Container-based virtualization is a type of virtualization technology. Compared with a virtual machine (VM), a container is lighter and more convenient to deploy. Docker is currently a mainstream container engine, which supports platforms such as Linux and Windows, as well as mainstream Docker orchestration systems such as Kubernetes (K8S), Swarm, and Rocket (RKT). Common container networks support multiple models such as Bridge, Overlay, Host, and user-defined networks. Systems such as K8S rely on the Container Network Interface (CNI) plug-ins for network management. Commonly used CNI plug-ins include Calico and Flannel.
This article will introduce the basics of container networks. Based on Alibaba Cloud's Elastic Network Interface (ENI) technology, the ECS container network features high performance, easy deployment and maintenance, strong isolation, and high security.
This section introduces the working principle of traditional container networks.
CNI is an open source project managed by the Cloud Native Computing Foundation (CNCF). It develops standards and provides source code libraries for major vendors to develop plug-ins for Linux container network management. Well-known CNI plug-ins include Calico and Flannel. Calico implements protocols such as BGP through Flex/Bird, and stores them into a distributed in-memory database to establish a large Layer 3 network, enabling containers on different hosts to communicate with containers on different subnets without sending ARP.
Flannel implements a container overlay network based on tunneling technologies such as VXLAN. The CNIs such as Calico/Flannel use VETH pairs to configure the container network. A pair of VETH devices are created, with one end bound to the container, and the other end to the VM. The VM forwards the container network through technologies such as the network protocol stack (overlay network), Iptables (Calico plug-in), or Linux Bridge. (When the container network is connected to the vSwitch through the bridge in the ECS, the VPC can only reach the ECS level, and the container network is a private network on the bridge.)
The following figure shows the workflow of the currently mainstream container network, which differs from the multi-NIC container network from the following aspects: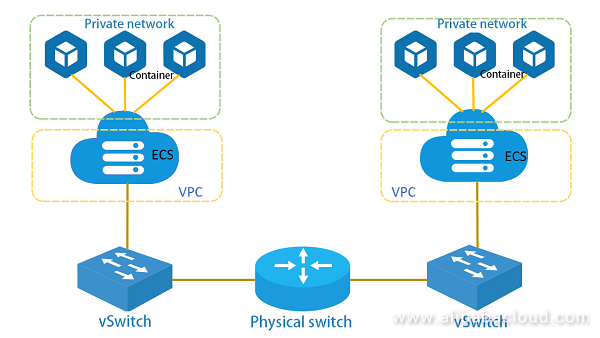
Smart home is one of the most prominent application of IoT, and many companies have invested heavily in this field.
The Internet of Things (IoT) has led to the innovation of a variety solutions, covering both consumer and industrial applications. Smart home is one of the most prominent application of IoT, and many companies have invested heavily in this field. However, a major drawback with smart home and other IoT applications is network security. Since all devices are connected to each other, a single faulty device can affect the integrity of the entire network. For smart-home owners, the security requirements on networks are demanding. A breached smart home allows unauthorized access to premises, or even the failure of critical systems such as fire protection systems.
To better understand the methods of securing smart homes, let us review the concept of network communications security.
In a Local Area Network (LAN), a third party might snoop transmitted information via the network. Although communication in a LAN is passive, a malicious listener can snoop critical data that is being communicated through the network. Additionally, malicious users can deceive the network using Address Resolution Protocol (ARP) and other means to obtain data without being detected.
What are some effective ways to solve this problem? In general, there are two methods to ensure the security of a communication network:
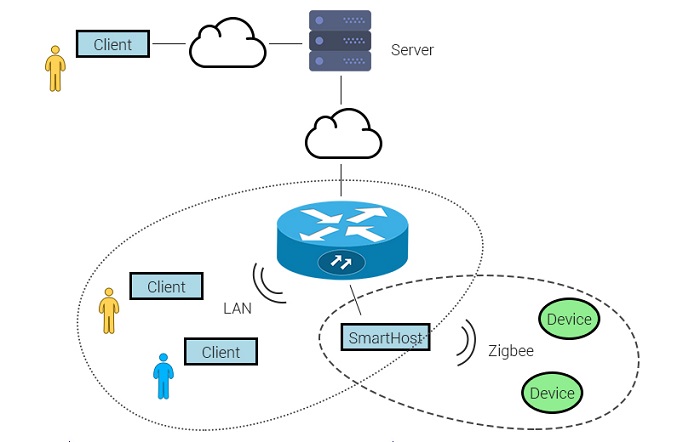
The image below shows a typical structure of a smart home system.
Wu Hanqing, Chief Security Researcher at Alibaba Cloud, talks about the various security measures to ensure the success of the Double 11 Shopping Festival.
Often times we talk about the impressive computing power needed to support a large-scale e-commerce event such as Alibaba's annual Double 11 Shopping Festival (Singles' Day). However, you probably won't notice the challenges of protecting data, not only for the customers but also for the organization, at such a scale.
The man responsible for ensuring the security of Double 11 is Wu Hanqing, Chief Security Researcher at Alibaba Cloud, who is better known as "Brother Dao". In this article, Brother Dao will talk about Alibaba Cloud's various security measures to ensure the success of the Double 11 Shopping Festival.
The senior director of the Cloud security department at Alibaba Cloud discusses the idea of next-gen enterprise security architecture designs based on cloud-native tech.
Relive the best moments of the Apsara Conference 2019 at https://www.alibabacloud.com/apsara-conference-2019.
"With development of the digital economy, an increasing number of enterprises are migrating their business to the cloud. With this move, enterprises are building next-generation enterprise-level security architecture designs based on cloud-native security technologies, upgrading from a flat architecture to a three-dimensional architecture. With this move, the benefits of cloud-native security technologies will be maximized," said Xiao Li, Senior Director of Cloud Computing Security Department, Alibaba Cloud Intelligence, at the Cloud Security Summit on September 27, 2019 during the Apsara Conference.
During the summit, Xiao Li stressed that cloud-native security technologies will be embedded in every module of the enterprise security architecture, which will help to improve the overall security of the system.
At the summit, Xiao Li released the Alibaba Cloud Security White Paper 4.0, in which the core capabilities required for the next-generation enterprise security architecture designs from the perspective of five horizontal systems and two vertical systems were described.
From the horizontal perspective, users need to build five systems. These five systems form a bottom-up security architecture that is tailored towards users' business requirements. The security of the Cloud platform serves as the base layer, upon which the basic security, data security, application security, and business security layers on the user side are stacked on top of each other. Cloud-native security technologies can be implemented in each module of this architecture in the form of product functions or security services, allowing enterprises to enjoy various advantages, such as higher performance, stronger scalability, and more intelligent defense, of cloud-native security technologies.
From the vertical perspective, users need to build two systems: account security and operations security systems. These two systems cover all aspects and nodes. In this case, enterprises can thoroughly transform the flat security architecture to a three-dimensional security architecture. The vertical systems are essential for the cloud security architectures of all enterprises.
In the whitepaper, Xiao Li demonstrated the cloud security best practices provided by Alibaba Cloud to users. His intention is to help enterprises build systems of higher-level security. These best practices include unified account authentication, network access control, data security, threat detection and response, and global security defense.
The growth of cloud-native security brings about boundless benefits to the public and enterprise users alike, making the "unified" security model an inescapable trend. In response to this trend, Alibaba Cloud has applied cloud-native security technologies in their products and services that are provided to cloud-based enterprises, and recommends such best practices to the industry.
This course is associated with Network Series Courses. You must purchase the certification package before you are able to complete all lessons for a certificate.
The network is the only entry point for all cloud services. Network attacks, especially denial of service attacks, are the most diverse and harmful, and one of the most difficult to protect against network risks. This course is designed to help students understand the principles of DoS attacks in a minimum amount of time and learn common protection methods and Alibaba Cloud Anti-DDoS protection solutions to minimize or reduce the risk of network layer attacks, protect your cloud network security.
For the security measures of the host on the cloud, we need to consider more factors, such as the configuration of the firewall inside the host, as well as various settings related to operating system user management and privilege management. Only by understanding and correctly configuring the security settings inside these hosts you can better cooperate with various cloud security products. This course is designed to help you better understand these security setup and learn how to properly configure them to maximize the security hardening of hosts on the cloud.
Through this course, you can understand the functions and usage scenarios of Alibaba Cloud Network products, and be able to use basic service functions. Study Now
Offers centralized configuration, policy-based provisioning, update management and end-to-end network monitoring for your Fortinet installation - You can further simplify management of your network security by grouping devices into geographic or functional administrative domains (ADOMs) - Easily manage VPN policy and configuration while leveraging FortiManager virtual appliances as a local distribution point for software and policy updates
Instant visibility, situation awareness, real-time threat intelligence and actionable analytics
This topic describes how to connect network instances by calling CEN API actions.
To connect network instances in the same region under the same account, follow these steps:
To connect network instances among different regions under the same account, follow these steps:
Simple Application Server has built-in firewalls which opens ports 22, 80, and 443 by default, and closes others. You can configure which ports to open.
Simple Application Server uses VPC by default, and all instances of one user are deployed in one VPC, which guarantees an isolated networking environment of each user.
For now, one user’s cloud products on different VPCs cannot be connected. For example, your Simple Application Server cannot access your RDS on another VPC.
Provides network acceleration service for your Internet-facing application globally with guaranteed bandwidth and high reliability.
A global network for rapidly building a distributed business system and hybrid cloud to help users create a network with enterprise level-scalability and the communication capabilities of a cloud network
A unified security management system that identifies, analyzes, and notifies you of security threats in real time.
Cloud-Native: Best Practices for Container Technology Implementation
A Guide to Data Visualization Definition, Tools and Examples

2,593 posts | 793 followers
FollowAlibaba Clouder - March 21, 2019
Alibaba Clouder - July 18, 2019
Deepuu - September 1, 2025
Alibaba Clouder - July 19, 2019
Alibaba Clouder - June 22, 2020
Alibaba Clouder - January 5, 2021

2,593 posts | 793 followers
Follow Anti-DDoS
Anti-DDoS
A comprehensive DDoS protection for enterprise to intelligently defend sophisticated DDoS attacks, reduce business loss risks, and mitigate potential security threats.
Learn More Anti DDoS Basic
Anti DDoS Basic
A cloud-based security service that protects your data and application from DDoS attacks
Learn MoreMore Posts by Alibaba Clouder