prevention feature for the entire Cloud Firewall.
Ignore an intrusion event
If you determine that an intrusion event is normal activity, find the event that you want to ignore and click Ignore in the Actions column.
NoteAn event that is marked as Ignored is removed from the intrusion event list. Cloud Firewall no longer generates alerts for this event.
View event details
Find the event whose details you want to view and click Details in the Actions column to view detailed information about the intrusion event and the corresponding security recommendations.
AI-assisted event analysis: Click the
 icon in the AI Analysis column to quickly analyze breach alerts with the Security AI Assistant.
icon in the AI Analysis column to quickly analyze breach alerts with the Security AI Assistant.The analysis includes:
Payload content analysis: Includes a brief description of the selected alert and the results of the AI analysis.
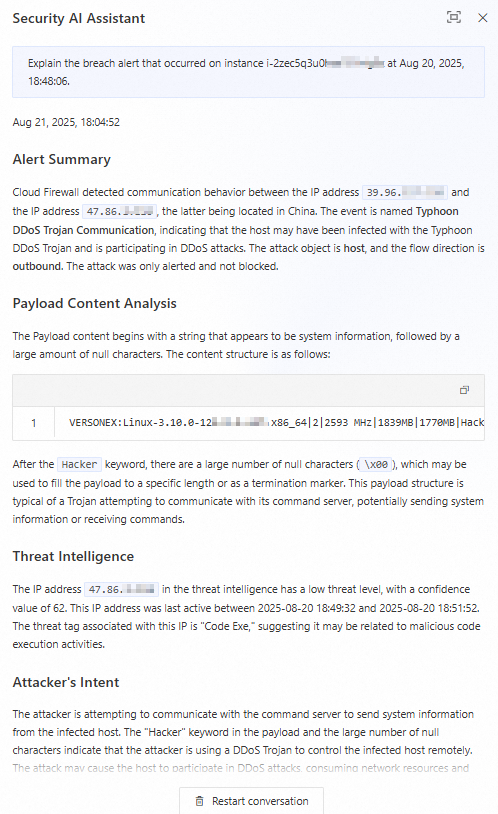
Attacker intent: The predicted intent of the attacker based on AI analysis.
Defense recommendations: Provides suggestions for Cloud Firewall mitigation settings, such as Access Control List (ACL) policies and IPS configurations, and asset investigation.
References
The Mitigation Settings feature lets you set the running mode of the threat engine and configure settings for threat intelligence, basic protection, intelligent defense, and virtual patches. These settings help you more accurately identify and block intrusion threats. For more information, see IPS Configuration.
The intrusion prevention system (IPS) feature can detect and block malicious traffic in real time, such as malicious attacks, vulnerability exploits, brute-force attacks, worms, mining programs, backdoor trojans, and DoS attacks. This feature protects your cloud-based enterprise information systems and network architecture. For more information, see Overview of the IPS feature and IPS.
Cloud Firewall can sync vulnerabilities that are detected by Security Center and exploited by network attacks. It also provides defense against such vulnerabilities. For more information, see Vulnerability Prevention.