By Shantanu Kaushik
Cloud security offers solutions to numerous threats that arise on the Internet every day. Ransomware, Distributed Denial of Service (DDoS), and other phishing attacks have significantly impacted the performance and reliability of cloud services. The IT industry created solutions to counter these arbitrary impacts on services, ward-off attacks, and provide highly reliable and available service solutions.
Cloud service providers like Alibaba Cloud have numerous products in their security products lineup:
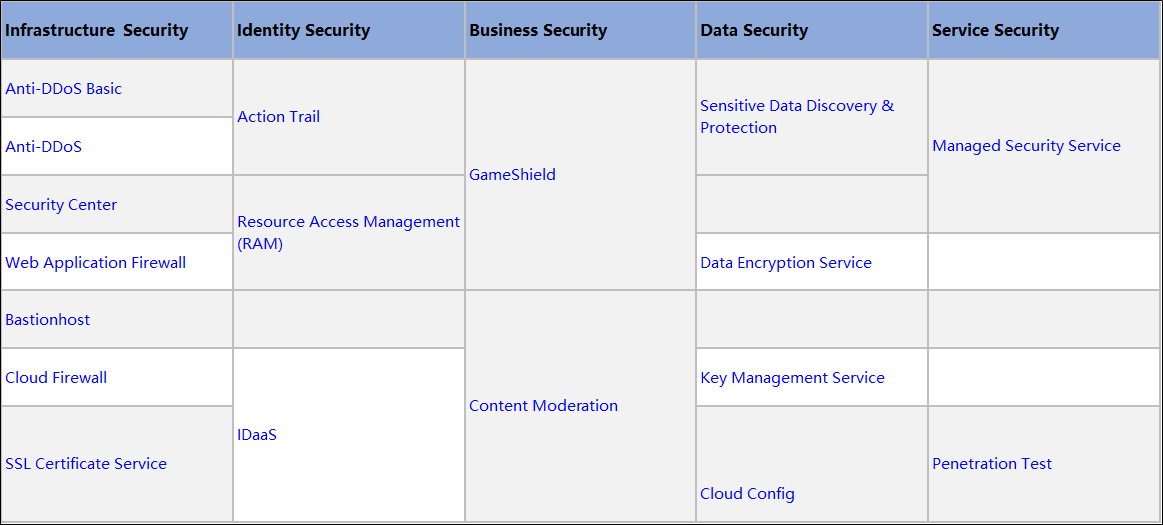
This article discusses all aspects of the Alibaba Cloud Security Center.
Alibaba Cloud Security Center is an all-in-one security management platform that can centrally-manage all of the security systems associated with your Alibaba Cloud account. The Security Center can identify and analyze security threats on the fly. If a threat is detected, the Security Center automatically sends an alert to the administrator.
The Alibaba Cloud Security Center feature set offers:
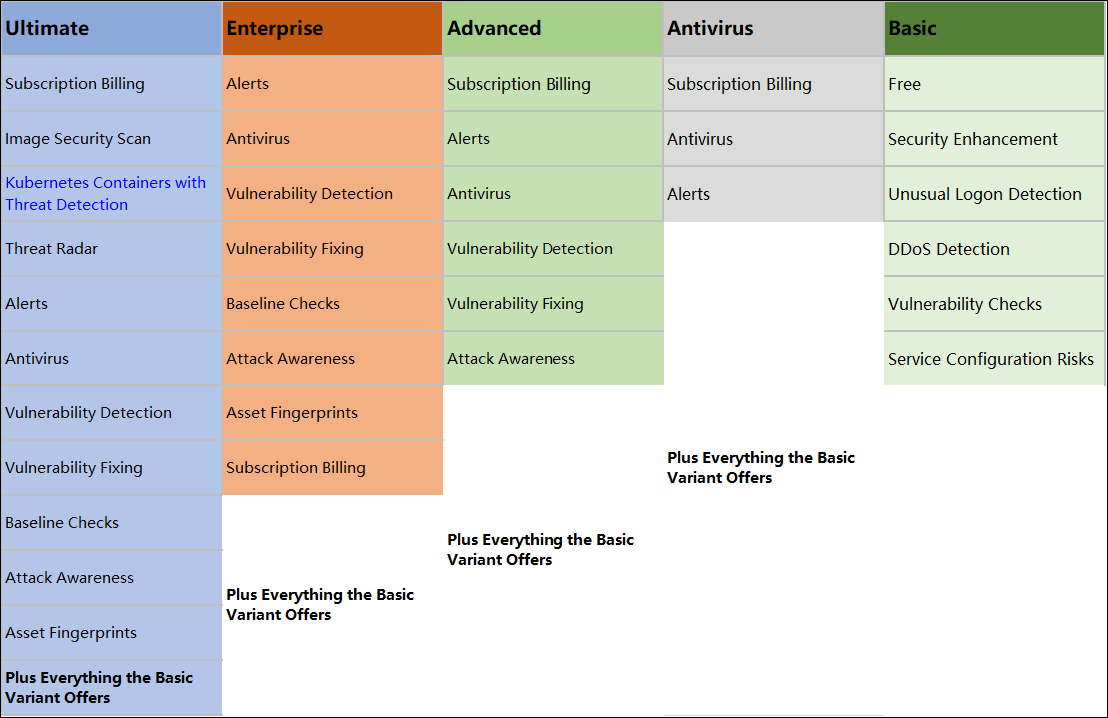
Alibaba Cloud Security Center offers the highest security levels. It packs an intelligent system powered by big data technologies that automate and regulate security tasks and operations. The Security Center is highly efficient with threat tracing and responding to threats. It enables security for cloud resources and the servers located in data centers. The basic variant of the Alibaba Cloud Security Center protects against DDoS attacks, unusual logons, service configuration risks, and server vulnerabilities. It also offers a security enhancement service.
Alibaba Cloud Security Center activates automatically after you purchase any Alibaba Cloud product and select a security enhancement. You can choose from different Alibaba Cloud Security Center variants based on your requirements. The chart below shows the differences between the Security Center variants:
Alibaba Cloud Security Center features more than 250 threat detection models. These models are based on big data technologies, which help the system assess current information and become more capable with analytics to stop any threat. Alibaba Cloud has over a decade of experience with security implementations, including classification of different threat types like ransomware, viruses, and DDoS.
Alibaba Cloud Security Center is compatible with multiple operating systems and offers server guard management on different platforms. Even if you are deploying your services across regions, you can perform operations using the Security Center in any region.
The Security Center sends out alerts whenever the threats are detected and watches for any vulnerability and configuration issues to ensure the whole system runs smoothly. The Security Center uses situation analysis to maintain a high-performance with your security solution. The most impressive part is the graphical user interface that showcases any traces of threats and gives analysis reports of the security events.
Security Center offers real-time threat detection for Alibaba Cloud Container Service for Kubernetes (ACK). It can detect viruses and other malicious threats within the containers or on the hosts. Alibaba Cloud Security Center generates different warnings based on the type of threat detected. The threat detection includes:
1. Container Escapes: The Security Center is highly capable of misconfigurations detection within containers. Improper container configurations, operating system vulnerabilities, or Docker vulnerabilities cause Container escapes.
2. High-Risk Operations: Alibaba Cloud Security Center minimizes the potential of any vulnerabilities that might be used to exploit the entire service, including Docker API leaks, Kubernetes API leaks, or some form of privilege escalation. Container intrusion due to layer 4 attacks of the OSI model, where an attacker can try to publish malicious scripts inside containers using unauthorized access, is also averted by the Alibaba Cloud Security Center.
3. Image Startups and Viruses: The Security Center proactively monitors for any issues, malicious programs, or mining programs inside container images. This real-time monitoring helps generate alerts and detects any Trojans, viruses, scripts, or web-shells.
4. The Security Center detects:
Alibaba Cloud Security Center has a multi-dimensional approach towards asset handling. It provides a security score that is calculated based on the security status of your assets. Higher scores represent fewer issues. The Security Center displays information about each protected server, including information about the risk status, Virtual Private Cloud (VPC), and regions.
Alibaba Cloud has defined this security management service to operate in a centralized manner. It can automatically analyze the exposure of your ECS instances and present a visual representation of the communication between the ECS instances and the Internet. This helps paint a clearer picture of any system vulnerabilities.
Alibaba Cloud Security Center is a full-fledged, power-packed resource that can handle any security vulnerability.
Solving the Complexities – Starting the Digital Transformation Journey
Cloud Enterprise Network (CEN): A Secure, Global Private Network

2,593 posts | 793 followers
FollowAlibaba Cloud Service Column - November 21, 2022
Alibaba Clouder - January 13, 2021
Alibaba Clouder - April 26, 2019
OpenAnolis - May 8, 2023
Alibaba Cloud Community - December 14, 2021
Alibaba Cloud Community - February 4, 2022

2,593 posts | 793 followers
Follow ECS(Elastic Compute Service)
ECS(Elastic Compute Service)
Elastic and secure virtual cloud servers to cater all your cloud hosting needs.
Learn More Elastic Container Instance
Elastic Container Instance
An agile and secure serverless container instance service.
Learn More Anti-DDoS
Anti-DDoS
A comprehensive DDoS protection for enterprise to intelligently defend sophisticated DDoS attacks, reduce business loss risks, and mitigate potential security threats.
Learn More Anti DDoS Basic
Anti DDoS Basic
A cloud-based security service that protects your data and application from DDoS attacks
Learn MoreMore Posts by Alibaba Clouder