By Shantanu Kaushik
Cloud storage has evolved in-sync with cloud computing. Over the years, different practices and trends have set a steady pace of development for the industry and the technology that drives it. Security and access control define the two most important parameters for any technology to work correctly.
Maintaining functionality and user experience is critical. Any product that can maintain a steady delivery system can account for high data durability. This persistence of service is what sets the Alibaba Cloud Storage solutions apart. In this article, we will showcase the implementation scenarios that make your choice of cloud storage a secure one.
Integration with industry-leading tools like the Alibaba Cloud Resource Access Management (RAM) service and the latest encryption model is the key focus of this article.
Alibaba Cloud storage products, including Object Storage Service (OSS), Block Storage, and Apsara File Storage NAS offer extensive security capabilities. Security features like server-side encryption, client-side encryption, log audit, fine-grained access control, and hot-link protection are offered as standards. Retention policies based on WORM and lifecycle policy management are also an added benefit that comes by default with Alibaba Cloud Storage solutions.
The Object Storage Service (OSS), Block Storage, Apsara File Storage NAS, and Storage Capacity Unit (SCU) offer an access control list (ACL). You can use this feature to control access based on permissions. You can assign read/write access based on user type. You can select authorization based on public and private access lists. You have the option to define these policies based on specific needs.
Resource Access Management (RAM) is used for identification and access control. You can set policies based on user responsibilities and manage users by configuring RAM policies. RAM allows you to create and define policies that can control resources assigned to a particular user of a group.
Object Storage Service provides hotlink protection to avoid unauthorized access to your buckets. You can easily set the HTTP/HTTPS referrer to configure the referrer whitelist to allow requests from specific domain names. Access is also provided if the HTTP/HTTPS referrer is included with the request to access the OSS resource. Hotlink protection prevents any hotlinking of data in public read and public read/write buckets.
Server-side encryption for uploaded data processes the data to encrypt it while the data is uploaded and decrypts it back when it's downloaded. Server-side encryption is used to protect static data, which is recommended for high data security scenarios that may include online document collaboration or examples of deep learning.
You can implement the following methods for server-side encryption:
In this method, the Customer Master Keys (CMKs) are rotated regularly to ensure better security practices and to enable regular encrypting and decrypting operations on objects. Object Storage Service uses AES-256 for encryption of objects with different data keys. The data keys are generated and managed by OSS.
SSE-KMS enables encryption and decryption of large amounts of data using a specified CMK ID or a default key stored in KMS. This is relatively a more cost-worthy method as there is no requirement of transmitting user data to KMS through networks.
KMS is secure, can be easily managed, and uses AES-256 encryption. Alibaba Cloud KMS has high integrity, security, and availability features and offers a seamless experience. It allows you to custom-build encryption/decryption solutions to align with your business needs.
Before the data is uploaded to OSS, client-side encryption is performed to encrypt objects. With client-side encryption, symmetric encryption is achieved by generating a random data key. This random data key is generated by the client and uploaded as a part of object metadata, which is stored on the Object Storage Service (OSS). Whenever an object is downloaded, the random data key is decrypted using the CMK, and the generated data key is used to decrypt the object.
There are two ways to use Client-Side encryption:
The illustration below is an example of CMK managed by KMS:
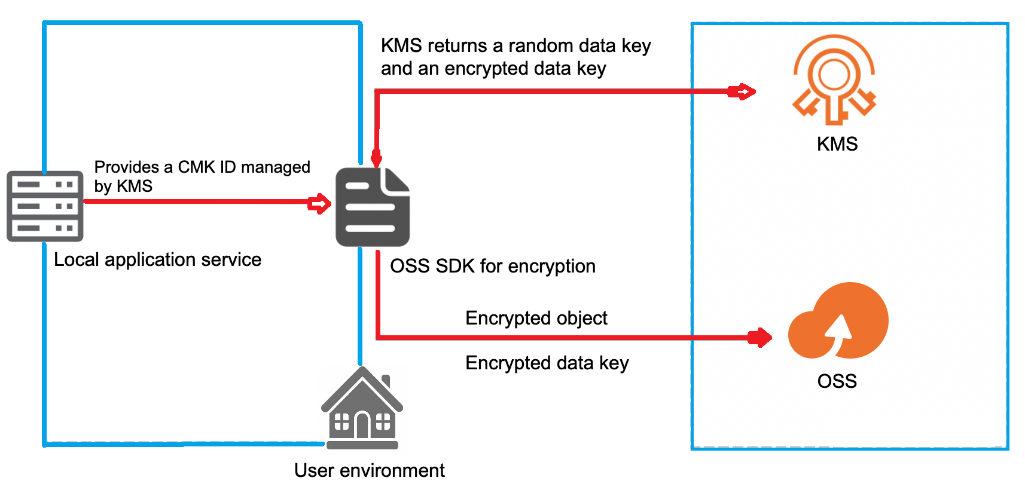
The basic steps included are:
Upload
Download
In this scenario, the CMKs have to be generated by the client. When an upload operation is executed, you need to perform the client-side encryption of the object. You need to upload an asymmetric or symmetric CMK.
The illustration below depicts this scenario:
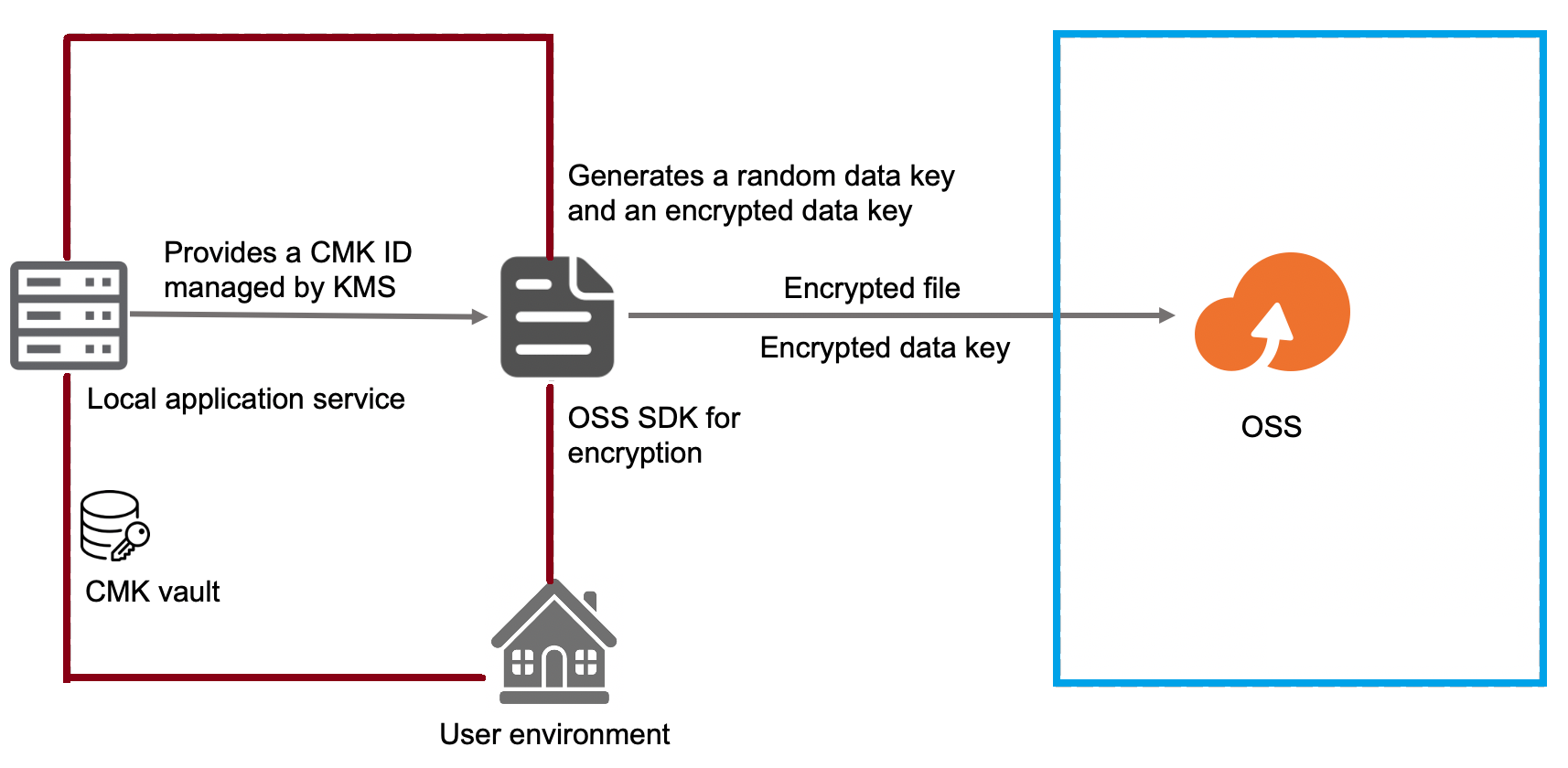
Encrypt an Object
Decrypt an Object
Data Security is an essential component of any service that is responsible for handling critical and sensitive data. Alibaba Cloud hosts a variety of services that enable and execute security parameters at the highest level. It is imperative to maintain data while at rest or while transmitting. It is the level of integration that makes any solution a reliable one. Alibaba Cloud's line of products works in sync to maintain and extend the high-standards of data durability.
1. Security and Monitoring Practices with Alibaba Cloud Storage Solutions – Part 2
We will focus on Object Storage Service Sandboxing, overall monitoring, and metrics collection with Alibaba Cloud Storage Solutions.
2. Apsara File Storage NAS – What and How?
We will discuss the complete architecture and usage scenarios with the Apsara File Storage NAS solution by Alibaba Cloud.
Alibaba Cloud Launches Enterprise-Level Cloud-Native Data Lake during 2020 Double 11
Security and Monitoring Practices – Alibaba Cloud Storage Solutions – Part 2

2,599 posts | 768 followers
FollowAlibaba Clouder - November 17, 2020
Alibaba Clouder - November 19, 2020
Alibaba Clouder - October 29, 2020
Alibaba Clouder - November 12, 2020
Alibaba Clouder - November 26, 2020
Nick Patrocky - January 24, 2024

2,599 posts | 768 followers
Follow Storage Capacity Unit
Storage Capacity Unit
Plan and optimize your storage budget with flexible storage services
Learn More Hybrid Cloud Storage
Hybrid Cloud Storage
A cost-effective, efficient and easy-to-manage hybrid cloud storage solution.
Learn More Hybrid Cloud Distributed Storage
Hybrid Cloud Distributed Storage
Provides scalable, distributed, and high-performance block storage and object storage services in a software-defined manner.
Learn More Data Lake Storage Solution
Data Lake Storage Solution
Build a Data Lake with Alibaba Cloud Object Storage Service (OSS) with 99.9999999999% (12 9s) availability, 99.995% SLA, and high scalability
Learn MoreMore Posts by Alibaba Clouder