After you add your asset that is assigned a public IP address to an Anti-DDoS Origin Enterprise instance, you can query the DDoS attack events that occur on the asset and the event details on the Attack Analysis page. This way, you can view the details of the attack mitigation process in a visualized manner. This helps improve attack analysis experience. In this topic, assets that are assigned public IP addresses are referred to as assets for short. This topic describes how to view the event details on the Attack Analysis page.
Prerequisites
An Anti-DDoS Origin instance is purchased. For more information, see Purchase an Anti-DDoS Origin Enterprise instance.
The assets that you want to protect are added to the Anti-DDoS Origin instance. For more information, see Add objects for protection.
Procedure
Log on to the Traffic Security console.
In the left-side navigation pane, choose .
On the Attack Analysis page, select a time range to query attack events.
NoteIf your Alibaba Cloud account has the multi-account management feature enabled and is the management account, you can also select an account range to query attack events.
All accounts: You can view the DDoS attack events of the assets that belong to the management account and members. The assets must be added to the instances that belong to the management account.
A single member: You can view the DDoS attack events of the assets that belong to a member. The assets must be added to the instances that belong to the management account.
For more information, see Use the multi-account management feature.
You can query attack events within the last six months.
Attack Types: Only Volumetric Attack is supported.
Attack Target: the asset that is attacked.
Start and End Time: the start time and end time of the attack.
Owner Account of Event: the Alibaba Cloud account to which the asset belongs.
Peak Attack Throughput: the peak attack bandwidth in bit/s and the peak forwarding rate of attack packets in pps.
View event details.
You can click View Details in the Actions column of an attack event to go to the Details of the incident page. On this page, you can view the event details and perform the required operations.
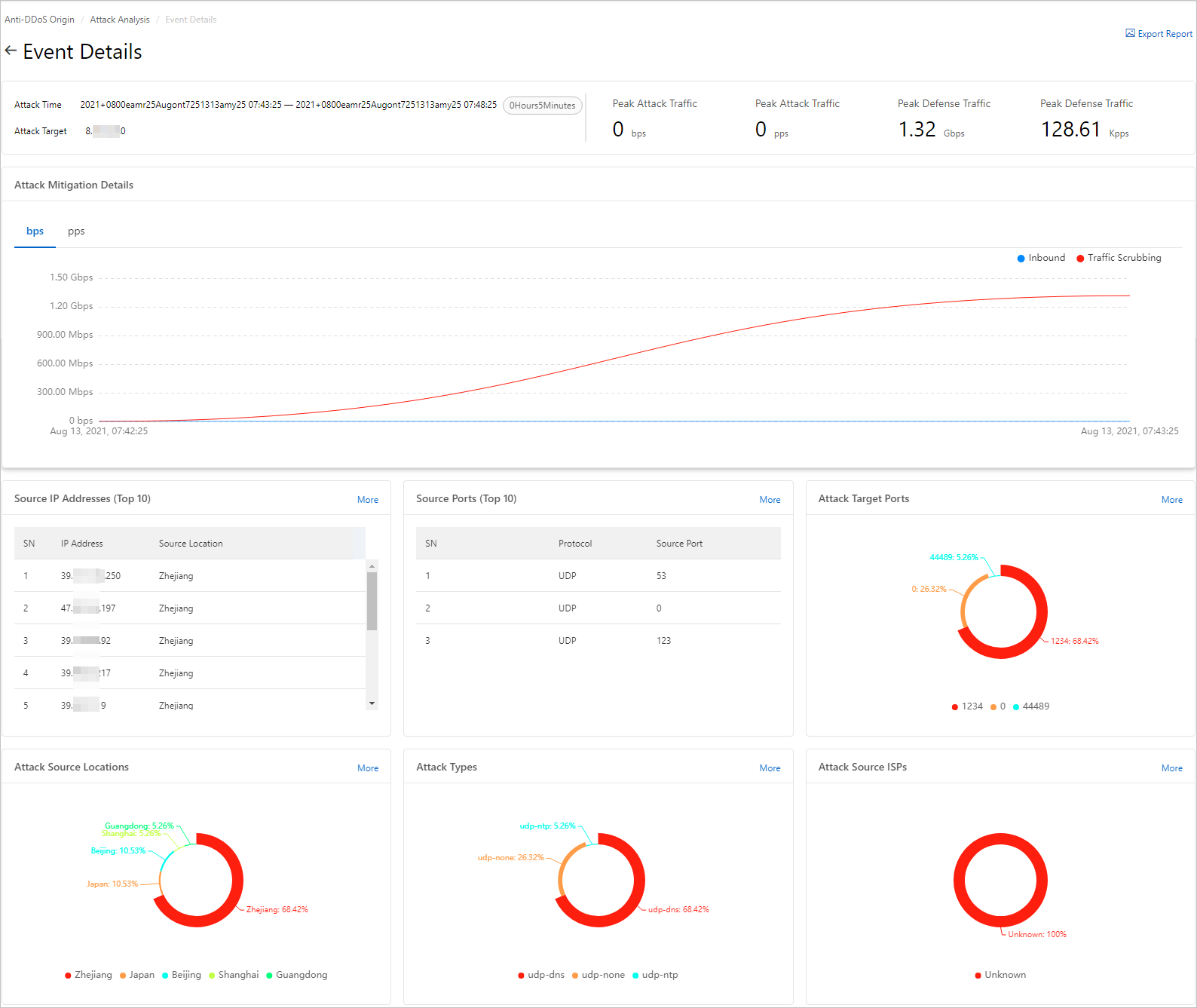
The Details of the incident page displays the following information:
Attack Time, Attack Target, Peak Attack Traffic, and Peak Defense Traffic, which are in the upper part of the page.
Peak Attack Traffic: displays the peak attack bandwidth and the peak forwarding rate of the attack packets that are detected by the Anti-DDoS Origin Enterprise instance. Peak Defense Traffic: displays the peak attack bandwidth that is scrubbed by the Anti-DDoS Origin Enterprise instance and the peak forwarding rate of the attack packets. The peak attack bandwidth is in bit/s and the peak forwarding rate is in pps.
Attack Mitigation Details: displays the trends of bandwidth changes to the inbound traffic and the scrubbed traffic, and the trends of forwarding rate changes to the inbound packets and the traffic scrubbing packets. The bandwidths of the inbound traffic and the scrubbed traffic are in bit/s and the forwarding rates of the inbound packets and the traffic scrubbing packets are in pps.
Attack Source IP Addresses: displays the source locations and IP addresses of requests. The list displays the top 10 IP addresses from which the most requests are initiated. You can click More to view the top 100 IP addresses.
NoteThe requests include attack requests and normal service requests.
Source Ports (Top 10): displays the source ports and protocols of the requests. The list displays the top 10 ports from which the most requests are initiated. You can click More to view the top 100 ports.
NoteThe requests include attack requests and normal service requests.
Attack Target Ports: displays the distribution of destination ports. You can click More to view the distribution of requests destined for different destination ports.
NoteThe requests include attack requests and normal service requests.
Attack Source Locations: displays the distribution of locations from which attack traffic is originated. You can click More to view the distribution of requests originated from different locations.
Attack Type: displays the distribution of attack types. You can click More to view the distribution of different attack types.
Attack Source ISPs: displays the distribution of Internet service providers (ISPs) from which attack traffic is originated. You can click More to view the distribution of requests originated from different ISP networks.