On June 1, 2017, the Cybersecurity Law of the People's Republic of China was officially implemented, marking an important milestone in China's establishment of strict network governance guidelines. On May 13, 2019, the "Baseline for Classified Protection of Cybersecurity" and other relevant national standards were officially released, opening the era of Classified Protection 2.0. Additionally, the "Measures for Data Security Management (Draft for Comments)", "Regulation on the Protection of Children's Personal Information Online", "Guideline for Internet Personal Information Security Protection", "Measures for Security Assessment of Cross-Border Data Transfer of Personal Information and Important Data", and "Cryptography Law of the People's Republic of China" were released in quick succession. The General Data Protection Regulation (GDPR) issued by the European Union in 2018 is currently the most stringent and detailed law designed to protect the security of user data. Starting in January 2020, the California Consumer Privacy Act (CCPA) came into force. This act regulates all business activities that involve data related to California residents.
With the introduction of laws and regulations around the world, data security is becoming increasingly important. In data collection, application, and storage procedures, data security protection and privacy protection are no longer optional.
Constant attacks by ransomware also pose major challenges to data security. There are familiar names like GlobeImposter, Phobos, and Cryosis as well as new names like HackedSecret and Makop. All of these ransomware launched violent attacks against various systems.
Software vendors and cloud service providers must constantly enhance their ransomware detection capabilities to prevent the reinfection of backup data. At the same time, ransomware defense technology needs to move from detecting and alerting against attacks to identifying malicious code before intrusion to protect the security of backup data.
Protecting data security against human error is an aspect of data security that is often overlooked. Inside enterprises, such human errors include the improper selection of technologies, weak security awareness, lack of backup and disaster recovery planning, and improper process configurations, such as improper permissions or privileged users. Manual operations can result in service crashes or the deletion of core databases, which can permanently damage the operational capabilities and competitiveness of an enterprise.
Data sharing platforms based on a centralized data exchange mechanism have the problems of complex processes, high costs, and low efficiency in personal privacy protection. Therefore, data security needs to be empowered by new digital technologies. For example, artificial intelligence (AI) technology is required to implement more efficient data security management, help ensure the secure use of data at large scale, and advance the digital transformation of the economy and society.
Data access permissions specify when, how, and by whom data can be obtained. Access management is an effective way to protect data.
Alibaba Cloud storage products support standard directory and file-specific operations in file systems, read, write, and execute permissions for users and groups, Virtual Private Cloud (VPC) mount points, and classic network mount points. These products also support allowing only Elastic Compute Service (ECS) instances to access file systems in the same VPC or under the same account. At the same time, our storage products provide the permission group function, which can add permission group rules through a whitelist. This allows only the specified IP addresses or network segments to access the file system. In addition, users can apply different levels of fine-grained access permissions to different IP addresses or network segments. These methods implement effective permission control for data access and make data more secure.
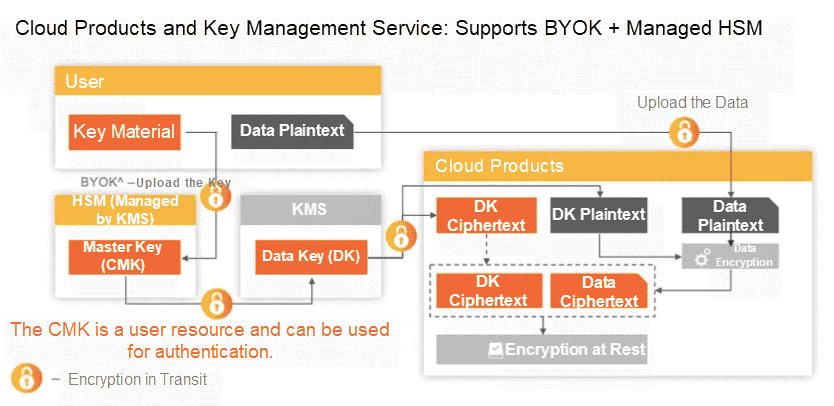
As the most common data security method, data encryption can be performed by the source, intermediate device, or transmission channel. The main problems in data encryption are how to store and use keys properly.
At the storage stage, Alibaba Cloud Object Storage Service (OSS) provides the read many feature, which allows users to prevent the tampering with or deletion of data stored in the cloud. The data encryption feature of OSS supports both client-side encryption and server-side encryption. OSS can use key hosting services and user-defined key methods for encryption, greatly improving data security and compliance.
At the same time, Alibaba Cloud provides services for transparent internal operations, which allow users to view and control operation logs on the cloud platform, increasing users' trust in the security of Alibaba Cloud.
In the data transmission phase, Alibaba Cloud Network Attached Storage (NAS) provides encryption in transit and encryption at rest functions to guarantee data security during transmission through managed keys and private key encryption. Alibaba Cloud Disk is integrated with Alibaba Cloud Key Management Service (KMS) to allow users to encrypt disks and ensure data privacy and autonomy. Users can encrypt their data by using the one-click cloud disk encryption function.
For cloud users, it is very important to know who accessed what data at what time and what operations they performed. In particular, when a security event occurs, users must be able to quickly locate the source of the event by querying operation records, determine whether the event is resulting from an internal or external attack, and address the event immediately.
To this end, Alibaba Cloud provides operation log storage services for cloud users. Data owners can enable access logging for their data in the Alibaba Cloud Storage console. After access logging is enabled, access logs are automatically generated on an hourly basis, named according to predefined naming rules, and then written to a specified location. Users can analyze these log files directly by using the Alibaba Cloud Data Lake solution or by building a Spark cluster. Users can also set lifecycle management rules to convert the storage class of log files to Archive for long-term archiving.
The real-time log query function combines storage with log services. This feature allows users to query relevant access logs in the console and helps users perform data access operation audits, compile access statistics, backtrack abnormal activities, and locate problems.
To ensure the security of users' log data, all HTTP requests to the log service API must undergo security verification. The verification process is based on the Alibaba Cloud Access Key mechanism and completed by using the symmetric encryption algorithm. This feature prevents log tampering and comprehensively improves the security and compliance of Log Service.
In terms of security for enterprise data, ransomware is one of the most dangerous cyberattack forms. After data is encrypted by ransomware, it is difficult to decrypt unless you pay the ransom. Data center faults, natural disasters, and accidental deletion may also incur data security risks and business interruptions. The intrinsic resource advantages of the cloud provide the conditions that make it possible to solve these problems.
Alibaba Cloud provides storage products with multi-version functions that allow users to retain and restore previous file versions and customize the retention period. In the event of data loss or damage caused by ransomware or human errors, data can be restored by rolling back to a previous version. This ensures that user businesses are not affected.
In June 2018, Alibaba Cloud officially released Hybrid Backup Recovery (HBR) and Hybrid Disaster Recovery (HDR), the first cloud-native products in China. HBR and HDR provide cloud backup and disaster recovery protection and allow users to deploy disaster recovery solutions in minutes. Alibaba Cloud released a storage service that allows users to deploy three availability zones in the same city, which was also a first in the Chinese market. This service can meet enterprise users' need for zero data loss and uninterrupted business in the case of data center-level disasters.
Compared with the construction of offline, local disaster recovery data centers, OSS zone-redundant storage provides a 99.95% availability service-level-agreement (SLA) guarantee, 99.9999999999% reliability, and one-click deployment of cloud-based zone disaster recovery services. By incorporating cross-region replication capabilities, OSS can provide complete disaster recovery services at the data center, region, and cross-region levels.
AI security technology for protecting data privacy has developed in the field of distributed computing and information security, providing a new computing model for collaborative network computing. This approach uses multiple technologies to protect data security, including secure multi-party computing, differential privacy, dynamic encryption, and encrypted search and computing. By leveraging AI and related technologies, Alibaba Cloud storage products are evolving to be more automated and intelligent in the security and governance of stored data. At the same time, the Alibaba Cloud Storage team will work with DAMO Academy to explore ways to reduce trust costs and financial costs and give full play to the value of data.
Currently, Alibaba Cloud provides storage services to millions of customers in government, Internet, finance, healthcare, and education. Our storage services are deployed on a global scale with a capacity exceeding 100 EB. Alibaba Cloud is committed to providing users with stable, secure, reliable, and easy-to-use storage services.
In the future, we will continue to focus on customer needs and refine our storage technology and products to create more value for customers. We aim to allow customers to enjoy the technical and service benefits made possible by cloud computing.
Ant Financial's ApsaraDB for OceanBase Now Available on Alibaba Cloud
A Guide to CDN Security Protection: Managing Tampering, Attacks, and Content

31 posts | 5 followers
FollowAlibaba Clouder - November 6, 2017
Alibaba Clouder - March 3, 2021
Alibaba Cloud New Products - June 10, 2020
Nick Fan - January 17, 2023
Alibaba Clouder - August 26, 2020
Alibaba Clouder - March 26, 2020

31 posts | 5 followers
Follow Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Data Security on the Cloud Solution
Data Security on the Cloud Solution
This solution helps you easily build a robust data security framework to safeguard your data assets throughout the data security lifecycle with ensured confidentiality, integrity, and availability of your data.
Learn More Backup and Archive Solution
Backup and Archive Solution
Alibaba Cloud provides products and services to help you properly plan and execute data backup, massive data archiving, and storage-level disaster recovery.
Learn More Data Lake Storage Solution
Data Lake Storage Solution
Build a Data Lake with Alibaba Cloud Object Storage Service (OSS) with 99.9999999999% (12 9s) availability, 99.995% SLA, and high scalability
Learn MoreMore Posts by Alibaba Cloud New Products