11.11 The Biggest Deals of the Year. 40% OFF on selected cloud servers with a free 100 GB data transfer! Click here to learn more.
In your application deployment environment, do you experience the following situations?
If any of the above sounds familiar, then your production environment may be at risk of data leakage. Read on further to understand how you can increase your data security with Alibaba Cloud Application Configuration Management (ACM).
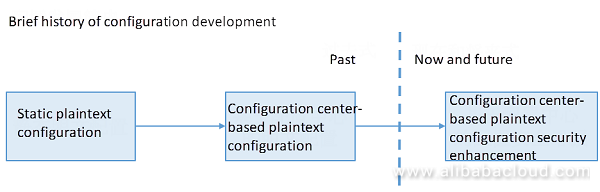
Let's look at why relying solely on the first two methods can be problematic.
Before the distributed Internet architecture, the initial configuration were stored in static files. For example, database connection data (including passwords) is manually packaged in various environments (such as development, testing, pre-release, production) as shown in the following figure:
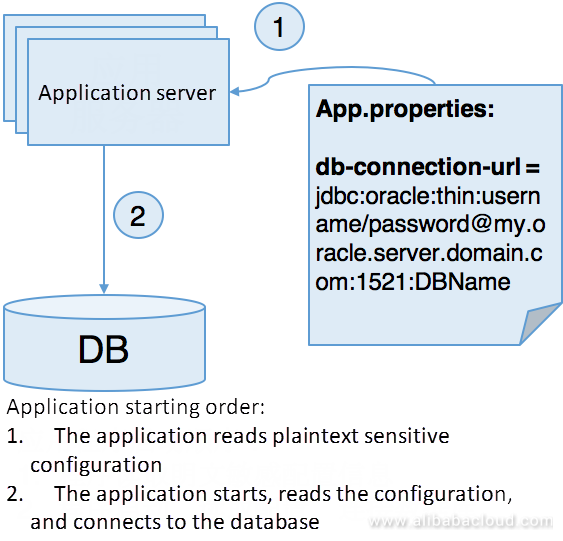
The biggest problem with this deployment method is that a significant amount of sensitive information will get stored in the configuration file. Regardless of what development, testing or O&M personnel did to secure the file, it is easy for hackers to obtain sensitive data. Although the methods of packaging and deployment have been evolving from static file configuration to environment-based static packaging and deployment and on to container orchestration, the methods of static file configuration are virtually unchanged. With the automation of deployment tools, the security problems of its configuration have become more dangerous, for example:
Configuration centers' most significant advantage is that configuration can be dynamically modified and released while configuring and releasing the decoupling. Other benefits and various scenarios of the configuration center are not the focus of this document. Refer to Configuration Center Scenarios to learn more about these scenarios.
The primary impact of the configuration center on configuration security gets described here. A simple schematic of the configuration center storing the configuration is shown in the figure below.
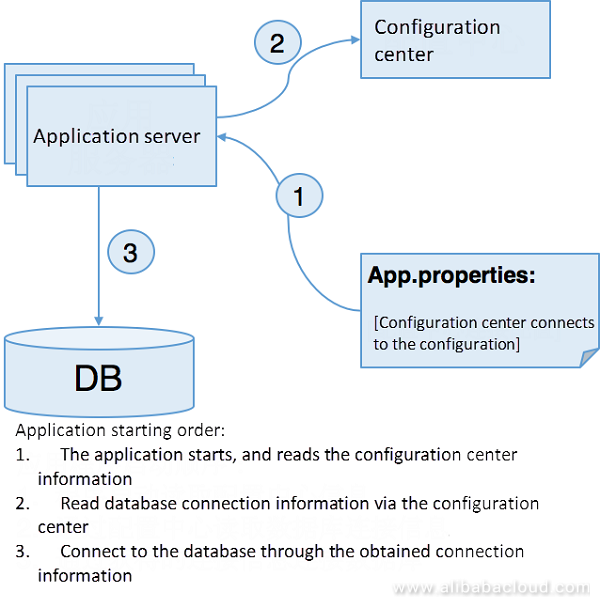
The configuration center has the following security impacts on the application configuration:
From the security aspect, configuration management based on the configuration center solves the problem of sensitive information leakage in the production environment. However, another issue that arises is the security of the configuration center itself. Almost all products store the actual configuration in plaintext looking at the product design of the above several configuration centers. If the configuration center gets attacked, all stored sensitive information will get leaked entirely. In today's cloud era, this challenge is particularly critical for cloud vendors that provide configuration center services when facing a security compliance audit such as the level 3 protection.
Recently, Alibaba Cloud has released a "security configuration" function for users to store configurations in the configuration center in a more secure way using Application Configuration Management (ACM). The description of its functional details is in the following sections.
Alibaba Cloud Application Configuration Management (ACM) recently added a function for configuration security called "Security Configuration". This is created through the interconnection of a series of configuration security related products, to completely solve the above configuration center security problems. ACM's approach to solving security problems is similar to other industry-leading configuration center products. It works not by solving security problems independently, but rather by integrating with other security products from Alibaba Cloud. Let's see how ACM works.
In this regard, Alibaba Cloud ACM solves this problem through integrating with the RAM and KMS products:
The core idea of ACM security configuration is to encrypt/decrypt the configuration through KMS. A detailed description is as below.
First, we will see what steps are required if a user wants to use ACM's security configuration function as shown in the following figure.
The figure below shows the process for a user to write security configuration on the ACM console:
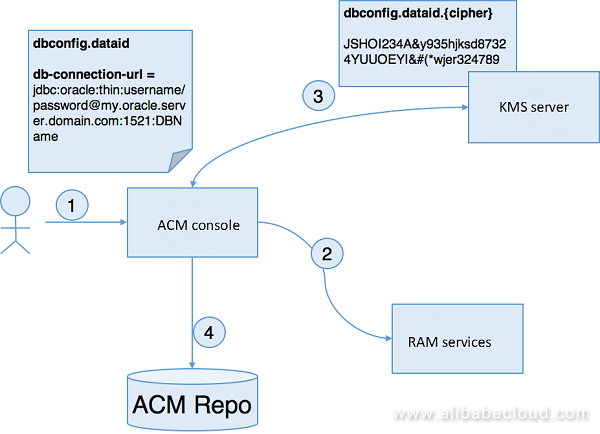
Detailed steps:
From the above process, we can see that:
Theoretically, in the above steps, when the user writes the configuration, the user can write on the console after KMS encryption entirely without relying on the ACM console functions. Of course, this will cause a problem with ease of use. In process design of writing ACM security configuration, calling KMS through authorization interconnection with the RAM not only ensures security but also brings great convenience to the user in creation of the configuration; this is a very balanced compromise.
The figure below shows the process for an application to read security configuration through ACM SDK:
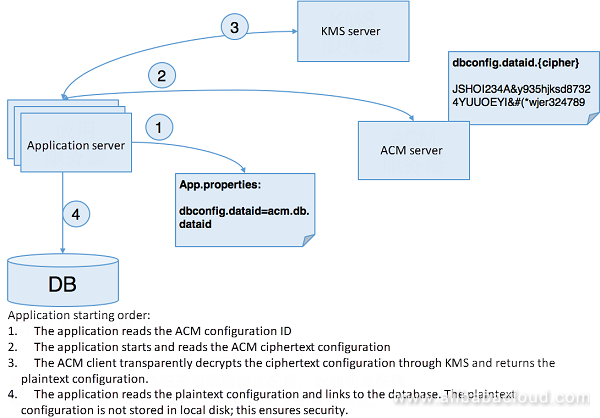
Detailed steps:
From the above process, we can see that:
From the above sections, it can is visible that the Application Configuration Management (ACM) security configuration achieves a good balance between security and ease of use.

As a product oriented to the configuration center and focused on user configuration, the primary goal of ACM in the cloud era is to ensure the security of the user's configuration. On this basis, ACM will protect the security of the user's configuration through integration with more Alibaba Cloud products. The scenarios will include but are not limited to:
Read similar articles and learn more about Alibaba Cloud's products and solutions at www.alibabacloud.com/blog
Building a RESTful API with Express, PostgreSQL, and Node Using ES6
Using Second-Level Monitoring to Troubleshoot MongoDB Errors

2,599 posts | 762 followers
FollowAlibaba Cloud Community - February 2, 2022
Alibaba Cloud Community - November 12, 2024
Alibaba Cloud Community - February 21, 2022
Alibaba Clouder - July 10, 2020
Alibaba Clouder - August 16, 2019
Alibaba Clouder - November 5, 2020

2,599 posts | 762 followers
FollowLearn More
 Key Management Service
Key Management Service
Create, delete and manage encryption keys with Alibaba Cloud Key Management Service
Learn More RAM(Resource Access Management)
RAM(Resource Access Management)
Secure your cloud resources with Resource Access Management to define fine-grained access permissions for users and groups
Learn MoreMore Posts by Alibaba Clouder