This topic describes the billable items and the relevant rules for overdue payments, expiration, and refunds of Anti-DDoS Origin 2.0 (Subscription).
Instance types and selection guide
Anti-DDoS Origin 2.0 offers best-effort protection for assets with public IP addresses. You can select one of the following instance types:
Anti-DDoS Origin 2.0 instance of Inclusive Edition for Small and Medium Enterprises: If you have no more than 30 assets that are assigned public IP addresses, the assets reside in the same region, and no more than two DDoS attacks occur on the assets per month, you can select this instance type.
Anti-DDoS Origin 2.0 Enterprise instance: If you have more than 30 assets that are assigned public IP addresses, the assets reside in multiple regions, and both IPv4 addresses and IPv6 addresses are used, you can select this instance type.
Both instance types support Insurance and Unlimited protection modes. The table below outlines the differences in mitigation sessions and supported network protocols for each type.
Item | Inclusive Edition for Small and Medium Enterprises | Anti-DDoS Origin Enterprise |
Item | Inclusive Edition for Small and Medium Enterprises | Anti-DDoS Origin Enterprise |
Mitigation capabilities | The mitigation capabilities vary based on regions. For more information, see Mitigation capabilities. | Best-effort protection. |
Mitigation sessions | Insurance: two sessions per month. | Unlimited: unlimited sessions. |
Network protocol | An instance can protect only assets that are assigned IPv4 addresses or IPv6 addresses. | An instance can protect assets that are assigned both IPv4 addresses and IPv6 addresses. |
Supported regions | An instance can protect only assets that are assigned public IP addresses and that reside in the same region. | An instance can protect assets that are assigned public IP addresses and that reside in any region in the Chinese mainland. Important If your service is deployed outside the Chinese mainland, we recommend that you purchase an elastic IP address (EIP) with Anti-DDoS (Enhanced) enabled or an Anti-DDoS Proxy (Outside Chinese Mainland) instance. If you want to use an Anti-DDoS Origin 2.0 (Subscription) instance, contact us. For more information, see Contact us. |
Number of protected assets that are assigned public IP addresses | No more than 30. | Unlimited. |
Clean bandwidth | You can specify a bandwidth of up to 1,000 Mbit/s. | Unlimited. |
Metering Method of 95th Percentile Burstable Clean Bandwidth | Not supported. | Supported. When enabled, the total of the clean bandwidth and the burstable clean bandwidth is five times the clean bandwidth. |
Mitigation logs feature | Not supported. | Supported. |
Scenarios that support upgrade
The following section describes the scenarios in which you can increase the number of mitigation sessions and supported regions. You can also increase the clean bandwidth and the number of assets that are assigned public IP addresses based on your business requirements.
Inclusive Edition for Small and Medium Enterprises (Insurance)
If you require more than two mitigation sessions per month, you can upgrade your instance to Inclusive Edition for Small and Medium Enterprises (Unlimited).
If you want to protect assets that are assigned public IP addresses and reside in multiple regions, you can upgrade your instance to Anti-DDoS Origin 2.0 Enterprise (Insurance) or Anti-DDoS Origin 2.0 Enterprise (Unlimited).
Inclusive Edition for Small and Medium Enterprises (Unlimited)
If you want to protect assets that are assigned public IP addresses and reside in multiple regions, you can upgrade your instance to Anti-DDoS Origin 2.0 Enterprise (Unlimited).
Anti-DDoS Origin 2.0 Enterprise (Insurance)
If you require more than two mitigation sessions per month, you can upgrade your instance to Anti-DDoS Origin 2.0 Enterprise (Unlimited).
Note
You can select Inclusive Edition for Small and Medium Enterprises (Unlimited) or Anti-DDoS Origin 2.0 Enterprise (Insurance) only during instance upgrade. You cannot select the instance types when you purchase a new instance.
Billable items
Total fee for an instance = Subscription fee (Fee for the protection mode + Fee for the clean bandwidth + Fee for protected assets that are assigned public IP addresses) + Pay-as-you-go fee (Fee for the burstable clean bandwidth feature)
Subscription
Fee for the protection mode
The basic protection fee of the instance. The fee varies based on the protection mode of the instance.
Protection mode | Unit price (USD per month) |
Protection mode | Unit price (USD per month) |
Inclusive Edition for Small and Medium Enterprises (Insurance) | 1,950 |
Anti-DDoS Origin 2.0 Enterprise (Unlimited) | 6,000 |
Fee for the clean bandwidth
Protection mode | Unit price (USD per month per Mbit/s) |
Protection mode | Unit price (USD per month per Mbit/s) |
| 10 |
| 5 |
Fee for the protected assets that are assigned public IP addresses
You are charged based on the number of protected assets that are assigned public IP addresses. The actual fee is calculated based on the tiered prices and varies based on the protection mode of the instance. If the numbers of protected assets that are assigned public IP addresses listed in the following table cannot meet your business requirements, contact us. For more information, see Contact us.
Protection mode | Number of protected assets that are assigned public IP addresses | Unit price (USD per month per asset) |
Protection mode | Number of protected assets that are assigned public IP addresses | Unit price (USD per month per asset) |
Inclusive Edition for Small and Medium Enterprises (Insurance) and Inclusive Edition for Small and Medium Enterprises (Unlimited) | [0,100] | 24 |
Anti-DDoS Origin 2.0 Enterprise (Insurance) and Anti-DDoS Origin 2.0 Enterprise (Unlimited) | [0,30] | 0 |
(30,100] | 24 |
(100,300] | 19.2 |
(300,500] | 14.4 |
(500,700] | 12 |
(700,1000] | 9.6 |
For example, you purchase an Anti-DDoS Origin 2.0 Enterprise (Unlimited) instance and select 200 protected assets. You can calculate the fee for the protected assets by performing the following steps:
The fee for the 30 protected assets is calculated based on the pricing tier [0,30]. The monthly fee is USD 0.
The fee for the 70 protected assets is calculated based on the pricing tier (30,100]. The monthly fee is calculated by using the following formula: 24 x 70 = USD 1,680.
The fee for the additional 100 protected assets is calculated based on the pricing tier (100,300]. The monthly fee is calculated by using the following formula: 19.2 x 100 = USD 1,920.
The total monthly fee for the protected assets is calculated by using the following formula: 1,680 + 1,920 = USD 3,600.
Pay-as-you-go
Pay-as-you-go includes the fee for the burstable clean bandwidth feature.
After enabling the Metering Method of 95th Percentile Burstable Clean Bandwidth, the burstable clean bandwidth is five times the clean bandwidth. For example, if the clean bandwidth is 1 Gbit/s, after enabling this option, the clean bandwidth can increase by 4 Gbit/s, totaling 5 Gbit/s.
Traffic that exceeds the allowed peaks for the instance will incur postpaid fees, while traffic within the clean bandwidth will not. The usage of burstable clean bandwidth can be monitored in the Billing Center. For more information, see Query usage details on the Billing Management page.
Billing method | Unit price | Fee calculation |
Billing method | Unit price | Fee calculation |
Daily 95th Percentile | 1.79 USD per month per Mbit/s | Fee = 95th percentile bandwidth × Unit price The 95th percentile bandwidth is determined in the following steps: Calculate the total peak traffic: Identify the total peak traffic by collecting traffic peaks every five minutes over a calendar day, resulting in 288 values. Exclude the top five values and any values recorded during DDoS attacks. The highest of the remaining values is the total peak traffic. Calculate the 95th percentile bandwidth: The 95th percentile bandwidth = The lesser of the total peak traffic or the total clean bandwidth - The clean bandwidth Note that the total clean bandwidth is five times the amount of the clean bandwidth.
|
Monthly 95th Percentile | 12.5 USD per month per Mbit/s | Fee = 95th percentile bandwidth × Effective factor × Unit price The 95th percentile bandwidth is determined in the following steps: Calculate the total peak traffic: Record the daily bandwidth peak by collecting traffic peaks every five minutes throughout a calendar day, excluding any values during DDoS attacks. Use the highest of the remaining 288 values as the daily bandwidth peak. Sort the daily bandwidth peaks for the month in descending order and average the top five to establish the total peak traffic.
Calculate the 95th percentile bandwidth: The 95th percentile bandwidth = The lesser of the total peak traffic or the total clean bandwidth - The clean bandwidth The total clean bandwidth is calculated by taking the highest of clean bandwidth corresponding to the top five daily bandwidth peaks and multiplying it by five. The clean bandwidth is the value recorded on the last day of the month when the burstable clean bandwidth feature is enabled.
The effective factor is the ratio of the number of valid days in a calendar month to the total number of days in that month. For instance, if the burstable clean bandwidth feature is activated on July 15, 2024, and remains enabled for the rest of July, the effective factor for the 16 valid days out of 31 total days is 0.51612903.
|
Note
Monthly 95th percentile billing method is recommended by default. Daily 95th percentile billing method is suitable for short-term sales promotions.
Disabling either billing method takes effect the day after the action is completed. You can disable each method only once per month.
You can switch directly between monthly and daily 95th percentile billing methods. The switch takes effect in the following month, and you can switch only once a month.
The following table shows the billing and settlement times, with specific timings subject to the system:
Billing method | Billing time | Settlement time |
Billing method | Billing time | Settlement time |
Daily 95th Percentile | Around 10:00 on the following day, the bill of the previous day will be sent to the contact registered for your Alibaba Cloud account by email and internal message. | Around 16:00 on the following day, Alibaba Cloud will send notifications on the burstable bandwidth usage and deduct the corresponding fees from your account balance. |
Monthly 95th Percentile | Around 10:00 on the first day of the following month, the bill of the previous month will be sent to the contact registered for your Alibaba Cloud account by email and internal message. | Around 11:00 on the third day of the following month, Alibaba Cloud will send notifications on the burstable bandwidth usage and deduct the corresponding fees from your account balance. |
Mitigation sessions
The system logs attack traffic every 5 seconds, resulting in 12 logs per minute. When attack traffic surpasses N Gbit/s, the system calculates the attack duration by summing the values of X and Y, as depicted below. When the total duration exceeds 15 minutes, or 180 logs, a session of best-effort protection is formed.
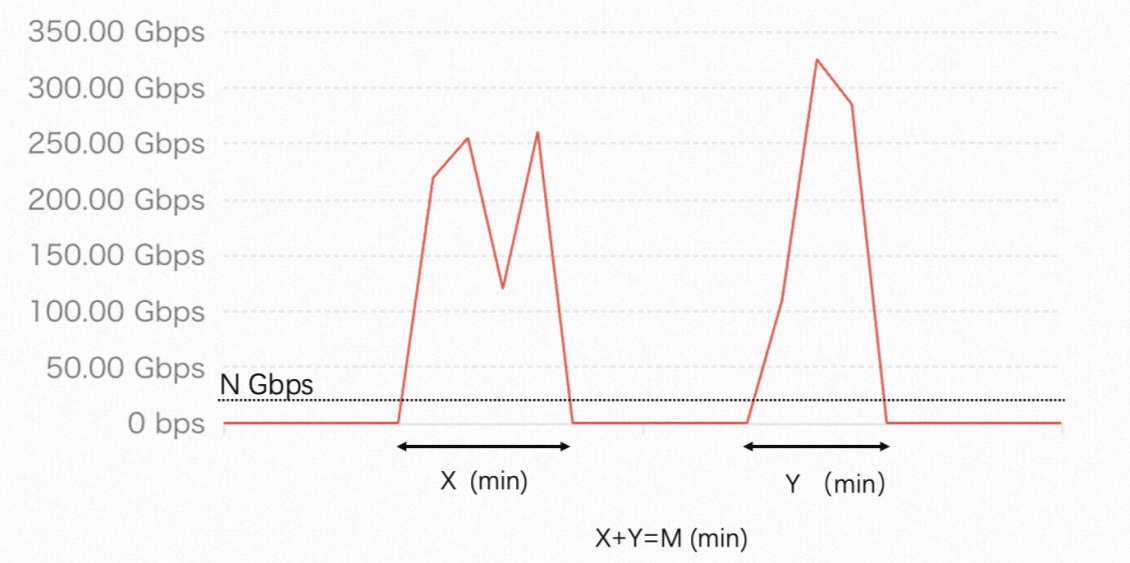
The red curve in the figure represents the inbound bandwidth of an asset with a public IP address.
For assets within the Chinese mainland, N is set at 20 Gbit/s.
For assets outside the Chinese mainland, N is set at 10 Gbit/s.
To learn how to check the remaining mitigation sessions, refer to Query the number of remaining mitigation sessions for an instance of Inclusive Edition for Small and Medium Enterprises.
Business scale estimation
You can estimate your business scale by using the following method:
Sample inbound and outbound bandwidth at five-minute intervals. Calculate the average inbound and outbound bandwidth. Use the greater average value as the bandwidth of the sample point. At the end of each month, sort all sample points in descending order, ignore the top 5% of sample points, and then use the first value of the remaining 95% of sample points as the 95th percentile bandwidth.
Bandwidth overuse
Anti-DDoS Origin allows your clean bandwidth to exceed the clean bandwidth of your Anti-DDoS Origin instance for a short period of time. If the period exceeds 36 hours, the Anti-DDoS Origin mitigation becomes invalid and only basic mitigation capabilities are provided. After exceeding the limit, Alibaba Cloud will send an over-limit notification through the channels you have configured in the message notifications.
To restore Anti-DDoS Origin mitigation capabilities, you can:
Wait for automatic restoration in the next month.
For Anti-DDoS Origin 2.0 (Subscription) Enterprise instances, you can enable the burstable clean bandwidth feature to restore the capabilities. This will increase the clean bandwidth by four times.
Upgrade the clean bandwidth of your Anti-DDoS Origin instance. Once upgraded, protection will automatically restore, and the overuse time will reset.
Important
If the clean bandwidth exceeded the limit for 36 hours before using Method 2 and 3, resulting in the Anti-DDoS Origin mitigation being disabled, any further overages that month will downgrade protection the next day.
If the clean bandwidth exceeded the limit but not yet 36 hours before using Method 2 and 3, the over-limit duration will continue to accumulate. Once the total reaches 36 hours, protection will downgrade the next day.
View overuse details in the Billing Center. For more information, see Query usage details on the Billing Management page.
Overdue payments
As Anti-DDoS Origin 2.0 (Subscription) instances are prepaid, there are no overdue payments. Before you can purchase, upgrade, or renew an instance, make sure that your account balance is sufficient. To avoid service disruption, we recommend enabling auto-renewal for your instance.
Expiration
Days after the expiration date | Impact of expiration | Solution |
Days after the expiration date | Impact of expiration | Solution |
Within seven days after the instance expires | After the instance expires, the instance is suspended. After you renew the instance, the instance is restored. | Renew an instance |
More than seven days after the instance expires | On the eighth day after the instance expires, the instance is released and cannot be restored. | None |
Refunds
After you purchase an Anti-DDoS Origin 2.0 (Subscription) instance, you cannot request a refund for the instance.
 Elastic Compute Service (ECS)
Elastic Compute Service (ECS)
 Lingma
Lingma



























