This topic describes the issues that may occur when you use access control policies of Cloud Firewall to control business traffic. This topic also provides solutions to the issues.
FAQ about features
FAQ about operations
If I enable both WAF in transparent proxy mode and the Internet firewall, can traffic over forwarding ports be controlled by access control policies of Cloud Firewall?
If you enable both Web Application Firewall (WAF) in transparent proxy mode and the Internet firewall, you can use the access control policies that are created for the Internet firewall to control the traffic over forwarding ports. However, you cannot perform log audit, log analysis, or traffic statistic collection on the traffic over the forwarding ports. Traffic over other ports is not affected.
Can I increase the default quota for access control policies?
If you use Cloud Firewall that uses the subscription billing method (Premium Edition, Enterprise Edition, and Ultimate Edition), and the quota for access control policies of the Internet firewall, NAT firewalls, or virtual private clouds (VPC) firewalls cannot meet your business requirements, you can configure the Quota for Additional Policy parameter on the Cloud Firewall purchase page to increase the quota. For more information, see Subscription 2.0.
If you use Cloud Firewall that uses the pay-as-you-go billing method, you cannot increase the quota for access control policies. For more information, see Pay-as-you-go.
Can I increase the protected VPC traffic bandwidth?
Yes, if the purchased VPC traffic processing capability cannot meet your business requirements, you can configure the Protected VPC Traffic parameter to increase the peak cross-VPC traffic that can be protected.
Enterprise Edition: The basic price includes 200 Mbit/s of protected traffic. You can increase the quota to a value from 200 to 5,000 Mbit/s.
Ultimate Edition: The basic price includes 1,000 Mbit/s of protected traffic. You can increase the quota to a value from 1,000 to 10,000 Mbit/s.
Can Cloud Firewall block traffic of IPv6 CIDR blocks?
Yes, Cloud Firewall can control the traffic of IPv6 CIDR blocks after you create access control policies for the Internet firewall. The policies are supported in all editions of Cloud Firewall. For more information, see Create access control policies for the Internet firewall.
What are the differences between Cloud Firewall and security groups?
A security group is a virtual host firewall provided by Elastic Compute Service (ECS) to control the traffic between ECS instances.
Cloud Firewall provides the Internet firewall to control the traffic at the Internet boundary, NAT firewalls to control the traffic at the NAT boundary, VPC firewalls to control the traffic at the VPC boundary, and internal firewalls to control the traffic between ECS instances.
Compared with security groups, Cloud Firewall provides the following unique features:
Application-based access control. You can control traffic by protocol such as HTTP without the need to specify ports.
Domain name-based access control. For example, you can allow ECS instances to send requests only to a specific domain name.
Intrusion prevention. Cloud Firewall provides preemptive measures against common system vulnerabilities and brute-force attacks.
The monitor mode of access control policies. Cloud Firewall monitors traffic but does not block potential malicious traffic.
Complete traffic logs and real-time traffic analysis.
Centralized platform security management. The access control policies that are created for internal firewalls in the Cloud Firewall console are automatically synchronized to ECS security groups. This simplifies security management.
What are the priorities of access control policies and security group rules that are used to match traffic?
In the network security architecture of Alibaba Cloud, inbound traffic is first matched against access control policies of Cloud Firewall and then security group rules, and outbound traffic is first matched against security group rules and then access control policies.
Access control policies and security group rules are independent protection mechanisms. Traffic is allowed only if it is allowed by both access control policies and security group rules.
If traffic is allowed by an access control policy but denied by a security group rule, the traffic is denied. If traffic is denied by an access control policy but allowed by a security group rule, the traffic is still denied.
What are the differences between common policy groups and enterprise policy groups?
Policy groups that are configured for an internal firewall between ECS instances correspond to the security groups of ECS instances. Policy groups are virtual firewalls that control inbound and outbound traffic between ECS instances. Policy groups are classified into common and enterprise policy groups, which are suitable for different scenarios.
A common policy group corresponds to a basic security group of ECS instances. Resources in the same basic security group can communicate with each other. A common policy group can be specified as authorization objects in the rules of other security groups. The number of private IP addresses that can be contained in a common policy group is less than that in an enterprise policy group.
An enterprise security group corresponds to an advanced security group of ECS instances. You can configure access control policies for more private IP addresses in an enterprise policy group. However, resources in the same enterprise security group cannot communicate with each other, or an enterprise policy group cannot be specified as authorization objects in the rules of other security groups.
For more information, see Basic security groups and advanced security groups.
I configured an outbound access control policy whose application type is HTTP or HTTPS for a domain name. How do I check whether the policy is valid?
You can run the curl command or enter the domain name in the address bar of a browser to check whether the policy is valid. For example, you can run the curl -k "https://www.aliyundoc.com" command, and then log on to the Cloud Firewall console to view the number of times that the policy is hit and the audit logs.
Do not run the telnet command to check whether the policy takes effect on the domain name. When you run the telnet command, such as the telnet example.com 80 command, only TCP handshake traffic is generated. Complete HTTP or HTTPS requests are not simulated. In this case, the application type of the traffic is identified as Unknown and the traffic does not hit a policy whose application type is HTTP or HTTPS.
How do I troubleshoot the error that is returned after I apply the default Allow policies to a security group?
The error is reported because the security groups associated with the IP address for which you apply the policies do not support the default Allow policies due to the following reasons:
The security groups that are associated with the IP address are advanced security groups.
Advanced security groups do not support the default Allow policies.
The Internet firewall is disabled for the IP address.
To better protect your assets, we recommend that you do not apply the default Allow policies to resources for which the firewalls provided by Cloud Firewall are disabled. We recommend that you do not disable the firewalls for resources to which you have applied the default Allow policies.
When I apply the default Allow policies, the system prompts that a configuration conflict cannot be resolved. How do I do?
Possible cause
The priorities, protocol types, port ranges, and authorization objects of the security group rules for the security groups that are associated with the IP address are the same as those of the default Allow policies to be applied.
Solution
We recommend that you go to the Security Groups page of the ECS console to view and adjust the priorities of conflicting rules. For more information, see Modify a security group rule. You can also submit a ticket to obtain technical support.
Why is the Quick Apply icon unavailable? How do I troubleshoot the error?
Possible cause
Conflicting security group rules exist.
Solution
You must resolve the conflicts between the rules in the ECS security groups associated with the IP address for which you click Apply as prompted before you can apply the default Allow policies. For more information, see Internet Firewall.
How do I eliminate false positives for suspicious outbound connections that are caused by Internet-based scans?
Possible cause
If false positives are generated for suspicious outbound connections when Internet-based port scans are performed, the inbound access control policies are weak. When an attacker scans a port that is disabled on a server, the server returns an Internet Control Message Protocol (ICMP) packet that indicates the port is inaccessible. Cloud Firewall considers the ICMP packet as an outbound connection that is initiated by the client.
Solution
To resolve this issue, we recommend that you configure an inbound access control policy to allow traffic only over the ports that are required for your workloads. For more information, see Create access control policies for the Internet firewall.
I configured an outbound Deny access control policy whose Source is set to 0.0.0.0/0 for the Internet firewall. However, some traffic is still allowed because no policy is matched. Why?
Possible causes
The domain name of the traffic is not identified.
You configured a domain name-based access control policy that has a high priority, and the source IP address, destination IP address, and application type of traffic are identified. However, the domain name of the traffic is not identified. In this case, the traffic is allowed. This ensures that the domain name of the traffic can be identified by subsequent access control policies.
The application type of traffic is not identified.
You configured an application-based access control policy that has a high priority, and the source IP address, destination IP address, and port of traffic are identified. However, the application type of traffic is not identified. In this case, the traffic is allowed. This ensures that the application type of the traffic can be identified by subsequent access control policies.
Solutions
Enable the strict mode for access control policies of the Internet firewall.
After you enable the strict mode, Cloud Firewall matches the preceding traffic against other access control policies until the application type or domain name of the traffic is identified. If a Deny policy is configured, traffic whose application type or domain name is identified as Unknown is denied. For more information, see Configure the mode of the access control engine.
Create only Layer 4 access control policies. Do not create Layer 7 access control policies.
When you create a Layer 4 access control policy, set the Application parameter to ANY. Do not specify domain names for Destination. If Cloud Firewall matches traffic to the Layer 4 access control policy, Cloud Firewall processes the traffic based on the action that is specified in the policy. For more information, see Create access control policies for the Internet firewall.
How do I configure access control policies to allow access only to a specified subdomain name of a secondary domain name?
In this example, the xyz.com domain name is used. To configure access control policies to allow access only to the abc.xyz.com domain name, perform the following operations:
Create an access control policy to block access to the
*.xyz.comdomain name and set the priority of the policy to Lowest.Create an access control policy to allow access to the
abc.xyz.comdomain name and set the priority of the policy to Highest.
Make sure that the policy that allows access to the subdomain name has a higher priority than the policy that denies access to other websites. For more information, see Create access control policies for the Internet firewall.
How do I use Cloud Firewall to strengthen access control on the domain names of a bastion host?
Bastionhost is a comprehensive O&M management platform, which provides various features such as O&M identity authentication, account management, and system operation audit. A bastion host stores and manages a large amount of sensitive information such as account information. Therefore, bastion hosts are prone to attacks. The new version of Bastionhost supports domain name-based access. In this case, unauthorized users may log on to a bastion host to access a large number of assets.
We recommend that you use Cloud Firewall to perform access control on the domain names of a bastion host. If you purchase both Bastionhost and Cloud Firewall, Bastionhost is automatically added to the asset type of Cloud Firewall, and the purchased bastion host is automatically synchronized to the asset list of Cloud Firewall. You can use Cloud Firewall to perform access control, intrusion prevention, and network traffic analysis on the bastion host to manage and protect the public IP addresses of the bastion host in a centralized manner.
Access control:
Configure inbound access control policies for the Internet firewall to allow traffic from the Internet or the Internet in specified areas to the open ports of the bastion host.
Configure outbound access control policies for the Internet firewall to allow traffic from the bastion host to public IP addresses.
Intrusion prevention: Enable a firewall for the bastion host to redirect inbound and outbound traffic of the bastion host to Cloud Firewall for protection.
For more information, see Configure access control policies in scenarios in which Cloud Firewall is deployed together with Bastionhost.
Does an access control policy take effect if the time range specified for recurrence spans two calendar days?
When you configure an access control policy, if the time range that you specify for the Recurrence Cycle parameter spans two calendar days and the start time specified for the Effective Date parameter falls within the time range, the actual end time for recurrence is rolled over to the specified end time on the next day.
For example, if you set the Recurrence Cycle parameter to Every Tuesday from 18:00 - 08:00 (+1) and set the Effective Date parameter to 2024.08.20 - 2024.08.22, the access control policy takes effect from 18:00 on August 20, 2024 to 08:00 on August 21, 2024.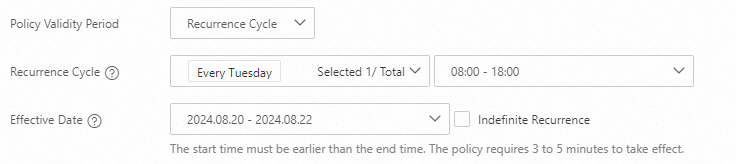
What do I do if unidirectional traffic on a VPC firewall created for an Enterprise Edition transit router of a CEN instance is blocked when I change its traffic redirection scenario?
Possible cause
You configured an access control policy that allows traffic from VPC 1 to VPC 2 and a default Deny policy. When you enable or disable a traffic redirection scenario, unidirectional routing issues occur, causing the response packets of ICMP and UDP traffic to be treated as initial traffic and redirected to Cloud Firewall. TCP traffic is not affected. In this case, the source and destination IP addresses of traffic are reversed. The traffic cannot hit the Allow policy, and then it is blocked by the Deny policy.

Solution
If short-term business jitters are unacceptable, we recommend that you configure a 0.0.0.0/0 Allow policy with the highest priority for the VPC firewall created for an Enterprise Edition transit router of a Cloud Enterprise Network (CEN) instance before you enable or disable the VPC firewall. In this case, reverse traffic is allowed when you change traffic redirection scenarios. After the VPC firewall is enabled or disabled, you can delete the policy.
