By Jessie Angelica,Solution Architect Intern
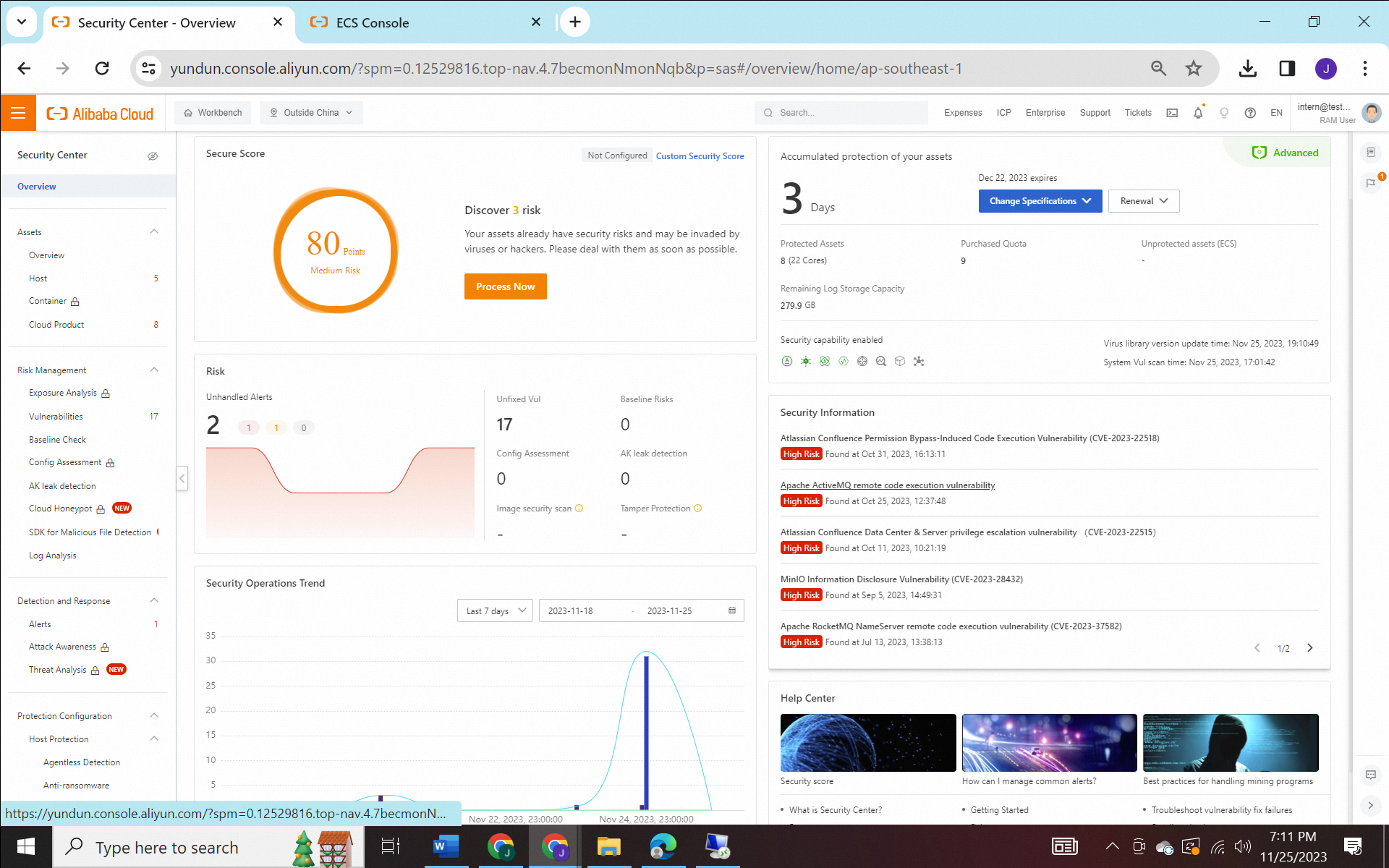
Zero-Day Resilience: Ransomware Defense with Cloud Firewall and Security Center
Ransomware is a type of malicious program or malware that threatens victims by encrypting or blocking access to critical data or systems until a ransom is paid. Ransomware attacks rely on seizing control of individual or organizational data or devices as a means of extortion. Recently, human-operated ransomware has become more popular among criminals due to its significant ransom potential. For instance, vulnerabilities arise when numerous servers run a multitude of programs/libraries or use outdated packages. This susceptibility can result from various sources, including email, leading to potential exploits by ransomware, viruses, RDP attacks, malware, or cryptocurrency mining.
Ransomware kill chain :
1) Infection: If your servers or databases are infected with ransomware, your business data may be encrypted for ransom, and it is impossible to decrypt most of the time. It can cause severe risks, such as service interruptions, data leaks, and data loss.
2) Command and Control (C&C) Communication: The compromised hardware/device attempts to establish communication with the cybercriminal's server to obtain the encryption key.
3) Encryption of Device: Application of encryption to the infected device to restrict access and demand ransom.
4) Propagation: Beyond the initial infected device, the ransomware seeks to propagate to other devices, potentially leveraging network vulnerabilities or specific files for transmission.
In this blog, we will discuss two Alibaba products designed to prevent ransomware: Security Center and Cloud Firewall. These are recommended, especially for companies with extensive internet interactions, massive online presence, and high levels of activity. So, How do they work to mitigate ransomware threats?
1) Security Hardening: Implement IP restrictions for accessing RDP and SSH ports and regularly update software. Apply security measures on Alibaba Cloud, such as using Cloud Firewall to monitor traffic, restricting IP access, and communicating with specific servers and ports. Additionally, employ a Security Center for vulnerability patching.
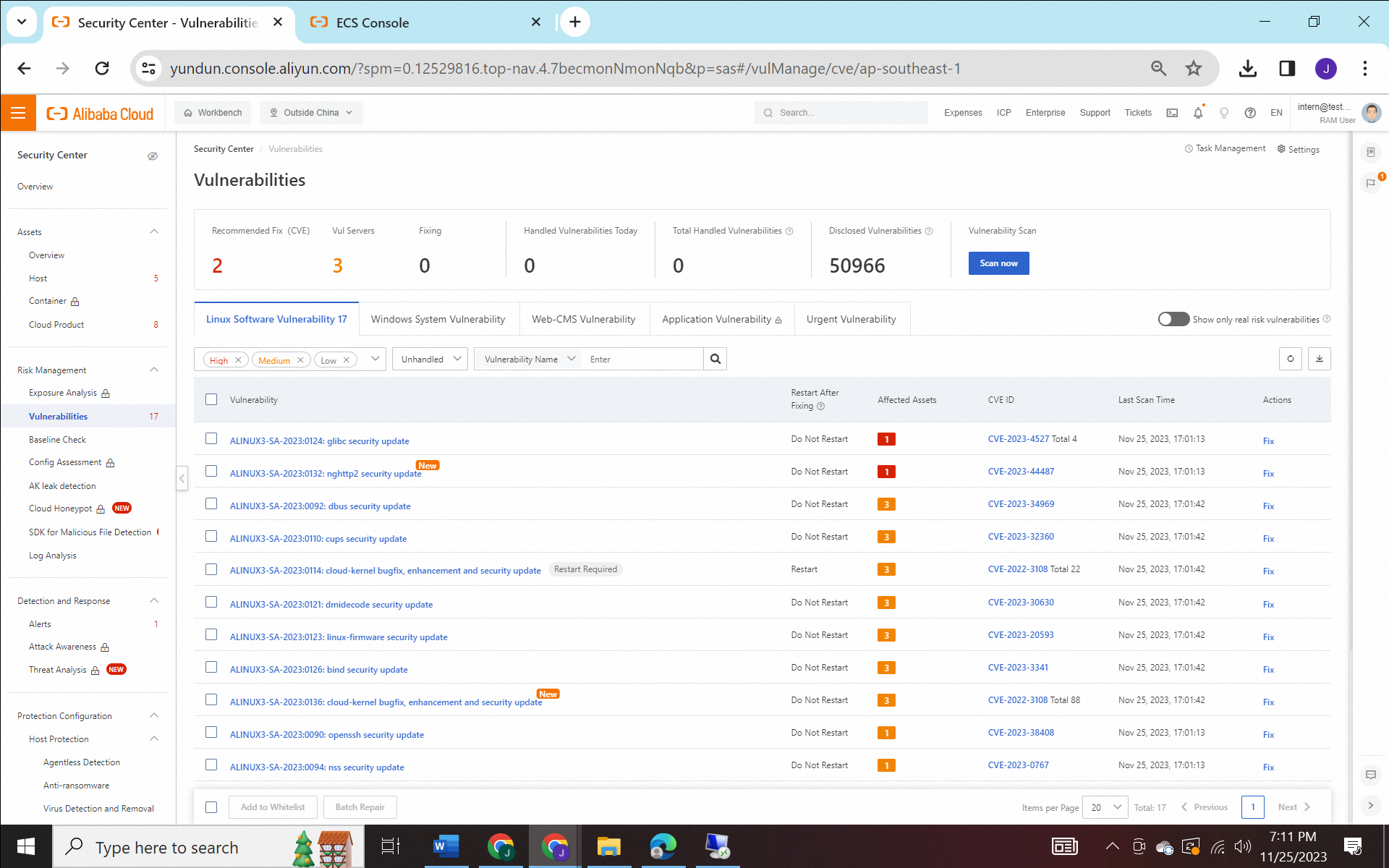
2) Vulnerability Defense: Perform actions like patching, baseline checking, and configuration assessment to ensure server compliance and identify potential vulnerabilities.
3) C&C Communication: Leverage the role of Cloud Firewall to block or lock specific URLs, allowing access only to designated third parties and restricting servers to communicate solely with specific endpoints.
4) Process Interception: Intercept anomalies or malicious activities occurring on servers or networks.
5) Handle Spread Internally: Contain affected servers to prevent the Spread of the ransomware to other systems.
6) Periodic Backup: Implement periodic backups as a safety net, as even with steps 1-5 in place, there is always a risk of encountering new ransomware types or zero-day attacks.
Security Center is a centralized security management system that dynamically identifies and analyzes security threats, and generates alerts when threats are detected. Security Center provides multiple features to ensure the security of cloud resources and servers in data centers (secure the host). The features include anti-ransomware, antivirus, web tamper proofing, container image scan, and compliance check.
Features of Security Center :
1) Security prevention: vulnerability detection and patch fix, and security baseline check. bisa memberikan rekomendasi hal yang perlu direpair dan cara repairnya misal harus menggunakan password rotation, configure password age policies, event audit policies
2) Threat Detection: Security Center have intrusion detection, virus detection, and integrated threat intelligence to detect the abnormal logon detection and behaviour, webshell, and others threat
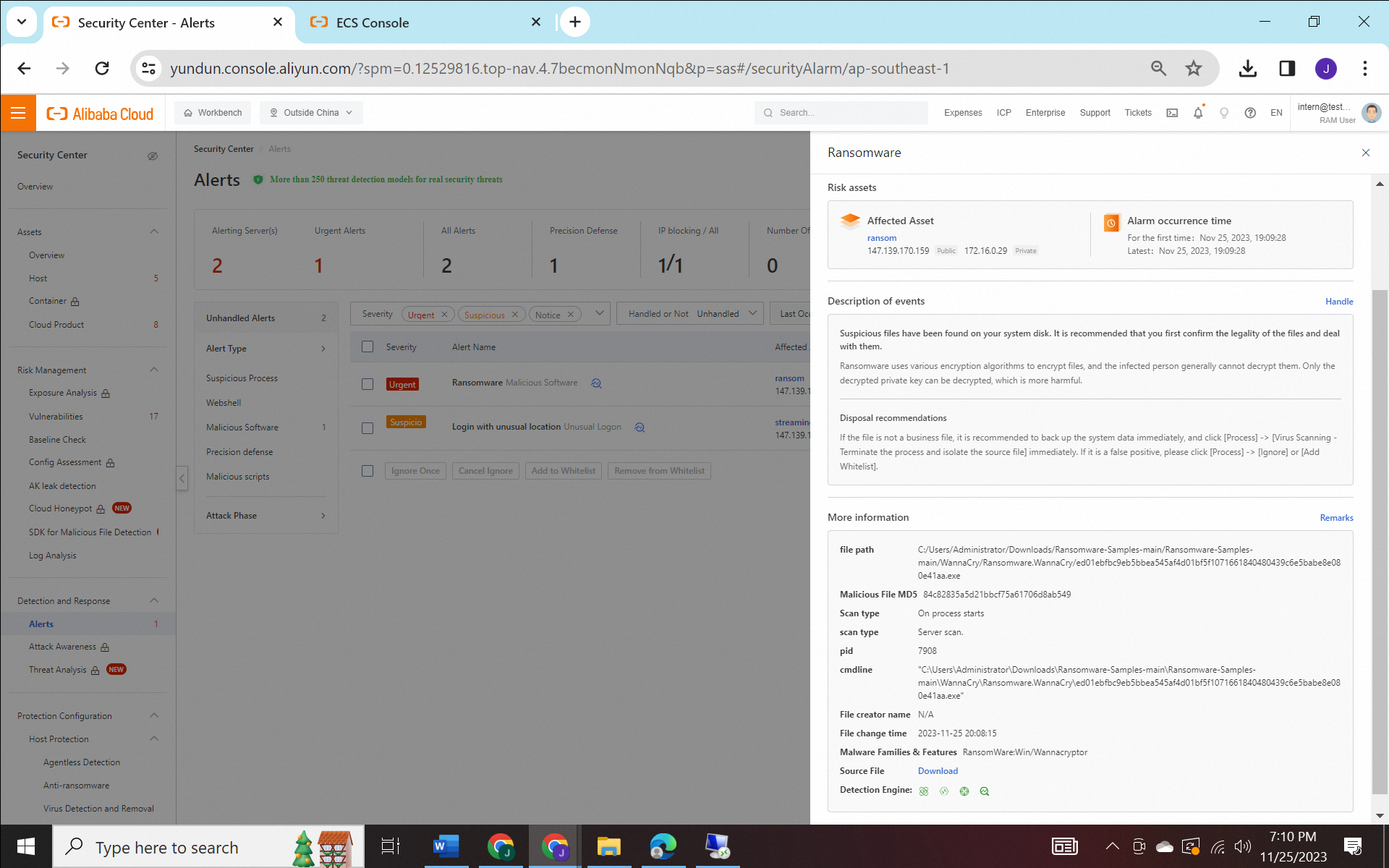
3) Detection and Response: Once abnormal encryption behavior is identified, it will be intercepted and a notification will be sent directly to the user.
4) Security Defense: security center is equipped by anti-brute force cracking, anti-virus, application whitelist, webpage tamper-proof, and anti-ransomware
5) Security Operations: the custom policies feature is used to configured and back up data on your critical servers or databases (inclusing directory). If your business data is encrypted by ransomware, you can restore the encrypted files based on the backup data. This reduces the adverse impacts on your workloads.
How to Create Anti-Ransomware Policy:
After you create an anti-ransomware policy, Security Center automatically backs up data in protected directories on your server.
1) Log on to the Security Center console. In the top navigation bar, select the region of the asset that you want to manage. The following regions are supported: China and Outside China.
2) In the left-side navigation pane, choose Protection Configuration > Host Protection > Anti-ransomware.
3) On the Server extortion virus protection tab of the Anti-ransomware page, click Create Policies.
4) In the Create Policies panel, configure the policy name, server type, server asset. The protection also provides the recommendation policy by default. The click OK.
After the anti-ransomware policy is created, the policy is enabled by default, and Security Center installs the anti-ransomware agent on your server. Then, Security Center backs up data in the protected directories of your server based on the backup settings that you configure in the anti-ransomware policy.
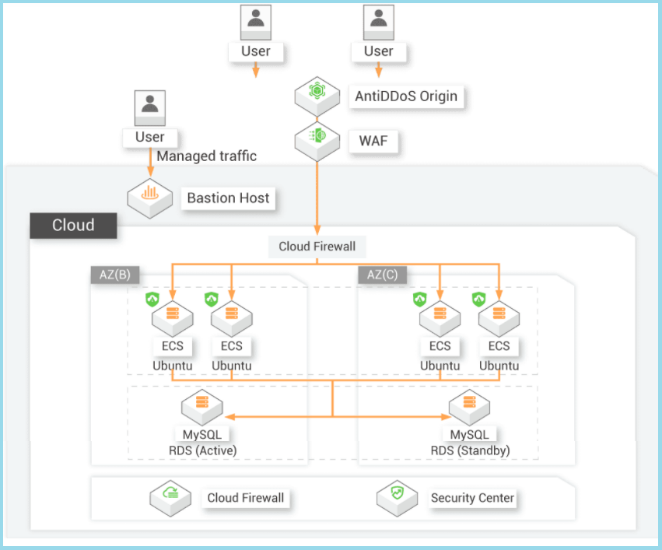
Cloud Firewall of Alibaba Cloud is a cloud security solution that provides firewalls as a service. Cloud Firewall implements centralized security isolation and traffic control for your cloud assets at the Internet, virtual private cloud (VPC), and host boundaries. Cloud Firewall integrates access by Alibaba Cloud network service, such as Virtual Private Cloud (VPC), Cloud Enterprise Network (CEN), Elastic IP Address (EIP), and Server Load Balancer (SLB).
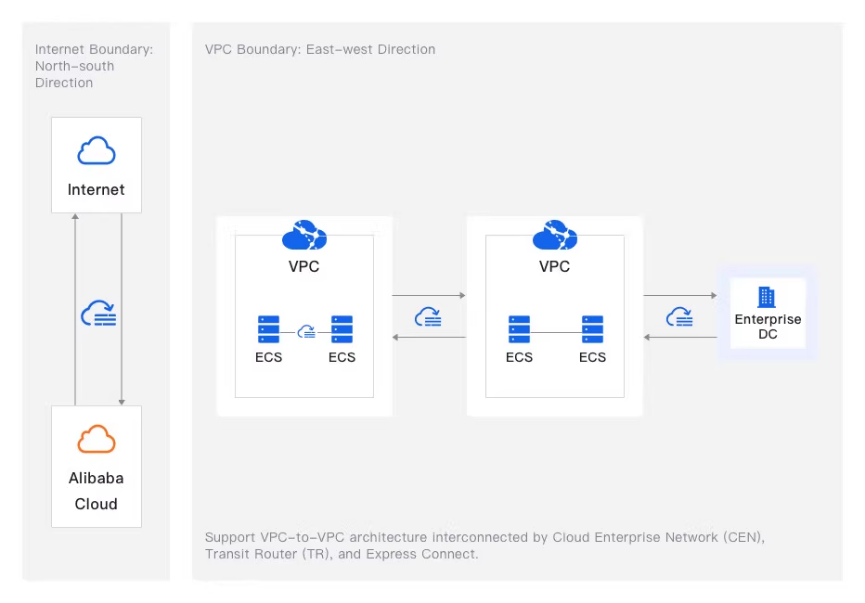
In its implementation, the Cloud Firewall serving as a gateway between Virtual Private Clouds (VPCs) and interconnectivity to data centers such as leased line, express connect, and Cloud Enterprise Network (CEN). Its responsibilities extend to impeding communication from internal networks to external cybercriminal servers, and containing servers to prevent further propagation. Furthermore, in the face of ransomware threats, the Cloud Firewall has threat intelligence and virtual patch features to define the rules and policies, enabling the allowance or denial of specific ports and providing a proactive defense strategy.
Features :
1) Fine-Grained Access Control: Cloud Firewall supports fine-grained access control from Layer 4 to Layer 7, including filtering out any IP addresses, ports, applications, domains, and locations, helping reduce the network attack surface.
2) Detection and Protection of Outbound Connections: Cloud Firewall can display outbound connection traffic mirror sessions for your assets in real-time, helping detect suspicious hosts and breaches
3) VPC Isolation-and Control: VPC firewalls help detect and control the traffic between VPCs and the traffic between VPCs and data centers, and .
4) Real-Time Intrusion Detection and Protection: Cloud Firewall blocks and intercepts the common attacks in real-time, including command executions, reverse shells, database attacks, mining and trojan programs, viruses, and worms.
5) Network Log Audit and Visualized Traffic Analysis: Cloud Firewall supports the log records in real-time. For example, you can audit and track attack defense logs and hit results of access control rules. It also monitors the traffic information, traffic trend charts of all public IP addresses, and inbound and outbound traffic.
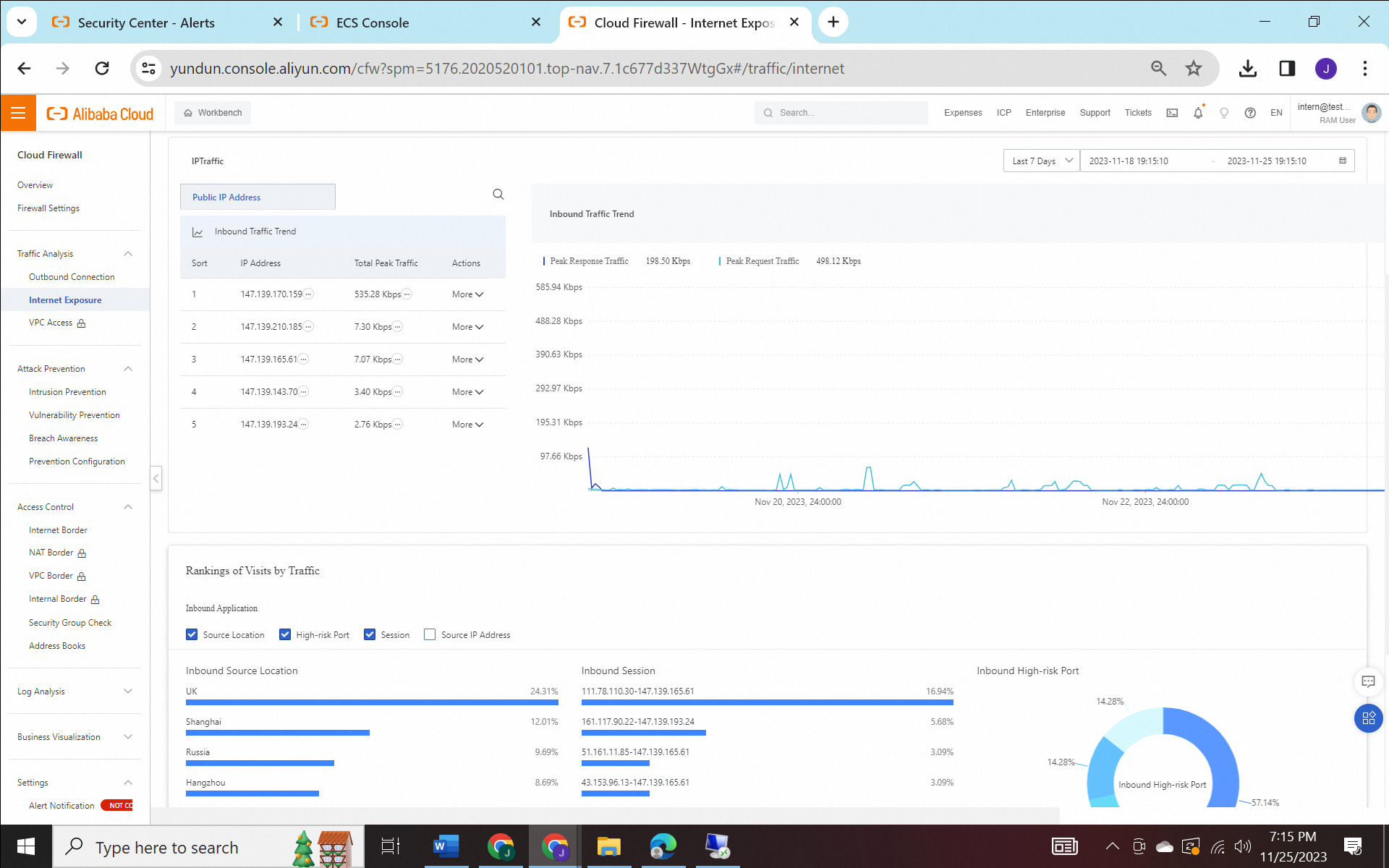
At the internet border, the cloud firewall is responsible for monitoring inbound traffic to assess the amount of attempts to access our server. Simultaneously, in the outbound policy, the cloud firewall is actively engaged in identifying and preventing potential cyber attacksto communicate with our server. This involves the ability to filter and establish policies that dictate which connections should be allowed and which ones should be denied. It also has the ability to identify the country of origin of an attacker.
119 posts | 21 followers
FollowAlibaba Cloud Community - December 8, 2023
Alibaba Cloud Indonesia - January 8, 2025
Amuthan Nallathambi - August 24, 2023
Balaban - March 17, 2021
Dikky Ryan Pratama - May 17, 2023
PM - C2C_Yuan - June 3, 2024
119 posts | 21 followers
Follow Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Cloud Governance Center
Cloud Governance Center
Set up and manage an Alibaba Cloud multi-account environment in one-stop mode
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Cloud Hardware Security Module (HSM)
Cloud Hardware Security Module (HSM)
Industry-standard hardware security modules (HSMs) deployed on Alibaba Cloud.
Learn MoreMore Posts by Alibaba Cloud Indonesia